DBOS: a Proposal for a Data-Centric Operating System
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Chapter 1: Introduction What Is an Operating System?
Chapter 1: Introduction What is an Operating System? Mainframe Systems Desktop Systems Multiprocessor Systems Distributed Systems Clustered System Real -Time Systems Handheld Systems Computing Environments Operating System Concepts 1.1 Silberschatz, Galvin and Gagne 2002 What is an Operating System? A program that acts as an intermediary between a user of a computer and the computer hardware. Operating system goals: ) Execute user programs and make solving user problems easier. ) Make the computer system convenient to use. Use the computer hardware in an efficient manner. Operating System Concepts 1.2 Silberschatz, Galvin and Gagne 2002 1 Computer System Components 1. Hardware – provides basic computing resources (CPU, memory, I/O devices). 2. Operating system – controls and coordinates the use of the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, video games, business programs). 4. Users (people, machines, other computers). Operating System Concepts 1.3 Silberschatz, Galvin and Gagne 2002 Abstract View of System Components Operating System Concepts 1.4 Silberschatz, Galvin and Gagne 2002 2 Operating System Definitions Resource allocator – manages and allocates resources. Control program – controls the execution of user programs and operations of I/O devices . Kernel – the one program running at all times (all else being application programs). -

Blockchain Database for a Cyber Security Learning System
Session ETD 475 Blockchain Database for a Cyber Security Learning System Sophia Armstrong Department of Computer Science, College of Engineering and Technology East Carolina University Te-Shun Chou Department of Technology Systems, College of Engineering and Technology East Carolina University John Jones College of Engineering and Technology East Carolina University Abstract Our cyber security learning system involves an interactive environment for students to practice executing different attack and defense techniques relating to cyber security concepts. We intend to use a blockchain database to secure data from this learning system. The data being secured are students’ scores accumulated by successful attacks or defends from the other students’ implementations. As more professionals are departing from traditional relational databases, the enthusiasm around distributed ledger databases is growing, specifically blockchain. With many available platforms applying blockchain structures, it is important to understand how this emerging technology is being used, with the goal of utilizing this technology for our learning system. In order to successfully secure the data and ensure it is tamper resistant, an investigation of blockchain technology use cases must be conducted. In addition, this paper defined the primary characteristics of the emerging distributed ledgers or blockchain technology, to ensure we effectively harness this technology to secure our data. Moreover, we explored using a blockchain database for our data. 1. Introduction New buzz words are constantly surfacing in the ever evolving field of computer science, so it is critical to distinguish the difference between temporary fads and new evolutionary technology. Blockchain is one of the newest and most developmental technologies currently drawing interest. -

An Introduction to Cloud Databases a Guide for Administrators
Compliments of An Introduction to Cloud Databases A Guide for Administrators Wendy Neu, Vlad Vlasceanu, Andy Oram & Sam Alapati REPORT Break free from old guard databases AWS provides the broadest selection of purpose-built databases allowing you to save, grow, and innovate faster Enterprise scale at 3-5x the performance 14+ database engines 1/10th the cost of vs popular alternatives - more than any other commercial databases provider Learn more: aws.amazon.com/databases An Introduction to Cloud Databases A Guide for Administrators Wendy Neu, Vlad Vlasceanu, Andy Oram, and Sam Alapati Beijing Boston Farnham Sebastopol Tokyo An Introduction to Cloud Databases by Wendy A. Neu, Vlad Vlasceanu, Andy Oram, and Sam Alapati Copyright © 2019 O’Reilly Media Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://oreilly.com). For more infor‐ mation, contact our corporate/institutional sales department: 800-998-9938 or [email protected]. Development Editor: Jeff Bleiel Interior Designer: David Futato Acquisitions Editor: Jonathan Hassell Cover Designer: Karen Montgomery Production Editor: Katherine Tozer Illustrator: Rebecca Demarest Copyeditor: Octal Publishing, LLC September 2019: First Edition Revision History for the First Edition 2019-08-19: First Release The O’Reilly logo is a registered trademark of O’Reilly Media, Inc. An Introduction to Cloud Databases, the cover image, and related trade dress are trademarks of O’Reilly Media, Inc. The views expressed in this work are those of the authors, and do not represent the publisher’s views. -

