David Gries Advisory Board F.L
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Software Tools: a Building Block Approach
SOFTWARE TOOLS: A BUILDING BLOCK APPROACH NBS Special Publication 500-14 U.S. DEPARTMENT OF COMMERCE National Bureau of Standards ] NATIONAL BUREAU OF STANDARDS The National Bureau of Standards^ was established by an act of Congress March 3, 1901. The Bureau's overall goal is to strengthen and advance the Nation's science and technology and facilitate their effective application for public benefit. To this end, the Bureau conducts research and provides: (1) a basis for the Nation's physical measurement system, (2) scientific and technological services for industry and government, (3) a technical basis for equity in trade, and (4) technical services to pro- mote public safety. The Bureau consists of the Institute for Basic Standards, the Institute for Materials Research, the Institute for Applied Technology, the Institute for Computer Sciences and Technology, the Office for Information Programs, and the ! Office of Experimental Technology Incentives Program. THE INSTITUTE FOR BASIC STANDARDS provides the central basis within the United States of a complete and consist- ent system of physical measurement; coordinates that system with measurement systems of other nations; and furnishes essen- tial services leading to accurate and uniform physical measurements throughout the Nation's scientific community, industry, and commerce. The Institute consists of the Office of Measurement Services, and the following center and divisions: Applied Mathematics — Electricity — Mechanics — Heat — Optical Physics — Center for Radiation Research — Lab- oratory Astrophysics^ — Cryogenics^ — Electromagnetics^ — Time and Frequency*. THE INSTITUTE FOR MATERIALS RESEARCH conducts materials research leading to improved methods of measure- ment, standards, and data on the properties of well-characterized materials needed by industry, commerce, educational insti- tutions, and Government; provides advisory and research services to other Government agencies; and develops, produces, and distributes standard reference materials. -

Blockchain Database for a Cyber Security Learning System
Session ETD 475 Blockchain Database for a Cyber Security Learning System Sophia Armstrong Department of Computer Science, College of Engineering and Technology East Carolina University Te-Shun Chou Department of Technology Systems, College of Engineering and Technology East Carolina University John Jones College of Engineering and Technology East Carolina University Abstract Our cyber security learning system involves an interactive environment for students to practice executing different attack and defense techniques relating to cyber security concepts. We intend to use a blockchain database to secure data from this learning system. The data being secured are students’ scores accumulated by successful attacks or defends from the other students’ implementations. As more professionals are departing from traditional relational databases, the enthusiasm around distributed ledger databases is growing, specifically blockchain. With many available platforms applying blockchain structures, it is important to understand how this emerging technology is being used, with the goal of utilizing this technology for our learning system. In order to successfully secure the data and ensure it is tamper resistant, an investigation of blockchain technology use cases must be conducted. In addition, this paper defined the primary characteristics of the emerging distributed ledgers or blockchain technology, to ensure we effectively harness this technology to secure our data. Moreover, we explored using a blockchain database for our data. 1. Introduction New buzz words are constantly surfacing in the ever evolving field of computer science, so it is critical to distinguish the difference between temporary fads and new evolutionary technology. Blockchain is one of the newest and most developmental technologies currently drawing interest. -

An Introduction to Cloud Databases a Guide for Administrators
Compliments of An Introduction to Cloud Databases A Guide for Administrators Wendy Neu, Vlad Vlasceanu, Andy Oram & Sam Alapati REPORT Break free from old guard databases AWS provides the broadest selection of purpose-built databases allowing you to save, grow, and innovate faster Enterprise scale at 3-5x the performance 14+ database engines 1/10th the cost of vs popular alternatives - more than any other commercial databases provider Learn more: aws.amazon.com/databases An Introduction to Cloud Databases A Guide for Administrators Wendy Neu, Vlad Vlasceanu, Andy Oram, and Sam Alapati Beijing Boston Farnham Sebastopol Tokyo An Introduction to Cloud Databases by Wendy A. Neu, Vlad Vlasceanu, Andy Oram, and Sam Alapati Copyright © 2019 O’Reilly Media Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://oreilly.com). For more infor‐ mation, contact our corporate/institutional sales department: 800-998-9938 or [email protected]. Development Editor: Jeff Bleiel Interior Designer: David Futato Acquisitions Editor: Jonathan Hassell Cover Designer: Karen Montgomery Production Editor: Katherine Tozer Illustrator: Rebecca Demarest Copyeditor: Octal Publishing, LLC September 2019: First Edition Revision History for the First Edition 2019-08-19: First Release The O’Reilly logo is a registered trademark of O’Reilly Media, Inc. An Introduction to Cloud Databases, the cover image, and related trade dress are trademarks of O’Reilly Media, Inc. The views expressed in this work are those of the authors, and do not represent the publisher’s views. -

