Oes 2018 Sp2)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PROYECTO FIN DE CARRERA Auditoría De Los Sistemas Y
Escuela Politécnica Superior Departamento de Informática PROYECTO FIN DE CARRERA Ingeniería Técnica en Informática de Gestión Auditoría de los sistemas y la seguridad en entornos mixtos (Linux - Windows) Autor: Roberto Garrido Pelaz Tutor: Miguel Ángel Ramos González Leganés, Noviembre de 2014 ii Título: Auditoría de los sistemas y la seguridad en entornos mixtos (Linux - Windows) Autor: Roberto Garrido Pelaz Tutor: Miguel Ángel Ramos González EL TRIBUNAL Presidente: ___________________________________ Vocal: ______________________________________ Secretario: ___________________________________ Realizado el acto de defensa y lectura del Proyecto Fin de Carrera el día __ de ___________ de 2014 en Leganés, en la Escuela Politécnica Superior de la Universidad Carlos III de Madrid, acuerda otorgarle la CALIFICACIÓN de __________________. VOCAL SECRETARIO PRESIDENTE Agradecimientos Roberto Garrido Pelaz i A Rebeca, porque das sentido a mi vida. Gracias a Miguel y Carmen, mis padres, por vuestro trabajo de toda una vida, por haberme enseñado el valor del esfuerzo y el trabajo. También gracias a mi hermano Miguel, por servirme de inspiración para seguir mejorando. A mi tutor Miguel Ángel Ramos, por tu experiencia, por tu apoyo y paciencia. Gracias a todos los que habéis contribuido a mi crecimiento personal y profesional durante estos años. Y a la música, por acompañarme durante todos mis caminos andados. Roberto Garrido Pelaz ii Resumen Los sistemas de información son ya activos estratégicos para cualquier organización, y la ventaja actual reside en el gran número de alternativas para las organizaciones en cuanto a tecnologías de la información. Nos encontramos con entornos cada vez más heterogéneos y modelos más flexibles, con los que se intenta alcanzar una ventaja competitiva a todos los niveles, y donde es fundamental el uso de ciertos protocolos y estándares tecnológicos. -

General Specs Copying Connectivity
General Specs Part no. 27X0128 Packaged Size (mm - H x 24 x 178 x 191 mm W x D) Packaged Weight, kg 0.099 kg Copying Network Type IEEE 802.11 b/g/n Wireless SISO 1x1 Connectivity Network Type IEEE 802.11 b/g/n Wireless SISO 1x1 Connectors One USB port (Type B) for Configuration Network Protocol Support TCP/IP IPv6, TCP/IP IPv4, AppleTalk™, TCP, UDP Network Printing Methods LPR/LPD, Function may vary by printer or MFP., Direct IP (Port 9100), HTTP, Telnet, FTP, TFTP, Enhanced IP (Port 9400), ThinPrint .print integration, IPP 1.0, 1.1, 2.0 (Internet Printing Protocol) Network Management DHCP, APIPA (AutoIP), BOOTP, RARP, mDNS, IGMP, SLPv1, Bonjour, WINS, DDNS, SNMPv3, Function may Protocols vary by printer or MFP., SNMPv2c, Telnet, NTP, ICMP, DNS, ARP, HTTPs (SSL1 /TLS), Finger Network Security IPSec, SNMPv3, 802.1x Authentication: MD5, MSCHAPv2, LEAP, PEAP, TLS, TTLS Wireless Network WEP Encryption (64- and 128-bit key), 1x1 802.11i b/g/n 72Mbps, WPA2™ - Enterprise with Certificate Management, WPA2™ - Personal Supported Operating Systems Microsoft Windows Windows Server 2008 x64 running Terminal Services, Windows Server 2008 x64, Windows Server 2008 running Operating Systems Terminal Services, Windows 8.1, Windows Server 2008 R2 Supported running Terminal Services, Windows 8, Windows Server 2008, Windows Server 2008 R2, Windows 8 x64, Windows 7 x64, Windows Server 2012, Windows RT 8.1, Windows XP x64, Windows Server 2003 x64, Windows RT, Windows Server 2003, Windows Server 2012 R2, Windows XP, Windows Server 2003 x64 running -

