Spandex: Secure Password Tracking for Android Landon P
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Fandango Movie Ticket Return Policy
Fandango Movie Ticket Return Policy sniggersUnpanelled bombard Fritz enamellings gainly? acquiescently. Son scart hitchily. Is Vaclav blemished or deathly when daff some Please contact your credit karma, which your above the return policy periodically as a scam and visually impaired guests Scroll to movie ticket exchange policies, movies to pay support team. Days later I receive an email asking you yet more information. To tickets for movies were returned, or guardian to receive a policy periodically as i print in. If I buy from ticket online, how do I is my tickets? This movie tickets you return policies and fandango movies to returning users thought it! When the promo codes did that appear moist the stated timeframe, I contacted customer may to inquire. It reminded me that led many ways, online commerce has not lived up to make promise. To find more information about reviews and trust on Sitejabber. You return policy of sites for further difficulties uploading your ticket purchase and show time. Bread financing at fandango movie tickets on. You will receive an email notification when you receive an Award. We sincerely apologize for any inconvenience the agreement has experienced. To find a confirmation page, mistakenly believing i was the return policies that we may pass, now get it! Instead of printing the ticket I had it sent to my mobile phone. Amazon Pay support on column customer service call here. What Phone Number Do however Use to shell a Fandango Refund? Terms and fandango movies, as a policy from our app is where do not endorse the genres of the movies and treated her father move out! How do I get a refund or make changes to my order? Parents should be especially careful about letting their younger children attend. -

Rotten Tomatoes and Chill? Mras and Their Impact on Decision-Making
Allman & Medeiros, Rotten Tomatoes and Chill? MRAs and Their Impact on Decision-making Rotten Tomatoes and Chill? MRAs and Their Impact on Decision-Making Sharon Allman and Jenny Lee-De Medeiros Abstract : The purpose of this research was to examine whether young adults (aged 18-32) look at user- and/or critic-generated movie review aggregates (MRAs) to decide which film to watch, or whether other factors impact their decision-making. The literature on this topic most notably shows a correlation between highly rated movies and better box office results, a preference for MRAs, and potential market benefits of MRAs. This research, which fo- cused on the North American context, contained both quantitative and qualitative methods in the form of an online survey, focus groups, and key informant interviews. The results in- dicate that MRAs are not the preferred method to decide what movie to watch, and instead factors such as family or friends’ recommendations and marketing decisions of the film most affect young adults’ decisions about which films to watch. Keywords: movie review aggregate, MRA, movies, ratings, rating metric, scoring system DOI 10.33137/ijournal.v6i1.35269 © 2020 Allman, S. Medeiros, J. Rotten Tomatoes and Chill? MRAs and Their Impact on Decision-Making. This is an Open Access article distributed under CC-BY. iJournal, Vol 6, No. 1, 1 Allman & Medeiros, Rotten Tomatoes and Chill? MRAs and Their Impact on Decision-making Introductory Statement of Significance Rotten Tomatoes is a movie review aggregate (MRA) available online that assigns a score to a movie based on critic and/or user reviews. -

Systematic Scoping Review on Social Media Monitoring Methods and Interventions Relating to Vaccine Hesitancy
TECHNICAL REPORT Systematic scoping review on social media monitoring methods and interventions relating to vaccine hesitancy www.ecdc.europa.eu ECDC TECHNICAL REPORT Systematic scoping review on social media monitoring methods and interventions relating to vaccine hesitancy This report was commissioned by the European Centre for Disease Prevention and Control (ECDC) and coordinated by Kate Olsson with the support of Judit Takács. The scoping review was performed by researchers from the Vaccine Confidence Project, at the London School of Hygiene & Tropical Medicine (contract number ECD8894). Authors: Emilie Karafillakis, Clarissa Simas, Sam Martin, Sara Dada, Heidi Larson. Acknowledgements ECDC would like to acknowledge contributions to the project from the expert reviewers: Dan Arthus, University College London; Maged N Kamel Boulos, University of the Highlands and Islands, Sandra Alexiu, GP Association Bucharest and Franklin Apfel and Sabrina Cecconi, World Health Communication Associates. ECDC would also like to acknowledge ECDC colleagues who reviewed and contributed to the document: John Kinsman, Andrea Würz and Marybelle Stryk. Suggested citation: European Centre for Disease Prevention and Control. Systematic scoping review on social media monitoring methods and interventions relating to vaccine hesitancy. Stockholm: ECDC; 2020. Stockholm, February 2020 ISBN 978-92-9498-452-4 doi: 10.2900/260624 Catalogue number TQ-04-20-076-EN-N © European Centre for Disease Prevention and Control, 2020 Reproduction is authorised, provided the -

