An Introduction to Intel® AMT Remote Configuration Certificate Selection
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Paypal's Security
PayPal’s Security Key PayPal is a great service for enabling both businesses and consumers to buy and sell goods and services online without exposing private financial information to the other parties in a transaction. As a consumer, you can safely purchase goods and services online without exposing your credit or debit card information to be recorded and possibly misused. As a business, you can be paid for your goods or services using the Web or email without the need of storing your customer’s private financial information. A big concern with PayPal is that anyone who knows the password of your PayPal account can access the financial services that you have authorized to be used with PayPal. For consumers, this means that unauthorized purchases or cash transfer may be performed from your credit cards and bank accounts. As a business, unauthorized PayPal access can be a source of fraudulent purchases. Password security is always the responsibility of the PayPal account holder; but now PayPal has a service to make the disclosure of your PayPal password an almost insignificant threat. In February 2007, PayPal introduced an optional security key system for users to access their PayPal accounts. The security key does not replace your PayPal password; instead, it adds an extra layer of security by requiring an additional security code be entered with your password when you log into your PayPal account. What makes this security code so different from a password is that it randomly generated by a small, electronic device called a security token, which is a key fob that easily fits in the palm of your hand. -

Intel® Core™ I7 and Intel® Core™ I5 Processor-Based Platforms for Embedded Computing
PLATFORM BRieF Intel® Core™ i7 and i5 Processors with Mobile Intel® QM57 Express Chipset Embedded Computing Intel® Core™ i7 and Intel® Core™ i5 Processor-based Platforms for Embedded Computing Product Overview developers can create one board design Based on 32nm process technology, and scale their product line with a variety Intel® Core™ i7 and Intel® Core™ i5 proces- of performance-per-watt processors using sors feature intelligent performance, the same socket. Thermal design power power efficiency, integrated graphics, and (TDP) options range from 18W to 35W. error correcting code (ECC) memory1 on industry-standard x86 architecture. When Product Highlights paired with the Mobile Intel® QM57 Express Integrated graphics engine: Supports chipset, this integrated two-chip platform enhanced graphics capabilities and perfor- provides excellent graphics, memory and mance while reducing overall platform I/O bandwidth, as well as remote manage- power requirements and footprint. ment capabilities and reliability to meet Memory Error Correction: ECC memory the requirements of a broad range of provides a high level of data integrity, embedded applications including retail and reliability, and system uptime (select SKUs). transaction solutions, gaming platforms and industrial automation equipment. Intel® Intelligent Power Technology4: Reduces idle power consumption through The processors feature dual-core proc- architectural improvements such as essing with industry-leading performance integrated power gates and automated capabilities, including Intel® Turbo Boost low-power states. Technology2 and Intel® Hyper-Threading Technology.3 Advanced Encryption Standard Intel® Turbo Boost Technology: Applica- Instructions (AES-NI) help accelerate data tions take advantage of higher speed encryption and decryption, and improve execution on demand by using available performance. -

Your Securi As Strong a Weakest
Your security is only as strong as it’s weakest link. LAST WORDS Our business is protecting yours Glimpses at how technology has changed—and changed our lives. That’s why Dell and Kensington provide employee compliance services such as viral posters and e-reminders to ensure that every employee uses their What is this? laptop lock. Talk to Dell who’ll be able to help you make your security investments work harder for you. Here’s a Visit: www.logon-lockon.com memory. MicroSaver Laptop Lock Dell# 461-10054 1984 2010 The IBM AT 4GB is no big is introduced deal for personal and has 256k computers. of RAM. KE6442 Dell Compliance Ad UK.indd 1 5/14/10 11:15:44 AM Courtesy of Computer History Museum So, that’s 256,000 bytes We’ll give you a hint: it’s not a piece of compared to 4,000,000,000 furniture. It is a device based on technology. bytes, a 15,000-fold Let us know what you think this is, and email increase! your answer to [email protected] We’ll reveal the answer in the next issue of Catalyst and recognise the winner. 1980 2010 Lighten up. 1981: Adam Osborne introduces the Osborne I, the first successful portable computer. It weighs 25 pounds. 2010: The lightest netbooks can weigh less than 3 pounds. My, you’ve changed! Experts in laptop protection for over 25 years; Targus offers business Dell N.V., Zone 3 Doornveld 130, 1731 Asse-Zellik, Terms and Conditions of Sales, Service and Finance apply and are available on HYPERLINK “http://www.dell.be/business” www.dell.be/business. -

