JOINT FORCE QUARTERLY ISSUE NINETY, 3RD QUARTER 2018 Joint Force Quarterly Founded in 1993 • Vol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
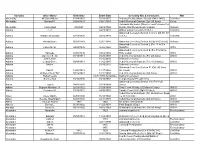
Surname Given Name Birth Date Death Date Cemetery Site & Comments
Surname Given Name Birth Date Death Date Cemetery Site & Comments. War Abernathy William Wilkins 11/24/1825 02/15/1875 Bethany Presby (Home Guard) (1861-1865) Civil War Abernathy Garland P. 03/08/1931 03/01/1984 Iredell Memorial Gardens (Cpl US Army) Korea Rehoboth Methodist (Sherrils Ford/Catawba Co) Abernathy Jimmy Edd 03/20/47 02/02/1969 Bronze Star/Purple Heart) Vietnam Vietnam Adams J. P. 04/25/1881 Willow Valley Cemetery (C.S.A.) Civil War Oakwood Cemetery Section C (Co C 4th NC Inf Adams William McLelland 07/13/1838 02/02/1918 C.S.A.) Civil War Adams Ronald Elam 06/28/1943 12/01/1988 Oakwood Cemetery Section Q (Sp 4 US Army) Vietnam Oakwood Cemetery Section L (Pvt 13 Inf Co Adams Calvin M. Sr. 04/24/1889 05/06/1968 MGOTS) WW I Oakwood Cemetery Section E (Pvt STU Army Adams Talmage 03/05/1899 09/02/1969 TNG Corps) WW I Adams Clarence E., Sr. 08/19/1911 08/20/1993 Iredell Memorial Gardens (Pvt US Army) WW II Adams John Lester 01/15/2010 Belmont Cemetery Adams Leland Orville 09/04/1914 11/02/1987 Iredell Memorial Gardens (Tec 4 US Army) WW II Adams Melvin 04/19/2012 Belmont Cemetery Oakwood Cemetery Section R (Cpl US Army Adams Paul K. 12/20/1919 11/17/1992 Air Corps) WW II Adams William Alfred "Bill" 07/26/1923 12/11/1998 Iredell Memorial Gardens (US Army) WW II Adams Robert Lewis 08/31/1991 burial date Belmont Cemetery Adams Stamey Neil 10/14/1936 10/14/1992 Temple Baptist Pfc US Army Oakwood Cemetery Section Vet (Tec4 US Adcox Floyd A. -

Offensive Against the Syrian City of Manbij May Be the Beginning of a Campaign to Liberate the Area Near the Syrian-Turkish Border from ISIS
June 23, 2016 Offensive against the Syrian City of Manbij May Be the Beginning of a Campaign to Liberate the Area near the Syrian-Turkish Border from ISIS Syrian Democratic Forces (SDF) fighters at the western entrance to the city of Manbij (Fars, June 18, 2016). Overview 1. On May 31, 2016, the Syrian Democratic Forces (SDF), a Kurdish-dominated military alliance supported by the United States, initiated a campaign to liberate the northern Syrian city of Manbij from ISIS. Manbij lies west of the Euphrates, about 35 kilometers (about 22 miles) south of the Syrian-Turkish border. In the three weeks since the offensive began, the SDF forces, which number several thousand, captured the rural regions around Manbij, encircled the city and invaded it. According to reports, on June 19, 2016, an SDF force entered Manbij and occupied one of the key squares at the western entrance to the city. 2. The declared objective of the ground offensive is to occupy Manbij. However, the objective of the entire campaign may be to liberate the cities of Manbij, Jarabulus, Al-Bab and Al-Rai, which lie to the west of the Euphrates and are ISIS strongholds near the Turkish border. For ISIS, the loss of the area is liable to be a severe blow to its logistic links between the outside world and the centers of its control in eastern Syria (Al-Raqqah), Iraq (Mosul). Moreover, the loss of the region will further 112-16 112-16 2 2 weaken ISIS's standing in northern Syria and strengthen the military-political position and image of the Kurdish forces leading the anti-ISIS ground offensive. -

