MEMOIRE DE FIN D'etudes En Vue De L'obtention Du DIPLOME De Licence Ès Sciences Techniques DEVELOPPEMENT D'un LOGICIEL DE
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ironpython in Action
IronPytho IN ACTION Michael J. Foord Christian Muirhead FOREWORD BY JIM HUGUNIN MANNING IronPython in Action Download at Boykma.Com Licensed to Deborah Christiansen <[email protected]> Download at Boykma.Com Licensed to Deborah Christiansen <[email protected]> IronPython in Action MICHAEL J. FOORD CHRISTIAN MUIRHEAD MANNING Greenwich (74° w. long.) Download at Boykma.Com Licensed to Deborah Christiansen <[email protected]> For online information and ordering of this and other Manning books, please visit www.manning.com. The publisher offers discounts on this book when ordered in quantity. For more information, please contact Special Sales Department Manning Publications Co. Sound View Court 3B fax: (609) 877-8256 Greenwich, CT 06830 email: [email protected] ©2009 by Manning Publications Co. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by means electronic, mechanical, photocopying, or otherwise, without prior written permission of the publisher. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in the book, and Manning Publications was aware of a trademark claim, the designations have been printed in initial caps or all caps. Recognizing the importance of preserving what has been written, it is Manning’s policy to have the books we publish printed on acid-free paper, and we exert our best efforts to that end. Recognizing also our responsibility to conserve the resources of our planet, Manning books are printed on paper that is at least 15% recycled and processed without the use of elemental chlorine. -

Introducing Visual Studio 2010
INTRODUCING VISUAL STUDIO 2010 DAVID CHAPPELL MAY 2010 SPONSORED BY MICROSOFT CONTENTS Tools and Modern Software Development ............................................................................................ 3 Understanding Visual Studio 2010 ........................................................................................................ 3 The Components of Visual Studio 2010 ................................................................................................... 4 A Closer Look at Team Foundation Server............................................................................................... 5 Work Item Tracking ............................................................................................................................. 7 Version Control .................................................................................................................................... 8 Build Management: Team Foundation Build ...................................................................................... 9 Reporting and Dashboards.................................................................................................................. 9 Using Visual Studio 2010 ..................................................................................................................... 12 Managing Requirements ....................................................................................................................... 12 Architecting a Solution ......................................................................................................................... -

Visual Studio 2010 Tools for Sharepoint Development
Visual Studio 2010 for SharePoint Open XML and Content Controls COLUMNS Toolbox Visual Studio 2010 Tools for User Interfaces, Podcasts, Object-Relational Mappings SharePoint Development and More Steve Fox page 44 Scott Mitchell page 9 CLR Inside Out Profi ling the .NET Garbage- Collected Heap Subramanian Ramaswamy & Vance Morrison page 13 Event Tracing Event Tracing for Windows Basic Instincts Collection and Array Initializers in Visual Basic 2010 Generating Documents from SharePoint Using Open XML Adrian Spotty Bowles page 20 Content Controls Data Points Eric White page 52 Data Validation with Silverlight 3 and the DataForm John Papa page 30 Cutting Edge Data Binding in ASP.NET AJAX 4.0 Dino Esposito page 36 Patterns in Practice Functional Programming Core Instrumentation Events in Windows 7, Part 2 for Everyday .NET Developers MSDN Magazine Dr. Insung Park & Alex Bendetov page 60 Jeremy Miller page 68 Service Station Building RESTful Clients THIS MONTH at msdn.microsoft.com/magazine: Jon Flanders page 76 CONTRACT-FIRST WEB SERVICES: Schema-Based Development Foundations with Windows Communication Foundation Routers in the Service Bus Christian Weyer & Buddihke de Silva Juval Lowy page 82 TEST RUN: Partial Anitrandom String Testing Concurrent Affairs James McCaffrey Four Ways to Use the Concurrency TEAM SYSTEM: Customizing Work Items Runtime in Your C++ Projects Rick Molloy page 90 OCTOBER Brian A. Randell USABILITY IN PRACTICE: Getting Inside Your Users’ Heads 2009 Charles B. Kreitzberg & Ambrose Little Vol 24 No 10 Vol OCTOBER 2009 VOL 24 NO 10 OCTOBER 2009 VOLUME 24 NUMBER 10 LUCINDA ROWLEY Director EDITORIAL: [email protected] HOWARD DIERKING Editor-in-Chief WEB SITE MICHAEL RICHTER Webmaster CONTRIBUTING EDITORS Don Box, Keith Brown, Dino Esposito, Juval Lowy, Dr. -