Middleware-Based Database Replication: the Gaps Between Theory and Practice
Appears in Proceedings of the ACM SIGMOD Conference, Vancouver, Canada (June 2008) Middleware-based Database Replication: The Gaps Between Theory and Practice Emmanuel Cecchet George Candea Anastasia Ailamaki EPFL EPFL & Aster Data Systems EPFL & Carnegie Mellon University Lausanne, Switzerland Lausanne, Switzerland Lausanne, Switzerland [email protected] [email protected] [email protected] ABSTRACT There exist replication “solutions” for every major DBMS, from Oracle RAC™, Streams™ and DataGuard™ to Slony-I for The need for high availability and performance in data Postgres, MySQL replication and cluster, and everything in- management systems has been fueling a long running interest in between. The naïve observer may conclude that such variety of database replication from both academia and industry. However, replication systems indicates a solved problem; the reality, academic groups often attack replication problems in isolation, however, is the exact opposite. Replication still falls short of overlooking the need for completeness in their solutions, while customer expectations, which explains the continued interest in developing new approaches, resulting in a dazzling variety of commercial teams take a holistic approach that often misses offerings. opportunities for fundamental innovation. This has created over time a gap between academic research and industrial practice. Even the “simple” cases are challenging at large scale. We deployed a replication system for a large travel ticket brokering This paper aims to characterize the gap along three axes: system at a Fortune-500 company faced with a workload where performance, availability, and administration. We build on our 95% of transactions were read-only. Still, the 5% write workload own experience developing and deploying replication systems in resulted in thousands of update requests per second, which commercial and academic settings, as well as on a large body of implied that a system using 2-phase-commit, or any other form of prior related work. -

Personal-Computer Systems • Parallel Systems • Distributed Systems • Real -Time Systems
Module 1: Introduction • What is an operating system? • Simple Batch Systems • Multiprogramming Batched Systems • Time-Sharing Systems • Personal-Computer Systems • Parallel Systems • Distributed Systems • Real -Time Systems Applied Operating System Concepts 1.1 Silberschatz, Galvin, and Gagne Ď 1999 What is an Operating System? • A program that acts as an intermediary between a user of a computer and the computer hardware. • Operating system goals: – Execute user programs and make solving user problems easier. – Make the computer system convenient to use. • Use the computer hardware in an efficient manner. Applied Operating System Concepts 1.2 Silberschatz, Galvin, and Gagne Ď 1999 Computer System Components 1. Hardware – provides basic computing resources (CPU, memory, I/O devices). 2. Operating system – controls and coordinates the use of the hardware among the various application programs for the various users. 3. Applications programs – define the ways in which the system resources are used to solve the computing problems of the users (compilers, database systems, video games, business programs). 4. Users (people, machines, other computers). Applied Operating System Concepts 1.3 Silberschatz, Galvin, and Gagne Ď 1999 Abstract View of System Components Applied Operating System Concepts 1.4 Silberschatz, Galvin, and Gagne Ď 1999 Operating System Definitions • Resource allocator – manages and allocates resources. • Control program – controls the execution of user programs and operations of I/O devices . • Kernel – the one program running at all times (all else being application programs). Applied Operating System Concepts 1.5 Silberschatz, Galvin, and Gagne Ď 1999 Memory Layout for a Simple Batch System Applied Operating System Concepts 1.7 Silberschatz, Galvin, and Gagne Ď 1999 Multiprogrammed Batch Systems Several jobs are kept in main memory at the same time, and the CPU is multiplexed among them. -