Edsger W. Dijkstra: a Commemoration
Edsger W. Dijkstra: a Commemoration Krzysztof R. Apt1 and Tony Hoare2 (editors) 1 CWI, Amsterdam, The Netherlands and MIMUW, University of Warsaw, Poland 2 Department of Computer Science and Technology, University of Cambridge and Microsoft Research Ltd, Cambridge, UK Abstract This article is a multiauthored portrait of Edsger Wybe Dijkstra that consists of testimo- nials written by several friends, colleagues, and students of his. It provides unique insights into his personality, working style and habits, and his influence on other computer scientists, as a researcher, teacher, and mentor. Contents Preface 3 Tony Hoare 4 Donald Knuth 9 Christian Lengauer 11 K. Mani Chandy 13 Eric C.R. Hehner 15 Mark Scheevel 17 Krzysztof R. Apt 18 arXiv:2104.03392v1 [cs.GL] 7 Apr 2021 Niklaus Wirth 20 Lex Bijlsma 23 Manfred Broy 24 David Gries 26 Ted Herman 28 Alain J. Martin 29 J Strother Moore 31 Vladimir Lifschitz 33 Wim H. Hesselink 34 1 Hamilton Richards 36 Ken Calvert 38 David Naumann 40 David Turner 42 J.R. Rao 44 Jayadev Misra 47 Rajeev Joshi 50 Maarten van Emden 52 Two Tuesday Afternoon Clubs 54 2 Preface Edsger Dijkstra was perhaps the best known, and certainly the most discussed, computer scientist of the seventies and eighties. We both knew Dijkstra |though each of us in different ways| and we both were aware that his influence on computer science was not limited to his pioneering software projects and research articles. He interacted with his colleagues by way of numerous discussions, extensive letter correspondence, and hundreds of so-called EWD reports that he used to send to a select group of researchers. -

A Common Programming Language for the Depart Final Ment of Defenses-Background and Technical January -December 1975 1 Requirements «
Approved for public release; distribution unlimited I 1 PAPER P-1191 A COMMON PROGRAMMING LANGUAGE 1 FOR THE DEPARTMENT OF DEFENSE - - I BACKGROUND AND TECHNICAL REQUIREMENTS I I D. A. Fisher June 1976 I 1 I I I I INSTITUTE FOR DEFENSE ANALYSES I SCIENCE AND TECHNOLOGY DIVISION I I IDA Log No. HQ 76-18215 I Cop-)*- > . -JJ . of 155. cop I ess Approved for public release; distribution unlimited I I I I The work reported in this document was conducted under contract DAHC15 73 C 0200 for the Department of Defense. The publication I of this IDA Paper does not indicate endorsement by the Department of Defense, nor should the contents be construed as reflecting the official position of that agency. I I I I This document has been approved for public release, distribution is unlimited. I I 1 1 1 I I I Copyright IDA/Scanned June 2007 I 1 Approved for public release; distribution unlimited UNCLASSIFIED - ©; ; ; : ;" -; .©, . 1 SECURITY CLASSIFICATION OF THIS PAGE CWnen DM* Entered; READ INSTRUCTIONS REPORT DOCUMENTATION PAGE BEFORE COMPLETING FORM ). RECIPIENT©S CATALOG NUMBER 1 Paper P-J.191. 4. TITLE fend Subtitle.) 5. TYPE Of REPORT e PERIOD COVERED A Common Programming Language for the Depart Final ment of Defenses-Background and Technical January -December 1975 1 Requirements «. PERFORMING ORG. REPORT NUMBER P-1191 I. CONTRACT OR GRANT NUMBERflJ 1 DAHC15 73 C 0200 D.A, Fisher 10. PROGRAM ELEMENT. PROJECT TASK 1 INSTITUTE FOR DEFENSE ANALYSES AREA * WORK UNIT NUMBERS 400 Army-Navy Drive Task T-36 Arlington. Virginia 22202 11. -

