Program Analysis Based Approaches to Ensure Security and Safety of Emerging Software Platforms
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Android Devices
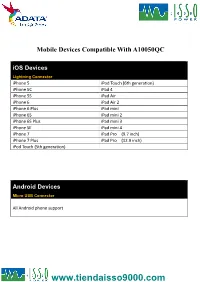
Mobile Devices Compatible With A10050QC iOS Devices Lightning Connector iPhone 5 iPod Touch (6th generation) iPhone 5C iPad 4 iPhone 5S iPad Air iPhone 6 iPad Air 2 iPhone 6 Plus iPad mini iPhone 6S iPad mini 2 iPhone 6S Plus iPad mini 3 iPhone SE iPad mini 4 iPhone 7 iPad Pro (9.7 inch) iPhone 7 Plus iPad Pro (12.9 inch) iPod Touch (5th generation) Android Devices Micro USB Connector All Android phone support Smartphone With Quick Charge 3.0 Technology Type-C Connector Asus ZenFone 3 LG V20 TCL Idol 4S Asus ZenFone 3 Deluxe NuAns NEO VIVO Xplay6 Asus ZenFone 3 Ultra Nubia Z11 Max Wiley Fox Swift 2 Alcatel Idol 4 Nubia Z11miniS Xiaomi Mi 5 Alcatel Idol 4S Nubia Z11 Xiaomi Mi 5s General Mobile GM5+ Qiku Q5 Xiaomi Mi 5s Plus HP Elite x3 Qiku Q5 Plus Xiaomi Mi Note 2 LeEco Le MAX 2 Smartisan M1 Xiaomi MIX LeEco (LeTV) Le MAX Pro Smartisan M1L ZTE Axon 7 Max LeEco Le Pro 3 Sony Xperia XZ ZTE Axon 7 Lenovo ZUK Z2 Pro TCL Idol 4-Pro Smartphone With Quick Charge 3.0 Technology Micro USB Connector HTC One A9 Vodafone Smart platinum 7 Qiku N45 Wiley Fox Swift Sugar F7 Xiaomi Mi Max Compatible With Quick Charge 3.0 Technology Micro USB Connector Asus Zenfone 2 New Moto X by Motorola Sony Xperia Z4 BlackBerry Priv Nextbit Robin Sony Xperia Z4 Tablet Disney Mobile on docomo Panasonic CM-1 Sony Xperia Z5 Droid Turbo by Motorola Ramos Mos1 Sony Xperia Z5 Compact Eben 8848 Samsung Galaxy A8 Sony Xperia Z5 Premium (KDDI Japan) EE 4GEE WiFi (MiFi) Samsung Galaxy Note 4 Vertu Signature Touch Fujitsu Arrows Samsung Galaxy Note 5 Vestel Venus V3 5070 Fujitsu -

Complete 2020 Annual Report (PDF)
2020 REPORT TO THE COMMUNITY Youth wade into Crissy Field Marsh during Project WISE in fall 2019 (See story, page 5). Crissy Field Center moves into new space at DEAR FRIEND the Tunnel Tops in 2021. We’ll improve those trails we missed so much. We’ll welcome back OF THE PARKS, our volunteers and visitors with open arms—or maybe a friendly wave. With our partners, our hat a year to start as only the second focus on making parks accessible for all—so W CEO in the history of the Golden Gate that everyone feels welcome in parks and can National Parks Conservancy. Throughout this enjoy the many health benefits of nature—is Report to the Community, we shine a light on more important now than ever. our major accomplishments of 2019. We had That’s why I’m so grateful for my first year no idea what was just around the corner. at the helm of the Parks Conservancy. I’ve I came into this job believing strongly in gotten to see the park spirit shine bright under the power of national parks to inspire and the toughest conditions. The snapshot of heal. The Bay Area shelter-in-place orders 2019 you’ll get in this report shows us what’s somehow strengthened that conviction. When possible for our long-term future, and I can’t we lose something, we miss it more than ever. wait to get there. It may take some time to And, we learn a powerful lesson in not taking recover, but with your help, our parks will it for granted. -