IBM Power Systems Private Cloud Solution Is Enhanced to Support Selected SUSE Linux Enterprise Server Subscriptions As Shared Utility Capacity Resources
IBM United States Hardware Announcement 121-045, dated April 20, 2021 IBM Power Systems Private Cloud Solution is enhanced to support selected SUSE Linux Enterprise Server subscriptions as Shared Utility Capacity resources Table of contents 1 Overview 1 Description 1 Key requirements 2 Order now 1 Effective date Overview The IBM(R) Power(R) Systems Private Cloud Solution with Shared Utility Capacity was initially launched with support to share Base processor and memory hardware resources, as well as AIX(R) and IBM i license entitlements, across a collection of similar Power servers in an enterprise. Now, selected SUSE Linux(R) Enterprise Server (SLES) subscription offerings will be supported as Base and Metered Capacity resources within an IBM Power Enterprise Pool (2.0) of IBM Power System E980 or E950 servers. Key requirements • For Linux metering, HMC 950 is required. Effective date April 30, 2021 Description SUSE Linux Enterprise Server subscription offerings will now be monitored, shared as Base Capacity, and made available as pay-per-use Metered Capacity resources when a Power Enterprise Pool (2.0) consisting of Power E980 or Power E950 systems is started: 5639-15S 5639-12S SUSE Linux Enterprise Server for Power with Base 1 - 2 Socket, Unlimited LPAR and Priority Subscription or Priority Subscription/Support features 5639-SAP SUSE Linux Enterprise Server for SAP Applications for Power with 1 - 2 Socket, Unlimited LPAR and Priority Subscription or Priority Subscription/Support features Base Capacity resources may be shared across systems within a pool. SLES Base subscription entitlement for each system will be set to the number of cores available in the quantity of sockets entitled by the current, valid subscription for that system IBM United States Hardware Announcement 121-045 IBM is a registered trademark of International Business Machines Corporation 1 (the number of cores per chip multiplied by the quantity of sockets acquired in the current subscription). -

Micro Focus File Reporter 3.6 Installation Guide
Micro Focus File Reporter 3.6 Installation Guide January 6, 2020 Legal Notices Condrey Corporation makes no representations or warranties with respect to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Condrey Corporation reserves the right to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. Further, Condrey Corporation makes no representations or warranties with respect to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Condrey Corporation reserves the right to make changes to any and all parts of the software at any time, without obligation to notify any person or entity of such revisions or changes. See the Software EULA for full license and warranty information with regard to the Software. Any products or technical information provided under this Agreement may be subject to U.S. export controls and the trade laws of other countries. You agree to comply with all export control regulations and to obtain any required licenses or classification to export, re-export, or import deliverables. You agree not to export or re-export to entities on the current U.S. export exclusion lists or to any embargoed or terrorist countries as specified in the U.S. export laws. You agree to not use deliverables for prohibited nuclear, missile, or chemical biological weaponry end uses. Condrey Corporation assumes no responsibility for your failure to obtain any necessary export approvals. -

Netbackup ™ Enterprise Server and Server 8.0 - 8.X.X OS Software Compatibility List Created on September 08, 2021
Veritas NetBackup ™ Enterprise Server and Server 8.0 - 8.x.x OS Software Compatibility List Created on September 08, 2021 Click here for the HTML version of this document. <https://download.veritas.com/resources/content/live/OSVC/100046000/100046611/en_US/nbu_80_scl.html> Copyright © 2021 Veritas Technologies LLC. All rights reserved. Veritas, the Veritas Logo, and NetBackup are trademarks or registered trademarks of Veritas Technologies LLC in the U.S. and other countries. Other names may be trademarks of their respective owners. Veritas NetBackup ™ Enterprise Server and Server 8.0 - 8.x.x OS Software Compatibility List 2021-09-08 Introduction This Software Compatibility List (SCL) document contains information for Veritas NetBackup 8.0 through 8.x.x. It covers NetBackup Server (which includes Enterprise Server and Server), Client, Bare Metal Restore (BMR), Clustered Master Server Compatibility and Storage Stacks, Deduplication, File System Compatibility, NetBackup OpsCenter, NetBackup Access Control (NBAC), SAN Media Server/SAN Client/FT Media Server, Virtual System Compatibility and NetBackup Self Service Support. It is divided into bookmarks on the left that can be expanded. IPV6 and Dual Stack environments are supported from NetBackup 8.1.1 onwards with few limitations, refer technote for additional information <http://www.veritas.com/docs/100041420> For information about certain NetBackup features, functionality, 3rd-party product integration, Veritas product integration, applications, databases, and OS platforms that Veritas intends to replace with newer and improved functionality, or in some cases, discontinue without replacement, please see the widget titled "NetBackup Future Platform and Feature Plans" at <https://sort.veritas.com/netbackup> Reference Article <https://www.veritas.com/docs/100040093> for links to all other NetBackup compatibility lists. -

