Certification Report Netiq® Identity Manager 4.7
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Relevé Des Frais Annuels De L'entente De Licence Destinée À L
Relevé des frais annuels de l’entente de licence destinée à l’enseignement postsecondaire AOÛT 2016 Les Informations de Programme scolaire Relient Les Instructions de Sélection de produit : As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). Sélectionnez un seul modèle : ___ Modèle ETP; ___ Modèle par poste de travail; ___ Modèle par poste de travail de service EMBALLER CALCUL INSTRUCTIONS : A. Place une marque dans le Modèle de colonne A Choisi la boîte des produits que vous souhaitez acheter OU choisir un Paquet de Valeur. Si un Paquet de Valeur n'est pas choisi, au moins quatre (4) les produits doivent être choisis. B. Calcule le Total A Emballé le Prix (TBP) en ajoutant les prix appropriés des produits choisis et le modèle d'évaluation approprié. C. Le Total A Emballé le Prix sera utilisé pour calculer les Frais annuels. Vous ne pouvez pas utiliser le modèle de FTE dans calculer vos Frais annuels à moins que votre population de FTE dépasse votre compte de poste de travail. POUR EMPECHER DES RETARDS DANS TRAITER VOTRE ORDRE DE RENOUVELLEMENT, S'IL VOUS PLAIT SOUMETTRE VOTRE FACTURE D'ACHAT ET VOTRE FEUILLE DE TRAVAIL COMPLETEE ENSEMBLE MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your ALA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. -

OES 2015 SP1: Installation Guide Is Available at the Open Enterprise Server 2015 SP1 Documentation Website
Open Enterprise Server 2015 SP1 Installation Guide June 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent policy, and FIPS compliance, see https://www.novell.com/company/legal/. Copyright © 2016 Novell, Inc., a Micro Focus company. All Rights Reserved. Contents About This Guide 9 1 What’s New or Changed in the OES Install 11 1.1 What’s New (Update 28-OES 2015 SP1). .11 1.2 What’s New (OES 2015 SP1) . 11 1.3 What’s New (January 2016 eDirectory 8.8 SP8 Patch 6 Hot Patch 1). 12 1.4 What’s New (OES 2015) . 12 2 Preparing to Install OES 2015 SP1 15 2.1 Before You Install . 15 2.2 Meeting All Server Software and Hardware Requirements . 15 2.2.1 Server Software . 15 2.2.2 Server Hardware . 16 2.3 NetIQ eDirectory Rights Needed for Installing OES. 17 2.3.1 Rights to Install the First OES Server in a Tree . 17 2.3.2 Rights to Install the First Three Servers in an eDirectory Tree . 17 2.3.3 Rights to Install the First Three Servers in any eDirectory Partition . 17 2.4 Installing and Configuring OES as a Subcontainer Administrator . 17 2.4.1 Rights Required for Subcontainer Administrators . 18 2.4.2 Providing Required Rights to the Subcontainer Administrator for Installing and Managing Samba. 20 2.4.3 Starting a New Installation as a Subcontainer Administrator . 22 2.4.4 Adding/Configuring OES Services as a Different Administrator. -
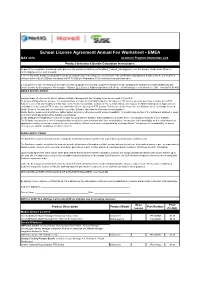
School License Agreement Annual Fee Worksheet - EMEA MAY 2016 Academic Program Information Link Product Selection & Bundle Calculation Instructions
School License Agreement Annual Fee Worksheet - EMEA MAY 2016 Academic Program Information Link Product Selection & Bundle Calculation Instructions: As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). 1. Select any of the bundles or products below by checking the box in the Model Selected column. Any combination of products or bundles may be selected for a minimum price of $2.36 USD per enrollment or $35.70 USD per Workstation. $1000 minimum total purchase price. 2. Compute the Total Price based on the total cost of the products selected and compute the Annual Fee by multiplying the total Enrollment/Workstation/Mobile Device number by the total price. For example: 1 Bundle @ 2.25 plus 2 Additional products ($0.60 ea) = $3.45 total price x enrollment of 1,000 = Annual Fee $3,450. MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your SLA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. Subject to the terms and conditions of this Agreement, the license purchase authorizes You to install and use one copy of the Mobile Management Application on each Mobile Device (for an FTE license, for each Mobile Device used by an FTE person). This license allows You to use the Software solely to manage licensed Mobile Devices. You may not use or allow the use of the Software other than for Your own internal purposes. -

