Secure Exchange of Information in Electronic Health Records Alejandro Flores University of Wollongong
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linux: Come E Perchх
ÄÒÙÜ Ô ©2007 mcz 12 luglio 2008 ½º I 1. Indice II ½º Á ¾º ¿º ÈÖÞÓÒ ½ º È ÄÒÙÜ ¿ º ÔÔÖÓÓÒÑÒØÓ º ÖÒÞ ×Ó×ØÒÞÐ ÏÒÓÛ× ¾½ º ÄÒÙÜ ÕÙÐ ×ØÖÙÞÓÒ ¾ º ÄÒÙÜ ÀÖÛÖ ×ÙÔÔ ÓÖØØÓ ¾ º È Ð ÖÒÞ ØÖ ÖÓ ÓØ Ù×Ö ¿½ ½¼º ÄÒÙÜ × Ò×ØÐÐ ¿¿ ½½º ÓÑ × Ò×ØÐÐÒÓ ÔÖÓÖÑÑ ¿ ½¾º ÒÓÒ ØÖÓÚÓ ÒÐ ×ØÓ ÐÐ ×ØÖÙÞÓÒ ¿ ½¿º Ó׳ ÙÒÓ ¿ ½º ÓÑ × Ð ××ØÑ ½º ÓÑ Ð ½º Ð× Ñ ½º Ð Ñ ØÐ ¿ ½º ÐÓ ½º ÓÑ × Ò×ØÐÐ Ð ×ØÑÔÒØ ¾¼º ÓÑ ÐØØÖ¸ Ø×Ø ÐÖ III Indice ¾½º ÓÑ ÚÖ Ð ØÐÚ×ÓÒ ¿ 21.1. Televisioneanalogica . 63 21.2. Televisione digitale (terrestre o satellitare) . ....... 64 ¾¾º ÐÑØ ¾¿º Ä 23.1. Fotoritocco ............................. 67 23.2. Grafica3D.............................. 67 23.3. Disegnovettoriale-CAD . 69 23.4.Filtricoloreecalibrazionecolori . .. 69 ¾º ×ÖÚ Ð ½ 24.1.Vari.................................. 72 24.2. Navigazionedirectoriesefiles . 73 24.3. CopiaCD .............................. 74 24.4. Editaretesto............................. 74 24.5.RPM ................................. 75 ¾º ×ÑÔ Ô ´ËÐе 25.1.Montareundiscoounapenna . 77 25.2. Trovareunfilenelsistema . 79 25.3.Vedereilcontenutodiunfile . 79 25.4.Alias ................................. 80 ¾º × ÚÓÐ×× ÔÖÓÖÑÑÖ ½ ¾º ÖÓÛ×Ö¸ ÑÐ ººº ¿ ¾º ÖÛÐРгÒØÚÖÙ× Ð ÑØØÑÓ ¾º ÄÒÙÜ ½ ¿¼º ÓÑ ØÖÓÚÖ ÙØÓ ÖÖÑÒØ ¿ ¿½º Ð Ø×ØÙÐ Ô Ö Ð ×ØÓÔ ÄÒÙÜ ¿¾º ´ÃµÍÙÒØÙ¸ ÙÒ ×ØÖÙÞÓÒ ÑÓÐØÓ ÑØ ¿¿º ËÙÜ ÙÒ³ÓØØÑ ×ØÖÙÞÓÒ ÄÒÙÜ ½¼½ ¿º Á Ó Ò ÄÒÙÜ ½¼ ¿º ÃÓÒÕÙÖÓÖ¸ ÕÙ×ØÓ ½¼ ¿º ÃÓÒÕÙÖÓÖ¸ Ñ ØÒØÓ Ô Ö ½½¿ 36.1.Unaprimaocchiata . .114 36.2.ImenudiKonqueror . .115 36.3.Configurazione . .116 IV Indice 36.4.Alcuniesempidiviste . 116 36.5.Iservizidimenu(ServiceMenu) . 119 ¿º ÃÓÒÕÙÖÓÖ Ø ½¾¿ ¿º à ÙÒ ÖÖÒØ ½¾ ¿º à ÙÒ ÐÙ×ÓÒ ½¿½ ¼º ÓÒÖÓÒØÓ Ò×ØÐÐÞÓÒ ÏÒÓÛ×È ÃÍÙÒØÙ º½¼ ½¿¿ 40.1. -
PDF File, 212 KB
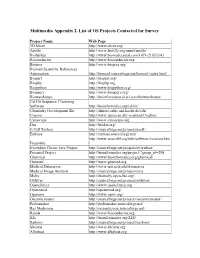
Multimedia Appendix 2. List of OS Projects Contacted for Survey Project Name Web Page 3D Slicer http://www.slicer.org/ Apollo http://www.fruitfly.org/annot/apollo/ Biobuilder http://www.biomedcentral.com/1471-2105/5/43 Bioconductor http://www.bioconductor.org Biojava http://www.biojava.org/ Biomail Scientific References Automation http://biomail.sourceforge.net/biomail/index.html Bioperl http://bioperl.org/ Biophp http://biophp.org Biopython http://www.biopython.org/ Bioquery http://www.bioquery.org/ Biowarehouse http://bioinformatics.ai.sri.com/biowarehouse/ Cd-Hit Sequence Clustering Software http://bioinformatics.org/cd-hit/ Chemistry Development Kit http://almost.cubic.uni-koeln.de/cdk/ Coasim http://www.daimi.au.dk/~mailund/CoaSim/ Cytoscape http://www.cytoscape.org Das http://biodas.org/ E-Cell System http://sourceforge.net/projects/ecell/ Emboss http://emboss.sourceforge.net/ http://www.ensembl.org/info/software/versions.htm Ensemble l Eviewbox Dicom Java Project http://sourceforge.net/projects/eviewbox/ Freemed Project http://bioinformatics.org/project/?group_id=298 Ghemical http://www.bioinformatics.org/ghemical/ Gnumed http://www.gnumed.org Medical Dataserver http://www.mii.ucla.edu/dataserver Medical Image Analysis http://sourceforge.net/projects/mia Moby http://biomoby.open-bio.org/ Olduvai http://sourceforge.net/projects/olduvai/ Openclinica http://www.openclinica.org Openemed http://openemed.org/ Openemr http://www.oemr.org/ Oscarmcmaster http://sourceforge.net/projects/oscarmcmaster/ Probemaker http://probemaker.sourceforge.net/ -

Comparison of Open-Source Electronic Health Record Systems Based on Functional and User Performance Criteria
