Guidelines on Electronic Mail Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SMTP (Simple Mail Transfer Protocol)
P1: JsY JWBS001A-60.tex WL041/Bidgoli WL041-Bidgoli.cls May 12, 2005 3:27 Char Count= 0 SMTP (Simple Mail Transfer Protocol) Vladimir V. Riabov, Rivier College Introduction 1 SMTP Security Issues 12 SMTP Fundamentals 1 SMTP Vulnerabilities 12 SMTP Model and Protocol 2 SMTP Server Buffer Overflow Vulnerability 15 User Agent 4 Mail Relaying SMTP Vulnerability 15 Sending e-Mail 4 Mail Relaying SMTP Vulnerability in Microsoft Mail Header Format 4 Windows 2000 15 Receiving e-Mail 4 Encapsulated SMTP Address Vulnerability 15 The SMTP Destination Address 4 Malformed Request Denial of Service 16 Delayed Delivery 4 Extended Verb Request Handling Flaw 16 Aliases 5 Reverse DNS Response Buffer Overflow 16 Mail Transfer Agent 5 Firewall SMTP Filtering Vulnerability 16 SMTP Mail Transaction Flow 5 Spoofing 16 SMTP Commands 6 Bounce Attack 16 Mail Service Types 6 Restricting Access to an Outgoing Mail SMTP Service Extensions 8 Server 17 SMTP Responses 8 Mail Encryption 17 SMTP Server 8 Bastille Hardening System 17 On-Demand Mail Relay 8 POP and IMAP Vulnerabilities 17 Multipurpose Internet Mail Extensions Standards, Organizations, and (MIME) 8 Associations 18 MIME-Version 10 Internet Assigned Numbers Authority 18 Content-Type 10 Internet Engineering Task Force Working Content-Transfer-Encoding 10 Groups 18 Content-Id 11 Internet Mail Consortium 18 Content-Description 11 Mitre Corporation 18 Security Scheme for MIME 11 Conclusion 18 Mail Transmission Types 11 Glossary 18 Mail Access Modes 11 Cross References 19 Mail Access Protocols 11 References 19 POP3 11 Further Reading 22 IMAP4 12 INTRODUCTION and IMAP4), SMTP software, vulnerability and security issues, standards, associations, and organizations. -

Understanding Post Office Protocol (POP3)
Understanding Post Office Protocol (POP3) Author: Conrad Chung, 2BrightSparks Introduction Most Internet users with email accounts would have used some form of “client” software (Outlook, Thunderbird etc.) to access and manage their email at one point or another. To retrieve emails, these email clients may require the configuration of Post Office Protocol (or POP3) before messages can be downloaded from the server. This article will help readers understand what POP3 is and how it works. What is Post Office Protocol? The Post Office Protocol (POP3) is an Internet standard protocol used by local email software clients to retrieve emails from a remote mail server over a TCP/IP connection. Since the first version was created in 1984, the Post Office Protocol (currently at Version 3) has since became one of the most popular protocols and is used by virtually every email client to date. Its popularity lies in the protocol’s simplicity to configure, operate and maintain. Email servers hosted by Internet service providers also use POP3 to receive and hold emails intended for their subscribers. Periodically, these subscribers will use email client software to check their mailbox on the remote server and download any emails addressed to them. Once the email client has downloaded the emails, they are usually deleted from the server, although some email clients allow users to specify that mails be copied or saved on the server for a period of time. Email clients generally use the well-known TCP port 110 to connect to a POP3 server. If encrypted communication is supported on the POP3 server, users can optionally choose to connect either by using the STLS command after the protocol initiation stage or by using POP3S, which can use the Transport Layer Security (TLS) or Secure Sockets Layer (SSL) on TCP port 995 to connect to the server. -

What Is the Difference Between Email Protocols