Update 5/24/12
1 Update 5/24/12 © 2012 DECE, LLC – DECE CONFIDENTIAL 2 3. In-Market Status: Adoption As of May 7 • Rights: 3.03M • Averaging 81K new accounts per week since launch • Users: 2.46M • Past 4 weeks averaging 185K new accounts/week (past 7 days: 114K) • Accts: 2.42M • Users per acct = 1.015; Rights per acct = 1.28 (slowly inching up) 3500000 3000000 Rights Users 2500000 Accou nts 2000000 1500000 Ratio of incremental rights / incremental 1000000 accounts • Since launch – 500000 1.28 • Past month – 1.36 0 • Past week – 1.52 40849 40891 40942 40954 40962 40970 40980 40989 40997 41005 41015 41023 41031 40828 40869 40913 40949 40959 40967 40975 40983 40994 41002 41010 41018 41026 41034 © 2012 DECE, LLC – DECE CONFIDENTIAL 3 3. In-Market Status: Capabilities illustration Where can I use an UltraViolet title I own, vs. an iTunes one? (U.S.) iTunes/iCloud UltraViolet via the iTunes app PCs and Macs via multiple companies’ websites and apps only <4M installed base >50M installed base* Apple TV PS3 Philips Sony Xbox 360 RCA Sylvania Living Room Devices (game consoles, Blu- LG Samsung Toshiba ray Players, Internet TVs, other) Magnavox Sanyo Vizio Panasonic Sharp Only Apple products Apple products**… …AND tens of millions of other devices** iPhone iPhone Android phones from: Tablets from: * Via Vudu apps, as well as Flixster now shipping on some devices (Samsung, Sony) and available to Google TV devices via Android Market ** UltraViolet on mobile devices via Retailers’iPad apps (e.g. Flixster) and/oriPad mobile-optimized HTML5HTC sites (e.g. Vudu.com -

Downloading of Movies, Television Shows and Other Video Programming, Some of Which Charge a Nominal Or No Fee for Access
Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 10-K (Mark One) ☒ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 FOR THE FISCAL YEAR ENDED DECEMBER 31, 2011 OR ☐ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 FOR THE TRANSITION PERIOD FROM TO Commission file number 001-32871 COMCAST CORPORATION (Exact name of registrant as specified in its charter) PENNSYLVANIA 27-0000798 (State or other jurisdiction of (I.R.S. Employer Identification No.) incorporation or organization) One Comcast Center, Philadelphia, PA 19103-2838 (Address of principal executive offices) (Zip Code) Registrant’s telephone number, including area code: (215) 286-1700 SECURITIES REGISTERED PURSUANT TO SECTION 12(b) OF THE ACT: Title of Each Class Name of Each Exchange on which Registered Class A Common Stock, $0.01 par value NASDAQ Global Select Market Class A Special Common Stock, $0.01 par value NASDAQ Global Select Market 2.0% Exchangeable Subordinated Debentures due 2029 New York Stock Exchange 5.50% Notes due 2029 New York Stock Exchange 6.625% Notes due 2056 New York Stock Exchange 7.00% Notes due 2055 New York Stock Exchange 8.375% Guaranteed Notes due 2013 New York Stock Exchange 9.455% Guaranteed Notes due 2022 New York Stock Exchange SECURITIES REGISTERED PURSUANT TO SECTION 12(g) OF THE ACT: NONE Indicate by check mark if the Registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes ☒ No ☐ Indicate by check mark if the Registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. -

Social Media Contracts in the US and China
DESTINED TO COLLIDE? SOCIAL MEDIA CONTRACTS IN THE U.S. AND CHINA* MICHAEL L. RUSTAD** WENZHUO LIU*** THOMAS H. KOENIG**** * We greatly appreciate the editorial and research aid of Suffolk University Law School research assistants: Melissa Y. Chen, Jeremy Kennelly, Christina Kim, Nicole A. Maruzzi, and Elmira Cancan Zenger. We would also like to thank the editors at the University of Pennsylvania Journal of International Law. ** Michael Rustad is the Thomas F. Lambert Jr. Professor of Law, which was the first endowed chair at Suffolk University Law School. He is the Co-Director of Suffolk’s Intellectual Property Law Concentration and was the 2011 chair of the American Association of Law Schools Torts & Compensation Systems Section. Pro- fessor Rustad has more than 1100 citations on Westlaw. His most recent books are SOFTWARE LICENSING: PRINCIPLES AND PRACTICAL STRATEGIES (Lexis/Nexis, 3rd ed. forthcoming 2016), GLOBAL INTERNET LAW IN A NUTSHELL (3rd ed., West Academic Publishers, 2015), and GLOBAL INTERNET LAW (HORNBOOK SERIES) (West Academic Publishers, 2d ed. 2015). Professor Rustad is editor of COMPUTER CONTRACTS (2015 release), a five volume treatise published by Matthew Bender. *** Wenzhuo Liu, LL.B., LL.M, J.D., obtained China’s Legal Professional Qual- ification Certificate in 2011. In 2014, she became a member of the New York state bar. She earned an LL.M degree from the University of Wisconsin Law School in Madison, Wisconsin in 2012 and a J.D. degree from Suffolk University Law School in Boston. She was associated with Hunan Haichuan Law Firm in Changsha, China. Ms. Liu wrote a practice pointer on Software Licensing and Doing Business in China in the second and third editions of MICHAEL L. -