Netiq Securelogin User Guide About This Guide
User Guide SecureLogin 8.0 October, 2013 Legal Notice NetIQ Product Name is protected by United States Patent No(s): nnnnnnnn, nnnnnnnn, nnnnnnnn. THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE AGREEMENT OR A NON‐DISCLOSURE AGREEMENT. EXCEPT AS EXPRESSLY SET FORTH IN SUCH LICENSE AGREEMENT OR NON‐DISCLOSURE AGREEMENT, NETIQ CORPORATION PROVIDES THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ʺAS ISʺ WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. SOME STATES DO NOT ALLOW DISCLAIMERS OF EXPRESS OR IMPLIED WARRANTIES IN CERTAIN TRANSACTIONS; THEREFORE, THIS STATEMENT MAY NOT APPLY TO YOU. For purposes of clarity, any module, adapter or other similar material (ʺModuleʺ) is licensed under the terms and conditions of the End User License Agreement for the applicable version of the NetIQ product or software to which it relates or interoperates with, and by accessing, copying or using a Module you agree to be bound by such terms. If you do not agree to the terms of the End User License Agreement you are not authorized to use, access or copy a Module and you must destroy all copies of the Module and contact NetIQ for further instructions. This document and the software described in this document may not be lent, sold, or given away without the prior written permission of NetIQ Corporation, except as otherwise permitted by law. Except as expressly set forth in such license agreement or non‐disclosure agreement, no part of this document or the software described in this document may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, or otherwise, without the prior written consent of NetIQ Corporation. -

Oes 2018 Sp2)
Open Enterprise Server 2018 SP2 Installation Guide August 2020 Legal Notices Copyright © 2017 - 2020 Micro Focus or one of its affiliates. The only warranties for products and services of Micro Focus and its affiliates and licensors (“Micro Focus”) are as may be set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. Micro Focus shall not be liable for technical or editorial errors or omissions contained herein. The information contained herein is subject to change without notice. Contents About This Guide 9 1 What’s New or Changed in the OES Install 11 1.1 What’s New or Changed (OES 2018 SP2) . .11 1.2 What’s New or Changed (OES 2018 SP1) . .11 1.3 What's New or Changed (Update 6 - OES 2018 - Recommended) . 12 1.4 What’s New or Changed (OES 2018) . 12 2 Preparing to Install OES 2018 SP2 13 2.1 Before You Install . 13 2.2 Meeting All Server Software and Hardware Requirements . 13 2.2.1 Server Software . 13 2.2.2 Server Hardware . 14 2.3 NetIQ eDirectory Rights Needed for Installing OES. .15 2.3.1 Rights to Install the First OES Server in a Tree . 15 2.3.2 Rights to Install the First Three Servers in an eDirectory Tree . 15 2.3.3 Rights to Install the First Three Servers in any eDirectory Partition . 15 2.4 Installing and Configuring OES as a Subcontainer Administrator . 15 2.4.1 Rights Required for Subcontainer Administrators . 16 2.4.2 Providing Required Rights to the Subcontainer Administrator for Installing and Managing Samba. -

Novell Zenworks Mobile Management Datasheet
Data Sheet Endpoint Management Novell ZENworks Mobile Management Extend your endpoint management to all the mobile devices in your IT environment from a single administrative console. Protect yourself from risk with security policies and manage both employee-owned and company-owned devices. Product Overview If you answered yes to any of these questions, System Requirements Novell® ZENworks® Mobile Management pro- you already know how valuable ZENworks Please visit www.novell.com/zmm for detailed vides advanced device controls and policy Mo bile Management can be: It meets all of product specifications and system requirements. management for iOS and Android, and other these management challenges and many Ac tiveSync -enabled devices—all from a sin- more. track device use and the applications gle administrative console. The product ad- that users download onto their devices. dresses all of the pain points administrators Key Benefits BYOD support that helps you optimize and managers face to day, including bring- Novell ZENworks Mobile Management helps user productivity on a variety of device your-own-device policies (BYOD), security, your organization with: platforms—including iOS and Android, application management, asset and inventory and most other ActiveSync devices. management and compliance issues. Centralized management tools Security and compliance capabilities that make it easy to deploy new mobile that provide auditing and compliance Are your users bringing in their own iPads, devices in the workforce, whether the management tools so you know who is Androids and other devices, then asking devices are company issued or privately controlling what and how they are doing it. for access to corporate email? owned. -