Original Article Healthc Inform Res. 2019 April;25(2):89-98. https://doi.org/10.4258/hir.2019.25.2.89 pISSN 2093-3681 • eISSN 2093-369X Comparison of Open-Source Electronic Health Record Systems Based on Functional and User Performance Criteria Saptarshi Purkayastha1, Roshini Allam1, Pallavi Maity1, Judy W. Gichoya2 1Department of BioHealth Informatics, Indiana University–Purdue University Indianapolis, Indianapolis, IN, USA 2Dotter Institute, Oregon Health and Science University, Portland, OR, USA Objectives: Open-source Electronic Health Record (EHR) systems have gained importance. The main aim of our research is to guide organizational choice by comparing the features, functionality, and user-facing system performance of the five most popular open-source EHR systems. Methods: We performed qualitative content analysis with a directed approach on recently published literature (2012–2017) to develop an integrated set of criteria to compare the EHR systems. The functional criteria are an integration of the literature, meaningful use criteria, and the Institute of Medicine’s functional requirements of EHR, whereas the user-facing system performance is based on the time required to perform basic tasks within the EHR system. Results: Based on the Alexa web ranking and Google Trends, the five most popular EHR systems at the time of our study were OSHERA VistA, GNU Health, the Open Medical Record System (OpenMRS), Open Electronic Medical Record (OpenEMR), and OpenEHR. We also found the trends in popularity of the EHR systems and the locations where they were more popular than others. OpenEMR met all the 32 functional criteria, OSHERA VistA met 28, OpenMRS met 12 fully and 11 partially, OpenEHR-based EHR met 10 fully and 3 partially, and GNU Health met the least with only 10 criteria fully and 2 partially. -
Step-By-Step Install Guide OSCAR Mcmaster CMS on Linux Ubuntu 10.04 LTS (Lucid Lynx)
Global Open Versity eHealth Labs Install Guide OSCAR McMaster CMS on Linux Ubuntu 10.04 LTS v1.5 Global Open Versity e-Health Management Systems Hands-on Labs Training Manual Step-by-Step Install Guide OSCAR McMaster CMS on Linux Ubuntu 10.04 LTS (Lucid Lynx) Kefa Rabah Global Open Versity, Vancouver Canada [email protected] www.globalopenversity.org Table of Contents Page No. STEP-BY-STEP INSTALL GUIDE OSCAR MCMASTER CMS ON LINUX UBUNTU 10.04 LTS 3 1.0 Introduction 3 Part 1: Install & Configure Linux Ubuntu 10.04 LTS Desktop 4 Step 1: Getting Started & Hardware Pre-requisites 4 Step 2: Install Linux Ubuntu 10.04 LTS 4 Step 3: Update Ubuntu 10.04 Operating Systems 4 Part 2: Installing OSCAR McMaster CMS on Linux Ubuntu 8.04 LTS Server 5 Step 1: Preamble 5 Part 3: Installing the Infrastructure Packages 6 Step 1: Install OpenSSH Package 6 Step 2: Install Sun-Java6-JDK Package 7 Step 3: Install Ant Package 8 Step 4: Install MySQL Database Server Package 8 Step 5: Install Apache Tomcat 6 Package 9 Step 6: Install Pretty Good Privacy (PGP) Package 9 Step 7: Install CVS 10 Step 8: Install PostgreSQL database server 10 Step 9: Install UNZIP Package 10 Step 10: Install Network Time Protocol (NTP) Service 11 Step 11: Reboot the server 11 Step 12: Configuring the Base Packages 11 Step 13: Configuring Tomcat6 12 Step 14: Secure Apache Tomcat6 using SSL 13 Part 5: Install OSCAR CMS Server 15 Step 1: Download & Install OSCAR 15 Step 2: Create OSCAR Database on MySQL 16 Part 6: Enabling New eCharts 18 Step 1: Enable eChart 18 Part 7: Drugref2/3 -

LIFE Packages
LIFE packages Index Office automation Desktop Internet Server Web developpement Tele centers Emulation Health centers Graphics High Schools Utilities Teachers Multimedia Tertiary schools Programming Database Games Documentation Internet - Firefox - Browser - Epiphany - Nautilus - Ftp client - gFTP - Evolution - Mail client - Thunderbird - Internet messaging - Gaim - Gaim - IRC - XChat - Gaim - VoIP - Skype - Videomeeting - Gnome meeting - GnomeBittorent - P2P - aMule - Firefox - Download manager - d4x - Telnet - Telnet Web developpement - Quanta - Bluefish - HTML editor - Nvu - Any text