Middleware-Based Database Replication: the Gaps Between Theory and Practice
Appears in Proceedings of the ACM SIGMOD Conference, Vancouver, Canada (June 2008) Middleware-based Database Replication: The Gaps Between Theory and Practice Emmanuel Cecchet George Candea Anastasia Ailamaki EPFL EPFL & Aster Data Systems EPFL & Carnegie Mellon University Lausanne, Switzerland Lausanne, Switzerland Lausanne, Switzerland [email protected] [email protected] [email protected] ABSTRACT There exist replication “solutions” for every major DBMS, from Oracle RAC™, Streams™ and DataGuard™ to Slony-I for The need for high availability and performance in data Postgres, MySQL replication and cluster, and everything in- management systems has been fueling a long running interest in between. The naïve observer may conclude that such variety of database replication from both academia and industry. However, replication systems indicates a solved problem; the reality, academic groups often attack replication problems in isolation, however, is the exact opposite. Replication still falls short of overlooking the need for completeness in their solutions, while customer expectations, which explains the continued interest in developing new approaches, resulting in a dazzling variety of commercial teams take a holistic approach that often misses offerings. opportunities for fundamental innovation. This has created over time a gap between academic research and industrial practice. Even the “simple” cases are challenging at large scale. We deployed a replication system for a large travel ticket brokering This paper aims to characterize the gap along three axes: system at a Fortune-500 company faced with a workload where performance, availability, and administration. We build on our 95% of transactions were read-only. Still, the 5% write workload own experience developing and deploying replication systems in resulted in thousands of update requests per second, which commercial and academic settings, as well as on a large body of implied that a system using 2-phase-commit, or any other form of prior related work. -

Database Technology for Bioinformatics from Information Retrieval to Knowledge Systems
Database Technology for Bioinformatics From Information Retrieval to Knowledge Systems Luis M. Rocha Complex Systems Modeling CCS3 - Modeling, Algorithms, and Informatics Los Alamos National Laboratory, MS B256 Los Alamos, NM 87545 [email protected] or [email protected] 1 Molecular Biology Databases 3 Bibliographic databases On-line journals and bibliographic citations – MEDLINE (1971, www.nlm.nih.gov) 3 Factual databases Repositories of Experimental data associated with published articles and that can be used for computerized analysis – Nucleic acid sequences: GenBank (1982, www.ncbi.nlm.nih.gov), EMBL (1982, www.ebi.ac.uk), DDBJ (1984, www.ddbj.nig.ac.jp) – Amino acid sequences: PIR (1968, www-nbrf.georgetown.edu), PRF (1979, www.prf.op.jp), SWISS-PROT (1986, www.expasy.ch) – 3D molecular structure: PDB (1971, www.rcsb.org), CSD (1965, www.ccdc.cam.ac.uk) Lack standardization of data contents 3 Knowledge Bases Intended for automatic inference rather than simple retrieval – Motif libraries: PROSITE (1988, www.expasy.ch/sprot/prosite.html) – Molecular Classifications: SCOP (1994, www.mrc-lmb.cam.ac.uk) – Biochemical Pathways: KEGG (1995, www.genome.ad.jp/kegg) Difference between knowledge and data (semiosis and syntax)?? 2 Growth of sequence and 3D Structure databases Number of Entries 3 Database Technology and Bioinformatics 3 Databases Computerized collection of data for Information Retrieval Shared by many users Stored records are organized with a predefined set of data items (attributes) Managed by a computer program: the database -
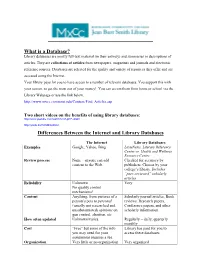
What Is a Database? Differences Between the Internet and Library
What is a Database? Library databases are mostly full-text material (in their entirety) and summaries or descriptions of articles. They are collections of articles from newspapers, magazines and journals and electronic reference sources. Databases are selected for the quality and variety of resources they offer and are accessed using the Internet. Your library pays for you to have access to a number of relevant databases. You support this with your tuition, so get the most out of your money! You can access them from home or school via the Library Webpage or use the link below. http://www.mxcc.commnet.edu/Content/Find_Articles.asp Two short videos on the benefits of using library databases: http://www.youtube.com/watch?v=VUp1P-ubOIc http://youtu.be/Q2GMtIuaNzU Differences Between the Internet and Library Databases The Internet Library Databases Examples Google, Yahoo, Bing LexisNexis, Literary Reference Center or Health and Wellness Resource Center Review process None – anyone can add Checked for accuracy by content to the Web. publishers. Chosen by your college’s library. Includes “peer-reviewed” scholarly articles. Reliability Unknown Very No quality control mechanisms! Content Anything, from pictures of a Scholarly journal articles, Book person’s pets to personal reviews, Research papers, (usually not researched and Conference papers, and other unsubstantiated) opinions on scholarly information gun control, abortion, etc. How often updated Unknown/varies. Regularly – daily, quarterly monthly Cost “Free” but some of the info Library has paid for you to you may need for your access these databases. assignment requires a fee. Organization Very little or no organization Very organized Availability Websites come and go. -