School License Agreement Annual Fee Worksheet - USD DECEMBER 2017 Academic Program Information Link
School License Agreement Annual Fee Worksheet - USD DECEMBER 2017 Academic Program Information Link Product Selection & Bundle Calculation Instructions: As part of the compliance and annual order process, this worksheet must be sent to EMEA_Contract_Admin@Micro Focus.com (for Europe, Middle East, Africa) or contractadmin@Micro Focus.com (rest of world). 1. Select any of the bundles or products below by checking the box in the Model Selected column. Any combination of products or bundles may be selected for a minimum price of $2.50 USD per enrollment or $38.00 USD per Workstation. $1000 minimum total purchase price. 2. Compute the Total Price based on the total cost of the products selected and compute the Annual Fee by multiplying the total Enrollment/Workstation/Mobile Device number by the total price. For example: 1 Bundle @ 2.50 plus 2 Additional products ($0.60 ea) = $3.70 total price x enrollment of 1,000 = Annual Fee $3,700. MOBILE DEVICE LICENSE: Upon purchase of a license for ZENworks Mobile Management, the following terms become part of Your SLA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. Subject to the terms and conditions of this Agreement, the license purchase authorizes You to install and use one copy of the Mobile Management Application on each Mobile Device (for an FTE license, for each Mobile Device used by an FTE person). This license allows You to use the Software solely to manage licensed Mobile Devices. -

Hacking for Dummies.Pdf
01 55784X FM.qxd 3/29/04 4:16 PM Page i Hacking FOR DUMmIES‰ by Kevin Beaver Foreword by Stuart McClure 01 55784X FM.qxd 3/29/04 4:16 PM Page v 01 55784X FM.qxd 3/29/04 4:16 PM Page i Hacking FOR DUMmIES‰ by Kevin Beaver Foreword by Stuart McClure 01 55784X FM.qxd 3/29/04 4:16 PM Page ii Hacking For Dummies® Published by Wiley Publishing, Inc. 111 River Street Hoboken, NJ 07030-5774 Copyright © 2004 by Wiley Publishing, Inc., Indianapolis, Indiana Published by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permis- sion of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4447, e-mail: permcoordinator@ wiley.com. Trademarks: Wiley, the Wiley Publishing logo, For Dummies, the Dummies Man logo, A Reference for the Rest of Us!, The Dummies Way, Dummies Daily, The Fun and Easy Way, Dummies.com, and related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc. -

School District U-46 Job Description Information Services Department
SCHOOL DISTRICT U-46 JOB DESCRIPTION INFORMATION SERVICES DEPARTMENT SYSTEMS ENGINEER JOB DESCRIPTION REVISION DATE: 8/21/2015 POSITION TITLE: Systems Engineer DEPARTMENT: Information Services REPORTS TO: Director of Information Services SUPERVISES: None POSITION GOAL: Implement, troubleshoot, analyze and maintain the information technology infrastructure environment; including network switching, routing, connectivity, wireless, network security, firewalls, Windows server administration, Linux server administration, server virtualization, enterprise Storage Area Network (SAN), data backup/restore, Windows desktop imaging, and Windows desktop management. Identify, research and resolve technical problems. Familiar with a variety of the technology networking and infrastructure concepts, practices, and procedures. Rely on experience and judgment to plan and accomplish goals. Perform a variety of complicated information technology tasks, and provides support for escalated trouble tickets. ESSENTIAL FUNCTIONS: 1. Respond and resolve departmental requests and reports of exceptions regarding information technology infrastructure in a professional, timely, and efficient manner. 2. Take ownership of infrastructure issues, applying best practices, internal tools, and advanced techniques, exhausting all available resources to resolve before escalation. 3. Capture accurate, succinct information regarding issues as they occur, using the District’s Help Desk system to enhance management processes. 4. Facilitate communications about changes within the -

