A Hybrid Interface Recovery Method for Android Kernels Fuzzing335
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Strategies of Yota (Scartel) - 4G Operator in Russian Federation
Netra Pal Singh1 JEL: L11 2 Manisha Kaushik DOI: 10.5937/industrija41-4700 UDK: 621.39:339.13(470) ;005.21:621.39 Professional Paper Strategies of Yota (Scartel) - 4G Operator in Russian Federation Article history Received: 20 September 2013 Sent for revision: 20 October 2013 Received in revised form: 13 November 2013 Accepted: 17 November 2013 Available online: 26 November 2013 Abstract: Russian Federation is one of the high growth markets for telecom services which are expected to reach $48.5 billion by 2013. With the granting of 4G LTE licenses, it is expected that 4G market in Russian Federation will be dominated by four cellular operators, i.e., MTS, Beeline, and MegaFon, Rostelecom along with two new startups, i.e., Osnova Telecom and Red Tel- ecom. In addition, other companies such as Yota, Synterra, COMSTAR, Freshtel etc. are also operating in Russian WiMax & LTE telecom market to provide similar services. This paper is an attempt to analyze some of the pa- rameters of LTE turn Yota WiMax Telecom Operator in Russian Federation. The paper covers current achievements of Yota, its reach in Russian Federa- tion, its network size & technology, its services, expansion plans for future, strategies for survival (in question) in a highly competitive market of big com- panies, and its ultimate fate. Keywords: WiMax, Long Term Evolution (LTE), Yota, Russian Markets, MTS, Beeline, MegaFon, Rostelecom. Strategija Yota (Scartel) – 4G operatera u Ruskoj Federaciji Apstrakt: Ruska Federacija je jedno od brzo rastućih tržišta telekomunikacionih usluga za koje se očekuje da će dostići $ 48.5 milijardi dolara tokom 2013. -
Android Devices
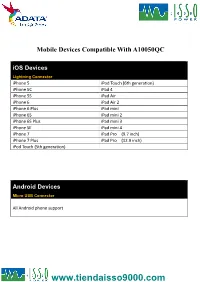
Mobile Devices Compatible With A10050QC iOS Devices Lightning Connector iPhone 5 iPod Touch (6th generation) iPhone 5C iPad 4 iPhone 5S iPad Air iPhone 6 iPad Air 2 iPhone 6 Plus iPad mini iPhone 6S iPad mini 2 iPhone 6S Plus iPad mini 3 iPhone SE iPad mini 4 iPhone 7 iPad Pro (9.7 inch) iPhone 7 Plus iPad Pro (12.9 inch) iPod Touch (5th generation) Android Devices Micro USB Connector All Android phone support Smartphone With Quick Charge 3.0 Technology Type-C Connector Asus ZenFone 3 LG V20 TCL Idol 4S Asus ZenFone 3 Deluxe NuAns NEO VIVO Xplay6 Asus ZenFone 3 Ultra Nubia Z11 Max Wiley Fox Swift 2 Alcatel Idol 4 Nubia Z11miniS Xiaomi Mi 5 Alcatel Idol 4S Nubia Z11 Xiaomi Mi 5s General Mobile GM5+ Qiku Q5 Xiaomi Mi 5s Plus HP Elite x3 Qiku Q5 Plus Xiaomi Mi Note 2 LeEco Le MAX 2 Smartisan M1 Xiaomi MIX LeEco (LeTV) Le MAX Pro Smartisan M1L ZTE Axon 7 Max LeEco Le Pro 3 Sony Xperia XZ ZTE Axon 7 Lenovo ZUK Z2 Pro TCL Idol 4-Pro Smartphone With Quick Charge 3.0 Technology Micro USB Connector HTC One A9 Vodafone Smart platinum 7 Qiku N45 Wiley Fox Swift Sugar F7 Xiaomi Mi Max Compatible With Quick Charge 3.0 Technology Micro USB Connector Asus Zenfone 2 New Moto X by Motorola Sony Xperia Z4 BlackBerry Priv Nextbit Robin Sony Xperia Z4 Tablet Disney Mobile on docomo Panasonic CM-1 Sony Xperia Z5 Droid Turbo by Motorola Ramos Mos1 Sony Xperia Z5 Compact Eben 8848 Samsung Galaxy A8 Sony Xperia Z5 Premium (KDDI Japan) EE 4GEE WiFi (MiFi) Samsung Galaxy Note 4 Vertu Signature Touch Fujitsu Arrows Samsung Galaxy Note 5 Vestel Venus V3 5070 Fujitsu -

