Lan Mail Software
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
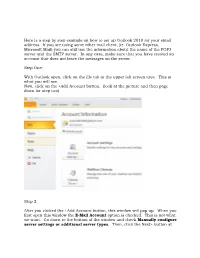
Here Is a Step by Step Example on How to Set up Outlook 2010 for Your Email Address
Here is a step by step example on how to set up Outlook 2010 for your email address. If you are using some other mail client, (ie. Outlook Express, Microsoft Mail) you can still use the information about the name of the POP3 server and the SMTP server. In any case, make sure that you have created an account that does not leave the messages on the server. Step One: With Outlook open, click on the file tab in the upper left screen area. This is what you will see. Now, click on the +Add Account button. (look at the picture and then page down for step two) Step 2: After you clicked the +Add Account button, this window will pop up. When you first open this window the E-Mail Account option is checked. This is not what we want. Go down to the bottom of the window and check Manually configure server settings or additional server types. Then, click the Next> button at the bottom of the window. (look at the picture and then page down for step three) Step 3: After you clicked the Next > button, this window will pop up. This time, the correct selection is already chosen. If, for some reason it is not checked, please check the Internet E-Mail and then click the Next> button at the bottom of the window. look at the picture and then page down for step four) Step 4: After you clicked the Next> button, this window will pop up. User Informatio n: This window is set up for the Red Knights Regalia Treasurer. -

Dynamic Allocation of Mail Server Resources Among Users
INTERNATIONAL JOURNAL OF SCIENTIFIC & TECHNOLOGY RESEARCH VOLUME 9, ISSUE 03, MARCH 2020 ISSN 2277-8616 Dynamic Allocation Of Mail Server Resources Among Users Basti M.Aliyeva Index:The article was dedicated to the solution of the problem on the dynamic allocation of mail server resources among users. It was noted that recently the electronic mail system had undergone serious changes and new features have been added to this system. The article examines the working principles of email and defines possible operating modes for subscribers. It was noted that mail server memory should be dynamically allocated among users so that the email can successfully perform its functions. In the article,the linear programming is applied to the problem of dynamic allocation of mail server memory. Known methods at every operation can resolve this issue.Proximity measure has been defined based on the Levenstein Distance (LD) for the determination of the renewal of documents on the server to improve the use of the server resources. This tool can be used to determine whether the documents have changed on the server.In the result, similar documents can be identified, and their number can be reduced up to one. Key Words: email server, dynamic allocation of the memory, operating modes of subscribes, Levenstein Distance (LD), Measures of document proximity. ———————————————————— 1. INTRODUCTİON information networks. In this case, it is essential to pay It is known that e-mail is one of the most important special attention to data transmission issues.Numerous information resources of the Internet, as well as it is the ways to transmit data and many software tools have been most massive communication tool. -

Guidelines on Electronic Mail Security
Special Publication 800-45 Version 2 Guidelines on Electronic Mail Security Recommendations of the National Institute of Standards and Technology Miles Tracy Wayne Jansen Karen Scarfone Jason Butterfield NIST Special Publication 800-45 Guidelines on Electronic Mail Security Version 2 Recommendations of the National Institute of Standards and Technology Miles Tracy, Wayne Jansen, Karen Scarfone, and Jason Butterfield C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 February 2007 U .S. Department of Commerce Carlos M. Gutierrez, Secretary Technology Administration Robert C. Cresanti, Under Secretary of Commerce for Technology National Institute of Standards and Technology William Jeffrey, Director Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security, and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-45 Version 2 Natl. Inst. Stand. Technol. Spec. Publ. 800-45 Version 2, 139 pages (Feb. -