Micro Focus Story Is Part
THE 40-YEAR MICRO FOCUS STORY IS PART Sure, as with any good storytelling it might have been embellished a bit here and there along the way, but there’s no doubt that it’s a chronicle of great success, continual challenges and dogged determination; of breathless chutzpah and calculated risks. And studded throughout the chapters are the colourful characters who give it flair, nuance and depth. In other words, a very entertaining read. 2 HISTORY, PART LEGEND, PART TALE Few people were more colourful than founder and original the foundations that have made Micro Focus what it is today. CEO, Brian Reynolds. Brian opened the doors (of a lean-to None of them could have contemplated the journey that lay office alongside his house in Notting Hill, England) to the ahead of Micro Focus, in all its many manifestations. inaugural incarnation of Micro Focus on 12 August 1976, to deliver what were then the first ever business-ready, Today, Micro Focus spans more than 90 offices across off-mainframe COBOL compilers and run-time technologies 39 countries. We have over 4,500 employees, more to be based purely on COBOL. Later that year, co-founders than 20,000 customers and 5,000 partners. Our market Paul O’Grady (Managing Director) and Stewart Lang capitalisation is over £5 billion, and we rank in the Top 15 (Technical Director) joined him, and they began building of Worldwide System Infrastructure Software Vendors. Oh, yes and we’re still telling stories. But how does the rest of this one go? 3 THE EARLY YEARS In this year, Micro Focus landed its first original equipment manufacturer (OEM) contract. -

Relevé Des Frais Annuels De L'entente De Licence Destinée À
Relevé des frais annuels de l’entente de licence destinée à l’enseignement primaire et secondaire AOÛT 2016 Les Informations de Programme scolaire Relient DIRECTIVES SUR LA SÉLECTION DE PRODUIT ET LE CALCUL POUR LA SOLUTION GROUPÉE : As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). 1. Sélectionnez l'une des solutions regroupées ou produits ci-dessous et cochez la case appropriée. Vous pouvez choisir toute combinaison de produits ou de solutions regroupées pour un prix minimal de 2,80 $ par inscription ou de 42 $ par poste de travail. 2. Calculez le prix total en fonction du prix total des produits choisis et calculez les frais annuels en multipliant le nombre d'inscriptions/postes de travail par le prix total. Par exemple : solution 1 au prix de 2,60 $ plus 2 produits additionnels (0,69 $ chaque) = un prix total de 3,98 $ x 1 000 inscriptions = frais annuels de 3 980 $. MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your SLA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. Subject to the terms and conditions of this Agreement, the license purchase authorizes You to install and use one copy of the Mobile Management Application on each Mobile Device (for an FTE license, for each Mobile Device used by an FTE person). -

Netiq Imanager Installation Guide
NetIQ® iManager Installation Guide December 2014 Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE AGREEMENT OR A NON-DISCLOSURE AGREEMENT. EXCEPT AS EXPRESSLY SET FORTH IN SUCH LICENSE AGREEMENT OR NON-DISCLOSURE AGREEMENT, NETIQ CORPORATION PROVIDES THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. SOME STATES DO NOT ALLOW DISCLAIMERS OF EXPRESS OR IMPLIED WARRANTIES IN CERTAIN TRANSACTIONS; THEREFORE, THIS STATEMENT MAY NOT APPLY TO YOU. For purposes of clarity, any module, adapter or other similar material ("Module") is licensed under the terms and conditions of the End User License Agreement for the applicable version of the NetIQ product or software to which it relates or interoperates with, and by accessing, copying or using a Module you agree to be bound by such terms. If you do not agree to the terms of the End User License Agreement you are not authorized to use, access or copy a Module and you must destroy all copies of the Module and contact NetIQ for further instructions. This document and the software described in this document may not be lent, sold, or given away without the prior written permission of NetIQ Corporation, except as otherwise permitted by law. Except as expressly set forth in such license agreement or non-disclosure agreement, no part of this document or the software described in this document may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, or otherwise, without the prior written consent of NetIQ Corporation.