The Role of Greek Culture Representation in Socio-Economic Development of the Southern Regions of Russia
European Research Studies Journal Volume XXI, Special Issue 1, 2018 pp. 136 - 147 The Role of Greek Culture Representation in Socio-Economic Development of the Southern Regions of Russia T.V. Evsyukova1, I.G. Barabanova2, O.V. Glukhova3, E.A. Cherednikova4 Abstract: This article researches how the Greek lingvoculture represented in onomasticon of the South of Russia. The South Russian anthroponyms, toponyms and pragmatonyms are considered in this article and how they verbalize the most important values and ideological views. It is proved in the article that the key concepts of the Greek lingvoculture such as: “Peace”, “Faith”, “Love”, “Heroism”, “Knowledge”, “Alphabet”, “Power”, “Charismatic person” and “Craft” are highly concentrated in the onomastic lexis of the researched region. The mentioned above concepts due to their specific pragmatic orientation are represented at different extend. Keywords: Culture, linguoculture, onomastics, concept anthroponym, toponym, pragmatonim. 1D.Sc. in Linguistics, Professor, Department of Linguistics and Intercultural Communication, Rostov State University of Economics, Rostov-on-Don, Russian Federation. 2Ph.D. in Linguistics, Associate Professor, Department of Linguistics and Intercultural Communication, Rostov State University of Economics, Rostov-on-Don, Russian Federation. 3Lecturer, Department of Linguistics and Intercultural Communication, Rostov State University of Economics, Rostov-on-Don, Russian Federation, E-mail: [email protected] 4Ph.D., Associate Professor, Department of Linguistics and Intercultural Communication, Rostov State University of Economics, Rostov-on-Don, Russian Federation. T.V. Evsyukova, I.G. Barabanova, O.V. Glukhova, E.A. Cherednikova 137 1. Introduction There is unlikely to be any other culture that influenced so much on the formation of other European cultures, as the Greek culture. -

Annual Report 2012 Annual Report
Annual Report 2012 Annual Report Annual Report www.AR2012.megafon.ru/en Chief Executive Officer I.V. Tavrin (signature) Chief Accountant L.N. Strelkina (signature) Annual Report 2012 CONTENTS MEGAFON MegaFon’s business model and key 2012 results 4 Finanсial and operational highlights for 2012 2012 marked a new 8 Our business page in MegaFon’s history STRATEGY Management’s overview of the results p. 14 and vision for growth 14 Letter of the Chairman of the Board LETTER 18 Letter of the CEO OF THE CHAIRMAN 22 Strategy OF THE BOARD 24 The Russian market in 2012 РERFORMANCE MegaFon’s operating and financial results 30 Review of operations 48 Finanсial review GOVERNANCE Free cash flow reached RUB 70.8 billion Corporate governance and risk management systems 52 Risk management p. 48 56 Corporate governance 69 Shareholder’s equity FINANCIAL REVIEW SUSTAINABILITY Our mission is Responsibility to employees to bring Russia and community together through 74 Sustainable development communication technology APPENDICES 82 Management responsibility statement 82 US GAAP Consolidated Financial Statements p. 74 128 Appendices SUSTAINABLE 160 Contacts DEVELOPMENT generated at BeQRious.com This Annual Report focuses principally on our operations in the Russian Federation. While we have operating subsidiaries in the For more information Republics of Tajikistan (TT mobile), Abkhazia (AQUafon-GSM) about MegaFon, see and South Ossetia (OSTELEKOM), they generate only 1% of the company website. our total consolidated revenues. Unless otherwise specifically The report is also indicated, this Annual Report provides consolidated financial and available online operational data www.AR2012.megafon.ru/en Approved Annual General Shareholders Meeting OJSC “MegaFon” Minutes dated 28.06.2013 Preliminarily Approved Board of Directors OJSC “MegaFon” Minutes № 192 (256) dated 14.05.2013 NATIONWIDE 4G AGREEMENT WITH NEW CAPEX LICENCE YOTA ON 4G NETWORK FRAMEWORK P. -