Relevé Des Frais Annuels De L'entente De Licence Destinée À L
Relevé des frais annuels de l’entente de licence destinée à l’enseignement postsecondaire AOÛT 2016 Les Informations de Programme scolaire Relient Les Instructions de Sélection de produit : As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). Sélectionnez un seul modèle : ___ Modèle ETP; ___ Modèle par poste de travail; ___ Modèle par poste de travail de service EMBALLER CALCUL INSTRUCTIONS : A. Place une marque dans le Modèle de colonne A Choisi la boîte des produits que vous souhaitez acheter OU choisir un Paquet de Valeur. Si un Paquet de Valeur n'est pas choisi, au moins quatre (4) les produits doivent être choisis. B. Calcule le Total A Emballé le Prix (TBP) en ajoutant les prix appropriés des produits choisis et le modèle d'évaluation approprié. C. Le Total A Emballé le Prix sera utilisé pour calculer les Frais annuels. Vous ne pouvez pas utiliser le modèle de FTE dans calculer vos Frais annuels à moins que votre population de FTE dépasse votre compte de poste de travail. POUR EMPECHER DES RETARDS DANS TRAITER VOTRE ORDRE DE RENOUVELLEMENT, S'IL VOUS PLAIT SOUMETTRE VOTRE FACTURE D'ACHAT ET VOTRE FEUILLE DE TRAVAIL COMPLETEE ENSEMBLE MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your ALA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. -

OES 2015 SP1: Installation Guide Is Available at the Open Enterprise Server 2015 SP1 Documentation Website
Open Enterprise Server 2015 SP1 Installation Guide June 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent policy, and FIPS compliance, see https://www.novell.com/company/legal/. Copyright © 2016 Novell, Inc., a Micro Focus company. All Rights Reserved. Contents About This Guide 9 1 What’s New or Changed in the OES Install 11 1.1 What’s New (Update 28-OES 2015 SP1). .11 1.2 What’s New (OES 2015 SP1) . 11 1.3 What’s New (January 2016 eDirectory 8.8 SP8 Patch 6 Hot Patch 1). 12 1.4 What’s New (OES 2015) . 12 2 Preparing to Install OES 2015 SP1 15 2.1 Before You Install . 15 2.2 Meeting All Server Software and Hardware Requirements . 15 2.2.1 Server Software . 15 2.2.2 Server Hardware . 16 2.3 NetIQ eDirectory Rights Needed for Installing OES. 17 2.3.1 Rights to Install the First OES Server in a Tree . 17 2.3.2 Rights to Install the First Three Servers in an eDirectory Tree . 17 2.3.3 Rights to Install the First Three Servers in any eDirectory Partition . 17 2.4 Installing and Configuring OES as a Subcontainer Administrator . 17 2.4.1 Rights Required for Subcontainer Administrators . 18 2.4.2 Providing Required Rights to the Subcontainer Administrator for Installing and Managing Samba. 20 2.4.3 Starting a New Installation as a Subcontainer Administrator . 22 2.4.4 Adding/Configuring OES Services as a Different Administrator. -

