Copyrighted Material
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Colossus: the Missing Manual
Colossus: The Missing Manual Mark Priestley Research Fellow, The National Museum of Computing — Bletchley Park, UK Thomas Haigh University of Wisconsin—Milwaukee & Siegen University 1 serialized ciper text English Cipher text of one message plain text 1 0 0 1 1 (5 channel tape) 0 1 0 1 0 0 1 0 0 0 They were already 1 0 1 1 0 1 0 0 1 0 looking at him as approached in the distance, because he just stood out. He had quite an old face, 01101 11101 01011 0010 Knockolt Newmanry Newmanry Testery Testery Hut 3 Outstation Set Chi Wheels Generate Set Psi & Decrypt Translate Intercept, & Verify Counts “dechi” Motor Wheels Message Message Record & Verify Message (Colossus) (Tunny analog (Hand methods) (Tunny analog (Bilingual machine) machine) humans) dechi 1 0 0 1 1 0 27, 12, 30, 43, 8 Chi wheel 0 1 0 1 0 1 Psi & 55, 22 Sie sahen ihn schon 0 1 0 0 0 von weitem auf sich start posns. 1 0 1 1 0 1 0 0 1 0 motor start posns. zukommen, denn er for msg el auf. Er hatte ein 31, 3, 25, 18, 5 ganz altes Gesicht, aber wie er ging, German 1 0 0 1 1 0 0 1 0 1 0 1 0110001010... plain text 0 1 0 0 0 Newmanry 1 0 1 1 0 0011010100... 1 0 0 1 0 10011001001... 01100010110... 1 0 0 1 1 0 Break Chi 01011001101... 0 1 0 1 0 1 0110001010... 0 1 0 0 0 Wheels 1 0 1 1 0 Chi wheel 0011010100.. -

Code Breaking at Bletchley Park
Middle School Scholars’ CONTENTS Newsletter A Short History of Bletchley Park by Alex Lent Term 2020 Mapplebeck… p2-3 Alan Turing: A Profile by Sam Ramsey… Code Breaking at p4-6 Bletchley Park’s Role in World War II by Bletchley Park Harry Martin… p6-8 Review: Bletchley Park Museum by Joseph Conway… p9-10 The Women of Bletchley Park by Sammy Jarvis… p10-12 Bill Tutte: The Unsung Codebreaker by Archie Leishman… p12-14 A Very Short Introduction to Bletchley Park by Sam Corbett… p15-16 The Impact of Bletchley Park on Today’s World by Toby Pinnington… p17-18 Introduction A Beginner’s Guide to the Bombe by Luca “A gifted and distinguished boy, whose future Zurek… p19-21 career we shall watch with much interest.” This was the parting remark of Alan Turing’s Headmaster in his last school report. Little The German Equivalent of Bletchley could he have known what Turing would go on Park by Rupert Matthews… 21-22 to achieve alongside the other talented codebreakers of World War II at Bletchley Park. Covering Up Bletchley Park: Operation Our trip with the third year academic scholars Boniface by Philip Kimber… p23-25 this term explored the central role this site near Milton Keynes played in winning a war. 1 intercept stations. During the war, Bletchley A Short History of Bletchley Park Park had many cover names, which included by Alex Mapplebeck “B.P.”, “Station X” and the “Government Communications Headquarters”. The first mention of Bletchley Park in records is in the Domesday Book, where it is part of the Manor of Eaton. -

