Avaya Aura Conferencing 8.0 Port Matrix
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Readytalk for Online Meetings
ReadyTalk for Online Meetings Online collaboration with colleagues, partners and customers is effective and easy with ReadyTalk’s audio and web conferencing technology. Audio & Web Conferencing Audio & Web Conferencing audio and web conferencing Save Time and Money with Conferencing Cutbacks in business travel, more flexible work schedules and advances in technology have increased the demand for and value of online collaboration. The ability to easily join an audio and web conference and view the same content, applications and documents is no longer a “nice to have.” It’s a business necessity. All the Tools You Need Effective online meetings require a conferencing platform that is easy to use and reliable. With ReadyTalk’s audio and web conferencing, you have full access to the tools needed for polished sales demos, customer training and remote meetings. Easy Access for Everyone Start meetings faster and on time. Participants with Flash join your meeting in less than 10 seconds with no downloads and an alternative auto-installing Java application means those without Flash can still attend. Plus, superior platform (Windows, Mac, Linux) and browser (Internet Explorer, Safari, Firefox, Chrome) support means everyone can join. Industry-Standard Recording Formats Capture the details of the meeting by recording the session. Recordings are available for download in four industry- standard file formats: Flash, .mp4, .mp3, and .wav and can be hosted on your servers for future playback or sharing with colleagues. ReadyTalk Offers a Full Range of Services: Audio Conferencing, Web Conferencing, Recording and Archiving 1 Start your meeting with ease. Whether you want to meet now or plan ahead, ReadyTalk makes it easy for you to start your conference and easy for your participants to attend your meeting: On-Demand Meetings Conduct an online meeting instantly – simply log in to ReadyTalk and dial in with your phone. -

Web Conferencing Comparison
Web Conferencing Comparison We offer a range of web conferencing solutions designed for use with different types of meetings: from less formal on-the-fly get-togethers to carefully structured company-wide conferences or training sessions. Unified Meeting®—let people see what you are talking about and collaborate during your online meetings with our proprietary web conferencing product. You get audio, web and video conferencing in a single system that integrates with everyday business tools, like calendaring systems and instant messaging clients, so starting and joining meetings is done just with a click of the mouse. The best part is that all of this comes as a service that is managed for you. Microsoft® Office® Live Meeting—host interactive, collaborative meetings by showing presentations, software and web sites. Office Live Meeting offers unique features, such as muting lines and dialing additional participants from the web interface, Microsoft Office integration, custom slides, reporting tools, recording and printing to PDF. It’s a flexible tool that can be configured to suit the needs of your conference—no matter what size or type. Cisco WebEx™ Meeting Center—engage your participants by sharing a PowerPoint presentation, demonstrating software, showing web site navigation, asking polling questions and transferring files. The integration with Reservationless-Plus® lets you control the audio portion of your meeting online. WebEx Meeting Center provides the ultimate collaborative platform for your day-to-day business communication needs. Cisco WebEx Training Center— deliver live, interactive training sessions with features specifically designed with the virtual classroom in mind. In addition to sharing presentations or demonstrating applications, you can conduct quizzes online, separate trainees into work groups for collaborative projects and host post-training tests for follow-up. -

Easing the Transition Into Remote Working Maximize Collaboration and Productivity with Voip and the Right Technology Tools
Easing the Transition into Remote Working Maximize collaboration and productivity with VoIP and the right technology tools www.3cx.com CONTENTS 3 Introduction: Remote Working is the New Reality 4 Remote Working Challenges 5 Benefits of Working Remotely 6 Why VoIP is a Must-Have for Effective Telecommuting 8 The 3CX Advantage 10 Tips To Choose The Right Business Communications Solution 11 Conclusion Remote Working is the New Reality Although remote working has been steadily increasing for a number of years, the Covid-19 pandemic and resulting lockdowns brought about a paradigm shift in our workings, and has led to several long-term changes in our lives. What began as a localised viral outbreak, quickly culminated into the largest remote working exercise in history, with a dramatic increase in the number of remote workers across the globe. The unprecedented event drove enterprises to quickly transition to the remote working model in order to ensure business continuity. Fortunately, remote working has provided companies with the flexibility and connection required to stay on top amidst such challenging times. Remote working or teleworking comes with several challenges, both from a human and a technology perspective. It demands meticulous business planning, change in mindset, and more than anything else, the right technology tools to make it a success. Voice over Internet Protocol (VoIP), which facilitates web conferencing, chat, and mobile collaboration, is central to ensuring effective remote working experience. With the right tools at hand, the challenges of remote working can be easily addressed to make it a win-win proposition for both the employees and the employer. -

