White Paper: a Proposal for DNAME Equivalence Mapping for TLD Strings
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Paypal's Security
PayPal’s Security Key PayPal is a great service for enabling both businesses and consumers to buy and sell goods and services online without exposing private financial information to the other parties in a transaction. As a consumer, you can safely purchase goods and services online without exposing your credit or debit card information to be recorded and possibly misused. As a business, you can be paid for your goods or services using the Web or email without the need of storing your customer’s private financial information. A big concern with PayPal is that anyone who knows the password of your PayPal account can access the financial services that you have authorized to be used with PayPal. For consumers, this means that unauthorized purchases or cash transfer may be performed from your credit cards and bank accounts. As a business, unauthorized PayPal access can be a source of fraudulent purchases. Password security is always the responsibility of the PayPal account holder; but now PayPal has a service to make the disclosure of your PayPal password an almost insignificant threat. In February 2007, PayPal introduced an optional security key system for users to access their PayPal accounts. The security key does not replace your PayPal password; instead, it adds an extra layer of security by requiring an additional security code be entered with your password when you log into your PayPal account. What makes this security code so different from a password is that it randomly generated by a small, electronic device called a security token, which is a key fob that easily fits in the palm of your hand. -

Zoom Go Boom!
Security Now! Transcript of Episode #761 Page 1 of 21 Transcript of Episode #761 Zoom Go Boom! Description: This week starts off with a bunch of web browser news including Firefox zero-days, Safari's recent scrape, more coronavirus-related feature rollbacks, the status of TLS v1.0 and 1.1, and some interesting developments on the Edge front. We revisit the lingering STIR and SHAKEN telco protocol mess, then look at a new DNS-filtering add-on service from Cloudflare and at the growing influence of an Internet group hoping to tighten up the mess with BGP. After a quick update on my SpinRite project, we take a look at what's been going on with the security of Zoom, the suddenly chosen tool for hosting Internet virtual classrooms and meetings of all kinds. High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-761.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-761-lq.mp3 SHOW TEASE: It's time for Security Now!. Steve Gibson is here. Lots to talk about including a Mozilla Firefox zero-day. It's been fixed, but just barely. A problem with Safari. BGP gets some MANRS. And what's wrong with Zoom, and a pretty good alternative. It's all coming up next on Security Now!. Leo Laporte: This is Security Now! with Steve Gibson, Episode 761, recorded Tuesday, April 7th, 2020: Zoom Go Boom! It's time for Security Now!, the show where we cover your security and privacy and safety and quarantine online. -
2015 AGM Minutes
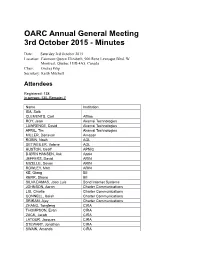
OARC Annual General Meeting 3rd October 2015 - Minutes Date: Saturday 3rd October 2015 Location: Fairmont Queen Elizabeth, 900 Rene Levesque Blvd. W Montreal, Quebec H3B 4A5, Canada Chair: Ondrej Filip Secretary: Keith Mitchell Attendees Registered: 138 In person: 130, Remote: 7 Name Institution ISA, Saib CLEMENTS, Carl Afilias ROY, Jean Akamai Technologies LAWRENCE, David Akamai Technologies APRIL, Tim Akamai Technologies MILLER, Donavan Amazon ROBIN, Noah AOL DETWEILER, Valerie AOL HUSTON, Geoff APNIC BJØRN HANSEN, Ask Apple JEFFERS, David ARIN MIZELLE, Devon ARIN ROWLEY, Matt ARIN KE, Qiang BII KERR, Shane BII SILVA DAMAS, Joao Luis Bond Internet Systems JOHNSON, Aaron Charter Communications LIU, Charlie Charter Communications CONNELL, Isaiah Charter Communications SRIRAM, Ajay Charter Communications ZHANG, Tongfeng CIRA THOMPSON, Evan CIRA ZACK, Jacob CIRA LATOUR, Jacques CIRA STEWART, Jonathan CIRA SWAIN, Amanda CIRA MALENFANT, Eric CIRA CHANTIGNY, Rock CIRA BOOS, Roy Cisco Systems KWONG, David Cisco Systems VALSORDA, Filippo Cloudflare GUÐMUNDSSON, Ólafur CloudFlare ZHANG, Mingkai CNNIC XINYUE, Zhang CNNIC PAN, Lanlan CNNIC HAGOPIAN, Peter Comcast BARNITZ, John Comcast EBERSMAN, Paul Comcast HLAVACEK, Tomas CZ.NIC FILIP, Ondrej CZ.NIC SURÝ, Ondřej CZ.NIC PETRASCH, Christian DENIC BHABUTA, Denesh DNS-OARC KHEMLANI, Dalini DNS-OARC GRAVES, Susan DNS-OARC SOTOMAYOR, William DNS-OARC MITCHELL, Keith DNS-OARC DUARTE, Eduardo DNS.PT ROBERTS, Bruce DomainTools ALLEN, David Dyn GRAY, Robert Dyn COWIE, James Dyn HYNES, Liam Dyn KNIGHT, Dave -