A Note on His Role As World War Ii Cryptanalyst
Internatiuonal Journal ofApplied Engineering and Technology ISSN: 2277-212X (Online) An Online International Journal Available at http://www.cibtech.org/jet.htm 2013 Vol. 3 (1) January-March, pp.21-26/Afreen Historical Note ALAN TURING: A NOTE ON HIS ROLE AS WORLD WAR II CRYPTANALYST *Rahat Afreen *Department of MCA, Millenium Institute of Management, Dr. RafiqZakariaCampus,Aurangabad, Maharashtra *Author for Correspondence ABSTRACT Alan Mathison Turing is well known to the world of computer for the concept of Turing Machine- A conceptual machine presented by him which proves that automatic computation cannot solve all mathematical problems – also called as Halting Problem of Turing Machine. He was attributed as the founder of Computer Science. But, until late 20th century, his contributions in the field of Number Theory, Cryptography, Artificial Intelligence and more importantly how his ideas protected England in the times of world war II were unknown. Key Words: Alan Turing, Enigma, Bombe, Colossus, Tunny, ACE INTRODUCTION Alan Turing was born on 23rd June 1912 in Paddington, London. His father Julius Mathison Turing worked for Indian Civil Services at Orrisa for British government in India. But he and his wife decided to keep their children back in England for education. He got his education from Sherbrone School, Sherbrone and did his higher education from King‟s College Cambridge where he later became a fellow. He had an interest in the field of mathematics and presented numerous papers on famous problems of mathematics. At the age of 24 Turing wrote a paper entitled “On Computable Numbers, with an Application to the Entscheidungs problem”. -

The Essential Turing: Seminal Writings in Computing, Logic, Philosophy, Artificial Intelligence, and Artificial Life: Plus the Secrets of Enigma
The Essential Turing: Seminal Writings in Computing, Logic, Philosophy, Artificial Intelligence, and Artificial Life: Plus The Secrets of Enigma B. Jack Copeland, Editor OXFORD UNIVERSITY PRESS The Essential Turing Alan M. Turing The Essential Turing Seminal Writings in Computing, Logic, Philosophy, Artificial Intelligence, and Artificial Life plus The Secrets of Enigma Edited by B. Jack Copeland CLARENDON PRESS OXFORD Great Clarendon Street, Oxford OX2 6DP Oxford University Press is a department of the University of Oxford. It furthers the University’s objective of excellence in research, scholarship, and education by publishing worldwide in Oxford New York Auckland Cape Town Dar es Salaam Hong Kong Karachi Kuala Lumpur Madrid Melbourne Mexico City Nairobi New Delhi Taipei Toronto Shanghai With offices in Argentina Austria Brazil Chile Czech Republic France Greece Guatemala Hungary Italy Japan South Korea Poland Portugal Singapore Switzerland Thailand Turkey Ukraine Vietnam Published in the United States by Oxford University Press Inc., New York © In this volume the Estate of Alan Turing 2004 Supplementary Material © the several contributors 2004 The moral rights of the author have been asserted Database right Oxford University Press (maker) First published 2004 All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, without the prior permission in writing of Oxford University Press, or as expressly permitted by law, or under terms agreed with the appropriate reprographics rights organization. Enquiries concerning reproduction outside the scope of the above should be sent to the Rights Department, Oxford University Press, at the address above. -

Simply Turing
Simply Turing Simply Turing MICHAEL OLINICK SIMPLY CHARLY NEW YORK Copyright © 2020 by Michael Olinick Cover Illustration by José Ramos Cover Design by Scarlett Rugers All rights reserved. No part of this publication may be reproduced, distributed, or transmitted in any form or by any means, including photocopying, recording, or other electronic or mechanical methods, without the prior written permission of the publisher, except in the case of brief quotations embodied in critical reviews and certain other noncommercial uses permitted by copyright law. For permission requests, write to the publisher at the address below. [email protected] ISBN: 978-1-943657-37-7 Brought to you by http://simplycharly.com Contents Praise for Simply Turing vii Other Great Lives x Series Editor's Foreword xi Preface xii Acknowledgements xv 1. Roots and Childhood 1 2. Sherborne and Christopher Morcom 7 3. Cambridge Days 15 4. Birth of the Computer 25 5. Princeton 38 6. Cryptology From Caesar to Turing 44 7. The Enigma Machine 68 8. War Years 85 9. London and the ACE 104 10. Manchester 119 11. Artificial Intelligence 123 12. Mathematical Biology 136 13. Regina vs Turing 146 14. Breaking The Enigma of Death 162 15. Turing’s Legacy 174 Sources 181 Suggested Reading 182 About the Author 185 A Word from the Publisher 186 Praise for Simply Turing “Simply Turing explores the nooks and crannies of Alan Turing’s multifarious life and interests, illuminating with skill and grace the complexities of Turing’s personality and the long-reaching implications of his work.” —Charles Petzold, author of The Annotated Turing: A Guided Tour through Alan Turing’s Historic Paper on Computability and the Turing Machine “Michael Olinick has written a remarkably fresh, detailed study of Turing’s achievements and personal issues. -

