TCPA’S Business Objectives
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Paypal's Security
PayPal’s Security Key PayPal is a great service for enabling both businesses and consumers to buy and sell goods and services online without exposing private financial information to the other parties in a transaction. As a consumer, you can safely purchase goods and services online without exposing your credit or debit card information to be recorded and possibly misused. As a business, you can be paid for your goods or services using the Web or email without the need of storing your customer’s private financial information. A big concern with PayPal is that anyone who knows the password of your PayPal account can access the financial services that you have authorized to be used with PayPal. For consumers, this means that unauthorized purchases or cash transfer may be performed from your credit cards and bank accounts. As a business, unauthorized PayPal access can be a source of fraudulent purchases. Password security is always the responsibility of the PayPal account holder; but now PayPal has a service to make the disclosure of your PayPal password an almost insignificant threat. In February 2007, PayPal introduced an optional security key system for users to access their PayPal accounts. The security key does not replace your PayPal password; instead, it adds an extra layer of security by requiring an additional security code be entered with your password when you log into your PayPal account. What makes this security code so different from a password is that it randomly generated by a small, electronic device called a security token, which is a key fob that easily fits in the palm of your hand. -

A Project Report on ³INVENTORY MANAGEMENT´
A Project Report on ³INVENTORY MANAGEMENT´ SUBMITTED BY: Mujif Rahuman M. 520828621 Operations Management Submitted in fulfillment of the requirement of IVth Semester of MBA course, Sikkim Manipal University 1 Table of Contents INTRODUCTION INVENTORY MANAGEMENT««««««««2 SIEMENS«««««««««««««««««««««.........8 OBJECTIVES AND NEED OF SUPPLY CHAIN MANAGEMENT..16 ACTIVITIES/FUNCTIONS OF SCM IN SIEMENS«««««.20 INVENTORY CONTROL MANAGEMENT««««««««25 WAREHOUSE««««««««««««««««««««..43 TRANSPORTATION««««««««««««««««.«.45 DISTRIBUTION«««««««««««««««««««..48 PACKAGING AND LABELLING««««««««««««.53 CONCLUSION««««««««««««««««««««.59 2 INVENTORY MANAGEMENT 1. INTRODUCTION DEFINATION AND MEANING Inventory is a list of goods and materials, or those goods and materials themselves, held available in stock by a business. Inventory are held in order to manage and hide from the customer the fact that manufacture/supply delay is longer than delivery delay, and also to ease the effect of imperfections in the manufacturing process that lower production efficiencies if production capacity stands idle for lack of materials. The reasons for keeping stock All these stock reasons can apply to any owner or product stage. Buffer stock is held in individual workstations against the possibility that the upstream workstation may be a little delayed in providing the next item for processing. Whilst some processes carry very large buffer stocks, Toyota moved to one (or a few items) and has now moved to eliminate this stock type. Safety stock is held against process or machine failure in the hope/belief that the failure can be repaired before the stock runs out. This type of stock can be eliminated by programmes like Total Productive Maintenance Overproduction is held because the forecast and the actual sales did not match. -

Report on the Completed Acquisition of Wincor Nixdorf AG by Diebold, Incorporated
Diebold and Wincor A report on the completed acquisition of Wincor Nixdorf AG by Diebold, Incorporated 16 March 2017 © Crown copyright 2017 You may reuse this information (not including logos) free of charge in any format or medium, under the terms of the Open Government Licence. To view this licence, visit www.nationalarchives.gov.uk/doc/open-government- licence/ or write to the Information Policy Team, The National Archives, Kew, London TW9 4DU, or email: [email protected]. Website: www.gov.uk/cma Members of the Competition and Markets Authority who conducted this inquiry Martin Cave (Chair of the Group) Sarah Chambers Roger Finbow Robert Spedding Acting Chief Executive of the Competition and Markets Authority Andrea Coscelli The Competition and Markets Authority has excluded from this published version of the report information which the Inquiry Group considers should be excluded having regard to the three considerations set out in section 244 of the Enterprise Act 2002 (specified information: considerations relevant to disclosure). The omissions are indicated by []. Some numbers have been replaced by a range. These are shown in square brackets. Non-sensitive wording is also indicated in square brackets. Contents Page Summary .................................................................................................................... 3 Findings .................................................................................................................... 10 1. The reference .................................................................................................... -