Teamcity 7.1 Documentation.Pdf
1. TeamCity Documentation . 4 1.1 What's New in TeamCity 7.1 . 5 1.2 What's New in TeamCity 7.0 . 14 1.3 Getting Started . 26 1.4 Concepts . 30 1.4.1 Agent Home Directory . 31 1.4.2 Agent Requirements . 32 1.4.3 Agent Work Directory . 32 1.4.4 Authentication Scheme . 33 1.4.5 Build Agent . 33 1.4.6 Build Artifact . 34 1.4.7 Build Chain . 35 1.4.8 Build Checkout Directory . 36 1.4.9 Build Configuration . 37 1.4.10 Build Configuration Template . 38 1.4.11 Build Grid . 39 1.4.12 Build History . 40 1.4.13 Build Log . 40 1.4.14 Build Number . 40 1.4.15 Build Queue . 40 1.4.16 Build Runner . 41 1.4.17 Build State . 41 1.4.18 Build Tag . 42 1.4.19 Build Working Directory . 43 1.4.20 Change . 43 1.4.21 Change State . 43 1.4.22 Clean Checkout . 44 1.4.23 Clean-Up . 45 1.4.24 Code Coverage . 46 1.4.25 Code Duplicates . 47 1.4.26 Code Inspection . 47 1.4.27 Continuous Integration . 47 1.4.28 Dependent Build . 47 1.4.29 Difference Viewer . 49 1.4.30 Guest User . 50 1.4.31 History Build . 51 1.4.32 Notifier . 51 1.4.33 Personal Build . 52 1.4.34 Pinned Build . 52 1.4.35 Pre-Tested (Delayed) Commit . 52 1.4.36 Project . 53 1.4.37 Remote Run . .. -

ASP.NET SQL Server
CYAN YELLOW MAGENTA BLACK PANTONE 123 C BOOKS FOR PROFESSIONALS BY PROFESSIONALS® THE EXPERT’S VOICE® IN SQL SERVER Companion eBook Available Pro ASP.NET for SQL Server: High Performance Data Access for Web Developers Pro Dear Reader, ASP.NET ASP.NET As web developers, we work with ASP.NET and SQL Server by using a rich toolkit of databound controls and database functionality that promises great Pro performance and productivity gains after we know how to use it properly. Unfortunately, that toolkit is cluttered with a wide spectrum of features—some ideal for the one-man shop building a tiny application, and others aimed at large developer teams producing websites used by thousands of people. This book carves out a path for the senior developer who needs to produce a professional website that will perform well under high load. I focus on what a senior developer should know and use daily while also for explaining which features to avoid and why. There are several, little-known features ASP.NET in ASP.NET and SQL Server that work very well together without requiring much effort. These features get detailed coverage. Each chapter includes a full sample project, to help you learn by digging into some good code. These projects are for designed to keep you engaged while using them to understand the chapter topics in greater detail. What you will learn from this book are techniques that allow you to leverage SQL Server the many performance and productivity improvements that have been provided ASP.NET and SQL Server. These improvements will help you produce better SQL Server websites with the desired results right from the start. -

Appendixes APPENDIX A
PART 8 Appendixes APPENDIX A COM and .NET Interoperability The goal of this book was to provide you with a solid foundation in the C# language and the core services provided by the .NET platform. I suspect that when you contrast the object model provided by .NET to that of Microsoft’s previous component architecture (COM), you’ll no doubt be con- vinced that these are two entirely unique systems. Regardless of the fact that COM is now considered to be a legacy framework, you may have existing COM-based systems that you would like to inte- grate into your new .NET applications. Thankfully, the .NET platform provides various types, tools, and namespaces that make the process of COM and .NET interoperability quite straightforward. This appendix begins by examin- ing the process of .NET to COM interoperability and the related Runtime Callable Wrapper (RCW). The latter part of this appendix examines the opposite situation: a COM type communicating with a .NET type using a COM Callable Wrapper (CCW). ■Note A full examination of the .NET interoperability layer would require a book unto itself. If you require more details than presented in this appendix, check out my book COM and .NET Interoperability (Apress, 2002). The Scope of .NET Interoperability Recall that when you build assemblies using a .NET-aware compiler, you are creating managed code that can be hosted by the common language runtime (CLR). Managed code offers a number of ben- efits such as automatic memory management, a unified type system (the CTS), self-describing assemblies, and so forth. As you have also seen, .NET assemblies have a particular internal compo- sition. -