WWII Innovations - Codebreaking, Radar, Espionage, New Bombs, and More
Part 6: WWII Innovation s - Codebreaking, Radar, Espionage, New Bombs, and More. Part 7: WWII Innovations - Codebreaking, Radar, Espionage, New Bombs, and More. Objective: How new innovations impacted the war, people in the war, and people after the war. Assessment Goals: 1. Research and understand at least three of the innovations of WWII that made a difference on the war and after the war. (Learning Target 3) 2. Determine whether you think dropping the atomic bombs on Hiroshima and Nagasaki was a wise decision or not. (Learning Target 2) Resources: Resources in Binder (Video links, websites, and articles) Note Graph (Create something similar in your notes): Use this graph for researching innovations: Innovation #1: ______________________ Innovation #2: ______________________ Innovation #3: ______________________ (Specific notes about impact on war and after) (Specific notes about impact on war and after) (Specific notes about impact on war and after) Use the graph on the next page to organize your research about the atomic bomb. Evidence that dropping the bombs was wise: Evidence that dropping the bombs was not wise: (Include quotes, document citations, and (Include quotes, document citations, and statistics) statistics) ● ● ● ● ● ● ● ● ● ● ● ● ● ● ● ● ● ● My position: My overall thoughts about the choice to drop the bombs: If I were a Japanese civilian, what would I have wanted to happen and why? If I were a U.S. soldier, what would I have wanted to happen and why? Resources: Part 7 - WW2 Innovations - Codebreaking, -

Linguaggio Nei Numeri E Numeri Nel Linguaggio. Linguistica, Matematica E Cryptonalisi
Linguaggio nei numeri e numeri nel linguaggio. Linguistica, Matematica e Cryptonalisi Thomas Christiansen Dipartimento Studi Umanistici, Università del Salento, Lecce, Italia 1 Intoduzione: la scienza della 1 Introduction: the Science of linguistica Linguistics Ai tradizionalisti, gli studi di matematica e di To the more traditionally minded, the studies of linguistica, potrebbero sembrare avere poco in mathematics and linguistics may seem to have comune, poiché costituiscono due modi di ap- little in common, constituting two very different prendimento molto differenti. Nelle università types of learning. In medieval universities, the medioevali le sette arti cosiddette liberali, era- seven so-called liberal arts were divided into a no separate in una divisione inferiore o trivium lower division or triuvium (grammar, rhetoric, (grammatica, retorica, e logica) e una superio- and logic) and a higher quadrivium (arithmetic, re, quadrivium (aritmetica, musica, geometria e music, geometry, and astronomy). Today, maths astronomia). Oggi la matematica è trattata come is treated as a science. Still, but increasingly less una scienza. Lo studio del linguaggio è anco- so, language is sometimes lumped together with ra, ma sempre meno, unito ad argomenti come things like literature and translation and classed letteratura e traduzione e classificato come una as one of the arts1. Added confusion comes from delle arti1. Ulteriore confusione emerge dal fatto the fact that the term linguist has quite different che il termine linguista viene utilizzato in modi uses: on the one hand, it can describe someone piuttosto differenti: da una parte descrive chi sa who is good at speaking different languages (i.e. parlare bene lingue diverse (cioè un poliglotta o a polyglot or plurilingual person); on the other, 1In maniera analoga, la logica è uscita dagli stretti con- 1Similarly, logic has also moved out of the strict confines fini del trivium in quattro campi differenti: filosofico, of the triuvium into four separate fields: philosophical, formale, informale e matematico. -