Zoom Go Boom!
Security Now! Transcript of Episode #761 Page 1 of 21 Transcript of Episode #761 Zoom Go Boom! Description: This week starts off with a bunch of web browser news including Firefox zero-days, Safari's recent scrape, more coronavirus-related feature rollbacks, the status of TLS v1.0 and 1.1, and some interesting developments on the Edge front. We revisit the lingering STIR and SHAKEN telco protocol mess, then look at a new DNS-filtering add-on service from Cloudflare and at the growing influence of an Internet group hoping to tighten up the mess with BGP. After a quick update on my SpinRite project, we take a look at what's been going on with the security of Zoom, the suddenly chosen tool for hosting Internet virtual classrooms and meetings of all kinds. High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-761.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-761-lq.mp3 SHOW TEASE: It's time for Security Now!. Steve Gibson is here. Lots to talk about including a Mozilla Firefox zero-day. It's been fixed, but just barely. A problem with Safari. BGP gets some MANRS. And what's wrong with Zoom, and a pretty good alternative. It's all coming up next on Security Now!. Leo Laporte: This is Security Now! with Steve Gibson, Episode 761, recorded Tuesday, April 7th, 2020: Zoom Go Boom! It's time for Security Now!, the show where we cover your security and privacy and safety and quarantine online. -
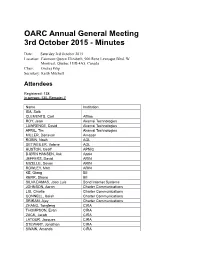
2015 AGM Minutes
OARC Annual General Meeting 3rd October 2015 - Minutes Date: Saturday 3rd October 2015 Location: Fairmont Queen Elizabeth, 900 Rene Levesque Blvd. W Montreal, Quebec H3B 4A5, Canada Chair: Ondrej Filip Secretary: Keith Mitchell Attendees Registered: 138 In person: 130, Remote: 7 Name Institution ISA, Saib CLEMENTS, Carl Afilias ROY, Jean Akamai Technologies LAWRENCE, David Akamai Technologies APRIL, Tim Akamai Technologies MILLER, Donavan Amazon ROBIN, Noah AOL DETWEILER, Valerie AOL HUSTON, Geoff APNIC BJØRN HANSEN, Ask Apple JEFFERS, David ARIN MIZELLE, Devon ARIN ROWLEY, Matt ARIN KE, Qiang BII KERR, Shane BII SILVA DAMAS, Joao Luis Bond Internet Systems JOHNSON, Aaron Charter Communications LIU, Charlie Charter Communications CONNELL, Isaiah Charter Communications SRIRAM, Ajay Charter Communications ZHANG, Tongfeng CIRA THOMPSON, Evan CIRA ZACK, Jacob CIRA LATOUR, Jacques CIRA STEWART, Jonathan CIRA SWAIN, Amanda CIRA MALENFANT, Eric CIRA CHANTIGNY, Rock CIRA BOOS, Roy Cisco Systems KWONG, David Cisco Systems VALSORDA, Filippo Cloudflare GUÐMUNDSSON, Ólafur CloudFlare ZHANG, Mingkai CNNIC XINYUE, Zhang CNNIC PAN, Lanlan CNNIC HAGOPIAN, Peter Comcast BARNITZ, John Comcast EBERSMAN, Paul Comcast HLAVACEK, Tomas CZ.NIC FILIP, Ondrej CZ.NIC SURÝ, Ondřej CZ.NIC PETRASCH, Christian DENIC BHABUTA, Denesh DNS-OARC KHEMLANI, Dalini DNS-OARC GRAVES, Susan DNS-OARC SOTOMAYOR, William DNS-OARC MITCHELL, Keith DNS-OARC DUARTE, Eduardo DNS.PT ROBERTS, Bruce DomainTools ALLEN, David Dyn GRAY, Robert Dyn COWIE, James Dyn HYNES, Liam Dyn KNIGHT, Dave -