Conferencing & Secure Instant Messaging
WEB CONFERENCING & SECURE INSTANT MESSAGING Conduct robust, low-cost Web meetings with Live Meeting & improve communication with Secure IM—both from Microsoft Overview Web Conferencing—utilizing Microsoft Live Meeting and Office Communications Server (OCS) 2007— enables you to conduct unlimited, real-time Web meetings with your customers. Live Meeting integrates seamlessly with Microsoft Outlook, enabling you to schedule Web meetings quickly and easily. In addition, we offer fully-integrated, Secure Instant Messaging (IM), as well as 24/7, U.S.- based, live customer service if you need assistance. While conducting a meeting you can give a presentation or demo, share your desktop, brainstorm, collaborate using whiteboards, and discuss business deals—from any Internet-connected PC. Plus, you can save time and money by avoiding the unnecessary hassle of travel. Web Conferencing Quickly and easily organize meetings around the world and save money via the following features and benefits: Features at a glance • Conduct meetings from your desk: Save time by hosting meetings online, and avoid the costs of • Conduct unlimited Web meetings for one business travel. low, monthly cost • Improve productivity: Avoid time spent traveling to and from meetings. You can also meet more • Reduce travel and long-distance telephone frequently with little to no downtime. expenses across the board • Reduce costs: Web Conferencing delivers a significant return on your investment vs. the cost of • Encourage team collaboration by traditional face-to-face meetings. conducting meetings using interactive • Keep your audience focused: Utilize dynamic communication tools in your presentations including audio and video video, chat, slides, and feedback tools. • Seamlessly integrate with your Microsoft • Record/reuse to get the most from meetings: Meetings/training events can be recorded and desktop applications, so you can schedule stored. -

Web Conferencing Services
TATA TELE BUSINESS SERVICES Web Conferencing Services Web conferencing is one of the strongest emerging mediums of communication helping organizations to expand their reach, to exchange better quality of information, and for speedier decision-making while reducing travel and time resource costs. Our Web Conferencing Service offers businesses an effortless solution for live meetings, conferencing, presentations and training via the internet particularly on TCP/IP connections. You can connect to your conference either by telephone or using your computer's speakers and microphone through a VoIP connection and build a collaboration on the go. MARKETING SOLUTIONS TATA TELE BUSINESS SERVICES BUSINESS • Cost-effective collaboration across geographies ADVANTAGES • An ideal tool for the new-age virtual commuter • Expand your reach to multiple offices • Improve productivity by saving time on commuting and gathering • Connect globally • Expand your reach with TTBS Web Conference Service Webinar • Work faster with convenient one-click access FEATURES • Enjoy a dedicated meeting room • Eliminate the hassle of software downloads for your guests • Connect to audio however you want • Manage audio meetings with your visual desktop audio controls or mobile devices • Share your screen with crystal clear quality • Personalise meetings with HD quality (H.264) webcam video for everyone • Recording meetings with one click. Send meeting record link to guests. • Stay engaged while on-the-go, easily transfer an ongoing meeting from your computer to a mobile device • Store and organise meeting files and folders in your personal cloud based file library. Share files in meetings. Transfer files or email file’s links to guests, even during meetings • Meeting reports are automatically stored in your File Library when a meeting ends. -