What Is The Difference Between Email Protocols Interactions between email servers and users are governed by email protocols. The most common incoming email protocols are POP, and IMAP. Most email applications/programs support one or more of these. This article is to help users understand and choose which protocol should be selected for each user’s situation. Outgoing Incoming POP (Post Office Protocol): IMAP (Internet Message Access Protocol): SSL (Secure Socket Layer): Differences Between POP and IMAP Backups / Email Loss Outgoing SMTP (Simple Mail Transfer Protocol) is the protocol used in sending (outgoing) emails. SMTP is the protocol always used for sending (outgoing) emails. Incoming POP (Post Office Protocol) and IMAP (Internet Message Access Protocol) are two different protocols that do the same thing differently. They are both used in receiving emails from a mail server and can both are available for standard and secure (?) connections. POP (Post Office Protocol): POP is an email accessing protocol used to download emails from a mail server. Applications like Outlook and Outlook Express using POP will download all emails from the server to the user’s computer, and then delete them on the server. Generally POP server uses port 110 to listen to the POP requests or securely using SSL (Secure Socket Layer) (?) POP uses port number 995. The POP protocol assumes that there is only one client/computer that will be connecting to the mailbox. Even though there is an option in most mail applications to leave the copies of the emails in the server, it is not generally used due to various reasons. -

Ii Jacobs Rp316
!II JACOBS RP316 RACIBORZ FLOOD RESERVOIR Public Disclosure Authorized Resettlement Action Plan Public Disclosure Authorized DRAFT Public Disclosure Authorized Public Disclosure Authorized March 2005 JACOBS Document control sheet Form IP180/B Client: PCU Project: Odra Flood Mitigation Job No: J24201A Title: Draft Resettlement Action Plan Prepared by Reviewed by Approved by ORIGINAL0 NAME NAME NAME P Devitt L J S Attewill see list of authors H Fiedler-Krukowicz J Loch | DATfE SIGNATURE SIGNATURE SIGNATURE REVISION NAME NAME NAME DATE SIGNATURE SIGNATURE SIGNATURE REVISION NAME NAME NAME DATE SIGNATURE SIGNATURE SIGNATURE REVISION NAME NAME NAME DATE SIGNATURE SIGNATURE SIGNATURE This report, and infonnabon or advice which it contains, is provided by JacobsGIBB Ltd solely for internal use and reliance by its Cient in performance of JacobsGIBB Ltd's duties and liabilities under its contract with the Client Any advice, opinions, or recomrnendatons within this report should be read and retied upon only in the context of the report as a whole. The advice and opinions in this report are based upon the information nmadeavailable to JacobsGIBB Ltd at the date of this report and on current UK standards, codes, technology and constnuction practices as at the date of this report. Folloving final delvery of this report to the Client, JacobsGIBB Ltd will have no further obligations or duty to advise She Client on any mafters, including developrrient affecting the information or advice provided in ths report This report has been prepared by JacobsGIBB Ltd in their professional capaaty as Consuhing Engineers The contents of the report do not, in any way, purport to include any mranner of legal advice or opinion This report is prepared in accordance wrth the terms and conditions of JacobsGIBB Ltd's contract with the Client. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Designing a User Interface for the Innovative E-Mail Client Semester Thesis
Designing a User Interface for the Innovative E-mail Client Semester Thesis Student: Alexandra Burns Supervising Professor: Prof. Bertrand Meyer Supervising Assistants: Stephanie Balzer, Joseph N. Ruskiewicz December 2005 - April 2006 1 Abstract Email Clients have become a crucial application, both in business and for per- sonal use. The term information overload refers to the time consuming issue of keeping up with large amounts of incoming and stored email. Users face this problem on a daily basis and therefore benefit from an email client that allows them to efficiently search, display and store their email. The goal of this thesis is to build a graphical user interface for the innovative email client developed in a previous master thesis. It also explores the possibilities of designing a user interface outside of the business rules that apply for commercial solutions. 