Alpine Start Advising Response to Proposed Amendment 3 to the .COM Registry Agreement Greg Rafert, Ph.D. February 14, 2020
Alpine Start Advising Response to Proposed Amendment 3 to the .COM Registry Agreement Greg Rafert, Ph.D. February 14, 2020 I. Executive Summary 1. This comment provides an economic analysis of Verisign, Inc.’s (Verisign) proposed price increase for .COM registrations. Based on my training as an economist, review of the available evidence, and experience with ICANN and the TLD marketplace, I conclude that there is no economic rationale for Verisign to increase prices for .COM and that increased prices will very likely harm consumers: In the face of heightened competition, which has been provided as one reason for increasing .COM pricing, economic theory and empirical economic studies predict that a firm would typically lower, not increase, prices. To my knowledge, Verisign has not provided a rationale as to why increased competition would require it to increase prices for .COM. Verisign’s gross profit and operating margins have grown significantly over time and are currently high relative to other firms. While not demonstrative as to whether Verisign has market power in the TLD Alpine Start Advising 1 marketplace, they do suggest that changes in Verisign’s costs are not driving Verisign’s interest in increasing prices for .COM. An increase in the price of .COM registrations will harm consumers worldwide, as consumers are unlikely to switch to other, less expensive TLDs due to the high costs associated with switching from a .COM domain. While Verisign may argue that it will use increased revenues from .COM price increases to further improve the security and stability of the internet, thus benefiting consumers, this is unlikely. -
Certificate Authority Trust List
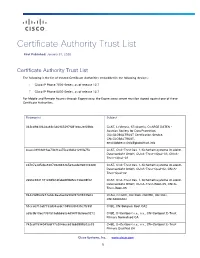
Certificate Authority Trust List First Published: January 31, 2020 Certificate Authority Trust List The following is the list of trusted Certificate Authorities embedded in the following devices: Cisco IP Phone 7800 Series, as of release 12.7 Cisco IP Phone 8800 Series, as of release 12.7 For Mobile and Remote Access through Expressway, the Expressway server must be signed against one of these Certificate Authorities. Fingerprint Subject 342cd9d3062da48c346965297f081ebc2ef68fdc C=AT, L=Vienna, ST=Austria, O=ARGE DATEN - Austrian Society for Data Protection, OU=GLOBALTRUST Certification Service, CN=GLOBALTRUST, [email protected] 4caee38931d19ae73b31aa75ca33d621290fa75e C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-nQual-03, CN=A- Trust-nQual-03 cd787a3d5cba8207082848365e9acde9683364d8 C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-Qual-02, CN=A- Trust-Qual-02 2e66c9841181c08fb1dfabd4ff8d5cc72be08f02 C=AT, O=A-Trust Ges. f. Sicherheitssysteme im elektr. Datenverkehr GmbH, OU=A-Trust-Root-05, CN=A- Trust-Root-05 84429d9fe2e73a0dc8aa0ae0a902f2749933fe02 C=AU, O=GOV, OU=DoD, OU=PKI, OU=CAs, CN=ADOCA02 51cca0710af7733d34acdc1945099f435c7fc59f C=BE, CN=Belgium Root CA2 a59c9b10ec7357515abb660c4d94f73b9e6e9272 C=BE, O=Certipost s.a., n.v., CN=Certipost E-Trust Primary Normalised CA 742cdf1594049cbf17a2046cc639bb3888e02e33 C=BE, O=Certipost s.a., n.v., CN=Certipost E-Trust Primary Qualified CA Cisco Systems, Inc. www.cisco.com 1 Certificate Authority -