Readytalk Web Conferencing
ReadyTalk Web Conferencing WEB CONFERENCING Meet with Confidence ReadyTalk lets you meet with confidence with a web conferencing service that is simple and intuitive, highly reliable and makes it easy to host or join a meeting. Concentrate on the substance of your meeting or webinar, not on the technology. Conferencing that Includes Everything ReadyTalk’s tools are designed so that meetings, sales demos, training sessions and webinars are easy to schedule and conduct. Unlike other web conferencing services, ReadyTalk doesn’t make you pick-and-choose features or the way you use them: • Need real-time collaboration? Hold an on-demand conference and take advantage of application and desktop sharing. Creative Ways to Use Web Conferencing • Hosting a high-profile webinar? Schedule a conference and create a branded experience with custom invitations, − Generate leads with marketing registration pages and more. webinars • Want to leverage recorded content? Use ReadyTalk’s embeddable media player, automated podcasting and built-in − Communicate with employees, social media promotion tools. customers or partners − Collaborate online with co-workers Regardless of how you use ReadyTalk’s web conferencing services, you have access to a full-featured tool set. No need to upgrade or − Host a sales demo with a prospect change packages; you get it all at one affordable price. − Conduct online training Conferencing for Everyone − Provide remote support A common complaint about web conferences is the hassle many − Enhance your website with recorded people experience when they try to join a conference. A hefty content download, the wrong version of Java or an unsupported platform or browser can frustrate participants or even make them abandon the process altogether. -
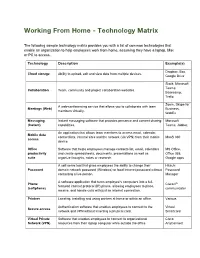
Technology Matrix
Working From Home - Technology Matrix The following sample technology matrix provides you with a list of common technologies that enable an organization to help employees work from home, assuming they have a laptop, Mac or PC to access. Technology Description Example(s) Dropbox, Box, Cloud storage Ability to upload, edit and view data from multiple devices. Google Drive Slack, Microsoft Teams, Collaboration Team, community and project collaboration websites. Basecamp, Trello Zoom, Skype for A web-conferencing service that allows you to collaborate with team Meetings (Web) Business, members virtually. WebEx Messaging Instant messaging software that provides presence and content sharing Microsoft (Instant) capabilities. Teams, Jabber, An application that allows team members to access email, calendar, Mobile data contact lists, internal sites and the network (via VPN) from their mobile MaaS 360 access device. Office Software that helps employees manage contacts list, email, calendars MS Office, productivity and create spreadsheets, documents, presentations as well as Office 365, suite organize thoughts, notes or research. Google apps A self-serve tool that gives employees the ability to change their Hitachi Password domain network password (Windows) or local intranet password without Password contacting a live person. Manager A software application that turns employee’s computers into a full- Phone Cisco IP featured internet protocol (IP) phone, allowing employees to place, (softphone) communicator receive, and handle calls with just an internet connection. Printers Locating, installing and using printers at home or within an office. Various Authentication software that enables employees to connect to the Virtual Secure access network and VPN without inserting a physical card. -

Easy Real-Time Online Collaboration Using Togetherjs
NEXT SLIDE Easy Real-Time Online Collaboration Using TogetherJS Scott Randby The University of Akron [email protected] http://srandby.org Easy Real-Time Online Collaboration Using TogetherJS • Section: Table of Contents • Page: 2 / 15 PREVIOUS SLIDE NEXT SLIDE TABLE OF CONTENTS Table of Contents 1. Why Real-Time Collaboration? 2. Real-Time Collaboration Options Overview 3. TogetherJS Easy Real-Time Online Collaboration Using TogetherJS • Section: Why Real-Time Collaboration? • Page: 3 / 15 PREVIOUS SLIDE NEXT SLIDE TABLE OF CONTENTS Why Real-Time Collaboration? I Creates a more intimate sense of a class community. I Brings students and instuctors together in a more immediate way than discussion groups or email. I Creates a more personal connection between instructors and students. I Students want (need) to feel that instructors care about them. I Real-time responses enhance that feeling. I Flexibility I Real-time issue resolution. I The most important reason for real-time collaboration. Easy Real-Time Online Collaboration Using TogetherJS • Section: Real-Time Collaboration Options Overview • Page: 4 / 15 PREVIOUS SLIDE NEXT SLIDE TABLE OF CONTENTS Real-Time Collaboration Options Overview There are four basic technologies that are used for real-time collaboration. I Text chatting I Audio communication I Video I Desktop/application sharing Easy Real-Time Online Collaboration Using TogetherJS • Section: Real-Time Collaboration Options Overview • Page: 5 / 15 PREVIOUS SLIDE NEXT SLIDE TABLE OF CONTENTS There are dozens of software applications that may be used for real-time collaboration. I Internet Relay Chat and instant messaging applications I VoIP applications (Skype, etc.) I Web conferencing systems (WebEx, etc.) I Google I Learning management systems Easy Real-Time Online Collaboration Using TogetherJS • Section: Real-Time Collaboration Options Overview • Page: 6 / 15 PREVIOUS SLIDE NEXT SLIDE TABLE OF CONTENTS Instructors need to make wise choices when deciding how to implement real-time collaboration in an online course. -