User's Manual for the ALCR-ILLINIS-7090 ALGL-60
•::../. ; '-> v.- V. -V.' skss Hi *lSn i'-fh B£H*wffi H HI BBfiffli? •LN. fln WW* WSMmm Ml H II B RAI^Y OF THE UN IVLRSITY Of ILLINOIS SlO.84 XSibus 1964 The person charging this material is re- sponsible for its return on or before the Latest Date stamped below. Theft, mutilation, and underlining of books are reasons for disciplinary action and may result in dismissal from the University. University of Illinois Library i 1970 LI61— O-10Q6 Digitized by the Internet Archive in 2013 http://archive.org/details/usersmanualforalOOuniv »" DIGITAL COMPUTER LABORATORY GRADUATE COLLEGE UNIVERSITY OF ILLINOIS User's Manual for the ALCpR-ILLIN0IS-7O9O ALG0L-6O Translator University of Illinois 2nd Edition Manual Written and Revised by R. Bayer E. Murphree, Jr. D. Gries September 28, I96U . : Preface In June, 19^2, by arrangement between the University of Illinois and the ALCOR group in Europe, Dr. Manfred Paul, Johannes Gutenberg Universitat, Mainz, and Dr. Rudiger Wiehle, Munchen Technische Hochschule, Munich, began the design of the ALC0R-ILLIN0IS-7O9O ALGOL-60 Translator, the use of which is described in this Manual. They were joined in July, I962, by David Gries and the writer and later by Michael Rossin, Theresa Wang and Rudolf Bayer, all graduate students at the University of Illinois This manual is an effort to explain the differences which exist between publication ALGOL-60 as it is defined by the Revised Report on the Algorithmic Language ALGOL-60 (as published in the January I963 issue of Communications of the Association for Computing Machinery) and as it actually has been implemented by the group named above, Relatively few features of ALGOL-60 have not been implemented, so this manual consists mostly of an explanation of the "hardware" representation of true ALGOL rather than deviations from it. -

Data Quality Requirements Analysis and Modeling December 1992 TDQM-92-03 Richard Y
Published in the Ninth International Conference of Data Engineering Vienna, Austria, April 1993 Data Quality Requirements Analysis and Modeling December 1992 TDQM-92-03 Richard Y. Wang Henry B. Kon Stuart E. Madnick Total Data Quality Management (TDQM) Research Program Room E53-320 Sloan School of Management Massachusetts Institute of Technology Cambridge, MA 02139 USA 617-253-2656 Fax: 617-253-3321 Acknowledgments: Work reported herein has been supported, in part, by MITís Total Data Quality Management (TDQM) Research Program, MITís International Financial Services Research Center (IFSRC), Fujitsu Personal Systems, Inc. and Bull-HN. The authors wish to thank Gretchen Fisher for helping prepare this manuscript. To Appear in the Ninth International Conference on Data Engineering Vienna, Austria April 1993 Data Quality Requirements Analysis and Modeling Richard Y. Wang Henry B. Kon Stuart E. Madnick Sloan School of Management Massachusetts Institute of Technology Cambridge, Mass 02139 [email protected] ABSTRACT Data engineering is the modeling and structuring of data in its design, development and use. An ultimate goal of data engineering is to put quality data in the hands of users. Specifying and ensuring the quality of data, however, is an area in data engineering that has received little attention. In this paper we: (1) establish a set of premises, terms, and definitions for data quality management, and (2) develop a step-by-step methodology for defining and documenting data quality parameters important to users. These quality parameters are used to determine quality indicators, to be tagged to data items, about the data manufacturing process such as data source, creation time, and collection method. -