John A. Weeks III [email protected]
John A. Weeks III [email protected] 1438 McAndrews Road East (612) 720-2854 Burnsville, MN 55337 John Weeks Skill Inventory: 1. Open Systems • HP9000, IBM RS/6000, Sun Enterprise Server • HP/UX, AIX, SunOS, Solaris, Linux, SCO UNIX, Xenix, 386/ix • Siemens SINIX, Sequent DYNIX, DEC OSF1, DG/UX, NCR, UNISYS • SVID, 4BSD, POSIX, XPG/4, i18n (Internationalization) • System Architecture, Capacity Planning, Disaster Recovery • System Administration, Performance Tuning, Back-up & Restore • UNIX Networking (DNS, NFS, NIS, R-commands, Internet) • Database Management (Sybase, Oracle, RDB, Informix) • Application Development, PERL, C, C++-Programming • Shell Programming (sh, csh, ksh, bash, AWK, sed, PERL, vi) • System Security, Security Audits, PAM, S2/S3 System Scanners • Best/1, BMC Patrol, Tivoli, NetView-6000, HP OPenview • Redundant & High Availability Systems • Veritas Volume Manager, File System, Cluster Manager, DMP • DASD, JBOD Disk Arrays, Raid Disk Arrays, Storage Area Networks 2. Networking • Most popular protocols (TCP/IP, IPX/SPX, NetBIOS, NetBEUI) • AppleTalk, AppleTalk Phase 2, LocalTalk, EtherTalk, TokenTalk • Exposure to SNA, DecNET, XNS, SCSI over Fiber Optic Cable • ODI, NDIS, Packet Driver, WinSock • CSU/DSU, TIU, NT1, Modem • Terminal Servers, Multiport Cards, Remote Access Servers • Hub, MAU, Repeater, Concentrator • Bridges, Smart Bridge, Learning Bridge, Network Switch • Router (Cisco, Wellfleet, Morningstar), BRouters • 56KB, Analog, DDS, Fractional T-1, T-1, T-3, DS-3 • ISDN, ATM, Frame Relay, DSL, Broadband • Category 3, Category 5, ThinNet, ThickNet, Fiber Optic, Coax • Ethernet, Fast Ethernet, Gigabit Ethernet, Token Ring, FDDI, ArcNet • RIP, OSPF, EGRP, Source Routing, NAT • SNMP, HP OpenView, SunNet Manager, MRTG • Pentascanner, Sniffer, Novell LANalyzer Skill Inventory: Weeks, Page 1 3. -
Download Calendar Program Windows 10 5 Best Free Open Source Calendar Software for Windows
download calendar program windows 10 5 Best Free Open Source Calendar Software for Windows. Here is a list of best free open source calendar software for Windows. These are free desktop calendar software which come with open source license. You can freely download and study source code of these calendar software and even manipulate the source code. These calendar software let you view the calendar in monthly, daily, weekly, or yearly view. You can also add and schedule important events on particular dates in a month. All of these software provide appointment editor tool to add and manage multiple appointments with date and time, reminder settings, priority, etc. You also get a feature to add and manage various contacts in a few of these software. Additionally, you can create a to-do list in these software to keep up with your daily tasks. You can also add essential notes and memos on particular dates. In one of these software, you can also import iCalendar files to add calendar events. Also, for students, there is a nice software with features including time table and booklet creator. Other than that, you get various useful features in these software which include task categories creator, email alert generator, setup calendar appearance, reminder tone, etc. In general, these are featured open source calendar software which are useful in keeping up with the dates and managing important tasks. My favorite Free Open Source Calendar Software for Windows: BORG Calendar is a good desktop calendar software which comes with a lot of handy tools including appointment editor, tasks creator, memos creator, checklists maker, etc. -

SMART SOLUTIONS Terms & Conditions - FAQ
BUSINESS SMART SOLUTIONS Terms & Conditions - FAQ Basic Total Flex Connect VIP PRO SUPER Price USD US $18 US $21 US $27 US $24 US $32 US $34 US $36 Helpdesk Concierge Secured Cloud Storage Bir Defender Security Digital and Email Marketing (1500) Website and Online Store 10 Business Email Module Definition Help Desk (Spanish and English) of technical engineers specialized in customer service and the resolution Digital Helpdesk of everyday technical incidences for SMBs through ticketing, email, dedicated phone number, and chat, 24 hours 7 days a week. This service offers a cloud storage of up to 2 Terabytes, so that the user can store all the information they Secure Cloud Storage have on their different devices (Windows, MacOS, iOS, Android) and can access that content whenever they want, from anywhere in the world and with the device you choose. Total Protection for Windows Mac OS, iOS and Android. Deployment of multiplatform device (10 Devices) Bitdefender Security with administration through Bitdefender Central with creation of security profiles through the product help desk (Basic). This tool allows customers to create different types of mailing campaigns, is easy and intuitive, and does not E-Marketing Pro require any technical expertise. The application provides templates for the creation of email campaigns, and an editor that allows customization. The service includes a user license to access the tools that allow creating a responsive website (optimized Website and Online Store for different screen sizes such as desktop, laptop, tablet and smartphones). The service includes Website Creation & Design, Domain, Hosting and Online Store. This service allows customers to make their business name a part of their domain name (e.g. -