Adobe Connect Quick Start Guide for Participants
Adobe Connect VISUAL QUICK START GUIDE FOR PARTICIPANTS Partcipate in Adobe Connect Meetings Meeting audio Adobe Connect is an enterprise web conferencing solution for online meetings, eLearning and Meeting hosts have control over how the audio portion of your meeting is conducted. They webinars used by leading corporations and government agencies. This Visual Quick Start Guide can choose to use Voice-over-IP (VoIP), Integrated Telephony, or Universal Voice (a non- provides you with the basics participating in an Adobe Connect meeting, virtual integrated teleconference). classroom, or webinar. Option 1: Voice-over-IP Attend an Adobe Connect meeting When this option is selected, you can hear 1. It is recommended that you test your computer prior to attending a meeting. You can do meeting audio through your computer this by going to http://admin.adobeconnect.com/common/help/en/support/meeting_test.htm speakers. If a meeting attendee is speaking using VoIP, you will see a microphone icon 2. The Connection Test checks your computer to make sure next to their name. all system requirements are met. If you pass the first three steps of the test, then you are ready to participate in a meeting. In some cases, meeting hosts may give you the ability to broadcast audio using VoIP. When this is the case, a dialog will alert you that you have the rights to use your microphone. Clicking the Speak Now link will activate the Tip: microphone icon in the Application Bar at the top of your screen. Tip: 3. If you do not pass the test, perform the suggested actions and run the test again. -

Lync Secure Chat & Conferencing
Lync Secure Chat & Conferencing Microsoft Lync Secure Instant Messaging from Intermedia gives you secure, business-grade communication and collaboration including chat, video, desktop sharing, web conferencing and more. Lync Communicate in real time Share information easily Collaborate easily via Reduce costs with from virtually anywhere with group chat and voice & video using a integration and shared desktop sharing single unified client infrastructure Collaboration that fuels growth and productivity Lync Secure Instant Messaging includes robust features that take office communications and collaboration to a new level while providing a secure and professional alternative to personal instant messaging services. With Lync, your employees get a full range of collaboration and communication tools rolled into one powerful cloud-based solution: • Instant Messaging. Communicate in real time with colleagues, customers and partners from virtually anywhere. • Rich Presence Capabilities. Know immediately if contacts are “available,” “away”, “busy”, and more. • Screen Sharing. Share any file or application so everyone on the team can stay in sync. • Group Chat. Chat with everyone on the team, regardless of where they’re located. • Voice and Video Chat. Reduce travel costs by holding voice- and video-enabled meetings. Empower your people Engage employees Enable innovation Give them the ability to work their Provide the right tools so they can Foster better relationships so users way—where, when, and how they stay more connected with their peers are -

IP Phones, Software Voip, and Integrated and Mobile Voip
Chapter 2 IP Phones, Software VoIP, and Integrated and Mobile VoIP Abstract In order to establish their technical, communication, and service affordances, this chapter explores and three types of VoIP tools: 1) IP Phones, 2) software VoIP, and 3) mobile and integrated VoIP. Type 1: IP Phones Another reply to my e-mail list call-out came from consul- tant Susan Knoer, who reflected: VoIP is an old technology now, and many people didn’t even realize that their “new” phone lines are VoIP. Even the smaller corporations I work with have ReportsLibrary Technology gone over. It might be more interesting to talk to campuses that don’t have VoIP and find out why.1 Figure 5 Cisco Ip phone handset. Excellent point, Susan. The first VoIP type I explore is the most institutionally established yet least obvious hardware externals they are also virtually indistinguish- form of networked calling: the mass-market carrier IP able from older phones (figure 5). Broadband IP calls are phones sitting inconspicuously on desks at a growing initiated with either specially made IP handsets or head- number of offices and homes. Digital voice is becoming sets or with existing handsets converted with adapters. standard for schools, organizations, and business, which Unlike the small-scale startup culture of software VoIP, still tend to rely on fixed-location communication. As IP IP phones tend to follow a more traditional provider- www.alatechsource.org phones are bundled with high-speed Internet and televi- subscriber customer service model. These characteristics sion subscriptions, individual consumers still interested make IP calling an easier conceptual leap for users who in landline service are steadily adopting them, as well. -

Technology-Based Learning Strategies
S O CIAL PO L ICY R ESEAR C H A SSO CIATES • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • • Technology-Based Learning Strategies Prepared by: Vinz Koller Sandra Harvey Micheline Magnotta Prepared for: U.S. Department of Labor Employment and Training Administration Office of Policy Development and Research 200 Constitution Ave., N.W. Washington, DC 20210 Under Contract #AF-12526-02-30 and the direction of Heidi M. Casta. 1330 Broadway, Suite 1426 Oakland, CA 94612 Tel: (510) 763-1499 Fax: (510) 763-1599 www.spra.com CONTENTS EXECUTIVE SUMMARY A. INTRODUCTION ..................................................................................................... 1 B. OVERVIEW ............................................................................................................. 3 What is Technology-Based Learning (TBL)? .................................................................... 4 Technology-Based Learning’s Potential............................................................................ 4 Benefits and Challenges ................................................................................................... 6 Benefits......................................................................................................................... 6 Challenges.................................................................................................................... 8 C. METHODOLOGIES AND TOOLS........................................................................