Diebold Nixdorf, Incorporated (Exact Name of Registrant As Specified in Its Charter)
Annual Report Transforming the Business Model to Generate Strong Free Cash Flow aanndd RReettuurrnn oonn IInnvveesstteedd CCapital1 The company is seeking to leverage its operating rigor and strong financial performance during 2020 to increase profitability, free cash flow generation and return on invested capital (ROIC) in 2021. $480 – $140 – $500 $170 ~18% 15% $453 $93 9% $401 $57 2019 2020 2021E 2019 2020 2021E 2019 2020 2021E Adjusted EBITDA1,2 Free Cash Flow 1,2 ROIC 1,2 Leveraging Competitive Differentiation for Growth Expecting 3% – 5% Revenue Growth in 2021 due to a strong product backlog and growth areas which include: $4,409 $4,000 – $4,100 $3,902 DN SeriesTM DN SeriesTM EASY DN AllConnectSM Data ATMs Self-Checkout Engine IoT-Enabled Solutions Service Model 2019 2020 2021E Revenue1 Managed Services Cloud-Native for Retailers and VynamicTM Payments Financial Institutions & Retail Software 1 All $ amounts are shown in millions. Company Outlook for 2021 provided on February 10, 2021. 2 Adjusted EBITDA, Free Cash Flow and ROIC are non-GAAP metrics. Please refer to “Notes for non-GAAP Measures,” following the “Exhibits” section of this report, for more information. Dear Shareholders Against the backdrop of a global pandemic, Diebold Nixdorf demonstrated the resiliency of its business model and a strong operating rigor in 2020. I am gratified by the many ways in which our employees adapted and responded to a dynamic and highly uncertain macro-environment. We cared for our employees, delivered for our customers, contributed to the well-being of our communities and generated strong financial results. Looking forward, we intend to build on this solid foundation in order to bring our DN Now transformation to a successful conclusion and evolve the business to deliver a balance of top-line growth, continuous operating improvements and significantly stronger free cash flow. -

Alpine Start Advising Response to Proposed Amendment 3 to the .COM Registry Agreement Greg Rafert, Ph.D. February 14, 2020
Alpine Start Advising Response to Proposed Amendment 3 to the .COM Registry Agreement Greg Rafert, Ph.D. February 14, 2020 I. Executive Summary 1. This comment provides an economic analysis of Verisign, Inc.’s (Verisign) proposed price increase for .COM registrations. Based on my training as an economist, review of the available evidence, and experience with ICANN and the TLD marketplace, I conclude that there is no economic rationale for Verisign to increase prices for .COM and that increased prices will very likely harm consumers: In the face of heightened competition, which has been provided as one reason for increasing .COM pricing, economic theory and empirical economic studies predict that a firm would typically lower, not increase, prices. To my knowledge, Verisign has not provided a rationale as to why increased competition would require it to increase prices for .COM. Verisign’s gross profit and operating margins have grown significantly over time and are currently high relative to other firms. While not demonstrative as to whether Verisign has market power in the TLD Alpine Start Advising 1 marketplace, they do suggest that changes in Verisign’s costs are not driving Verisign’s interest in increasing prices for .COM. An increase in the price of .COM registrations will harm consumers worldwide, as consumers are unlikely to switch to other, less expensive TLDs due to the high costs associated with switching from a .COM domain. While Verisign may argue that it will use increased revenues from .COM price increases to further improve the security and stability of the internet, thus benefiting consumers, this is unlikely. -
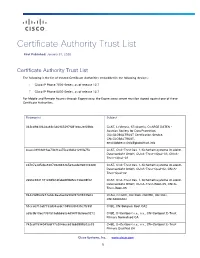
Certificate Authority Trust List
Certificate Authority Trust List First Published: January 31, 2020 Certificate Authority Trust List The following is the list of trusted Certificate Authorities embedded in the following devices: Cisco IP Phone 7800 Series, as of release 12.7 Cisco IP Phone 8800 Series, as of release 12.7 For Mobile and Remote Access through Expressway, the Expressway server must be signed against one of these Certificate Authorities. Fingerprint Subject 342cd9d3062da48c346965297f081ebc2ef68fdc C=AT, L=Vienna, ST=Austria, O=ARGE DATEN - Austrian Society for Data Protection, OU=GLOBALTRUST Certification Service, CN=GLOBALTRUST, [email protected] 4caee38931d19ae73b31aa75ca33d621290fa75e C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-nQual-03, CN=A- Trust-nQual-03 cd787a3d5cba8207082848365e9acde9683364d8 C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-Qual-02, CN=A- Trust-Qual-02 2e66c9841181c08fb1dfabd4ff8d5cc72be08f02 C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-Root-05, CN=A- Trust-Root-05 84429d9fe2e73a0dc8aa0ae0a902f2749933fe02 C=AU, O=GOV, OU=DoD, OU=PKI, OU=CAs, CN=ADOCA02 51cca0710af7733d34acdc1945099f435c7fc59f C=BE, CN=Belgium Root CA2 a59c9b10ec7357515abb660c4d94f73b9e6e9272 C=BE, O=Certipost s.a., n.v., CN=Certipost E-Trust Primary Normalised CA 742cdf1594049cbf17a2046cc639bb3888e02e33 C=BE, O=Certipost s.a., n.v., CN=Certipost E-Trust Primary Qualified CA Cisco Systems, Inc. www.cisco.com 1 Certificate Authority -