Russian Games Market Report.Pdf
Foreword Following Newzoo’s free 42-page report on China and its games market, this report focuses on Russia. This report aims to provide understanding of the Russian market by putting it in a broader perspective. Russia is a dynamic and rapidly growing games We hope this helps to familiarize our clients and friends market, currently number 12 in the world in terms of around the globe with the intricacies of the Russian revenues generated. It is quickly becoming one of market. the most important players in the industry and its complexity warrants further attention and This report begins with some basic information on examination. The Russian market differs from its demographics, politics and cultural context, as well as European counterparts in many ways and this can be brief descriptions of the media, entertainment, telecoms traced to cultural and economic traditions, which in and internet sectors. It also contains short profiles of the some cases are comparable to their Asian key local players in these sectors, including the leading neighbours. local app stores, Search Engines and Social Networks. Russia has been a part of the Newzoo portfolio since In the second part of the report we move onto describe 2011, allowing us to witness first-hand the the games market in more detail, incorporating data unprecedented growth and potential within this from our own primary consumer research findings as market. We have accumulated a vast array of insights well as data from third party sources. on both the Russian consumers and the companies that are feeding this growth, allowing us to assist our clients with access to, and interpretation of, data on We also provide brief profiles of the top games in Russia, the Russia games market. -

Program Analysis Based Approaches to Ensure Security and Safety of Emerging Software Platforms
Program Analysis Based Approaches to Ensure Security and Safety of Emerging Software Platforms by Yunhan Jia A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Computer Science and Engineering) in The University of Michigan 2018 Doctoral Committee: Professor Z. Morley Mao, Chair Professor Atul Prakash Assistant Professor Zhiyun Qian, University of California Riverside Assistant Professor Florian Schaub Yunhan Jia [email protected] ORCID iD: 0000-0003-2809-5534 c Yunhan Jia 2018 All Rights Reserved To my parents, my grandparents and Xiyu ii ACKNOWLEDGEMENTS Five years have passed since I moved into the Northwood cabin in Ann Arbor to chase my dream of obtaining a Ph.D. degree. Now, looking back from the end of this road, there are so many people I would like to thank, who are an indispensable part of this wonderful journey full of passion, love, learning, and growth. Foremost, I would like to gratefully thank my advisor, Professor Zhuoqing Morley Mao for believing and investing in me. Her constant support was a definite factor in bringing this dissertation to its completion. Whenever I got lost or stucked in my research, she would always keep a clear big picture of things in mind and point me to the right direction. With her guidance and support over these years, I have grown from a rookie to a researcher that can independently conduct research. Besides my advisor, I would like to thank my thesis committee, Professor Atul Prakash, Professor Zhiyun Qian, and Professor Florian Schaub for their insightful suggestions, com- ments, and support. -

Layered Mobile Device Architecture
ISSN (e): 2250 – 3005 || Volume, 08 || Issue,10|| October – 2018 || International Journal of Computational Engineering Research (IJCER) Layered Mobile Device Architecture 1Shinto Kurian 2Dr.K.Nirmala K, Research Scholar(Reg.No:PhD/10/PTE/1/2017, Madras University), Quaid-E-Millath College for Women, Chennai - 600 002, Tamilnadu,India. Assoc. Professor,Dept. of Computer Science, Quaid-E-Millath College for Women, Chennai - 600 002, Tamilnadu,India Corresponding Author: Shinto Kurian ABSTRACT Mobile device structure is organised in a layered architecture from electronic components to application user interface. Based on various functionalities, the mobile devices are separated into multiple layers. Each layer has well defined boundaries and interacts with each other using certain protocols. The layered separation helps the devices to segregate the functionalities in stabilized and secured manner. Depending on manufacture, the components in each layer change. Most of the mobile devices are follow a standard architecture but the components and methodologies used in each layer have differences. The degree of smoothness between the layers directly proportionate with user friendliness of the mobile device. KEYWORDS: Mobile Device, Operating system, Software, Hardware, BIOS, Firmware, User Interface. ----------------------------------------------------------------------------------------------------------------------------- ---------- Date of Submission: 15-12-2018 Date of acceptance: 31-12-2018 --------------------------------------------------------------------------------------------------------------------------------------------------- -