How to Decrypt a Lorenz SZ42 Message Using Virtual Colossus 3D
How to decrypt a Lorenz SZ42 message using Virtual Colossus 3D A tutorial on decrypting a German Lorenz SZ42 message using Virtual Colossus 3D https://virtualcolossus.co.uk This document will take you through an example process used on Colossus to get the start positions of a received message. There wasn't a set program which would run to work out the settings, it was a matter of following a "menu" of different algorithms and sometimes required knowledge of what worked on a particular radio link. Colossus was not able to run a sequence of algorithms or use the results of previous calculations (like we would expect from a computer today), each run required a decision by the operator or code breaker assigned to that machine on which operation would be the next best to run. Once the start positions of each of the twelve rotors are calculated, we can use a Lorenz machine to try to decipher the final message. Wheel breaking We will assume that we have already broken the wheel patterns for this message. Wheel breaking meant working out the pin settings of all 501 pins on each of the twelve Lorenz cipher wheels. This was generally done using a few methods including from messages in depth (where several messages were received enciphered with the same key) in a process devised by Alan Turing called Turingery. Later, a new process called rectangling allowed wheel breaking potentially using a single long message. Colossus could help with rectangling to assist with wheel breaking, and Colossus 6 was used almost exclusively for this, but in general, wheel breaking was done by hand methods. -
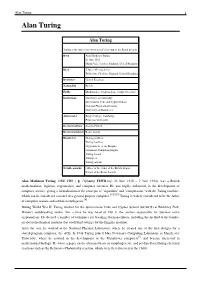
Alan Turing 1 Alan Turing
Alan Turing 1 Alan Turing Alan Turing Turing at the time of his election to Fellowship of the Royal Society. Born Alan Mathison Turing 23 June 1912 Maida Vale, London, England, United Kingdom Died 7 June 1954 (aged 41) Wilmslow, Cheshire, England, United Kingdom Residence United Kingdom Nationality British Fields Mathematics, Cryptanalysis, Computer science Institutions University of Cambridge Government Code and Cypher School National Physical Laboratory University of Manchester Alma mater King's College, Cambridge Princeton University Doctoral advisor Alonzo Church Doctoral students Robin Gandy Known for Halting problem Turing machine Cryptanalysis of the Enigma Automatic Computing Engine Turing Award Turing test Turing patterns Notable awards Officer of the Order of the British Empire Fellow of the Royal Society Alan Mathison Turing, OBE, FRS ( /ˈtjʊərɪŋ/ TEWR-ing; 23 June 1912 – 7 June 1954), was a British mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, giving a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which can be considered a model of a general purpose computer.[1][2][3] Turing is widely considered to be the father of computer science and artificial intelligence.[4] During World War II, Turing worked for the Government Code and Cypher School (GC&CS) at Bletchley Park, Britain's codebreaking centre. For a time he was head of Hut 8, the section responsible for German naval cryptanalysis. He devised a number of techniques for breaking German ciphers, including the method of the bombe, an electromechanical machine that could find settings for the Enigma machine. -