editor - HTML galerie - Album - Web server - XAMPP - Collaborative publishing system - Spip Desktop - Gnome - Desktop - Kde - Xfce Graphics - Advanced image editor - The Gimp - KolourPaint - Simple image editor - gPaint - TuxPaint - CinePaint - Video editor - Kino - OpenOffice Draw - Vector vraphics editor - Inkscape - Dia - Diagram editor - Kivio - Electrical CAD - Electric - 3D modeller/render - Blender - CAD system - QCad Utilities - Calculator - gCalcTool - gEdit - gxEdit - Text editor - eMacs21 - Leafpad - Application finder - Xfce4-appfinder - Desktop search tool - Beagle - File explorer - Nautilus -Archive manager - File-Roller - Nautilus CD Burner - CD burner - K3B - GnomeBaker - Synaptic - System updates - apt-get - IPtables - Firewall - FireStarter - BackupPC - Backup - Amanda - gnome-terminal - Terminal - xTerm - xTerminal - Scanner - Xsane - Partition editor - gParted - Making image of disks - Partitimage - Mirroring over network - UDP Cast -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

OSS Alphabetical List and Software Identification
Annex: OSS Alphabetical list and Software identification Software Short description Page A2ps a2ps formats files for printing on a PostScript printer. 149 AbiWord Open source word processor. 122 AIDE Advanced Intrusion Detection Environment. Free replacement for Tripwire(tm). It does the same 53 things are Tripwire(tm) and more. Alliance Complete set of CAD tools for the specification, design and validation of digital VLSI circuits. 114 Amanda Backup utility. 134 Apache Free HTTP (Web) server which is used by over 50% of all web servers worldwide. 106 Balsa Balsa is the official GNOME mail client. 96 Bash The Bourne Again Shell. It's compatible with the Unix `sh' and offers many extensions found in 147 `csh' and `ksh'. Bayonne Multi-line voice telephony server. 58 Bind BIND "Berkeley Internet Name Daemon", and is the Internet de-facto standard program for 95 turning host names into IP addresses. Bison General-purpose parser generator. 77 BSD operating FreeBSD is an advanced BSD UNIX operating system. 144 systems C Library The GNU C library is used as the C library in the GNU system and most newer systems with the 68 Linux kernel. CAPA Computer Aided Personal Approach. Network system for learning, teaching, assessment and 131 administration. CVS A version control system keeps a history of the changes made to a set of files. 78 DDD DDD is a graphical front-end for GDB and other command-line debuggers. 79 Diald Diald is an intelligent link management tool originally named for its ability to control dial-on- 50 demand network connections. Dosemu DOSEMU stands for DOS Emulation, and is a linux application that enables the Linux OS to run 138 many DOS programs - including some Electric Sophisticated electrical CAD system that can handle many forms of circuit design. -

Upgrade Issues
Upgrade issues Graph of new conflicts libsiloh5-0 libhdf5-lam-1.8.4 (x 3) xul-ext-dispmua (x 2) liboss4-salsa-asound2 (x 2) why sysklogd console-cyrillic (x 9) libxqilla-dev libxerces-c2-dev iceape xul-ext-adblock-plus gnat-4.4 pcscada-dbg Explanations of conflicts pcscada-dbg libpcscada2-dev gnat-4.6 gnat-4.4 Similar to gnat-4.4: libpolyorb1-dev libapq-postgresql1-dev adacontrol libxmlada3.2-dev libapq1-dev libaws-bin libtexttools2-dev libpolyorb-dbg libnarval1-dev libgnat-4.4-dbg libapq-dbg libncursesada1-dev libtemplates-parser11.5-dev asis-programs libgnadeodbc1-dev libalog-base-dbg liblog4ada1-dev libgnomeada2.14.2-dbg libgnomeada2.14.2-dev adabrowse libgnadecommon1-dev libgnatvsn4.4-dbg libgnatvsn4.4-dev libflorist2009-dev libopentoken2-dev libgnadesqlite3-1-dev libnarval-dbg libalog1-full-dev adacgi0 libalog0.3-base libasis2008-dbg libxmlezout1-dev libasis2008-dev libgnatvsn-dev libalog0.3-full libaws2.7-dev libgmpada2-dev