White Paper: a Proposal for DNAME Equivalence Mapping for TLD Strings
VeriSign® White Paper: A Proposal for DNAME Equivalence Mapping for TLD Strings COPYRIGHT NOTIFICATION ©2005 VeriSign, Inc. All rights reserved. VeriSign, the VeriSign logo “Where it all comes together,” and other trademarks, service marks, and designs are registered or unregistered trademarks of VeriSign and its subsidiaries in the United States and in foreign countries. 11/05. DISCLAIMER AND LIMITATION OF LIABILITY VeriSign, Inc. has made efforts to ensure the accuracy and completeness of the information in this document. However, VeriSign, Inc. makes no warranties of any kind (whether express, implied or statutory) with respect to the information contained herein. VeriSign, Inc. assumes no liability to any party for any loss or damage (whether direct or indirect) caused by any errors, omissions or statements of any kind contained in this document. Further, VeriSign, Inc. assumes no liability arising from the application or use of the product or service described herein and specifically disclaims any representation that the products or services described herein do not infringe upon any existing or future intellectual property rights. Nothing herein grants the reader any license to make, use, or sell equipment or products constructed in accordance with this document. Finally, all rights and privileges related to any intellectual property right described herein are vested in the patent, trademark, or service mark owner, and no other person may exercise such rights without express permission, authority, or license secured from the patent, trademark, or service mark owner. VeriSign Inc. reserves the right to make changes to any information herein without further notice. NOTICE AND CAUTION Concerning U.S. -

Siemens Annual Report 2001
s FINLAND annual review 2001 Global network of innovation Siemens in Finland The Siemens Osakeyhtiö Group is a technology and service company active in the information technology, communications, industry, energy and transportation sectors. During the year under review, the group had a turnover of €347 million and employed 1,677 people. The group includes subsidiaries Siemens Metering Oy and Netron Oy, AS Siemens in Estonia, and its subsidi- ary AS Siemens Electroservices, Siemens SIA in Latvia, and its subsidiary Teka Telekom (75% interest) and UAB Siemens in Lithuania. Wincor Nixdorf Oy is a joint venture owned by Wincor Nixdorf International GmbH (50.1%) and Siemens Osakeyhtiö (49.9%), PICSI Automation Oy is owned by PI-Consulting Oyj (70%) and Siemens Osakeyhtiö (30%) and CoPower SIA by PVO Engineering Oy, Vantaa Energy and Siemens Osakeyhtiö (33%). Other Siemens companies in Finland are BSH Kodinkoneet Oy, Epcos Nordic Oy, Fujitsu Siemens Computers Oy, Infineon Technologies Nordic Oy, Oy Osram Ab, Siemens Building Technologies Oy (Building Automation & HVAC Products and Security & Fire Systems), Siemens-Elema AB and Siemens Rahoitus Oy, which has a subsidiary in Estonia. Siemens companies in Finland and the Baltics have a turnover of around €578 million and employ 2,154 people. Siemens – Global network of innovation. SIEMENS GROUP KEY FIGURES €M 2001 2000 1999 1998 1997 New orders1) 412 419 390 349 247 Back orders1) 163 119 123 155 155 Invoicing2) 367 437 419 315 349 Turnover 347 282 298 238 221 Operating profit 17 17 14 13 11 as -