Self-Driving Car Autonomous System Overview
Self-Driving Car Autonomous System Overview - Industrial Electronics Engineering - Bachelors’ Thesis - Author: Daniel Casado Herráez Thesis Director: Javier Díaz Dorronsoro, PhD Thesis Supervisor: Andoni Medina, MSc San Sebastián - Donostia, June 2020 Self-Driving Car Autonomous System Overview Daniel Casado Herráez "When something is important enough, you do it even if the odds are not in your favor." - Elon Musk - 2 Self-Driving Car Autonomous System Overview Daniel Casado Herráez To my Grandfather, Family, Friends & to my supervisor Javier Díaz 3 Self-Driving Car Autonomous System Overview Daniel Casado Herráez 1. Contents 1.1. Index 1. Contents ..................................................................................................................................................... 4 1.1. Index.................................................................................................................................................. 4 1.2. Figures ............................................................................................................................................... 6 1.1. Tables ................................................................................................................................................ 7 1.2. Algorithms ........................................................................................................................................ 7 2. Abstract ..................................................................................................................................................... -

Layered Mobile Device Architecture
ISSN (e): 2250 – 3005 || Volume, 08 || Issue,10|| October – 2018 || International Journal of Computational Engineering Research (IJCER) Layered Mobile Device Architecture 1Shinto Kurian 2Dr.K.Nirmala K, Research Scholar(Reg.No:PhD/10/PTE/1/2017, Madras University), Quaid-E-Millath College for Women, Chennai - 600 002, Tamilnadu,India. Assoc. Professor,Dept. of Computer Science, Quaid-E-Millath College for Women, Chennai - 600 002, Tamilnadu,India Corresponding Author: Shinto Kurian ABSTRACT Mobile device structure is organised in a layered architecture from electronic components to application user interface. Based on various functionalities, the mobile devices are separated into multiple layers. Each layer has well defined boundaries and interacts with each other using certain protocols. The layered separation helps the devices to segregate the functionalities in stabilized and secured manner. Depending on manufacture, the components in each layer change. Most of the mobile devices are follow a standard architecture but the components and methodologies used in each layer have differences. The degree of smoothness between the layers directly proportionate with user friendliness of the mobile device. KEYWORDS: Mobile Device, Operating system, Software, Hardware, BIOS, Firmware, User Interface. ----------------------------------------------------------------------------------------------------------------------------- ---------- Date of Submission: 15-12-2018 Date of acceptance: 31-12-2018 --------------------------------------------------------------------------------------------------------------------------------------------------- -

RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.0 | March 2016 UFED LOGICAL ANALYZER
NOW SUPPORTING 19,203 DEVICE PROFILES +1,528 APP VERSIONS UFED TOUCH, UFED 4PC, RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.0 | March 2016 UFED LOGICAL ANALYZER COMMON/KNOWN HIGHLIGHTS System Images IMAGE FILTER ◼ Temporary root (ADB) solution for selected Android Focus on the relevant media files and devices running OS 4.3-5.1.1 – this capability enables file get to the evidence you need fast system and physical extraction methods and decoding from devices running OS 4.3-5.1.1 32-bit with ADB enabled. In addition, this capability enables extraction of apps data for logical extraction. This version EXTRACT DATA FROM BLOCKED APPS adds this capability for 110 devices and many more will First in the Industry – Access blocked application data with file be added in coming releases. system extraction ◼ Enhanced physical extraction while bypassing lock of 27 Samsung Android devices with APQ8084 chipset (Snapdragon 805), including Samsung Galaxy Note 4, Note Edge, and Note 4 Duos. This chipset was previously supported with UFED, but due to operating system EXCLUSIVE: UNIFY MULTIPLE EXTRACTIONS changes, this capability was temporarily unavailable. In the world of devices, operating system changes Merge multiple extractions in single unified report for more frequently, and thus, influence our support abilities. efficient investigations As our ongoing effort to continue to provide our customers with technological breakthroughs, Cellebrite Logical 10K items developed a new method to overcome this barrier. Physical 20K items 22K items ◼ File system and logical extraction and decoding support for iPhone SE Samsung Galaxy S7 and LG G5 devices. File System 15K items ◼ Physical extraction and decoding support for a new family of TomTom devices (including Go 1000 Point Trading, 4CQ01 Go 2505 Mm, 4CT50, 4CR52 Go Live 1015 and 4CS03 Go 2405). -