Joint Force Quarterly 97
Issue 97, 2nd Quarter 2020 JOINT FORCE QUARTERLY Broadening Traditional Domains Commercial Satellites and National Security Ulysses S. Grant and the U.S. Navy ISSUE NINETY-SEVEN, 2 ISSUE NINETY-SEVEN, ND QUARTER 2020 Joint Force Quarterly Founded in 1993 • Vol. 97, 2nd Quarter 2020 https://ndupress.ndu.edu GEN Mark A. Milley, USA, Publisher VADM Frederick J. Roegge, USN, President, NDU Editor in Chief Col William T. Eliason, USAF (Ret.), Ph.D. Executive Editor Jeffrey D. Smotherman, Ph.D. Production Editor John J. Church, D.M.A. Internet Publications Editor Joanna E. Seich Copyeditor Andrea L. Connell Associate Editor Jack Godwin, Ph.D. Book Review Editor Brett Swaney Art Director Marco Marchegiani, U.S. Government Publishing Office Advisory Committee Ambassador Erica Barks-Ruggles/College of International Security Affairs; RDML Shoshana S. Chatfield, USN/U.S. Naval War College; Col Thomas J. Gordon, USMC/Marine Corps Command and Staff College; MG Lewis G. Irwin, USAR/Joint Forces Staff College; MG John S. Kem, USA/U.S. Army War College; Cassandra C. Lewis, Ph.D./College of Information and Cyberspace; LTG Michael D. Lundy, USA/U.S. Army Command and General Staff College; LtGen Daniel J. O’Donohue, USMC/The Joint Staff; Brig Gen Evan L. Pettus, USAF/Air Command and Staff College; RDML Cedric E. Pringle, USN/National War College; Brig Gen Kyle W. Robinson, USAF/Dwight D. Eisenhower School for National Security and Resource Strategy; Brig Gen Jeremy T. Sloane, USAF/Air War College; Col Blair J. Sokol, USMC/Marine Corps War College; Lt Gen Glen D. VanHerck, USAF/The Joint Staff Editorial Board Richard K. -

The Syrian War and the Question of an American Mutiny
The Syrian War And The Question Of An American Mutiny By Adeyinka Makinde Region: Middle East & North Africa, USA Global Research, October 11, 2016 Theme: History, US NATO War Agenda Adeyinka Makinde In-depth Report: SYRIA A recent press conference given by US Army General Mark Milley, the present serving army chief of staff reminded me of the fictional character played by Burt Lancaster in the 1964 movie ‘Seven Days in May’. That film posited the scenario of James Scott (the Lancaster character) as a Chairman of the Joint Chiefs of Staff who, disgruntled about the serving president’s perceived weakness in seeking a treaty with the Soviet Union, plots to overthrow the civilian government. ‘Seven Days in May’ was based on a book that drew its inspiration from real life American political and military figures in the early 1960s during the Cold War. At that time Right-wing, verging on fascist-leaning generals such as Army General Lyman Lemnitzer the supremo at the Pentagon and Air Force Generals Curtis LeMay and Tommy Powers dominated the Pentagon. A Major General named Edwin Walker actually tried to indoctrinate troops under his command with the teachings of the Right-wing John Birch Society. It was in the prevailing atmosphere of fervent anti-communism at the time that these generals sought to undermine and even plot to overthrow the government of President John F. Kennedy. This view was not limited to a few senators and journalists of the time. The Kremlin apparently believed this to the extent that it is claimed to have influenced Nikita Khruschev’s decision to reach the settlement that he did with Kennedy over the Cuban Missile Crisis. -

Southern Medical and Surgical Journal
SOUTHERN MEDICAL AND SURGICAL JOURNAL. EDITED BY HENRY F. CAMPBELL, A.M., M. D., GEORGIA PROKES-OR OK BPECIAL AND COMPARATIVE ANATOMY IN TBI MEDICAL COLLEGK OF ROBERT CAMPBELL, A.M..M.D., DBMOSrtTRATOB OF ANATOMY IN THE MEDICAL COLLEGE MEPICAL COLLEGE OF GEORGIA. YOL. XIV.—1858.—NEW SERIES. AUGUSTA, G A: J. MORRIS, PRINTER AND PUBLISHER. 1858. SOUTHERN MEDICAL KM) SURGICAL JOURNAL. (NEW SERIES.) Vol. XIV.] AUGUSTA, GEORGIA, OCTOBER, 1838. [No. 10. ORIGINAL AXD ECLECTIC. ARTICLE XXII. Observations on Malarial Fever. By Joseph Joxes, A.M., M.D., Professor of Physics and Natural Theology in the University of Georgia, Athens; Professor of Chemistry and Pharmacy in the Medical College of Georgia, Augusta; formerly Professor of Medical Chemistry in the Medical College of Savannah. [Continued from page 601 of September Xo. 1858.] Case XXVIII.—Scotch seaman ; age 14 ; light hair, blue eyes, florid complexion; height 5 feet 2 inches; weight 95 lbs. From light ship, lying at the mouth of Savannah river. Was taken sick three days ago. September 16th, 7 o'clock P. M. Face as red as scarlet; skin in a profuse perspiration, which has saturated his thick flannel shirt and wet the bed-clothes. Pulse 100. Eespiration 24 : does not correspond with the flushed appearance of his face. Tem- perature of atmosphere, 88° F. ; temp, of hand, 102 ; temp, un- der tongue, 103.25. Tip and middle of tongue clean and of a bright red color; posterior portion (root) of tongue, coated with yellow fur; tongue rough and perfectly dry. When the finger is passed over the tongue, it feels as dry and harsh as a rough board. -