libgtkada2.14.2-dbg libgtkada2.14.2-dev libasis2008 ghdl libgnatprj-dev gnat libgnatprj4.4-dbg libgnatprj4.4-dev libaunit1-dev libadasockets3-dev libalog1-base-dev libapq-postgresql-dbg libalog-full-dbg Weight: 5 Problematic packages: pcscada-dbg hostapd initscripts sysklogd Weight: 993 Problematic packages: hostapd | initscripts initscripts sysklogd Similar to initscripts: conglomerate libnet-akamai-perl erlang-base screenlets xlbiff plasma-widget-yawp-dbg fso-config- general gforge-mta-courier libnet-jifty-perl bind9 libplack-middleware-session-perl libmail-listdetector-perl masqmail libcomedi0 taxbird ukopp -

Report on Existing Open-Source Electronic Medical Records
UCAM-CL-TR-768 Technical Report ISSN 1476-2986 Number 768 Computer Laboratory Report on existing open-source electronic medical records Cecily Morrison, Adona Iosif, Miklos Danka February 2010 15 JJ Thomson Avenue Cambridge CB3 0FD United Kingdom phone +44 1223 763500 http://www.cl.cam.ac.uk/ c 2010 Cecily Morrison, Adona Iosif, Miklos Danka Some figures in this document are best viewed in colour. If you received a black-and-white copy, please consult the online version if necessary. Technical reports published by the University of Cambridge Computer Laboratory are freely available via the Internet: http://www.cl.cam.ac.uk/techreports/ ISSN 1476-2986 INTRODUCTION One of the responsibilities of the World Health Organisation (WHO) is to contain outbreaks of emerging viral disease, such as Ebola or H1N1 (swine flu). To more quickly tackle outbreaks and perhaps even prevent the spread of disease, the WHO organisation needs ways to gain reliable data about diseases as soon as an outbreak is identified as well as to disseminate guidelines of care based on that data. Information Technology (IT) has been considered a good option to do this, although myriad problems of data standards has slowed the process. Recently experts on emerging viral diseases met as part of the EViDence Project to discuss and stipulate what such an IT system might do. This report, an adjunct to that meeting, considers whether there is an existing open-source Clinical Information Systems (CIS) that meets these requirements. EViDence project In October 2009, clinical experts -

Application of Open-Source Enterprise Information System Modules: an Empirical Study
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln Dissertations, Theses, and Student Research from the College of Business Business, College of Summer 7-20-2010 APPLICATION OF OPEN-SOURCE ENTERPRISE INFORMATION SYSTEM MODULES: AN EMPIRICAL STUDY Sang-Heui Lee University of Nebraska-Lincoln Follow this and additional works at: https://digitalcommons.unl.edu/businessdiss Part of the Management Information Systems Commons, Other Business Commons, and the Technology and Innovation Commons Lee, Sang-Heui, "APPLICATION OF OPEN-SOURCE ENTERPRISE INFORMATION SYSTEM MODULES: AN EMPIRICAL STUDY" (2010). Dissertations, Theses, and Student Research from the College of Business. 13. https://digitalcommons.unl.edu/businessdiss/13 This Article is brought to you for free and open access by the Business, College of at DigitalCommons@University of Nebraska - Lincoln. It has been accepted for inclusion in Dissertations, Theses, and Student Research from the College of Business by an authorized administrator of DigitalCommons@University of Nebraska - Lincoln. APPLICATION OF OPEN-SOURCE ENTERPRISE INFORMATION SYSTEM MODULES: AN EMPIRICAL STUDY by Sang-Heui Lee A DISSERTATION Presented to the Faculty of The Graduate College at the University of Nebraska In Partial Fulfillment of Requirements For the Degree of Doctor of Philosophy Major: Interdepartmental Area of Business (Management) Under the Supervision of Professor Sang M. Lee Lincoln, Nebraska July 2010 APPLICATION OF OPEN-SOURCE ENTERPRISE INFORMATION SYSTEM MODULES: AN EMPIRICAL STUDY Sang-Heui Lee, Ph.D. University of Nebraska, 2010 Advisor: Sang M. Lee Although there have been a number of studies on large scale implementation of proprietary enterprise information systems (EIS), open-source software (OSS) for EIS has received limited attention in spite of its potential as a disruptive innovation. -