Claudia Tapia, Director IPR Policy at the Ericsson
DT: a new technological and economic paradigm Dr Claudia Tapia, Director IPR Policy All views expressed in this speech are those of the author and do not necessarily represent the views of Ericsson Ericsson at a glance NETWORKS IT MEDIA INDUSTRIES Create one network for Transform IT to accelerate Delight the TV Connect industries to a million different needs business agility consumer every day accelerate performance Worldwide mobile 42,000 Patents 40% traffic provided by 222,6 B. SEK Net Sales our networks R&D Employees Licensing Countries with 23,700 >100 agreements 180 customers Average p.a. Licensing revenues Employees 5 B. usd in R&D 10 b. Sek 111,000 Page 2 415,000,000,000 Page 3 STANDARDISATION PROCESS Early Technical Unapproved contribution investment (described in R&D in a patent) Adopted by Standard FRAND CONSENSUS in essential commitment standard patent Return on Access to the investment standard Interoperable high performance devices at a FRAND = Fair, Reasonable and Non- reasonable price DiscriminatoryPage 4 (terms and conditions) 4,000,000,000,000 Page 5 3,452,040 Page 6 3G and LTE (3GPP - 1999 – Dec. 2014 ) 262,773 Submitted contributions 43,917 Approved contributions (16,7%) Source: Signals Research Group. The Essentials of IP, from 3G through LTE Release 12, May 2015 Page 7 LTE approved Contributions for 13 WGs (2009 - Q3 2015) –Source: ABI Research COMPANY RANK Ericsson 1 Huawei 2 Nokia Networks 3 Qualcomm 4 ALU 5 ZTE 6 Samsung 7 Anritsu 8 Rohde & Schwarz 9 CATT 10 Page 8 Principles of standardisation CONSENSUS TRANSPARENCY IMPARTIALITY OPENNESS .. -

Cybersecurity for Connected Cars Exploring Risks in 5G, Cloud, and Other Connected Technologies
Cybersecurity for Connected Cars Exploring Risks in 5G, Cloud, and Other Connected Technologies Numaan Huq, Craig Gibson, Vladimir Kropotov, Rainer Vosseler TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information Contents and educational purposes only. It is not intended and should not be construed to constitute legal advice. The information contained herein may not be applicable to all situations and may not reflect the most current situation. 4 Nothing contained herein should be relied on or acted upon without the benefit of legal advice based on the particular facts and circumstances presented and nothing The Concept of Connected Cars herein should be construed otherwise. Trend Micro reserves the right to modify the contents of this document at any time without prior notice. 7 Translations of any material into other languages are intended solely as a convenience. Translation accuracy is not guaranteed nor implied. If any questions arise Research on Remote Vehicle related to the accuracy of a translation, please refer to Attacks the original language official version of the document. Any discrepancies or differences created in the translation are not binding and have no legal effect for compliance or enforcement purposes. 13 Although Trend Micro uses reasonable efforts to include Cybersecurity Risks of Connected accurate and up-to-date information herein, Trend Micro makes no warranties or representations of any kind as Cars to its accuracy, currency, or completeness. You agree that access to and use of and reliance on this document and the content thereof is at your own risk. Trend Micro disclaims all warranties of any kind, express or implied. -