1 Contents 1 Introduction 4 2 Existing Work 6 2.1 ReMail ................................. 6 2.1.1 Methods ............................ 6 2.1.2 Problems Identified ...................... 7 2.1.3 Proposed Solutions ...................... 7 2.1.4 Assessment .......................... 8 2.2 Inner Circle .............................. 8 2.2.1 Methods ............................ 8 2.2.2 Problems Identified ...................... 9 2.2.3 Proposed Solutions ...................... 9 2.2.4 Assessment .......................... 10 2.3 TaskMaster .............................. 10 2.3.1 Methods ............................ 10 2.3.2 Problems Identified ...................... 11 2.3.3 Proposed Solution ...................... 11 2.3.4 Assessment .......................... 12 2.4 Email Overload ............................ 12 2.4.1 Methods ............................ 12 2.4.2 Problems Identified ...................... 13 2.4.3 Proposed Solutions ...................... 13 2.4.4 Assessment .......................... 14 3 Existing Solutions 16 3.1 Existing Email Clients ....................... -

Indicators for Missing Maintainership in Collaborative Open Source Projects
TECHNISCHE UNIVERSITÄT CAROLO-WILHELMINA ZU BRAUNSCHWEIG Studienarbeit Indicators for Missing Maintainership in Collaborative Open Source Projects Andre Klapper February 04, 2013 Institute of Software Engineering and Automotive Informatics Prof. Dr.-Ing. Ina Schaefer Supervisor: Michael Dukaczewski Affidavit Hereby I, Andre Klapper, declare that I wrote the present thesis without any assis- tance from third parties and without any sources than those indicated in the thesis itself. Braunschweig / Prague, February 04, 2013 Abstract The thesis provides an attempt to use freely accessible metadata in order to identify missing maintainership in free and open source software projects by querying various data sources and rating the gathered information. GNOME and Apache are used as case studies. License This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported (CC BY-SA 3.0) license. Keywords Maintenance, Activity, Open Source, Free Software, Metrics, Metadata, DOAP Contents List of Tablesx 1 Introduction1 1.1 Problem and Motivation.........................1 1.2 Objective.................................2 1.3 Outline...................................3 2 Theoretical Background4 2.1 Reasons for Inactivity..........................4 2.2 Problems Caused by Inactivity......................4 2.3 Ways to Pass Maintainership.......................5 3 Data Sources in Projects7 3.1 Identification and Accessibility......................7 3.2 Potential Sources and their Exploitability................7 3.2.1 Code Repositories.........................8 3.2.2 Mailing Lists...........................9 3.2.3 IRC Chat.............................9 3.2.4 Wikis............................... 10 3.2.5 Issue Tracking Systems...................... 11 3.2.6 Forums............................... 12 3.2.7 Releases.............................. 12 3.2.8 Patch Review........................... 13 3.2.9 Social Media............................ 13 3.2.10 Other Sources.......................... -

On the Security of Practical Mail User Agents Against Cache Side-Channel Attacks †