The Biden Administration and the Middle East: Policy Recommendations for a Sustainable Way Forward
THE BIDEN ADMINISTRATION AND THE MIDDLE EAST: POLICY RECOMMENDATIONS FOR A SUSTAINABLE WAY FORWARD THE MIDDLE EAST INSTITUTE MARCH 2021 WWW.MEI.EDU 2 The Biden Administration and the Middle East: Policy Recommendations for a Sustainable Way Forward The Middle East Institute March 2021 3 CONTENTS FOREWORD Iraq 21 Strategic Considerations for Middle East Policy 6 Randa Slim, Senior Fellow and Director of Conflict Paul Salem, President Resolution and Track II Dialogues Program Gerald Feierstein, Senior Vice President Ross Harrison, Senior Fellow and Director of Research Israel 23 Eran Etzion, Non-Resident Scholar POLICY BRIEFS Jordan 26 Dima Toukan, Non-Resident Scholar Countries/Regions Paul Salem, President US General Middle East Interests & Policy Priorities 12 Paul Salem, President Lebanon 28 Christophe Abi-Nassif, Director of Lebanon Program Afghanistan 14 Marvin G. Weinbaum, Director of Afghanistan and Libya 30 Pakistan Program Jonathan M. Winer, Non-Resident Scholar Algeria 15 Morocco 32 Robert Ford, Senior Fellow William Lawrence, Contributor Egypt 16 Pakistan 34 Mirette F. Mabrouk, Senior Fellow and Director of Marvin G. Weinbaum, Director of Afghanistan and Egypt Program Pakistan Program Gulf Cooperation Council (GCC) 18 Palestine & the Israeli-Palestinian Peace Process 35 Gerald Feierstein, Senior Vice President Nathan Stock, Non-Resident Scholar Khaled Elgindy, Senior Fellow and Director of Program Horn of Africa & Red Sea Basin 19 on Palestine and Palestinian-Israeli Affairs David Shinn, Non-Resident Scholar Saudi Arabia 37 Iran -

Political Science 279/479 War and the Nation-State
Political Science 279/479 War and the Nation-State Hein Goemans Course Information: Harkness 320 Fall 2010 Office Hours: Monday 4{5 Thursday 16:50{19:30 [email protected] Harkness 329 This course examines the development of warfare and growth of the state. In particular, we examine the phenomenon of war in its broader socio-economic context between the emergence of the modern nation-state and the end of World War II. Students are required to do all the reading. Student are required to make a group presentation in class on the readings for one class (25% of the grade), and there will be one big final (75%). Course Requirements Participation and a presentation in the seminar comprises 25% of your grade. A final exam counts for 75%. The final exam is given during the period scheduled by the University. In particular instances, students may substitute a serious research paper for the final. Students interested in the research paper option should approach me no later than one week after the mid-term. Academic Integrity Be familiar with the University's policies on academic integrity and disciplinary action (http://www.rochester.edu/living/urhere/handbook/discipline2.html#XII). Vi- olators of University regulations on academic integrity will be dealt with severely, which means that your grade will suffer, and I will forward your case to the Chair of the College Board on Academic Honesty. The World Wide Web A number of websites will prove useful: 1. General History of the 20th Century • http://www.bbc.co.uk/history/war/ • http://users.erols.com/mwhite28/20centry.htm • http://www.fsmitha.com/ 2. -