Supplerende Oplysninger Aktiebeholdning SAMPENSION INVEST
Supplerende oplysninger Aktiebeholdning SAMPENSION INVEST (GEM II) Pr. 31/12 2008 Navn Valuta Markedsværdi i 1000 DKK Anheuser-Busch IN Bev NV EUR 43.135 Asia Satellite Telecom HKD 3.933 China Foods Ltd HKD 1.861 Cosan Ltd USD 5.554 First Pacific Co HKD 2.007 Glorious Sun Enterprises HKD 1.813 LI & Fung Ltd. HKD 1.808 Shangri-La Asia Ltd- HKD 702 ALL America Latina Logist. BRL 11.929 Equatorial energia sa-ord BRL 3.322 Natura Cosmeticos SA BRL 7.247 Net Servicos De Comuni BRL 15.367 SUL America Sa BRL 8.575 Tractebel Energia SA BRL 12.795 Tele Norte Leste Part BRL 9.482 Terna participacoes S.A. BRL 10.286 Weg sa BRL 4.354 Inversiones Aguas Metropol CLP 8.569 China Telecom Corp.Ltd-H HKD 2.272 Wumart Stores Inc HKD 4.429 Ceske Energeticke Zavody A.S. CZK 6.751 Lecico Egypt Sae EGP 1.212 Highland Gold Mining Ltd GBP 3.269 Astro All Asia Networks MYR 2.234 Elephant Capital Plc GBP 4.570 Coca-Cola Hellenic Bottling EUR 11.062 Hongkong And China Gas HKD 44.208 Hopewell Holdings HKD 2.696 China Resources Enterprises HKD 28.658 China Mobile Ltd HKD 5.536 LENOVO GROUP LTD HKD 8.709 Gedeon Richter Rt HUF 14.636 BANK DANAMON PT IDR 943 Ormat industries ltd-ils ILS 5.012 Mizrahi Tefahot Bank Ltd ILS 8.558 Retalix Ltd. ILS 3.281 Retalix Ltd. USD 236 Check Point Software Technolog USD 24.048 Given Imaging Ltd. USD 3.108 Dabur india limited INR 3.168 Hindalco Industries Limited INR 2.517 Sun Pharmaceuticals Indus INR 8.539 Indian Hotels Co Ltd INR 8.497 Ambuja Cements Limited INR 4.101 Mahindra & Mahindra Limited INR 8.103 Godrej consumer products ltd INR 8.772 Tata Tea Ltd INR 5.307 Marico Ltd. -

Annual Report 2005 Key Figures
s Annual Report 2005 Key figures in millions of euros 2005 (1) 2004 (1) New orders(2) 83,791 75,789 Sales(2) 75,445 70,237 Income from continuing operations 3,058 3,450 Loss from discontinued operations, net of income taxes (810) (45) Net income 2,248 3,405 Net cash from operating and investing activities(2) (1,489) 3,015 therein: Net cash provided by operating activities 4,217 4,704 Net cash used in investing activities (5,706) (1,689) Supplemental contributions to pension trusts (included in net cash provided by (used in) operating activities) (1,496) (1,255) Net proceeds from the sale of Infineon shares (included in net cash provided by (used in) investing activities) – 1,794 Research and development expenses(2) 5,155 4,650 Shareholders’ equity (September 30) 27,117 26,855 Employees(2) (September 30, in thousands) 461 424 (1) Fiscal year from October 1 to September 30 (2) Continuing operations (excluding the discontinued mobile devices activities) Contents Letter to our Shareholders 6 Managing Board 12 Fit4More Performance and Portfolio 14 Operational Excellence 18 People Excellence 22 Corporate Responsibility 26 Group Presidents 30 Business Areas 32 Megatrends 48 Report of the Supervisory Board 64 Corporate Governance Report 72 Compensation Report 78 Information for shareholders* 88 Management’s discussion and analysis 90 Consolidated Financial Statements 136 Statement of the Managing Board 214 Independent auditors’ report 215 Supervisory Board 220 Managing Board 222 Siemens financial calendar 228 Corporate Structure** * With separate