Securing and Consolidating Industrial Automation Systems Based on Intel® Architecture Using Open Source Technology
White Paper Intel® Trusted Execution Technology and Intel® Virtualization Technology Design House and Platform Solutions Securing and Consolidating Industrial Automation Systems Based on Intel® Architecture Using Open Source Technology Using open source components, Intel demonstrates how Intel® Trusted Execution Technology and Intel® Virtualization Technology complement existing security measures for networked industrial systems based on Intel® Architecture. Executive Summary This paper presents an overview of the importance of security for today’s connected industrial automation systems and highlights the benefits of Intel® Trusted Execution Technology (Intel® TXT) and Intel® Virtualization Technology (Intel® VT) in complementing existing security measures. Furthermore, a demonstration system (a product separation industrial machine) using open source technology is described with a procedure that may be considered to set up the system. “This demonstration of a security solution for Background industrial automation Industrial automation systems are unknown security vulnerabilities in increasingly connected to each other the operating system and application systems uses open source in a manufacturing environment as software in order to access confidential technology with Intel® part of the Internet of Things (IoT) data or to manipulate processes in concept where real-time information connected systems. The potential Architecture. By designing from connected devices can be consequences of a security breach on security into its processors, -

Zoom Go Boom!
Security Now! Transcript of Episode #761 Page 1 of 21 Transcript of Episode #761 Zoom Go Boom! Description: This week starts off with a bunch of web browser news including Firefox zero-days, Safari's recent scrape, more coronavirus-related feature rollbacks, the status of TLS v1.0 and 1.1, and some interesting developments on the Edge front. We revisit the lingering STIR and SHAKEN telco protocol mess, then look at a new DNS-filtering add-on service from Cloudflare and at the growing influence of an Internet group hoping to tighten up the mess with BGP. After a quick update on my SpinRite project, we take a look at what's been going on with the security of Zoom, the suddenly chosen tool for hosting Internet virtual classrooms and meetings of all kinds. High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-761.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-761-lq.mp3 SHOW TEASE: It's time for Security Now!. Steve Gibson is here. Lots to talk about including a Mozilla Firefox zero-day. It's been fixed, but just barely. A problem with Safari. BGP gets some MANRS. And what's wrong with Zoom, and a pretty good alternative. It's all coming up next on Security Now!. Leo Laporte: This is Security Now! with Steve Gibson, Episode 761, recorded Tuesday, April 7th, 2020: Zoom Go Boom! It's time for Security Now!, the show where we cover your security and privacy and safety and quarantine online. -

Intel® AMT Configuration Utility User Guide
Intel® AMT Configuration Utility User Guide Version 11.0 Document Release Date: December 17, 2015 License Intel®Setup and Configuration Software (Intel® SCS) is furnished under license and may only be used or copied in accordance with the terms of that license. For more information, refer to the “Exhibit A” section of the “Intel(R) SCS License Agreement.rtf”, located in the Licenses folder. Legal Information No license (express or implied, by estoppel or otherwise) to any intellectual property rights is granted by this document. Intel disclaims all express and implied warranties, including without limitation, the implied warranties of merchantability, fitness for a particular purpose, and non-infringement, as well as any warranty arising from course of performance, course of dealing, or usage in trade. The products described may contain design defects or errors known as errata which may cause the product to deviate from published specifications. Current characterized errata are available on request. Intel technologies' features and benefits depend on system configuration and may require enabled hardware, specific software, or services activation. Performance varies depending on system configuration. Check with your system manufacturer or retailer. No computer system can be absolutely secure. Intel does not assume any liability for lost or stolen data or systems or any damages resulting from such losses. Intel® AMT should be used by a knowledgeable IT administrator and requires enabled systems, software, activation, and connection to a corporate network. Intel AMT functionality on mobile systems may be limited in some situations. Your results will depend on your specific implementation. Learn more by visiting Intel® Active Management Technology. -