Alan Turing: Founder of Computer Science
Alan Turing: Founder of Computer Science Jonathan P. Bowen Division of Computer Science and Informatics School of Engineering London South Bank University Borough Road, London SE1 0AA, UK Museophile Limited, Oxford, UK [email protected] http://www.jpbowen.com Abstract. In this paper, a biographical overview of Alan Turing, the 20th cen- tury mathematician, philosopher and early computer scientist, is presented. Tur- ing has a rightful claim to the title of ‘Father of modern computing’. He laid the theoretical groundwork for a universal machine that models a computer in its most general form before World War II. During the war, Turing was instru- mental in developing and influencing practical computing devices that have been said to have shortened the war by up to two years by decoding encrypted enemy messages that were generally believed to be unbreakable. After the war, he was involved with the design and programming of early computers. He also wrote foundational papers in the areas of what are now known as Artificial Intelligence (AI) and mathematical biology shortly before his untimely death. The paper also considers Turing’s subsequent influence, both scientifically and culturally. 1 Prologue Alan Mathison Turing [8,23,33] was born in London, England, on 23 June 1912. Ed- ucated at Sherborne School in Dorset, southern England, and at King’s College, Cam- bridge, he graduated in 1934 with a degree in mathematics. Twenty years later, after a short but exceptional career, he died on 7 June 1954 in mysterious circumstances. He is lauded by mathematicians, philosophers, and computer sciences, as well as increasingly the public in general. -

Tommy Flowers - Wikipedia
7/2/2019 Tommy Flowers - Wikipedia Tommy Flowers Thomas Harold Flowers, BSc, DSc,[1] MBE (22 December 1905 – 28 October 1998) Thomas Harold Flowers was an English engineer with the British Post Office. During World War II, Flowers MBE designed and built Colossus, the world's first programmable electronic computer, to help solve encrypted German messages. Contents Early life World War II Post-war work and retirement See also References Bibliography External links Tommy Flowers – possibly taken Early life around the time he was at Bletchley Flowers was born at 160 Abbott Road, Poplar in London's East End on 22 December Park 1905, the son of a bricklayer.[2] Whilst undertaking an apprenticeship in mechanical Born 22 December 1905 engineering at the Royal Arsenal, Woolwich, he took evening classes at the University of Poplar, London, London to earn a degree in electrical engineering.[2] In 1926, he joined the England telecommunications branch of the General Post Office (GPO), moving to work at the Died 28 October 1998 research station at Dollis Hill in north-west London in 1930. In 1935, he married Eileen (aged 92) Margaret Green and the couple later had two children, John and Kenneth.[2] Mill Hill, London, From 1935 onward, he explored the use of electronics for telephone exchanges and by England 1939, he was convinced that an all-electronic system was possible. A background in Nationality English switching electronics would prove crucial for his computer designs. Occupation Engineer Title Mr World War II Spouse(s) Eileen Margaret Flowers' first contact with wartime codebreaking came in February 1941 when his Green director, W. -

Jewel Theatre Audience Guide Addendum: Alan Turing Biography
Jewel Theatre Audience Guide Addendum: Alan Turing Biography directed by Kirsten Brandt by Susan Myer Silton, Dramaturg © 2019 ALAN TURING The outline of the following overview of Turing’s life is largely based on his biography on Alchetron.com (https://alchetron.com/Alan-Turing), a “social encyclopedia” developed by Alchetron Technologies. It has been embellished with additional information from sources such as Andrew Hodges’ books, Alan Turing: The Enigma (1983) and Turing (1997) as well as his website, https://www.turing.org.uk. The following books have also provided additional information: Prof: Alan Turing Decoded (2015) by Dermot Turing, who is Alan’s nephew by way of his only sibling, John; The Turing Guide by B. Jack Copeland, Jonathan Bowen, Mark Sprevak, and Robin Wilson (2017); and Alan M. Turing, written by his mother, Sara, shortly after he died. The latter was republished in 2012 as Alan M. Turing – Centenary Edition with an Afterword entitled “My Brother Alan” by John Turing. The essay was added when it was discovered among John’s writings following his death. The republication also includes a new Foreword by Martin Davis, an American mathematician known for his model of post-Turing machines. Extended biographies of Christopher Morcom, Dillwyn Knox, Joan Clarke (the character of Pat Green in the play) and Sara Turing, which are provided as Addendums to this Guide, provide additional information about Alan. Beginnings Alan Mathison Turing was an English computer scientist, mathematician, logician, cryptanalyst, philosopher and theoretical biologist. He was born in a nursing home in Maida Vale, a tony residential district of London, England on June 23, 1912.