The Nanyan Observer No
Published by: Best Ten Campus Media Nanyan News Agency, Shenzhen Graduate School in Guangdong Province Four Pages PEKING UNIVERSITY The Nanyan Observer No. CUMU092017 Monday, 5 December. 2016 General Director: Megan Mancenido Chief Editor: Karras Lambert Managing Editor: Longjun Qin Tel: 0755-26032131 Info: [email protected] PKU Holds 8th Annual Thanksgiving Celebration comes to campus once a year. Min from the neighboring Tsinghua Macarena. Table of Contents University Graduate School. After After several weeks of groundwork a brief introduction, they invited As the Thanksgiving event's PKU Celebrates Thanksgiving..... and coordination between various the School of Transnational Law’s planning assistant, Yang Wandong schools, offices, and volunteers, Assistant Dean Christian Pangilinan of the School of Urban Planning .................................................A1 the much anticipated day had onto the stage to kick the night off Design says it was "awesome to Shenzhen Runner's Guide........... finally arrived. The Chancellor’s with the annual Thanksgiving toast. see things come together in its .................................................A2 Secretariat Office held the 8th Once again, the dinner’s turkeys own way, with everyone's effort, Annual Thanksgiving Celebration were catered by Metro in European then finally take shape in an event Financial Journalism Program...... in B-building's Moot Court. What Town, the side dishes were prepared that people enjoyed. That sense .................................................A3 originally started out as a modest by Frankie’s American Bar & Grille in of accomplishment is what made it All You Need is Ecuador............... get together to share an American Nanshan, and the peach and cherry worthwhile." tradition with Chinese friends cobblers from Baeckerei Thomas in .................................................A4 and colleagues has, over the Shekou. -

Zbwleibniz-Informationszentrum
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Parker, Geoffrey; Petropoulos, Georgios; Marshall van Alstyne Working Paper Platform mergers and antitrust Bruegel Working Paper, No. 2021/01 Provided in Cooperation with: Bruegel, Brussels Suggested Citation: Parker, Geoffrey; Petropoulos, Georgios; Marshall van Alstyne (2021) : Platform mergers and antitrust, Bruegel Working Paper, No. 2021/01, Bruegel, Brussels This Version is available at: http://hdl.handle.net/10419/237621 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents have been made available under an Open gelten abweichend von diesen Nutzungsbedingungen die in der dort Content Licence (especially Creative Commons Licences), you genannten Lizenz gewährten Nutzungsrechte. may exercise further usage rights as specified in the indicated licence. www.econstor.eu PLATFORM MERGERS AND ANTITRUST TED VERSION 15 2021 JUNE 15 TED VERSION UPDA | GEOFFREY PARKER, GEORGIOS PETROPOULOS AND MARSHALL VAN ALSTYNE ISSUE 01/2021 ISSUE 01/2021 | Platform ecosystems rely on economies of scale, data-driven economies of scope, high quality algorithmic systems, and strong network effects that frequently promote winner-takes-most markets. -

携手新时代 共赢创未来 Innovating and Collaborating for What’S Next
携手新时代 共赢创未来 Innovating and collaborating for what’s next Qualcomm中国技术与合作峰会 Qualcomm Technology Day January 25, 2018 #Qualcomm中国技术与合作峰会# Beijing, China Welcome Frank Meng Chairman Qualcomm International, Inc. China January 25, 2018 #Qualcomm中国技术与合作峰会# Beijing, China The opportunity ahead Steve Mollenkopf CEO Qualcomm Incorporated Years of driving the 30+ evolution of wireless Fabless # semiconductor 1 company ~8.6 Billion Cumulative smartphone unit shipments forecast between 2017–2021 Source: Gartner, Sep. ‘17 Mobile technology is powering the 5G global economy The mobile roadmap is leading the way Qualcomm is the R&D engine A strategy for continued growth $20B — RF-Front End Extending the reach of mobile technology $77B — Adjacent industries Core mobile — $32B ~$150B Datacenter — $19B Serviceable addressable Automotive IoT and security opportunity in 2020 $16B $43B Mobile compute Networking $7B $11B Source: combination of third party and internal estimates. Includes SAM for pending NXP acquisition. Note: SAM excludes QTL. Executing on our strategy Automotive IoT and security >$3 Billion in FY17 QCT revenues Up >75% over FY15 Mobile compute Networking FY17 revenue across auto, IoT, security, networking and mobile compute A proven business model that has enabled value creation between China and US Invent Share Collaborate Our commitment to China Supporting growth across many industries China Mobile Semiconductors Automotive China Telecom SMIC | SJ Semiconductor Geely | BYD | ZongMu China Unicom Corp. Huaqin Longcheer IoT Mobile WingTech -