applied sciences Article On the Security of Practical Mail User Agents against Cache Side-Channel Attacks † Hodong Kim 1 , Hyundo Yoon 1, Youngjoo Shin 2 and Junbeom Hur 1,* 1 Department of Computer Science and Engineering, Korea University, Seoul 02841, Korea; [email protected] (H.K.); [email protected] (H.Y.) 2 School of Computer and Information Engineering, Kwangwoon University, Seoul 01897, Korea; [email protected] * Correspondence: [email protected] † This paper is an extended version of our paper published in the 2020 International Conference on Information Networking (ICOIN), Barcelona, Spain, 7–10 January 2020. Received: 30 April 2020; Accepted: 26 May 2020; Published: 29 May 2020 Abstract: Mail user agent (MUA) programs provide an integrated interface for email services. Many MUAs support email encryption functionality to ensure the confidentiality of emails. In practice, they encrypt the content of an email using email encryption standards such as OpenPGP or S/MIME, mostly implemented using GnuPG. Despite their widespread deployment, there has been insufficient research on their software structure and the security dependencies among the software components of MUA programs. In order to understand the security implications of the structures and analyze any possible vulnerabilities of MUA programs, we investigated a number of MUAs that support email encryption. As a result, we found severe vulnerabilities in a number of MUAs that allow cache side-channel attacks in virtualized desktop environments. Our analysis reveals that the root cause originates from the lack of verification and control over the third-party cryptographic libraries that they adopt. In order to demonstrate this, we implemented a cache side-channel attack on RSA in GnuPG and then conducted an evaluation of the vulnerability of 13 MUAs that support email encryption in Ubuntu 14.04, 16.04 and 18.04. -

Maplewood Weekly Events October 14-18, 2019
Maplewood Weekly Events October 14-18, 2019 MONDAY OCTOBER 14-WHITE 3:00PM MATH MEET @ MAPLEWOOD TUESDAY OCTOBER 15-BLUE 3:15-7:15PM PARENT/TEACHER CONFERENCES 4:30/5:45/7:00PM 6TH/7TH/8TH FB @ KIMBERLY WEDNESDAY OCTOBER 16-WHITE THURSDAY OCTOBER 17-BLUE FRIDAY OCTOBER 18-WHITE PICTURE RETAKE DAY Mark your Calendars!! Parent/Teacher Conferences Tuesday, October 15 3:15-7:15 For those new to Maplewood, the conferences are held in an arena-type setting. Sixth grade teachers will be in the community room. Seventh and eighth grade teachers will be in the large gym. There are no scheduled appointments. We hope that you are able to attend and meet your child’s teachers. GEMS Girls in Engineering, Math, and Science A half-day educational event for girls grades 6 through 8 featuring interactive GEMS-based workshops geared towards career exploration in engineering, math, and science Saturday, October 19 8:30 am – 12:00 pm Register today! Only $25 per student Call the Continuing Education Office at 920-832-2636 or go online to: https://ce.uwc.edu/menasha/catalog What’s the Buzz on Electric Vehicles?! Students will get to inspect and actively engage with the various components and mechanisms of an electric basic utility vehicle (frame, suspension, motor, transmission, steering, brakes, etc.). Students will also learn how to work with Unistrut to build frames and scaffolds for a variety of applications. Instructor: Warren Vaz, Assistant Professor of Engineering Water Beneath Our Feet Where does our water come from? How does it move? And what happens if it is polluted? Learn all about groundwater and how we use it with Dr. -

Bonanza Society
MAY 2021 • VOLUME TWENTY-ONE • NUMBER 5 AMERICAN BONANZA SOCIETY The Official Publication for Bonanza, Debonair, Baron & Travel Air Operators and Enthusiasts We’d Just Like to Say… Thanks Falcon Insurance and the American Bonanza Society For over 20 years, Falcon Insurance and the American Bonanza Society have worked together toward a common goal of promoting the safe enjoyment of all Beechcraft airplanes. Your Beechcraft. Nothing brings us greater joy than working with such enthusiastic owner-pilots and finding the best prices for your aviation needs, and knowing that in doing so, we are encouraging safe flying by supporting ABS’ development of new and improved flight safety training programs. And for that, we say thanks. Thanks for letting us be a part of the for single engine aircraft – to major airports – and everything in between American Bonanza Society and the Air Safety Foundation… and thanks for trusting us with your insurance needs. Barry Dowlen Henry