WIPO Domain Name Dispute: Case No. LRO2013-0066
ARBITRATION AND MEDIATION CENTER EXPERT DETERMINATION LEGAL RIGHTS OBJECTION Regtime Ltd. and Legato Ltd. v. VeriSign Sarl Case No. LRO2013-0066 1. The Parties The Objectors are Regtime Ltd. and Legato Ltd., Russian Federation, represented by Winston & Strawn LLP, United States of America. The Respondent/Applicant is VeriSign Sarl, Switzerland, represented by Thomas C. Indelicarto, VeriSign Inc., United States of America. 2. The applied-for gTLD string The applied-for gTLD string is <.ком> [xn--j1aef]. 3. Procedural History The Objection was filed with the WIPO Arbitration and Mediation Center (the “WIPO Center”) on March 13, 2013 (UTC), pursuant to the New gTLD Dispute Resolution Procedure (the “Procedure”). In accordance with Article 9 of the Procedure, the WIPO Center completed the review of the Objection on March 22, 2013, and determined that the Objection complies with the requirements of the Procedure and the World Intellectual Property Organization Rules for New gTLD Dispute Resolution for Existing Legal Rights Objections (the “WIPO Rules for New gTLD Dispute Resolution”). In accordance with Article 11(a) of the Procedure, the WIPO Center formally notified the Respondent of the Objection, and the proceedings commenced on April 22, 2013. In accordance with Article 11(b) and relevant communication provisions of the Procedure, the Response was timely filed with the WIPO Center on May 22, 2013. The WIPO Center appointed Assen Alexiev as the Panel in this matter on June 13, 2013. The Panel finds that it was properly constituted. The Panel has submitted the Statement of Acceptance and Declaration of Impartiality and Independence, as required by the WIPO Center to ensure compliance with Article 13(c) of the Procedure and Paragraph 9 of WIPO Rules for New gTLD Dispute Resolution. -

Intel® Remote Configuration Certificate Utility Frequently Asked Questions
Intel® Remote Configuration Certificate Utility Frequently Asked Questions General Info 1. What operating system do I have to use to run the wizard? 2. What configurations are required prior to running the wizard? 3. What user privileges do I need to have in order to run the application? 4. Why do I have to use Certificate Authority? 5. How does certificate signing work? 6. Can different users and servers be used to generate a certificate? 7. Is it possible to make a back-up of the private key? 8. Do I need to own the domain that I am going to use for purchasing a certificate? 9. Does this tool provision a client system for me? Certificate Install 10. Do I have to use your wizard to install the certificate? 11. How can I access the certificate after it is installed? 12. What are the next steps after I install the certificate? Working with Vendors 13. How do I determine if a certificate response is valid? 14. How do I save the certificate response? GoDaddy* 15. Can I use GoDaddy’s ‘Standard SSL’? 16. What should I enter in the “Company Name” field in the wizard, if I have purchased a certificate from GoDaddy? Comodo* 17. What certificates does Comodo support? VeriSign* 18. What certificates are supported by VeriSign managed PKI accounts? 19. How does the May 17, 2009 VeriSign Root migration affect remote configuration certificates? Other Considerations 20. What needs to be done in the Certificate Authority to support UCC Certificates? 21. What if I want to install a certificate type the utility does not recommend? Return to Top General Info Q1. -