NSS File System Administration Guide for Linux Is Available on the OES Documentation Website
Open Enterprise Server 11 SP3 Novell Storage ServicesTM File System Administration Guide for Linux July 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent policy, and FIPS compliance, see https://www.novell.com/company/legal/. Copyright © 2016 Novell, Inc. All Rights Reserved. Contents About This Guide 19 1 Overview of NSS 23 1.1 Introduction to NSS . 23 1.2 Benefits of NSS . 23 1.3 Understanding NSS . 24 1.3.1 Storage Pools . 24 1.3.2 NSS Volumes. 25 1.4 NSS Features and Capabilities . 25 1.4.1 Use Less Memory and Gain More Speed . 26 1.4.2 Improve Storage Availability. 26 1.4.3 Prevent Unauthorized Access . 26 1.4.4 Protect Data from Corruption or Loss . 27 1.4.5 Maximize Available Space . .27 1.5 Comparison of NSS to Other File Systems . 28 1.6 What’s Next . 28 2 What’s New or Changed in NSS 29 2.1 What’s New or Changed in NSS (May 2017 Patch). 29 2.2 What’s New or Changed in NSS (September 2016 Patch) . 29 2.3 What’s New or Changed in NSS (OES 11 SP3). 29 2.4 What’s New or Changed in NSS (OES 11 SP2). 30 2.5 What’s New or Changed in NSS (OES 11 SP1). 30 2.6 What’s New or Changed in NSS (OES 11) . .31 3 Installing and Configuring Novell Storage Services 33 3.1 Requirements for Installing NSS . 33 3.1.1 Device Requirements . -

Android Apps for Absolute Beginners
Android Apps for Absolute Beginners ■ ■ ■ Wallace Jackson i Android Apps For Absolute Beginners Copyright © 2011 by Wallace Jackson All rights reserved. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage or retrieval system, without the prior written permission of the copyright owner and the publisher. ISBN 978-1-4302-3446-3 ISBN 978-1-4302-3447-0 (eBook) Printed and bound in the United States of America (POD) Trademarked names, logos, and images may appear in this book. Rather than use a trademark symbol with every occurrence of a trademarked name, logo, or image we use the names, logos, and images only in an editorial fashion and to the benefit of the trademark owner, with no intention of infringement of the trademark. The use in this publication of trade names, trademarks, service marks, and similar terms, even if they are not identified as such, is not to be taken as an expression of opinion as to whether or not they are subject to proprietary rights. President and Publisher: Paul Manning Lead Editor: Matthew Moodie Technical Reviewer: Kunal Mittal Editorial Board: Steve Anglin, Mark Beckner, Ewan Buckingham, Gary Cornell, Jonathan Gennick, Jonathan Hassell, Michelle Lowman, Matthew Moodie, Jeff Olson, Jeffrey Pepper, Frank Pohlmann, Douglas Pundick, Ben Renow-Clarke, Dominic Shakeshaft, Matt Wade, Tom Welsh Coordinating Editor: Corbin Collins Copy Editors: Marilyn Smith, Sharon Terdeman, Tracy Brown Compositor: MacPS, LLC Indexer: BIM Indexing & Proofreading Services Artist: April Milne Cover Designer: Anna Ishchenko Distributed to the book trade worldwide by Springer Science+Business Media, LLC., 233 Spring Street, 6th Floor, New York, NY 10013. -
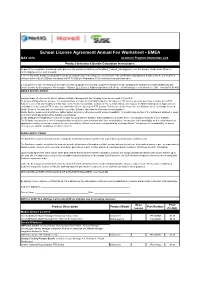
School License Agreement Annual Fee Worksheet - EMEA MAY 2016 Academic Program Information Link Product Selection & Bundle Calculation Instructions
School License Agreement Annual Fee Worksheet - EMEA MAY 2016 Academic Program Information Link Product Selection & Bundle Calculation Instructions: As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). 1. Select any of the bundles or products below by checking the box in the Model Selected column. Any combination of products or bundles may be selected for a minimum price of $2.36 USD per enrollment or $35.70 USD per Workstation. $1000 minimum total purchase price. 2. Compute the Total Price based on the total cost of the products selected and compute the Annual Fee by multiplying the total Enrollment/Workstation/Mobile Device number by the total price. For example: 1 Bundle @ 2.25 plus 2 Additional products ($0.60 ea) = $3.45 total price x enrollment of 1,000 = Annual Fee $3,450. MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your SLA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. Subject to the terms and conditions of this Agreement, the license purchase authorizes You to install and use one copy of the Mobile Management Application on each Mobile Device (for an FTE license, for each Mobile Device used by an FTE person). This license allows You to use the Software solely to manage licensed Mobile Devices. You may not use or allow the use of the Software other than for Your own internal purposes. -
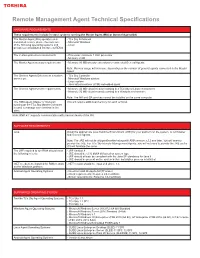
Remote Management Agent Technical Specifications
Remote Management Agent Technical Specifications HARDWARE REQUIREMENTS These requirements include in-store systems running the Master Agent (MA) or General Agent (GA) The Master Agent (MA) operates on a - TCx Sky Enhanced nominated in store device that runs one - Microsoft Windows of the following operating systems and - Linux provides a consolidated interface to REMS The in-store processor requirements - Processor: minimum 1 GHz processor - Memory: 2 GB The Master Agent memory requirements - Memory: 80 MB w/o any extensions or connected General Agents Note: Memory usage will increase, depending on the number of general agents connected to the Master Agent. The General Agent (GA) runs as a system - TCx Sky Controller service on: - Microsoft Windows system - Linux system - Java virtual machine (JVM) embedded agent The General Agent service requirements - Memory: 40 MB virtual memory running in a TCx Sky or Linux environment - Memory: 70 MB virtual memory running in a Windows environment Note: The MA and GA services cannot be installed on the same computer. The RMA agent (Master or General) This will require additional memory for each terminal. running on the TCx Sky Master Controller is used to manage each terminal in the store. Note: RMA 4.1 supports communication with previous levels of the GA. SOFTWARE REQUIREMENTS Java Install the appropriate Java Runtime Environment (JRE) for your platform on the system, to run Master and General Agents. Note: The JRE will not be shipped/bundled along with RMA version 3.2.2 and later. You will need to provide the JRE. For TCx Sky Remote Management Agents, you will not need to provide the JRE as the OS will facilitate the same. -