Special Characters Numbers
Index ■Special Characters AddServiceEndpoint( ) member, ServiceHost type, #define, preprocessor directive, 317–319 1032 #elif, preprocessor directive, 317–318 ADO.NET #else, preprocessor directive, 317–318 additional namespaces, 763–764 #endif, preprocessor directive, 317–318 vs. ADO classic, 759–760 #endregion, preprocessor directive, 317 application configuration files, 769–770 #if, preprocessor directive, 317–318 asynchronous data access, 792–793 #region, preprocessor directive, 317 autogenerated data components, 824–825 #undef, preprocessor directive, 317–319 autogenerating SQL commands, 816–817 % modulo operator, C#, 1097 autoincrementing, 797 & operator, pointer types, 312–313 binding DataTables to user interfaces, 804, 806 * operator, pointer types, 312–313 Command object, 781–782 ?? operator, 133 connected layer, 778 += operator, 610 connected vs. disconnected layer, 760 <%@Page%> directive attribute, ASP.NET, 846 connecting to database, Visual Studio 2005, 776 <%Import%> directive, ASP.NET, 846–847 connection objects, 779–780 => token, 1098 ConnectionStringBuilder object, 780–781 ? suffix, nullable types, 131 connectionStrings element, application configuration, 774–775 ■Numbers data access libraries, 1130 data adapter objects, 811–812 3D graphics graphical service, WPF, 1012 data providers, 760, 762 3D rendered animation, 970 data wizards, 822–825 100% code approach, 1048 DataColumn objects, 796, 798 ■ DataRelation objects, 817–820 A DataRow objects, 798–799, 801 A# programming language, 8 DataRow.RowState property, 799–800 Abort( -
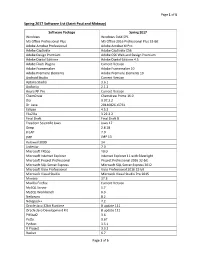
Spring 2017 Software List (Saint Paul and Midway)
Page 1 of 5 Spring 2017 Software List (Saint Paul and Midway) Software Package Spring 2017 Windows Windows 7x64 SP1 MS Office Professional Plus MS Office 2016 Professional Plus 32-Bit Adobe Acrobat Professional Adobe Acrobat XI Pro Adobe Captivate Adobe Captivate CS6 Adobe Design Premium Adobe CS6 Web and Design Premium Adobe Digital Editions Adobe Digital Editions 4.5 Adobe Flash Plugins Current Version Adobe Framemaker Adobe Framemaker 10 Adobe Premiere Elements Adobe Premiere Elements 10 Android Studio Current Version Aptana Studio 3.6.1 Audacity 2.1.2 Axure RP Pro Current Version ChemDraw Chemdraw Prime 16.0 Dia 0.97.2.2 Dr. Java 20140826-r5761 Eclipse 4.5.2 FileZilla 3.22.2.2 Final Draft Final Draft 8 Freedom Scientific Jaws Jaws 17 Gimp 2.8.18 JFLAP 7.0 JMP JMP 13 Kurzweil 3000 14 Lodestar 7.0 Microsoft FXCop 10.0 Microsoft Internet Explorer Internet Explorer 11 with Silverlight Microsoft Project Professional Project Professional 2016 32-bit Microsoft SQL Server Express Microsoft SQL Server Express 2012 Microsoft Visio Professional Visio Professional 2016 32-bit Microsoft Visual Studio Microsoft Visual Studio Pro 2015 Minitab 17.3 Mozilla Firefox Current Version MySQL Server 5.7 MySQL Workbench 6.3 Netbeans 8.2 Notepad++ 7.2 Oracle Java 32bit Runtime 8 update 111 Oracle Java Development Kit 8 update 111 PHStat2 3.6 Putty 0.67 Python 3.5.1 R Project 3.3.2 Racket 6.7 Page 1 of 5 Page 2 of 5 Software Package Spring 2017 Raptor Current Version SAP Client SAP Client 7.4.9 SAP Lumira 1.31.1 SAP Crystal Reports Current Version SPSS SPSS -

Discovering Ironpython
PART I Introducing IronPython ⊲⊲ CHAPTER 1: Discovering IronPython ⊲⊲ CHAPTER 2: Understanding the IronPython Basics COPYRIGHTED MATERIAL 548592c01.indd 1 2/24/10 12:47:07 PM 548592c01.indd 2 2/24/10 12:47:08 PM 1 Discovering IronPython WHAT’S IN THIS CHAPTER? ➤➤ Understanding why you want to add IronPython to your developer toolbox ➤➤ Obtaining and installing IronPython on your machine ➤➤ Understanding some underlying basics of how IronPython works ➤➤ Using IronPython at the console and within a window ➤➤ Designing and building a simple application IronPython: It sounds like some kind of metal snake infesting your computer, but it isn’t. IronPython is the .NET version of the open source Python language (http://www .python.org/). Python is a dynamic language that can greatly enhance your programming experience, help you create applications in less time, and make the applications you create significantly more responsive to user needs. Of course, you’ve heard these promises before from other languages. This chapter helps you understand how IronPython delivers on these promises in specific situations. The smart developer soon learns that every language serves specific needs and might not work well in others. So this chapter isn’t here to blow smoke at you — once you complete it, you’ll understand the strengths and weaknesses of IronPython. Of course, you’ll need to obtain a copy of IronPython before you can use it because Visual Studio doesn’t include IronPython as part of the default installation. This chapter helps you get IronPython installed on your system and tells you about some options you may want to install as well. -