Impresions of Soviet Education: a Second Look
DOCUMENT RESUME ED 084 957 HE 004 835 AUTHOR Lane,'George B., Ed. TITLE Impresions of Soviet Education: A Second Look. A Report of the Educational Staff Seminar Study Tour, Novem4er 16-30, 1972. INSTITUTION George Washington Univ., Washington, D.C. Inst. for Educational Leadership. PUB DATE Nov 72 NOTE 108p. EDRS PRICE MF-$0.65 HC-$6.58 DESCRIPTORS *Adult Education; *Cultural Awareness; *Early Childhood Education; Elementary Education; English Education; *Higher Education; *International Education; Secondary Education IDENTIFIERS *Soviet Union ABSTRACT This document presents the impressions of the edudational Staff Seminar Study tour of the Soviet Union. After the introduction and itinerary, the first chapter deals with the soviet scere including sections on religion, ideology, the social system and the soviet woman. The second chapter concerns the early childhood and preschool education of soviet youngsters, including daycare, student discipline, and early childhood education research. The third chapter concerns elementary and secondary education including specialized English language schools, pioneer palaces, the exceptional student and the slow learner, educational technology, and vocational-technical schools. The fourth chapter deals with higher education, adult eduCation and research, with sections on leadership goals, foreign literature, the Moscow State University, and the Institute of Adult Education Research. Teacher training, scientific and educational information dissemination, and perspectives on soviet health concern the -

RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.0 | March 2016 UFED LOGICAL ANALYZER
NOW SUPPORTING 19,203 DEVICE PROFILES +1,528 APP VERSIONS UFED TOUCH, UFED 4PC, RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.0 | March 2016 UFED LOGICAL ANALYZER COMMON/KNOWN HIGHLIGHTS System Images IMAGE FILTER ◼ Temporary root (ADB) solution for selected Android Focus on the relevant media files and devices running OS 4.3-5.1.1 – this capability enables file get to the evidence you need fast system and physical extraction methods and decoding from devices running OS 4.3-5.1.1 32-bit with ADB enabled. In addition, this capability enables extraction of apps data for logical extraction. This version EXTRACT DATA FROM BLOCKED APPS adds this capability for 110 devices and many more will First in the Industry – Access blocked application data with file be added in coming releases. system extraction ◼ Enhanced physical extraction while bypassing lock of 27 Samsung Android devices with APQ8084 chipset (Snapdragon 805), including Samsung Galaxy Note 4, Note Edge, and Note 4 Duos. This chipset was previously supported with UFED, but due to operating system EXCLUSIVE: UNIFY MULTIPLE EXTRACTIONS changes, this capability was temporarily unavailable. In the world of devices, operating system changes Merge multiple extractions in single unified report for more frequently, and thus, influence our support abilities. efficient investigations As our ongoing effort to continue to provide our customers with technological breakthroughs, Cellebrite Logical 10K items developed a new method to overcome this barrier. Physical 20K items 22K items ◼ File system and logical extraction and decoding support for iPhone SE Samsung Galaxy S7 and LG G5 devices. File System 15K items ◼ Physical extraction and decoding support for a new family of TomTom devices (including Go 1000 Point Trading, 4CQ01 Go 2505 Mm, 4CT50, 4CR52 Go Live 1015 and 4CS03 Go 2405). -

Claudia Tapia, Director IPR Policy at the Ericsson
DT: a new technological and economic paradigm Dr Claudia Tapia, Director IPR Policy All views expressed in this speech are those of the author and do not necessarily represent the views of Ericsson Ericsson at a glance NETWORKS IT MEDIA INDUSTRIES Create one network for Transform IT to accelerate Delight the TV Connect industries to a million different needs business agility consumer every day accelerate performance Worldwide mobile 42,000 Patents 40% traffic provided by 222,6 B. SEK Net Sales our networks R&D Employees Licensing Countries with 23,700 >100 agreements 180 customers Average p.a. Licensing revenues Employees 5 B. usd in R&D 10 b. Sek 111,000 Page 2 415,000,000,000 Page 3 STANDARDISATION PROCESS Early Technical Unapproved contribution investment (described in R&D in a patent) Adopted by Standard FRAND CONSENSUS in essential commitment standard patent Return on Access to the investment standard Interoperable high performance devices at a FRAND = Fair, Reasonable and Non- reasonable price DiscriminatoryPage 4 (terms and conditions) 4,000,000,000,000 Page 5 3,452,040 Page 6 3G and LTE (3GPP - 1999 – Dec. 2014 ) 262,773 Submitted contributions 43,917 Approved contributions (16,7%) Source: Signals Research Group. The Essentials of IP, from 3G through LTE Release 12, May 2015 Page 7 LTE approved Contributions for 13 WGs (2009 - Q3 2015) –Source: ABI Research COMPANY RANK Ericsson 1 Huawei 2 Nokia Networks 3 Qualcomm 4 ALU 5 ZTE 6 Samsung 7 Anritsu 8 Rohde & Schwarz 9 CATT 10 Page 8 Principles of standardisation CONSENSUS TRANSPARENCY IMPARTIALITY OPENNESS .. -