Abdullah President Vice President & ABS Program Director If you’d like to learn how Falcon Insurance can help you, Falcon Insurance Agency please call 1-800-259-4ABS, or visit http:/falcon.villagepress is the Insurance Program Manager for the ABS Insurance Program .com/promo/signup to obtain your free quote. When you do, we’ll make a $5 donation to ABS’ Air Safety Foundation. Falcon2 Insurance Agency • P.O. Box 291388, Kerrville,AMERICAN TX BONANZA 78029 SOCIETY • www.falconinsurance.com • Phone: 1-800-259-4227May 2021 We’d Just Like to Say… CONTENTS May 2021 AMERICA N Thanks BONANZA SOCIETY 2 President's Comments: Cultivating Passion Falcon Insurance and the American Bonanza Society May 2021 • Volume 21 • Number 5 By Paul Lilly For over 20 years, Falcon Insurance and the American Bonanza Society ABS Executive Director J. -
EAI Readiness in Tlds
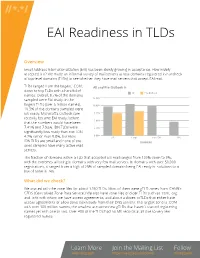
EAI Readiness in TLDs Overview Email Address Internationalization (EAI) has been slowly growing in acceptance. How widely accepted is it? We made an informal survey of mail servers across domains registered in hundreds of top-level domains (TLDs) to see whether they have mail servers that accept EAI mail. TLDs ranged from the largest, .COM, All and Pre-Outlook % down to tiny TLDs with a handful of All Pre-Outlook names. Overall, 9.7% of the domains sampled were EAI ready. In the 12.50% largest TLDs (over a million names), 10.00% 10.5% of the domains sampled were EAI ready. Microsoft’s Outlook.com 7.50% recently became EAI ready; before 5.00% that the numbers would have been 7.41% and 7.93%. IDN TLDs were 2.50% significantly less ready than non-IDN, 0.00% 4.7% rather than 9.8%, but most All Large non-IDN IDN IDN TLDs are small and none of the DOMAINS ones sampled have many active mail servers. The fraction of domains within a TLD that accepted EAI mail ranged from 100% down to 0%, with the extremes all being in domains with very few mail servers. In domains with over 50,000 registrations, it ranged from a high of 25% of sampled domains being EAI ready in .solutions to a low of none in .ren. What did we check? We started with the zone files for about 1250 TLDs. Most of them were gTLD zones from ICANN’s CZDS (Centralized Zone Data Service.) We also have zone files of older TLDs such as .com, .org, and .info with whom we have access agreements, and about a dozen ccTLDs that either have access agreements or allow zone downloads from their DNS servers. -

At Commands, Tor-Based Communications: Meet Attor, a Fantasy Creature and Also a Spy Platform
ESET Research white papers TLP: WHITE AT COMMANDS, TOR-BASED COMMUNICATIONS: MEET ATTOR, A FANTASY CREATURE AND ALSO A SPY PLATFORM Author: Zuzana Hromcová In the fantasy book “A Court of Thorns and Roses” by Sarah J. Maas, Attor was an evil Faerie. In that book, the Faeries ruled over all the known world and humans were their slaves. In cybersecurity, Attor is a cyberespionage platform designed to exfiltrate valuable information from its victims. Author: Zuzana Hromcová October 2019 1 AT commands, TOR-based communications: Meet Attor, a fantasy creature and also a spy platform TLP: WHITE CONTENTS 1 SUMMARY . 2 2 THE ESPIONAGE CAMPAIGN . 2 3 THE PLATFORM ARCHITECTURE . 4 3 .1 Persistence . 5 3 .2 Collection and exfiltration . 5 3 .3 Network communication . 5 4 TECHNICAL ANALYSIS . 7 4 .1 Dispatcher . 7 4 .1 .1 Encryption methods . 7 4 .1 .2 Evasion techniques . 7 4 .1 .3 Interface for plugins . 9 4 .2 Shared resources . 11 4 .2 .1 Plugin folder, Update folder . .11 4 .2 .2 Upload folder . 12 4 .2 .3 Resource folder . 13 4 .3 Plugins . 13 4 .3 .1 Device monitor (ID 0x01) . 15 4 .3 .2 Screengrabber (ID 0x02) . 18 4 .3 .3 Audio recorder (ID 0x03) . 19 4 .3 4. File uploader (ID 0x05) . 19 4 .3 .5 Command dispatcher/SOCKS proxy (ID 0x06) . 19 4 .3 6. Key/clipboard logger (ID 0x07) . 20 4 .3 .7 Tor client (ID 0x0D) . 20 4 .3 .8 Installer/watchdog (ID 0x10) . 21 5 CONCLUSION . 21 6 INDICATORS OF COMPROMISE (IOCS) . 21 7 MITRE ATT&CK TECHNIQUES .