Intel® NUC 9 Pro Kit Product Brief
INTEL® NUC 9 PRO A COMPACT WORKSTATION FOR ALL YOUR CREATIVE TASKS Render faster, visualize more with full-powered GPUs INTEL NUC TO SUPPORT DESKTOP CREATE AT WILL, INTEL® NUC 1ST GRAPHICS MORE WORKSTATON BANDWIDTH WITH 24/7/365 8X THUNDERBOLT™ 31 Behind every creator is a workhorse like the Intel® FEATURES IDEAL FOR NUC 9 Pro kit, a compact workstation with room for • Intel Xeon processor • Content creation the latest desktop graphics. Powered by the Intel® • Intel Core i7 vPro processor • AI development and inference NUC 9 Pro Compute Element, this first-ever Intel NUC • HDMI* 2.0a • Edge analytics workstation is built to handle demanding content • Two Thunderbolt 3 ports • Data visualization creation, data analysis, and AI development and • Four USB 3.1 ports • CAD • Supports 3x 4K displays inference tasks. (additional displays supported with The Intel NUC 9 Pro Compute Element, powered by an add-in graphics card) AVAILABLE SKUs an Intel® Xeon® or Intel® Core™ i7 vPro® processor, • Intel® Wi-Fi 6 • Intel® NUC Kit • Bluetooth* 5 • Intel® NUC Compute Element delivers top-end performance—all in a 5 liter chassis • Two Intel® Gigabit LAN ports small enough to sit behind a monitor. Plus, there are • Dual-slot PCIe x16 slot two Thunderbolt™ 3 ports for fast data transfers and • 3-year limited warranty 500 watts of onboard power for a dual-slot PCIe* x16 graphics card. Whether you’re visualizing a financial quantitative analysis or using AutoCAD to design a new building, the Intel NUC 9 Pro gives you the power to create. Intel NUC 9 Pro: Uncompromised -
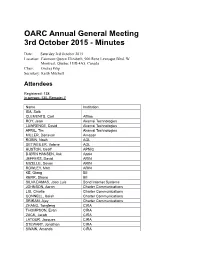
2015 AGM Minutes
OARC Annual General Meeting 3rd October 2015 - Minutes Date: Saturday 3rd October 2015 Location: Fairmont Queen Elizabeth, 900 Rene Levesque Blvd. W Montreal, Quebec H3B 4A5, Canada Chair: Ondrej Filip Secretary: Keith Mitchell Attendees Registered: 138 In person: 130, Remote: 7 Name Institution ISA, Saib CLEMENTS, Carl Afilias ROY, Jean Akamai Technologies LAWRENCE, David Akamai Technologies APRIL, Tim Akamai Technologies MILLER, Donavan Amazon ROBIN, Noah AOL DETWEILER, Valerie AOL HUSTON, Geoff APNIC BJØRN HANSEN, Ask Apple JEFFERS, David ARIN MIZELLE, Devon ARIN ROWLEY, Matt ARIN KE, Qiang BII KERR, Shane BII SILVA DAMAS, Joao Luis Bond Internet Systems JOHNSON, Aaron Charter Communications LIU, Charlie Charter Communications CONNELL, Isaiah Charter Communications SRIRAM, Ajay Charter Communications ZHANG, Tongfeng CIRA THOMPSON, Evan CIRA ZACK, Jacob CIRA LATOUR, Jacques CIRA STEWART, Jonathan CIRA SWAIN, Amanda CIRA MALENFANT, Eric CIRA CHANTIGNY, Rock CIRA BOOS, Roy Cisco Systems KWONG, David Cisco Systems VALSORDA, Filippo Cloudflare GUÐMUNDSSON, Ólafur CloudFlare ZHANG, Mingkai CNNIC XINYUE, Zhang CNNIC PAN, Lanlan CNNIC HAGOPIAN, Peter Comcast BARNITZ, John Comcast EBERSMAN, Paul Comcast HLAVACEK, Tomas CZ.NIC FILIP, Ondrej CZ.NIC SURÝ, Ondřej CZ.NIC PETRASCH, Christian DENIC BHABUTA, Denesh DNS-OARC KHEMLANI, Dalini DNS-OARC GRAVES, Susan DNS-OARC SOTOMAYOR, William DNS-OARC MITCHELL, Keith DNS-OARC DUARTE, Eduardo DNS.PT ROBERTS, Bruce DomainTools ALLEN, David Dyn GRAY, Robert Dyn COWIE, James Dyn HYNES, Liam Dyn KNIGHT, Dave -

Intel Vpro® Platform Vs. AMD* Pro Out-Of-Band Management White
INTEL vPro® vs. AMD® PRO* OUT-OF-BAND MANAGEMENT WHITE PAPER MARCH 2020 Deborah Mrazek Senior UX Strategist Colin Bay Chief Research Officer concreteUX.com OUT-OF-BAND MANAGEMENT (OOBM) PLATFORM COMPARISON DASH IT administrators and decision-makers seek the best solution for managing their networked endpoints for both wired and Wi-Fi connected devices when powered off or the OS isn’t running COMPETITIVE (i.e., out-of-band management). Hired by Intel as a third party, we put management of the Intel vPro® platform to the test in the ASSESSMENT hands of some pretty savvy IT administrators, then asked them to compare its capabilities with AMD PRO—you’ll want to hear what they had to say. They had some compelling ideas about which of these two platforms most capably and robustly meets the growing need for remote, in-band, and out-of-band endpoint management. THIRD-PARTY TESTING FINDS AMD® PRO MANAGEABILITY LAGS This white paper investigates and compares manageability aspects of the AMD PRO and Intel vPro platforms, with a focus on functionality, usability, and standards adherence. AMD ® BEHIND INTEL VPRO PLATFORM suggests that AMD PRO is more robust and more compatible than Intel vPro technology. We found stark differences. We’ll show you why. We’ll present user experience test findings, expert reviews, and analyses that spotlight the Intel vPro platform’s advantages, particularly in critical areas like security, features, and out-of-band management over Wi-Fi—one of the biggest advantages of the Intel vPro platform. We’ll also address knowledge gaps in customer understanding. -