Full Circle Magazine #27 1 Contents ^ Full Circle Program in Python - Pt1 P.07 Ubuntu Women P.24
full circle ISSUE #27 - July 2009 PROGRAM IN PYTHON PART 1 full circle magazine #27 1 contents ^ full circle Program In Python - Pt1 p.07 Ubuntu Women p.24 Inkscape - Part 4 p.11 Ubuntu Games p.26 My Story p.17 MOTU Interview p.21 Scan To PDF/DJVU p.13 Command & Conquer p.05 Associate A File-Type p.16 Review p.19 Letters p.22 Top 5 p.30 The articles contained in this magazine are released under the Creative Commons Attribution-Share Alike 3.0 Unported license. This means you can adapt, copy, distribute and transmit the articles but only under the following conditions: You must attribute the work to the original author in some way (at least a name, email or URL) and to this magazine by name ('full circle magazine') and the URL www.fullcirclemagazine.org (but not attribute the article(s) in any way that suggests that they endorse you or your use of the work). If you alter, transform, or build upon this work, you must distribute the resulting work under the same, similar or a compatible license. full circle magazine #27 2 contents ^ EDITORIAL This magazine was created using : Welcome to another issue of Full Circle magazine. nd welcome to another new series! ! Yes, last month I promised a new series on LAMP servers, but since so many people requested Python in our survey, I gave it priority. I don't like to have too many series' running at once, so maybe when the Inkscape series comes to Aan end, I'll start the LAMP series. -

Strong Dependencies Between Software Components
Specific Targeted Research Project Contract no.214898 Seventh Framework Programme: FP7-ICT-2007-1 Technical Report 0002 MANCOOSI Managing the Complexity of the Open Source Infrastructure Strong Dependencies between Software Components Pietro Abate ([email protected]) Jaap Boender ([email protected]) Roberto Di Cosmo ([email protected]) Stefano Zacchiroli ([email protected]) Universit`eParis Diderot, PPS UMR 7126, Paris, France May 24, 2009 Web site: www.mancoosi.org Contents 1 Introduction . .2 2 Strong dependencies . .3 3 Strong dependencies in Debian . .7 3.1 Strong vs direct sensitivity: exceptions . .9 3.2 Using strong dominance to cluster data . 11 3.3 Debian is a small world . 11 4 Efficient computation . 12 5 Applications . 13 6 Related works . 16 7 Conclusion and future work . 17 8 Acknowledgements . 18 A Case Study: Evaluation of debian structure . 21 Abstract Component-based systems often describe context requirements in terms of explicit inter-component dependencies. Studying large instances of such systems|such as free and open source software (FOSS) distributions|in terms of declared dependencies between packages is appealing. It is however also misleading when the language to express dependencies is as expressive as boolean formulae, which is often the case. In such settings, a more appropriate notion of component dependency exists: strong dependency. This paper introduces such notion as a first step towards modeling semantic, rather then syntactic, inter-component relationships. Furthermore, a notion of component sensitivity is derived from strong dependencies, with ap- plications to quality assurance and to the evaluation of upgrade risks. An empirical study of strong dependencies and sensitivity is presented, in the context of one of the largest, freely available, component-based system.