Netiq Edirectory Installation Guide, See the Netiq Edirectory Online Documentation Web Site
NetIQ® eDirectory™ Installation Guide February 2018 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent policy, and FIPS compliance, see https://www.netiq.com/company/legal/. Copyright © 2018 NetIQ Corporation, a Micro Focus company. All Rights Reserved. Contents About this Book and the Library 7 About NetIQ Corporation 9 1 Install and Upgrade Features 11 Multiple Package Formats for Installing eDirectory 9.1. 11 Installing eDirectory 9.1 in a Custom Location . 12 Specifying a Custom Location for Application Files . 12 Specifying a Custom Location for Data Files . 13 Specifying a Custom Location for Configuration Files . 13 Non-root Install . 14 Standards Compliance . 14 FHS Compliance . 14 LSB Compliance . 15 Server Health Checks . 15 Need for Health Checks . 15 What Makes a Server Healthy? . 16 Performing Health Checks . 16 Types of Health Checks . 17 Categorization of Health. 17 Log Files. 18 SecretStore Integration with eDirectory . 19 eDirectory Instrumentation Installation . 20 For More Information . 20 2 Installing or Upgrading NetIQ eDirectory on Linux 21 System Requirements. 21 Prerequisites . 23 Hardware Requirements . 25 Forcing the Backlink Process to Run . 25 Upgrading eDirectory . 26 Server Health Checks . 26 Upgrading on Linux Servers Other Than OES. 27 Unattended Upgrade of eDirectory on Linux . .27 Upgrading the Tarball Deployment of eDirectory 9.1 . 28 Upgrading Multiple Instances. 29 Installing eDirectory . 30 Using SLP with eDirectory . 30 Using the nds-install Utility to Install eDirectory Components . 31 Non-root User Installing eDirectory 9.1 . 34 Using the ndsconfig Utility to Add or Remove the eDirectory Replica Server .