Database Technology for Bioinformatics from Information Retrieval to Knowledge Systems
Database Technology for Bioinformatics From Information Retrieval to Knowledge Systems Luis M. Rocha Complex Systems Modeling CCS3 - Modeling, Algorithms, and Informatics Los Alamos National Laboratory, MS B256 Los Alamos, NM 87545 [email protected] or [email protected] 1 Molecular Biology Databases 3 Bibliographic databases On-line journals and bibliographic citations – MEDLINE (1971, www.nlm.nih.gov) 3 Factual databases Repositories of Experimental data associated with published articles and that can be used for computerized analysis – Nucleic acid sequences: GenBank (1982, www.ncbi.nlm.nih.gov), EMBL (1982, www.ebi.ac.uk), DDBJ (1984, www.ddbj.nig.ac.jp) – Amino acid sequences: PIR (1968, www-nbrf.georgetown.edu), PRF (1979, www.prf.op.jp), SWISS-PROT (1986, www.expasy.ch) – 3D molecular structure: PDB (1971, www.rcsb.org), CSD (1965, www.ccdc.cam.ac.uk) Lack standardization of data contents 3 Knowledge Bases Intended for automatic inference rather than simple retrieval – Motif libraries: PROSITE (1988, www.expasy.ch/sprot/prosite.html) – Molecular Classifications: SCOP (1994, www.mrc-lmb.cam.ac.uk) – Biochemical Pathways: KEGG (1995, www.genome.ad.jp/kegg) Difference between knowledge and data (semiosis and syntax)?? 2 Growth of sequence and 3D Structure databases Number of Entries 3 Database Technology and Bioinformatics 3 Databases Computerized collection of data for Information Retrieval Shared by many users Stored records are organized with a predefined set of data items (attributes) Managed by a computer program: the database -
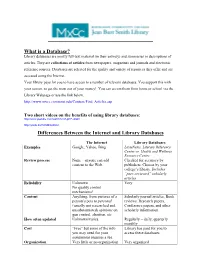
What Is a Database? Differences Between the Internet and Library
What is a Database? Library databases are mostly full-text material (in their entirety) and summaries or descriptions of articles. They are collections of articles from newspapers, magazines and journals and electronic reference sources. Databases are selected for the quality and variety of resources they offer and are accessed using the Internet. Your library pays for you to have access to a number of relevant databases. You support this with your tuition, so get the most out of your money! You can access them from home or school via the Library Webpage or use the link below. http://www.mxcc.commnet.edu/Content/Find_Articles.asp Two short videos on the benefits of using library databases: http://www.youtube.com/watch?v=VUp1P-ubOIc http://youtu.be/Q2GMtIuaNzU Differences Between the Internet and Library Databases The Internet Library Databases Examples Google, Yahoo, Bing LexisNexis, Literary Reference Center or Health and Wellness Resource Center Review process None – anyone can add Checked for accuracy by content to the Web. publishers. Chosen by your college’s library. Includes “peer-reviewed” scholarly articles. Reliability Unknown Very No quality control mechanisms! Content Anything, from pictures of a Scholarly journal articles, Book person’s pets to personal reviews, Research papers, (usually not researched and Conference papers, and other unsubstantiated) opinions on scholarly information gun control, abortion, etc. How often updated Unknown/varies. Regularly – daily, quarterly monthly Cost “Free” but some of the info Library has paid for you to you may need for your access these databases. assignment requires a fee. Organization Very little or no organization Very organized Availability Websites come and go. -

Operating System
OPERATING SYSTEM INDEX LESSON 1: INTRODUCTION TO OPERATING SYSTEM LESSON 2: FILE SYSTEM – I LESSON 3: FILE SYSTEM – II LESSON 4: CPU SCHEDULING LESSON 5: MEMORY MANAGEMENT – I LESSON 6: MEMORY MANAGEMENT – II LESSON 7: DISK SCHEDULING LESSON 8: PROCESS MANAGEMENT LESSON 9: DEADLOCKS LESSON 10: CASE STUDY OF UNIX LESSON 11: CASE STUDY OF MS-DOS LESSON 12: CASE STUDY OF MS-WINDOWS NT Lesson No. 1 Intro. to Operating System 1 Lesson Number: 1 Writer: Dr. Rakesh Kumar Introduction to Operating System Vetter: Prof. Dharminder Kr. 1.0 OBJECTIVE The objective of this lesson is to make the students familiar with the basics of operating system. After studying this lesson they will be familiar with: 1. What is an operating system? 2. Important functions performed by an operating system. 3. Different types of operating systems. 1. 1 INTRODUCTION Operating system (OS) is a program or set of programs, which acts as an interface between a user of the computer & the computer hardware. The main purpose of an OS is to provide an environment in which we can execute programs. The main goals of the OS are (i) To make the computer system convenient to use, (ii) To make the use of computer hardware in efficient way. Operating System is system software, which may be viewed as collection of software consisting of procedures for operating the computer & providing an environment for execution of programs. It’s an interface between user & computer. So an OS makes everything in the computer to work together smoothly & efficiently. Figure 1: The relationship between application & system software Lesson No. -

Data Quality Requirements Analysis and Modeling December 1992 TDQM-92-03 Richard Y
Published in the Ninth International Conference of Data Engineering Vienna, Austria, April 1993 Data Quality Requirements Analysis and Modeling December 1992 TDQM-92-03 Richard Y. Wang Henry B. Kon Stuart E. Madnick Total Data Quality Management (TDQM) Research Program Room E53-320 Sloan School of Management Massachusetts Institute of Technology Cambridge, MA 02139 USA 617-253-2656 Fax: 617-253-3321 Acknowledgments: Work reported herein has been supported, in part, by MITís Total Data Quality Management (TDQM) Research Program, MITís International Financial Services Research Center (IFSRC), Fujitsu Personal Systems, Inc. and Bull-HN. The authors wish to thank Gretchen Fisher for helping prepare this manuscript. To Appear in the Ninth International Conference on Data Engineering Vienna, Austria April 1993 Data Quality Requirements Analysis and Modeling Richard Y. Wang Henry B. Kon Stuart E. Madnick Sloan School of Management Massachusetts Institute of Technology Cambridge, Mass 02139 [email protected] ABSTRACT Data engineering is the modeling and structuring of data in its design, development and use. An ultimate goal of data engineering is to put quality data in the hands of users. Specifying and ensuring the quality of data, however, is an area in data engineering that has received little attention. In this paper we: (1) establish a set of premises, terms, and definitions for data quality management, and (2) develop a step-by-step methodology for defining and documenting data quality parameters important to users. These quality parameters are used to determine quality indicators, to be tagged to data items, about the data manufacturing process such as data source, creation time, and collection method. -