11Th Gen Intel Vpro® Platform
11th Gen Intel vPro® Platform Built for Business. Wherever Business Happens. PRODUCT BRIEF 11th Gen Intel Core™ vPro® Processors The latest Intel vPro® platform is powered business continuity. 1 by the world's best business processors. From small businesses to large enterprises, 11th Gen Intel® Core™ vPro® mobile end users and IT staff have long enjoyed processors enable amazing experiences for the benefits of Intel’s trusted, built-for- IT and end users and set a new standard in business computing platform. The Intel business security, performance, and remote vPro® platform delivers groundbreaking manageability. performance for amazing end user Today, more businesses and outsourced IT experiences, comprehensive security service providers are discovering how the features, and leading remote manageability built-in benefits of the Intel vPro® platform and PC stability. can support today’s needs and scale to provide a reliable foundation for growth and See backup for configuration details. For more complete information about performance and benchmark results, www.Intel.com/11thgenvpro for details. Results may vary. 2 The needs of today’s business PC users are changing to keep up with a business world that’s changing faster than ever. With more employees working remotely than ever The Business before, many businesses are struggling to keep up with security, manageability, and day-to-day PC World Is troubleshooting that would have otherwise been handled deskside and in-office. Changing To ensure business continuity, employees require a secure, premium computing experience anytime Faster Than and anyplace they create, share, and collaborate. For technology decision makers, selecting and Ever efficiently deploying the right hardware stands on the critical path to business results. -

Intel® Vpro™ and Intel® Centrino® Pro Processor Technology Quick Start Guide
Guide Intel® vPro™ and Intel® Intel® Centrino® with vPro™ Technology Intel® Core™2 Processor with vPro™ Technology Centrino® Pro Processor Technology Quick Start Guide Based on Intel® Active Management Technology and LANDesk® Management Suite 8.8 Version 1.8 October 2008 Intel® vPro™ and Intel® Centrino® Pro Processor Technology Quick Start Guide Contents Preface.................................................................................................................................3 Intended Audience....................................................................................................................................................................................3 What This Document Contains ...........................................................................................................................................................3 Process Overview..............................................................................................................4 Section 1: Deciding Which Provisioning Mode to Use .............................................5 Where do I go from here? .....................................................................................................................................................................5 Section 2 – Deploying Intel® vPro Using SMB (Basic) Mode Provisioning ............6 Process Flowchart....................................................................................................................................................................................6 -

Alpine Start Advising Response to Proposed Amendment 3 to the .COM Registry Agreement Greg Rafert, Ph.D. February 14, 2020
Alpine Start Advising Response to Proposed Amendment 3 to the .COM Registry Agreement Greg Rafert, Ph.D. February 14, 2020 I. Executive Summary 1. This comment provides an economic analysis of Verisign, Inc.’s (Verisign) proposed price increase for .COM registrations. Based on my training as an economist, review of the available evidence, and experience with ICANN and the TLD marketplace, I conclude that there is no economic rationale for Verisign to increase prices for .COM and that increased prices will very likely harm consumers: In the face of heightened competition, which has been provided as one reason for increasing .COM pricing, economic theory and empirical economic studies predict that a firm would typically lower, not increase, prices. To my knowledge, Verisign has not provided a rationale as to why increased competition would require it to increase prices for .COM. Verisign’s gross profit and operating margins have grown significantly over time and are currently high relative to other firms. While not demonstrative as to whether Verisign has market power in the TLD Alpine Start Advising 1 marketplace, they do suggest that changes in Verisign’s costs are not driving Verisign’s interest in increasing prices for .COM. An increase in the price of .COM registrations will harm consumers worldwide, as consumers are unlikely to switch to other, less expensive TLDs due to the high costs associated with switching from a .COM domain. While Verisign may argue that it will use increased revenues from .COM price increases to further improve the security and stability of the internet, thus benefiting consumers, this is unlikely.