Desktop Messaging User Guide for Novell Groupwise
Nortel CallPilot Desktop Messaging User Guide for Novell GroupWise NN44200-105 . Document status: Standard Document version: 01.04 Document date: 11 August 2009 Copyright © 2005-2009, Nortel Networks All Rights Reserved. Sourced in Canada. Information is subject to change without notice. Nortel Networks reserves the right to make changes in design or components as progress in engineering and manufacturing may warrant. The process of transmitting data and call messaging between CallPilot and its servers, switches or system is proprietary to Nortel Networks. Any other use of the data and the transmission process is a violation of the user license unless specifically authorized in writing by Nortel Networks prior to such use. Violations of the license by alternative usage of any portion of this process or the related hardware constitutes grounds for an immediate termination of the license and Nortel Networks reserves the right to seek all allowable remedies for such breach. Nortel Networks and third-party trademarks appear on the following pages: *Nortel, the Nortel logo, the Globemark, and Unified Networks, BNR, CallPilot, DMS, DMS-100, DMS-250, DMS-MTX, DMS-SCP, DPN, Dualmode, Helmsman, IVR, MAP, Meridian, Meridian 1, Meridian Link, Meridian Mail, Norstar, SL-1, SL-100, Succession, Supernode, Symposium, Telesis, and Unity are trademarks of Nortel Networks. 3COM is a trademark of 3Com Corporation. ACCENT is a trademark of Accent Software International Ltd. ADOBE is a trademark of Adobe Systems Incorporated. AMDEK is a trademark of Amdek Corporation. AT&T is a trademark of American Telephone and Telegraph Corporation. ATLAS is a trademark of Quantum Corporation. ATRIA is a trademark of Pure Atria Corporation. -

Configuring Mail Clients to Send Plain ASCII Text 3/13/17 2:19 PM
Configuring Mail Clients to Send Plain ASCII Text 3/13/17 2:19 PM Sign In Sign-Up We have copied this page for reference in case it disappears from the web. The copyright notice appears at the end. If you want the latest version go to the original page: http://www.expita.com/nomime.html Turning Off HTML or MIME to use a Remailer System. Index (5 topics) Introduction E-mail client programs (Turning Off HTML or MIME to use a Remailer System) Suggestions for HTML users Examples of HTML/MIME messages References What is wrong with sending HTML or MIME messages? There are now six main reasons for NOT doing this: 1. Many E-mail and Usenet News reader programs, usually the mail and news reader programs that come with browser packages, allow users to include binary attachments (MIME or other encoding) or HTML (normally found on web pages) within their E-mail messages. This makes URLs into clickable links and it means that graphic images, formatting, and even color coded text can also be included in E-mail messages. While this makes your E-mail interesting and pretty to look at, it can cause problems for other people who receive your E- mail because they may use different E-mail programs, different computer systems, and different application programs whose files are often not fully compatible with each other. Any of these can cause trouble with in-line HTML (or encoded attachments). Most of the time all they see is the actual HTML code behind the message. And if someone replies to the HTML formatted message, the quoting can render the message even more unreadable. -

Outlook 2000?
Microsoft® OOuuttllooookk 22000000 Student Edition Complete Computer Courseware © 2002 by CustomGuide, Inc. 1502 Nicollet Avenue South, Suite 1; Minneapolis, MN 55403 This material is copyrighted and all rights are reserved by CustomGuide, Inc. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language or computer language, in any form or by any means, electronic, mechanical, magnetic, optical, chemical, manual, or otherwise, without the prior written permission of CustomGuide, Inc. We make a sincere effort to ensure the accuracy of the material described herein; however, CustomGuide makes no warranty, expressed or implied, with respect to the quality, correctness, reliability, accuracy, or freedom from error of this document or the products it describes. Data used in examples and sample data files are intended to be fictional. Any resemblance to real persons or companies is entirely coincidental. The names of software products referred to in this manual are claimed as trademarks of their respective companies. CustomGuide is a registered trademark of CustomGuide, Inc. Table of Contents Introduction .......................................................................................................................... 7 Chapter One: The Fundamentals...................................................................................... 11 Lesson 1-1: What’s New in Outlook 2000?.........................................................................12 Lesson 1-2: -