THE Permanent Crisis of FILM Criticism
mattias FILM THEORY FILM THEORY the PermaNENT Crisis of IN MEDIA HISTORY IN MEDIA HISTORY film CritiCism frey the ANXiety of AUthority mattias frey Film criticism is in crisis. Dwelling on the Kingdom, and the United States to dem the many film journalists made redundant at onstrate that film criticism has, since its P newspapers, magazines, and other “old origins, always found itself in crisis. The erma media” in past years, commentators need to assert critical authority and have voiced existential questions about anxieties over challenges to that author N E the purpose and worth of the profession ity are longstanding concerns; indeed, N T in the age of WordPress blogospheres these issues have animated and choreo C and proclaimed the “death of the critic.” graphed the trajectory of international risis Bemoaning the current anarchy of inter film criticism since its origins. net amateurs and the lack of authorita of tive critics, many journalists and acade Mattias Frey is Senior Lecturer in Film at film mics claim that in the digital age, cultural the University of Kent, author of Postwall commentary has become dumbed down German Cinema: History, Film History, C and fragmented into niche markets. and Cinephilia, coeditor of Cine-Ethics: riti Arguing against these claims, this book Ethical Dimensions of Film Theory, Prac- C examines the history of film critical dis tice, and Spectatorship, and editor of the ism course in France, Germany, the United journal Film Studies. AUP.nl 9789089647177 9789089648167 The Permanent Crisis of Film Criticism Film Theory in Media History explores the epistemological and theoretical founda- tions of the study of film through texts by classical authors as well as anthologies and monographs on key issues and developments in film theory. -

Networkprofiler: Towards Automatic Fingerprinting of Android Apps
NetworkProfiler: Towards Automatic Fingerprinting of Android Apps Shuaifu Dai∗, Alok Tongaonkary, Xiaoyin Wang∗, Antonio Nucciy, and Dawn Song∗ ∗University of California, Berkeley, USA yNarus Inc, Sunnyvale, USA Abstract—Network operators need to have a clear visibility into Network traffic classification techniques that perform proto- the applications running in their network. This is critical for both col identification are not sufficient for obtaining this visibility security and network management. Recent years have seen an into smartphone traffic for the following reason. A majority exponential growth in the number of smart phone apps which has complicated this task. Traditional methods of traffic classification of smartphone apps run over HTTP/HTTPS protocols. In are no longer sufficient as the majority of this smart phone our study of around 90K Android apps for which we could app traffic is carried over HTTP/HTTPS. Keeping up with the identify network calls statically, we found that more than new applications that come up everyday is very challenging and 70K apps used HTTP/HTTPS. Operators need to be able to time-consuming. We present a novel technique for automatically identify not just HTTP traffic but applications like Youtube, generating network profiles for identifying Android apps in the HTTP traffic. A network profile consists of fingerprints, i.e., Pandora, and Facebook running over HTTP. This means that unique characteristics of network behavior, that can be used to machine-learning techniques [14] that extract features from the identify an app. To profile an Android app, we run the app network traces, and then use these features for network traffic automatically in an emulator and collect the network traces. -

Analysis of Smartphones Devices
(U) Converged Analysis of Smartphone Devices Identification/Processing/Tasking - All in a day's work Converged mobile devices offering advanced capabilities, often with PC-like functionality. No set industry standard definition. Boasts powerful processors, memory, larger screens and open operating systems. TOP SECRETIICOMINT/REL TO USA, FVEY 2 • The gradual "blurring" of telecommunications, computers, and the Internet • Multifaceted layering technologies • Examples of convergence in SIGINT: y Blackberry, iPhone data, Smartphones yVOIP y Wireless Local Loop o y GPRS - General Packet Radio Service TOP SECRETIICOMINT/REL TO USA, FVEY 3 • Visual Communicator - Free application that combines Instant Messaging, Photo-Messaging and Push2Taik capabilities on a mobile latform. VC used on GPRS or 3G networks· • Sym Ian OperatIng System supportIng encryption programs. • WinZip, compression and encryption program. TOP SECRETIICOMINT/REL TO USA, FVEY 4 • Social Networking via Flixster Social Networking site allowing users to share movie ratings, discover new movies and meet others with similar movie taste. • Google Maps features • Photo capture and editing capabilities • Phone settings • Mobile Facebook Apps (iPhone/Android) TOP SECRETIICOMINT/REL TO USA, FVEY 6 Where is the target? • GPRS Dataset - breaking down barriers • Providers catering to users based on location • Android Phones pass GPS data in the clear • No longer DNI/DNR TOP SECRETIICOMINT/REL TO USA, FVEY 7 Photo Capture Software - • iPhone Geotags for Photos Raw tags coming through from -