City of Atlanta 2016-2020 Capital Improvements Program (CIP) Community Work Program (CWP)
City of Atlanta 2016-2020 Capital Improvements Program (CIP) Community Work Program (CWP) Prepared By: Department of Planning and Community Development 55 Trinity Avenue Atlanta, Georgia 30303 www.atlantaga.gov DRAFT JUNE 2015 Page is left blank intentionally for document formatting City of Atlanta 2016‐2020 Capital Improvements Program (CIP) and Community Work Program (CWP) June 2015 City of Atlanta Department of Planning and Community Development Office of Planning 55 Trinity Avenue Suite 3350 Atlanta, GA 30303 http://www.atlantaga.gov/indeex.aspx?page=391 Online City Projects Database: http:gis.atlantaga.gov/apps/cityprojects/ Mayor The Honorable M. Kasim Reed City Council Ceasar C. Mitchell, Council President Carla Smith Kwanza Hall Ivory Lee Young, Jr. Council District 1 Council District 2 Council District 3 Cleta Winslow Natalyn Mosby Archibong Alex Wan Council District 4 Council District 5 Council District 6 Howard Shook Yolanda Adreaan Felicia A. Moore Council District 7 Council District 8 Council District 9 C.T. Martin Keisha Bottoms Joyce Sheperd Council District 10 Council District 11 Council District 12 Michael Julian Bond Mary Norwood Andre Dickens Post 1 At Large Post 2 At Large Post 3 At Large Department of Planning and Community Development Terri M. Lee, Deputy Commissioner Charletta Wilson Jacks, Director, Office of Planning Project Staff Jessica Lavandier, Assistant Director, Strategic Planning Rodney Milton, Principal Planner Lenise Lyons, Urban Planner Capital Improvements Program Sub‐Cabinet Members Atlanta BeltLine, -

Design and Control of a Personal Assistant Robot Yang Qian
Design and Control of a Personal Assistant Robot Yang Qian To cite this version: Yang Qian. Design and Control of a Personal Assistant Robot. Other. Ecole Centrale de Lille, 2013. English. NNT : 2013ECLI0005. tel-00864692 HAL Id: tel-00864692 https://tel.archives-ouvertes.fr/tel-00864692 Submitted on 23 Sep 2013 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. N° d’ordre : 219 ECOLE CENTRALE DE LILLE THESE Présentée en vue d’obtenir le grade de DOCTEUR En Automatique, Génie Informatique, Traitement du Signal et Image Par QIAN Yang DOCTORAT DELIVRE PAR L’ECOLE CENTRALE DE LILLE Titre de la thèse : Conception et Commande d’un Robot d’Assistance à la Personne Design and Control of a Personal Assistant Robot Soutenue le 04 Juillet 2013 devant le jury d’examen : Président Saïd MAMMAR Professeur, Université d'Evry Val d'Essonne, Evry Rapporteur Nacer K.M’SIRDI Professeur, Polytech Marseille, Marseille Rapporteur Daniel SIDOBRE Maître de Conférences, HDR, Université Paul Sabatier, Toulouse Rapporteur Jianming YANG Professeur, Meijo University, Japon Membre Belkacem Ould Boumama Professeur, Polytech Lille, Lille Membre Qiang ZHAN Professeur, Beihang University, Chine Directeur de thèse Ahmed RAHMANI Maître de Conférences, HDR, Ecole Centrale de Lille, Lille Thèse préparée dans le Laboratoire d’Automatique, Génie Informatique et Signal L.A.G.I.S. -

World War Ii
WORLD WAR II ANALYZING THE SACRIFICE AND ABANDONMENT OF AMERICAN TROOPS DEFENDING THE PHILIPPINE ISLANDS DECEMBER 8, 1941 TO MAY 10, 1942 COMPILED AND RESEARCHED BY EDWARD JACKFERT 28TH BOMB SQDN–19TH BOMB GRP CLARK FIELD, PHILIPPINE ISLANDS PAST NATIONAL COMMANDER AMERICAN DEFENDERS OF BATAAN & CORREGIDOR, INC I N D E X PAGES 1 Prologue 2 Historic data on acquisition of the Philippines in 1898. 3 Early defense forces of the Philippine Islands. 4 Photo of General MacArthur and his headquarters–the Manila Hotel. 5 U.S. Army forces in the Philippines prior to World War II–31st Infantry Regiment. 6 Fourth Marine Regiment 7 200th Coast Artillery–Provisional AA–5l5th Coast Artillery-New Mexico National Guard. 8 192nd and 194th Tank Battalions–17th Ordnance Company- National Guard 9 Philippilne Scouts 10 Corregidor-Fort Drum-Fort Frank-Fort Hughes----Guardians of Manila Bay 11 803 Engineer Battalion–Aviation 12 U.S. Army Air Corps—Far Eastern Air Force 13 Photos of aircraft in the Philippines prior to World War II. 14 The Asiatic Fleet based in Manila Bay. 15 Washington Naval Treaty of 1922 and its consequences-Map of Manila Bay area defenses. 16-17 Defense plans critiqued by confusion, disagreement, mistakes, sacrifice, and abandonment—President Roosevelt remarks on war in September 1940 and Defense Department on War Plan Orange which relates to sacrificing the Philippines April 1941. 18 War warning with Japan in dispatch dated November 27, 1941 sent to Philippine defense staff. 19 Map of Philippines showing landing areas of Japanese troops in December 1941. 20 Defending the Philippine Islands. -