Autonomous Vehicle (AV) Policy Framework, Part I: Cataloging Selected National and State Policy Efforts to Drive Safe AV Development
Autonomous Vehicle (AV) Policy Framework, Part I: Cataloging Selected National and State Policy Efforts to Drive Safe AV Development INSIGHT REPORT OCTOBER 2020 Cover: Reuters/Brendan McDermid Inside: Reuters/Stephen Lam, Reuters/Fabian Bimmer, Getty Images/Galimovma 79, Getty Images/IMNATURE, Reuters/Edgar Su Contents 3 Foreword – Miri Regev M.K, Minister of Transport & Road Safety 4 Foreword – Dr. Ami Appelbaum, Chief Scientist and Chairman of the Board of Israel Innovation Authority & Murat Sunmez, Managing Director, Head of the Centre for the Fourth Industrial Revolution Network, World Economic Forum 5 Executive Summary 8 Key terms 10 1. Introduction 15 2. What is an autonomous vehicle? 17 3. Israel’s AV policy 20 4. National and state AV policy comparative review 20 4.1 National and state AV policy summary 20 4.1.1 Singapore’s AV policy 25 4.1.2 The United Kingdom’s AV policy 30 4.1.3 Australia’s AV policy 34 4.1.4 The United States’ AV policy in two selected states: California and Arizona 43 4.2 A comparative review of selected AV policy elements 44 5. Synthesis and Recommendations 46 Acknowledgements 47 Appendix A – Key principles of driverless AV pilots legislation draft 51 Appendix B – Analysis of American Autonomous Vehicle Companies’ safety reports 62 Appendix C – A comparative review of selected AV policy elements 72 Endnotes © 2020 World Economic Forum. All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, including photocopying and recording, or by any information storage and retrieval system. -

Qualcomm Snapdragon Tech Summit 2019: Partner Quote Sheet
Qualcomm Snapdragon Tech Summit 2019: Partner Quote Sheet Day 1 - Tuesday, December 3, 2019 AT&T: “Together AT&T and Qualcomm Technologies continue to drive the industry forward to unleash the power of the next generation of wireless connectivity over 5G,” said Kevin Petersen, senior vice president AT&T Mobility. “We worked closely with Qualcomm Technologies to be the first to introduce the U.S. to millimeter wave 5G last year, and we’re working together now to begin offering consumers and businesses the latest low-band 5G smartphone technology.” HMD Global: “Our highest priority for 2020 is making 5G more accessible – bringing an affordable yet premium grade, future proof 5G experience for the best possible performance in NSA and SA networks with the Snapdragon 765 Mobile Platform,” said Juho Sarvikas, chief product officer, HMD Global. “Aside from being an excellent mobile platform for best-in-class 5G connectivity, Snapdragon 765 mobile platform allows us to offer breakthrough entertainment capabilities combined with our PureDisplay technology, and our unique ZEISS powered imaging solutions that enable fans to create and share amazing content over 5G. We also congratulate Qualcomm Technologies on the announcement of its Snapdragon Modular Platform. This innovative approach to making 5G more accessible to OEMs will dramatically streamline the development process and we look forward to exploring possibilities of working with Qualcomm Technologies on this exciting platform.” Motorola: “5G is a focus for the entire Lenovo organization - from network infrastructure to personal devices, being the first to launch a 5G smartphone and preview a 5G PC,” said Sergio Buniac, president, Motorola.