TCPA’S Business Objectives
Trusted Computing Platform Alliance: The Mother(board) of all Big Brothers Lucky Green c y p h e r p u n k s . t o TCPA’s Business Objectives | Prevent use of unlicensed software. | Digital Rights Management (DRM). z Prevent CD ripping and DivX creation. z Plug “analog hole.” z Enable information flow control. | Make PC the core of the home entertainment center, growing overall market. | Meet operational needs of law enforcement and intelligence services (FBI, Homeland, NSA, non-U.S. law enforcement). TCPA’s Technical Objectives | Prevent the owner of a computer from obtaining root access. | Enforce three levels of access privileges: z Privileged access [TCPA members only]. z Underprivileged access [platform owner]. z Unprivileged access [non-TCPA applications]. TCPA Heritage | To succeed where previous efforts have failed: z Processor ID (Intel, 1995-1998). z Encrypted CPU instruction sets (Intel, 1995-TCPA Phase II). z International Cryptography Framework (HP, 1996). z Smartcards on motherboard (IBM, ongoing). TCPA History | Founded in 1999 by: z Intel z Microsoft z HP z Compaq z IBM TCPA Membership Profile | The TCPA is a forum of platform product vendors. z CPU: • Intel, Advanced Micro Devices (AMD), Motorola. z BIOS/Chips: • Phoenix/Award, American Megatrends (AMI), National Semiconductor. z Security: • VeriSign, Wave Systems, RSA Security, Check Point, Certicom, Trend Micro, Symantec, Tripwire, Crypto AG [NSA]. z Applications: • Microsoft, Adobe. z Systems: • HP, IBM, Dell, Gateway, Fujitsu, Samsung, Toshiba. TCPA’s 170+ Member Companies 360 Degree Web Ethentica Microsoft Corporation SPYRUS, Inc. 3Com Corp. Excalibur Solutions, Inc Mitac International Corporation SSH Communications Security, Inc. Access360 FARGOS Development, LLC Mobile-Mind, Inc. -

Website Payments Pro Developer's Guide
Website Payments Pro Developer’s Guide © 2006 PayPal Inc. All rights reserved. PayPal, the PayPal logo, Payflow, and Payflow Pro are registered trademarks of PayPal Inc. Other trademarks and brands are the property of their respective owners. The information in this document belongs to PayPal Inc. It may not be used, reproduced or disclosed without the written approval of PayPal Inc. PayPal (Europe) Ltd. is authorised and regulated by the Financial Services Authority in the United Kingdom as an electronic money institution. PayPal FSA Register Number: 226056. Notice of Non-Liability PayPal Inc. is providing the information in this document to you “AS-IS” with all faults. PayPal Inc. makes no warranties of any kind (whether express, implied or statutory) with respect to the information contained herein. PayPal Inc. assumes no liability for damages (whether direct or indirect), caused by errors or omissions, or resulting from the use of this document or the information contained in this document or resulting from the application or use of the product or service described herein. PayPal Inc. reserves the right to make changes to any information herein without further notice. PayPal Inc. does not guarantee that the features described in this document will be announced or made available to anyone in the future. Contents Preface . 7 Intended Audience . 7 Scope . 7 Organisation of This Document . 7 Where to Go for More Information . 8 How to Contact Customer Service . 8 Chapter 1 Website Payments Pro Overview . 9 How Website Payments Pro Works . 9 Supported Transactions . 10 Supported Currencies . 10 Direct Payment Overview . 11 PayPal Express Checkout Overview. -

Financefinance Ough Agesthe Ages T R Ade
thr FinanceFinance ough agesthe ages t r ade Man’s first foray into personal finance took the form of barter – the exchange of what one had for what one needed. In ancient Egypt, farmers deposited their harvested grain in state-owned grain banks until they could be traded for other goods. For the Aztec Indians of Central America, the cacao seed (from which chocolate is derived) was the mainstay of one’s wealth, and used to obtain food, slaves... even gold. In contrast, natives on the Western Caroline Islands, southwest of Guam, utilized great carved wheels of stone which they rolled from place to place to exchange for commodities and services. Though widely utilized throughout the world, these forms of finance had their drawbacks: grain could be consumed by vermin and was subject to rot. Cacao seeds quickly became too bulky for large transactions. And because of their unwieldy size, stone wheels limited the area in which one could carry out personal business. Clearly, some other form of finance needed to be devised. Corporate Profile Intuit’s mission is to revolutionize the way individuals and small businesses manage their finances. Today, with 15 million customers and more than 3,500 dedicated and entrepre- neurial employees, Intuit is emerging as the leader in electronic finance (e-finance). Our products and services enable people to connect to a wide range of financial resources and destinations—from banks and insurance companies to lenders, investment firms and tax agencies. At the same time, we are creating links between these destinations, with the ultimate goal of completely interconnecting—and simplifying—all aspects of a person’s financial life. -