Losing an Empire, Losing a Role?: the Commonwealth Vision, British Identity, and African Decolonization, 1959-1963
LOSING AN EMPIRE, LOSING A ROLE?: THE COMMONWEALTH VISION, BRITISH IDENTITY, AND AFRICAN DECOLONIZATION, 1959-1963 By Emily Lowrance-Floyd Submitted to the graduate degree program in History and the Graduate Faculty of the University of Kansas in partial fulfillment of the requirements for the degree of Doctor of Philosophy. Chairperson Dr. Victor Bailey . Dr. Katherine Clark . Dr. Dorice Williams Elliott . Dr. Elizabeth MacGonagle . Dr. Leslie Tuttle Date Defended: April 6, 2012 ii The Dissertation Committee for Emily Lowrance-Floyd certifies that this is the approved version of the following dissertation: LOSING AN EMPIRE, LOSING A ROLE?: THE COMMONWEALTH VISION, BRITISH IDENTITY, AND AFRICAN DECOLONIZATION, 1959-1963 . Chairperson Dr. Victor Bailey Date approved: April 6, 2012 iii ABSTRACT Many observers of British national identity assume that decolonization presaged a crisis in the meaning of Britishness. The rise of the new imperial history, which contends Empire was central to Britishness, has only strengthened faith in this assumption, yet few historians have explored the actual connections between end of empire and British national identity. This project examines just this assumption by studying the final moments of decolonization in Africa between 1959 and 1963. Debates in the popular political culture and media demonstrate the extent to which British identity and meanings of Britishness on the world stage intertwined with the process of decolonization. A discursive tradition characterized as the “Whiggish vision,” in the words of historian Wm. Roger Louis, emerged most pronounced in this era. This vision, developed over the centuries of Britain imagining its Empire, posited that the British Empire was a benign, liberalizing force in the world and forecasted a teleology in which Empire would peacefully transform into a free, associative Commonwealth of Nations. -

Books Added to Benner Library from Estate of Dr. William Foote
Books added to Benner Library from estate of Dr. William Foote # CALL NUMBER TITLE Scribes and scholars : a guide to the transmission of Greek and Latin literature / by L.D. Reynolds and N.G. 1 001.2 R335s, 1991 Wilson. 2 001.2 Se15e Emerson on the scholar / Merton M. Sealts, Jr. 3 001.3 R921f Future without a past : the humanities in a technological society / John Paul Russo. 4 001.30711 G163a Academic instincts / Marjorie Garber. Book of the book : some works & projections about the book & writing / edited by Jerome Rothenberg and 5 002 B644r Steven Clay. 6 002 OL5s Smithsonian book of books / Michael Olmert. 7 002 T361g Great books and book collectors / Alan G. Thomas. 8 002.075 B29g Gentle madness : bibliophiles, bibliomanes, and the eternal passion for books / Nicholas A. Basbanes. 9 002.09 B29p Patience & fortitude : a roving chronicle of book people, book places, and book culture / Nicholas A. Basbanes. Books of the brave : being an account of books and of men in the Spanish Conquest and settlement of the 10 002.098 L552b sixteenth-century New World / Irving A. Leonard ; with a new introduction by Rolena Adorno. 11 020.973 R824f Foundations of library and information science / Richard E. Rubin. 12 021.009 J631h, 1976 History of libraries in the Western World / by Elmer D. Johnson and Michael H. Harris. 13 025.2832 B175d Double fold : libraries and the assault on paper / Nicholson Baker. London booksellers and American customers : transatlantic literary community and the Charleston Library 14 027.2 R196L Society, 1748-1811 / James Raven.