New Chips: the Potential Rollout of LTE+3G+Wifi Chips. Planning for Wimax-LTE Chips
New Chips: The Potential Rollout Of LTE+3G+Wifi Chips. Planning For WiMax-LTE Chips. Robert Syputa, Partner and Senior Advisor, Maravedis-BWA. Owner www.Maravedis.com, www.Green4G.com CLIENT CONFIDENTIAL BROADBAND WIRELESS INTELLIGENCE www.maravedis.com © 2010 Maravedis Inc. Agenda The Program General Overview of the WiMAX and LTE Market Environment The Evolving Technology and Market Landscape for LTE and WiMAX Chips Opportunities for Growth Q & A CLIENT CONFIDENTIAL BROADBAND WIRELESS INTELLIGENCE www.maravedis.com © 2010 Maravedis Inc. The Evolving Technology and Market Landscape 1. Wireless Broadband Demand has Skyrocketed 2. ‘Hot’Web Devices Drive Subscriber & Revenue Growth 3. WiMAX IC Vendors First to Market with LTE: Vendors Racing into the Market 4. Multiple-Mode WiMAX/LTE Chips to Enter 2nd Half 2010 5. WiMAX Operators Shift to LTE 6. Migration Path to WiMAX 2, and LTE CLIENT CONFIDENTIAL BROADBAND WIRELESS INTELLIGENCE www.maravedis.com © 2010 Maravedis Inc. WiMAX Industry In 2009: WiMAX Base Total WiMAX 5 million WiMAX 3.5 million new Station Sectors market size chipsets shipped WiMAX CPEs –10.9% US$1.36 billion (+332% Y-O-Y) deployed End-users want broadband wireless now Operators confused by future evolution Source: 4Ggear service 4 Selected LTE and WiMAX Key Trends - 4Ggear™ Report •WiMAX chipset •Vendors offer differentiated chipsets to address emerged markets •Aggressive chipset price: higher volume, optimized platforms •LTE chipset •Early solutions support LTE only •Early suppliers may not be the long term winners •WiMAX device •Diversified deployments of low cost CPEs, dual-mode USB dongles, and smartphones •LTE device •Demonstrators = single-mode followed by dual-mode USB dongles •4G equipment •WiMAX has established a beachhead for technological progress… •… LTE will benefit from it © 2010 Maravedis Inc. -

The Nanyan Observer No
Published by: Best Ten Campus Media Nanyan News Agency, Shenzhen Graduate School in Guangdong Province Four Pages PEKING UNIVERSITY The Nanyan Observer No. CUMU092017 Monday, 5 December. 2016 General Director: Megan Mancenido Chief Editor: Karras Lambert Managing Editor: Longjun Qin Tel: 0755-26032131 Info: [email protected] PKU Holds 8th Annual Thanksgiving Celebration comes to campus once a year. Min from the neighboring Tsinghua Macarena. Table of Contents University Graduate School. After After several weeks of groundwork a brief introduction, they invited As the Thanksgiving event's PKU Celebrates Thanksgiving..... and coordination between various the School of Transnational Law’s planning assistant, Yang Wandong schools, offices, and volunteers, Assistant Dean Christian Pangilinan of the School of Urban Planning .................................................A1 the much anticipated day had onto the stage to kick the night off Design says it was "awesome to Shenzhen Runner's Guide........... finally arrived. The Chancellor’s with the annual Thanksgiving toast. see things come together in its .................................................A2 Secretariat Office held the 8th Once again, the dinner’s turkeys own way, with everyone's effort, Annual Thanksgiving Celebration were catered by Metro in European then finally take shape in an event Financial Journalism Program...... in B-building's Moot Court. What Town, the side dishes were prepared that people enjoyed. That sense .................................................A3 originally started out as a modest by Frankie’s American Bar & Grille in of accomplishment is what made it All You Need is Ecuador............... get together to share an American Nanshan, and the peach and cherry worthwhile." tradition with Chinese friends cobblers from Baeckerei Thomas in .................................................A4 and colleagues has, over the Shekou.