Booking Holdings Inc
Filing ID #20018465 PerIODIC TrANSACTION rePOrT Clerk of the House of Representatives • legislative Resource Center • 135 Cannon Building • Washington, DC 20515 fIler INfOrmATION Name: Hon. William R. Keating Status: Member State/District: MA09 TrANSACTIONS ID Owner Asset Transaction Date Notification Amount Cap. Type Date Gains > $200? Accenture plc Class A Ordinary P 03/17/2021 03/26/2021 $1,001 - $15,000 gfedc Shares (ACN) [ST] FIlINg STATuS: New SuBHOlDINg OF: Bill's IRA Alphabet Inc. - Class A (gOOgl) P 03/17/2021 03/26/2021 $1,001 - $15,000 gfedc [ST] FIlINg STATuS: New SuBHOlDINg OF: Bill's IRA ANTHEM INC NOTE CAll MAKE P 04/16/2021 04/16/2021 $15,001 - gfedc WHOlE 3.65000% 12/01/2027 $50,000 [CS] FIlINg STATuS: New SuBHOlDINg OF: Bill's IRA DESCRIPTION: 036752AB9 Aramark (ARMK) [ST] P 03/17/2021 03/26/2021 $1,001 - $15,000 gfedc FIlINg STATuS: New SuBHOlDINg OF: Bill's IRA AutoZone, Inc. (AZO) [ST] P 03/17/2021 03/26/2021 $1,001 - $15,000 gfedc FIlINg STATuS: New SuBHOlDINg OF: Bill's IRA Baxter International Inc. (BAX) P 03/17/2021 03/26/2021 $1,001 - $15,000 gfedc [ST] FIlINg STATuS: New ID Owner Asset Transaction Date Notification Amount Cap. Type Date Gains > $200? SuBHOlDINg OF: Bill's IRA Baxter International Inc. (BAX) P 04/14/2021 04/16/2021 $1,001 - $15,000 gfedc [ST] FIlINg STATuS: New SuBHOlDINg OF: Bill's IRA BECTON DICKINSON &CO NOTE P 03/30/2021 04/06/2021 $15,001 - gfedc CAll MAKE WHOlE 3.73400% $50,000 12/15/2024 [CS] FIlINg STATuS: New SuBHOlDINg OF: Bill's IRA DESCRIPTION: corporate bond BJ's Wholesale Club Holdings, Inc. -

5 Mistakes Small Businesses Make Online Sponsored by Verisign Small Business Owners Are Busy
5 Mistakes Small Businesses Make Online Sponsored by Verisign Small business owners are busy. It’s difficult to focus the right amount of attention on all facets of your business when you’ve got both off- and online operations to juggle. So it’s no surprise that mistakes are made along the way. But when nine out of 10 U.S. consumers use the internet to look for local goods and services, and research a potential purchase,1 one mistake you can’t afford to make is neglecting your online presence. Here are a few common errors that many small businesses make online, and what you can do to help make sure your business is on the right track. 1. Using a social media page as your only web address Only 51% of small businesses have a website,2 yet 80% use social media.3 So for many small businesses, social media is key to growing your business. But how do your customers know where to find you on social media? One of the easiest ways to ensure customers can find you no matter where your online business is located is toregister a domain name and point it to your business’s social media page. Called domain forwarding, it works just like forwarding mail. You create a rule that automatically redirects anyone who visits your domain name to your page on Facebook, LinkedIn, Etsy or whatever social media platform you use as your business’s communications or e-commerce hub. Domain forwarding is easy to set up with your domain name registrar and can take as little as five minutes.