COSC 6385 Computer Architecture - Multi-Processors (IV) Simultaneous Multi-Threading and Multi-Core Processors Edgar Gabriel Spring 2011
COSC 6385 Computer Architecture - Multi-Processors (IV) Simultaneous multi-threading and multi-core processors Edgar Gabriel Spring 2011 Edgar Gabriel Moore’s Law • Long-term trend on the number of transistor per integrated circuit • Number of transistors double every ~18 month Source: http://en.wikipedia.org/wki/Images:Moores_law.svg COSC 6385 – Computer Architecture Edgar Gabriel 1 What do we do with that many transistors? • Optimizing the execution of a single instruction stream through – Pipelining • Overlap the execution of multiple instructions • Example: all RISC architectures; Intel x86 underneath the hood – Out-of-order execution: • Allow instructions to overtake each other in accordance with code dependencies (RAW, WAW, WAR) • Example: all commercial processors (Intel, AMD, IBM, SUN) – Branch prediction and speculative execution: • Reduce the number of stall cycles due to unresolved branches • Example: (nearly) all commercial processors COSC 6385 – Computer Architecture Edgar Gabriel What do we do with that many transistors? (II) – Multi-issue processors: • Allow multiple instructions to start execution per clock cycle • Superscalar (Intel x86, AMD, …) vs. VLIW architectures – VLIW/EPIC architectures: • Allow compilers to indicate independent instructions per issue packet • Example: Intel Itanium series – Vector units: • Allow for the efficient expression and execution of vector operations • Example: SSE, SSE2, SSE3, SSE4 instructions COSC 6385 – Computer Architecture Edgar Gabriel 2 Limitations of optimizing a single instruction -

Chapter 20: the Linux System
Chapter 20: The Linux System Operating System Concepts – 10th dition Silberschatz, Galvin and Gagne ©2018 Chapter 20: The Linux System Linux History Design Principles Kernel Modules Process Management Scheduling Memory Management File Systems Input and Output Interprocess Communication Network Structure Security Operating System Concepts – 10th dition 20!2 Silberschatz, Galvin and Gagne ©2018 Objectives To explore the history o# the UNIX operating system from hich Linux is derived and the principles upon which Linux’s design is based To examine the Linux process model and illustrate how Linux schedules processes and provides interprocess communication To look at memory management in Linux To explore how Linux implements file systems and manages I/O devices Operating System Concepts – 10th dition 20!" Silberschatz, Galvin and Gagne ©2018 History Linux is a modern, free operating system (ased on $NIX standards First developed as a small (ut sel#-contained kernel in -.91 by Linus Torvalds, with the major design goal o# UNIX compatibility, released as open source Its history has (een one o# collaboration by many users from all around the orld, corresponding almost exclusively over the Internet It has been designed to run efficiently and reliably on common PC hardware, but also runs on a variety of other platforms The core Linux operating system kernel is entirely original, but it can run much existing free UNIX soft are, resulting in an entire UNIX-compatible operating system free from proprietary code Linux system has -

The UNIX Time- Sharing System
1. Introduction There have been three versions of UNIX. The earliest version (circa 1969–70) ran on the Digital Equipment Cor- poration PDP-7 and -9 computers. The second version ran on the unprotected PDP-11/20 computer. This paper describes only the PDP-11/40 and /45 [l] system since it is The UNIX Time- more modern and many of the differences between it and older UNIX systems result from redesign of features found Sharing System to be deficient or lacking. Since PDP-11 UNIX became operational in February Dennis M. Ritchie and Ken Thompson 1971, about 40 installations have been put into service; they Bell Laboratories are generally smaller than the system described here. Most of them are engaged in applications such as the preparation and formatting of patent applications and other textual material, the collection and processing of trouble data from various switching machines within the Bell System, and recording and checking telephone service orders. Our own installation is used mainly for research in operating sys- tems, languages, computer networks, and other topics in computer science, and also for document preparation. UNIX is a general-purpose, multi-user, interactive Perhaps the most important achievement of UNIX is to operating system for the Digital Equipment Corpora- demonstrate that a powerful operating system for interac- tion PDP-11/40 and 11/45 computers. It offers a number tive use need not be expensive either in equipment or in of features seldom found even in larger operating sys- human effort: UNIX can run on hardware costing as little as tems, including: (1) a hierarchical file system incorpo- $40,000, and less than two man years were spent on the rating demountable volumes; (2) compatible file, device, main system software.