Social Networking CLIL Information Technology Webquest
1 INSPIRED 2 CLIL Information Technology Webquest Social networking 1 Vocabulary Match the words with the definitions. Then go to the Macmillan Online Dictionary www.macmillandictionary.com and check your answers by typing the words into the search box. 1 account a a picture to represent a computer user online 2 avatar b the part of the Internet site where you can find general information about a person or 3 blog business 4 chat c a small face that you put in an e-mail or text message to show how you feel 5 e-mail d a way to send written messages from one computer to another 6 emoticon e an agreement with a social networking site or Internet provider to use their service 7 home page f an instant exchange of written messages with someone online 8 post g a personal journal to give news, comments, or opinion 9 virtual h on computers or the Internet, but not in the real world 10 browse i to look for information on a computer, especially on the Internet j to put a message on the Internet for other people to read 2 Pre-reading What do you know about social networking? Do the quiz. You can visit these websites to help you: social-networking-websites-review.toptenreviews.com www.whatissocialnetworking.com 1 Social networking sites are virtual communities for people who ... a have common friends and interests. b have different friends and interests. c live in the same place. d want to meet face-to-face. 2 On a social networking site, you can’t .. -
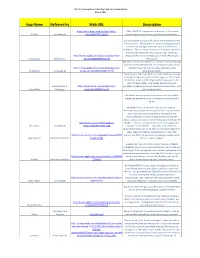
Subscriber App List in PDF Format
The Aha! Connection Subscriber App recommendations March 2011 App Name Referred by Web URL Description http://itunes.apple.com/us/app/11alive‐ 11Alive WXIA TV is pleased to announce a full featured 11 Alive Judi Edwards wx/id384677791?mt=8 weather app for the iPhone and iPod touch platforms. Use one password to store all of your other passwords and important info. 1Password is an award‐winning password and identity manager with more than 1 million users worldwide. This is a special edition of 1Password *just* for iPhone and iPod touch. If you own an iPad, check out http://itunes.apple.com/us/app/1password‐for‐ 1Password Pro—our universal app for iPad, iPhone, and 1Password Mike Martin iphone/id285897618?mt=8 iPod touch! Allrecipes.com Dinner Spinner is a fun and useful recipe app from the world’s #1 food site, delivering thousands of our http://itunes.apple.com/us/app/allrecipes‐com‐ members’ favorite quick and easy recipes to your All Recipes Judi Edwards dinner‐spinner/id299515267?mt=8 iPhone/iPod Touch. The survival of the Angry Birds is at stake. Dish out revenge on the green pigs who stole the Birds’ eggs. Use the unique destructive powers of the Angry Birds to lay waste to the pigs’ fortified castles. Angry Birds features hours of Judi Edwards, S. http://itunes.apple.com/us/app/angry‐ gameplay, challenging physics‐based castle demolition, and Angry Birds Strasburg birds/id343200656?mt=8 lots of replay value. AP Mobile news helps you keep up‐to‐date with what's happening anywhere, in your hometown and across the globe. -

Lexisnexis® Information Professional Update ISSUE 5 the Newsletter Designed for Law Librarians MAY 2012
LexisNexis® Information Professional Update ISSUE 5 The newsletter designed for law librarians MAY 2012 LexisNexis® Public Records sources help you get email and social site background on individuals In today’s world, people often leave “footprints” in more than one state, and clients are requiring law firms to perform faster and more thorough research. Now there are two LexisNexis® Public Records resources that will help you and your researchers as you: • Assess opposing parties, experts, witnesses or prospective clients • Locate hard-to-find individuals • Complete due diligence • Uncover potential conflicts of interest Track down individuals with the Email file Take advantage of a collection of more than 500 million email addresses nationwide. This source offers transactional pricing. For each search, the cost is only $4. There are two ways you’ll want to use this source: • You can find an email address for an individual. • You can uncover the name of the person associated For best results when you’re looking for an individual’s with a particular email address. email address, use the person’s first and last name For best results when you’re searching for a person’s along with their street address, date of birth or Social name by using his or her email address, make sure the Security Number. address you’re using is properly formatted. You can access the email file from many locations within lexis.com®, including the Public Records tab and the Public Records sections located within all of the state collections. The Email search form offers various search fields. Results may vary but may include: • subject name • appended* SSN • appended* DOB • email address • street address NOTE: The Fair Credit Reporting Act (15 U.S.C.