A Static Analysis Framework for Security Properties in Mobile and Cryptographic Systems
A Static Analysis Framework for Security Properties in Mobile and Cryptographic Systems Benyamin Y. Y. Aziz, M.Sc. School of Computing, Dublin City University A thesis presented in fulfillment of the requirements for the degree of Doctor of Philosophy Supervisor: Dr Geoff Hamilton September 2003 “Start by doing what’s necessary; then do what’s possible; and suddenly you are doing the impossible” St. Francis of Assisi To Yowell, Olivia and Clotilde Declaration I hereby certify that this material, which I now submit for assessment on the programme of study leading to the award of the degree of Doctor of Philosophy (Ph.D.) is entirely my own work and has not been taken from the work of others save and to the extent that such work has been cited and acknowledged within the text of my work. Signed: I.D. No.: Date: Acknowledgements I would like to thank all those people who were true sources of inspiration, knowledge, guidance and help to myself throughout the period of my doctoral research. In particular, I would like to thank my supervisor, Dr. Geoff Hamilton, without whom this work would not have seen the light. I would also like to thank Dr. David Gray, with whom I had many informative conversations, and my colleagues, Thomas Hack and Fr´ed´ericOehl, for their advice and guidance. Finally, I would like to mention that the work of this thesis was partially funded by project IMPROVE (Enterprise Ireland Strategic Grant ST/2000/94). Benyamin Aziz Abstract We introduce a static analysis framework for detecting instances of security breaches in infinite mobile and cryptographic systems specified using the languages of the π-calculus and its cryptographic extension, the spi calculus. -

Education in Programming David Gries Dr. Rer. Nat., Munich Institute
Education in Programming David Gries Dr. rer. nat., Munich Institute of Technology, 1966 Computer Science, Cornell University, Ithaca, NY 1 1 A Glimerick of Hope David Gries, 1995 Abstract Well I got my degree at that place The world is turning to C, And my ancestors came from that race Though at best it is taught awkwardly, Though Great New York C But we don’t have to mope, Was the Birthplace of me There’s a glimmer of hope, And CS at Cornell is my base. In the methods of formality President Mary of Eire So I don't have a real PhD. Was supposed to come to regale ya. It's the Dr. Rer. Nat. that's for me. But matters of State And it's from MIT Made her cancel that date --On your side of the sea So you’re stuck with this guy from Bavaria Munich Inst. of Technolology 2 2 In 1962–63, in Illinois writing the ALCOR-ILLINOIS 7090 ALGOL Compiler I came to Munich to get a PhD (and finish the compiler) Manfred Paul Rudiger Wiehle Elaine and David Gries 3 3 Instrumental in the development of programming languages and their implementation A early as 1952, Bauer: Keller principle Influential in development of Algol 60 Educate the next generation of computer scientists 1968 and 1969 NATO Conferences on Software Engineering (Garmisch and Rome) 4 4 1968 and 1969 NATO Conferences Software Engineering (Garmisch and Rome) 5 5 1968 and 1969 NATO Conferences Software Engineering (Garmisch and Rome) 6 6 Instrumental in the development of programming languages and their implementation Educate the next generation of computer scientists 1968 and 1969 NATO Conferences on Software Engineering (Garmisch and Rome) The Marktoberdorf Summer Schools now led ably by Manfred Broy 7 7 The teaching of programming simplicity elegance perfection intellectual honesty Edsger W.