NET Hacking & In-Memory Malware
.NET Hacking & In-Memory Malware Shawn Edwards Shawn Edwards Cyber Adversarial Engineer The MITRE Corporation Hacker Maker Learner Take stuff apart. Change it. Put Motivated by an incessant Devoted to a continuous effort it back together. desire to create and craft. of learning and sharing knowledge. Red teamer. Adversary Numerous personal and emulator. professional projects. B.S. in Computer Science. Adversary Emulation @ MITRE • Red teaming, but specific threat actors • Use open-source knowledge of their TTPs to emulate their behavior and operations • Ensures techniques are accurate to real world • ATT&CK (Adversarial Tactics Techniques and Common Knowledge) • Public wiki of real-world adversary TTPs, software, and groups • CALDERA • Modular Automated Adversary Emulation framework Adversary Emulation @ MITRE • ATT&CK • Adversarial Tactics Techniques and Common Knowledge • Public wiki of real-world adversary TTPs, software, and groups • Lets blue team and red team speak in the same language • CALDERA • Modular Automated Adversary Emulation framework • Adversary Mode: • AI-driven “red team in a box” • Atomic Mode: • Define Adversaries, give them abilities, run operations. Customize everything at will. In-Memory Malware • Is not new • Process Injection has been around for a long time • Typically thought of as advanced tradecraft; not really • Surged in popularity recently • Made easier by open-source or commercial red team tools • For this talk, only discuss Windows malware • When relevant, will include the ATT&CK Technique ID In-Memory -

20 Le Regular Expression Seconda Parte
������������������������������������������������������������� ��������������������������������������� ������������������������������������������������������������ ����������������������������� ���������������������������������� ��������������������������������������������������� ������������������������������������������������������������������������������������������������������������������������������������� 400X302 Computer programming.ind1 1 20-03-2007 10:29:34 ������������������������������������������������������������� ��������������������������������������� ������������������������������������������������������������ ����������������������������� ���������������������������������� ��������������������������������������������������� ������������������������������������������������������������������������������������������������������������������������������������� 400X302 Computer programming.ind1 1 20-03-2007 10:29:34 I N V E T R I N A V B J 7 5 Doing Objects Object-Oriented Programming Access Data in Visual Basic 2005 Languages: Interpretation Analysis Cookbook di D. Kurata di Craig - I. D. di K.Bluttman - W.S. Freeze Addison Wesley Springer O’ Reilly 552 pp - 46,95 Euro 256 pp - 36,70 Euro 366 pp - 47,20 Euro ISBN 9780321320490 ISBN 9781846287732 ISBN 9780596101220 Scrivi a [email protected] specificando nell’oggetto della e-mail: IN VETRINA VBJ n. 75 oppure inviaci il coupon al numero di fax 0587/732232 Potrai acquistare i libri qui riportati con uno SCONTO ECCEZIONALE del 10% anche se acquisti solo un libro oppure del 20% -

Surviving C#-Codereviews
Rainer Stropek | time cockpit Surviving C#-Codereviews Your Host Rainer Stropek Developer, Entrepreneur Azure MVP, MS Regional Director Trainer at IT-Visions Contact software architects gmbh [email protected] Twitter: @rstropek Agenda Es ist nicht unüblich, dass externe oder interne Kunden Experten beauftragen, die C#- Codebasis eines Projekts zu begutachten. Rainer Stropek, langjähriger MVP und MS Regional Director, macht solche Projekte regelmäßig. In dieser Session erklärt er, worauf er dabei Wert legt. • Welche Tools setzt er ein, um Verbesserungspotenziale zu suchen? • Wie findet er in großen Codebasen rasch die kritischen Bereiche? • Welche Best und Worst Practices kontrolliert er? • Wie würde er ein C#-Projekt aufsetzen, das jeden Codereview glänzend bestehen soll? Auf solche Fragen wird Rainer in der Session eingehen. Sie erhalten eine konkrete Checkliste von Punkten, die Sie bei Ihren Projekten beachten können, um die Qualität Ihres gelieferten C#- Codes noch weiter zu verbessern. Agenda Introduction Reviewing the process Why Code Review Projects? Automation My Rules for Review Projects Source code handling Reviewing the code State of the art? Development process Basics Team management Coding guidelines Code structure Summary Documentation Recommendations Testing Performance Security Why Code Review Projects? Why Code Review Projects? M&A Buy company or source of a product New management team Customer-vendor relationship Tip: Make code review criteria part of contract Large customers buys software strategic for their business Frequently: Large customer, small vendor Team wants/needs external advice Reviewer is a kind of external coach Accompanying Reviews Security review Legal reviews Who owns the source code? License terms of dependencies? Compliance to policies (internal/external) Standard certifications E.g.