PERANCANGAN MAIL SERVER INTRANET BERBASIS WEB BASE DENGAN OPTIMALISASI OPERASI SISTEM CLIENT Aziz Setyawan
JURNAL TEKNIK KOMPUTER VOL.I NO.1 FEBRUARI 2015 AMIK BSI PERANCANGAN MAIL SERVER INTRANET BERBASIS WEB BASE DENGAN OPTIMALISASI OPERASI SISTEM CLIENT Aziz Setyawan. H Abstract — Windows 7 operating system is a client-based operating Dengan mail berbasis web base pengguna dapat menggunakan system, or as a home edition. Which is used by the pengguna and sebuah aplikasi web browser tanpa meyimpan histori mail yang telah not as a server. With the use of the operating system is used as a digunakan oleh pengguna lain. Dengan system operasi berbasis client server or coorperate agencies no longer need to use a server-based yaitu windows 7 dapat dimaksimalkan untuk menjadi server. operating system that has had to spend to purchase a server license. E-mail server is a server system that can serve as a collective Kata kunci : Windows 7, Mail server, Web Base. storage mail to mail-mail client. Mail function to communicate information to each pengguna without the need for a print and . nature will always be saved unless the pengguna do the removal, with this system the pengguna can perform information together. I. PENDAHULUAN Development mail server rather different from the mail server at the time of development ever before, this is seen from the windows server computer operating system being used. This is because when Spesifikasi pada sistem operasi pada produk microsoft the windows issuing windows server 2008 in the development of Windows mempunyai perbedaan pada fungsinya. Dikarenakan this version of the mail server does not provide POP3 protocol spesifikasi pada fungsi inilah akan bergantung pada harga (Post Office Protocol version 3) is no longer available in the yang dikeluarkan oleh sebuah instansi maupun perorangan Windows server operating systems ranging from Windows Server dalam memiliki produk sistem operasi yang dikeluarkan oleh 2008. -
EAI Readiness in Tlds
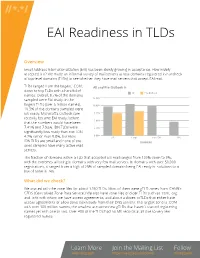
EAI Readiness in TLDs Overview Email Address Internationalization (EAI) has been slowly growing in acceptance. How widely accepted is it? We made an informal survey of mail servers across domains registered in hundreds of top-level domains (TLDs) to see whether they have mail servers that accept EAI mail. TLDs ranged from the largest, .COM, All and Pre-Outlook % down to tiny TLDs with a handful of All Pre-Outlook names. Overall, 9.7% of the domains sampled were EAI ready. In the 12.50% largest TLDs (over a million names), 10.00% 10.5% of the domains sampled were EAI ready. Microsoft’s Outlook.com 7.50% recently became EAI ready; before 5.00% that the numbers would have been 7.41% and 7.93%. IDN TLDs were 2.50% significantly less ready than non-IDN, 0.00% 4.7% rather than 9.8%, but most All Large non-IDN IDN IDN TLDs are small and none of the DOMAINS ones sampled have many active mail servers. The fraction of domains within a TLD that accepted EAI mail ranged from 100% down to 0%, with the extremes all being in domains with very few mail servers. In domains with over 50,000 registrations, it ranged from a high of 25% of sampled domains being EAI ready in .solutions to a low of none in .ren. What did we check? We started with the zone files for about 1250 TLDs. Most of them were gTLD zones from ICANN’s CZDS (Centralized Zone Data Service.) We also have zone files of older TLDs such as .com, .org, and .info with whom we have access agreements, and about a dozen ccTLDs that either have access agreements or allow zone downloads from their DNS servers. -

Rechtssichere E-Mail-Archivierung Powered by Mailstore™
Lösungen für mittelständische Unternehmen Rechtssichere E-Mail-Archivierung Powered by MailStore™ Einrichtung von ITSM!archiv Copyright © 2019 ITSM OHG ITSM OHG www.itsm-archiv.de [email protected] Elisabeth-Selbert-Str. 19 Fon +49 (0) 2173 10648-69 40764 Langenfeld / Rheinland Fax +49 (0) 2173 10648-48 Rechtssichere E-Mail-Archivierung: Einrichtung Stand: 15.04.2019 Seite 1 von 7 Lösungen für mittelständische Unternehmen Rechtssichere E-Mail-Archivierung Powered by MailStore™ Einrichtung von ITSM!archiv - Kurzfassung Die Tabelle weiter unten zeigt stichwortartig die notwendigen Schritte zur Einrichtung von ITSM!archiv. Auf den folgenden Seiten werden die einzelnen Schritte näher erläutert. ITSM unterstützt Sie bei Bedarf bei allen Schritten. Sie können aber den gesamten Vorgang auch eigenständig durchführen – ITSM benötigt in diesem Fall von Ihnen keine weiteren Daten oder administrative Rechte. ITSM kann sich mit den Ihnen übermittelten Zugangsdaten in Ihrer Instanz anmelden. Dazu wäre jedoch ein Eingriff im System erforderlich, der nicht löschbar aufgezeichnet würde, so dass Sie davon Kenntnis erhalten. ITSM wird sich nur auf ausdrückliche Aufforderung durch Sie für Supportzwecke in Ihrer Instanz anmelden. Notwendige Schritte: Wer? Was? Beide Systemvoraussetzungen klären Kunde Beauftragung der Testinstallation – E-Mail genügt ITSM Einrichten der Instanz im Rechenzentrum / Übermittlung der Zugangsdaten Kunde Download und Installation Outlook-Add-in und Client für Windows Kunde Test des Zugriffs Kunde Einrichten Benutzer Kunde Einrichten