Low-Level C Programming CSEE W4840
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MIPS® Architecture for Programmers Volume I-B: Introduction to the Micromips32™ Architecture, Revision 5.03
MIPS® Architecture For Programmers Volume I-B: Introduction to the microMIPS32™ Architecture Document Number: MD00741 Revision 5.03 Sept. 9, 2013 Unpublished rights (if any) reserved under the copyright laws of the United States of America and other countries. This document contains information that is proprietary to MIPS Tech, LLC, a Wave Computing company (“MIPS”) and MIPS’ affiliates as applicable. Any copying, reproducing, modifying or use of this information (in whole or in part) that is not expressly permitted in writing by MIPS or MIPS’ affiliates as applicable or an authorized third party is strictly prohibited. At a minimum, this information is protected under unfair competition and copyright laws. Violations thereof may result in criminal penalties and fines. Any document provided in source format (i.e., in a modifiable form such as in FrameMaker or Microsoft Word format) is subject to use and distribution restrictions that are independent of and supplemental to any and all confidentiality restrictions. UNDER NO CIRCUMSTANCES MAY A DOCUMENT PROVIDED IN SOURCE FORMAT BE DISTRIBUTED TO A THIRD PARTY IN SOURCE FORMAT WITHOUT THE EXPRESS WRITTEN PERMISSION OF MIPS (AND MIPS’ AFFILIATES AS APPLICABLE) reserve the right to change the information contained in this document to improve function, design or otherwise. MIPS and MIPS’ affiliates do not assume any liability arising out of the application or use of this information, or of any error or omission in such information. Any warranties, whether express, statutory, implied or otherwise, including but not limited to the implied warranties of merchantability or fitness for a particular purpose, are excluded. Except as expressly provided in any written license agreement from MIPS or an authorized third party, the furnishing of this document does not give recipient any license to any intellectual property rights, including any patent rights, that cover the information in this document. -

MIPS32™ Architecture for Programmers Volume I: Introduction to the MIPS32™ Architecture
MIPS32™ Architecture For Programmers Volume I: Introduction to the MIPS32™ Architecture Document Number: MD00082 Revision 0.95 March 12, 2001 MIPS Technologies, Inc. 1225 Charleston Road Mountain View, CA 94043-1353 Copyright © 2001 MIPS Technologies, Inc. All rights reserved. Unpublished rights reserved under the Copyright Laws of the United States of America. This document contains information that is proprietary to MIPS Technologies, Inc. (“MIPS Technologies”). Any copying, modifyingor use of this information (in whole or in part) which is not expressly permitted in writing by MIPS Technologies or a contractually-authorized third party is strictly prohibited. At a minimum, this information is protected under unfair competition laws and the expression of the information contained herein is protected under federal copyright laws. Violations thereof may result in criminal penalties and fines. MIPS Technologies or any contractually-authorized third party reserves the right to change the information contained in this document to improve function, design or otherwise. MIPS Technologies does not assume any liability arising out of the application or use of this information. Any license under patent rights or any other intellectual property rights owned by MIPS Technologies or third parties shall be conveyed by MIPS Technologies or any contractually-authorized third party in a separate license agreement between the parties. The information contained in this document constitutes one or more of the following: commercial computer software, commercial -

MCST~8 Assembly Language Programming Manual PRELIMINARY EDITION
INTEL CORP. 3065 Bowers Avenue, Santa Clara, California 95051 • (408) 246-7501 MCST~8 Assembly Language Programming Manual PRELIMINARY EDITION November 1973 © Intel Corporation 1973 -- TABLE OF CONTENTS -- 8008 PROGRAMMING MANUAL Page No. 1.0 INTRODUCTION 1-1 2.0 COMPUTER ORGANIZATION 2-1 2.1 THE CENTRAL PROCESSING UNIT 2-3 2.1.1 WORKING REGISTERS 2-3 2. 1 .2 THE STACK 2-5 2.1.3 ARITHMETIC AND LOGIC UNIT 2-7 2.2 MEMORY 2-8 2.3 COMPUTER PROGRAM REPRESENTATION IN MEMORY 2-8 2.4 MEMORY ADDRESSING 2-10 2.4.1 DIRECT ADDRESSING 2-11 2 .4 .2 INDEXED ADDRESSING 2-13 2.4.3 INDIRECT ADDRESSING 2-13 2.4.4 IMMEDIATE ADDRESSING 2-14 2.4.5 SUBROUTINES AND USE OF THE STACK FOR ADDRESSING 2-15 2.5 CONDITION BITS 2-18 2.5.1 CARRY BIT 2-18 2 .5 • 2 SIGN BIT 2-19 2 .5 . 3 ZERO BIT 2-19 2 • 5 . 4 PARITY BIT 2-20 3.{) THE 8008 INSTRUCTION SET 3-1 3.1 ASSEMBLY LANG UAGE 3-1 3.1.1 HOW ASSEMBLY LANGUAGE IS USED 3-1 3.1.2 STATEMENT MNEMONICS 3-4 3 • 1. 3 LABEL FIELD 3-5 3.1.4 CODE FIELD 3-7 3 • 1 .5 OPERAND FIELD 3-7 3.1.6 COMMENT FIELD 3-15 i Page No. 3.2 DATA STATEMENTS 3-15 3.2.1 TWO'S COMPLEMENT 3-16 3.2.2 DB DEFINE BYTE(S) OF DATA 3-20 3.2.3 DW DEFINE WORD (TWO BYTES) OF DATA 3-21 3.2.4 DS DEFINE STORAGE (BYTES) 3-22 3.3 SINGLE REGISTER INSTRUCTIONS 3-23 3.3.1 INR INCREMENT REGISTER 3-24 3.3.2 DCR DECREMENT REGISTER 3-24 3.4 MOV INSTRUCTION 3-25 3.5 REGISTER OR MEMORY TO ACCUMULATOR INSTRUCTIONS 3-28 3.5.1 ADD ADD REGISTER OR MEMORY TO ACCUMULATOR 3-29 3.5.2 ADC ADD REGISTI:R OR MEMORY TO ACCUMULATOR WITH CARRY 3-31 3.5.3 SUB SUBTRACT REGISTER OR MEMORY -

Notes on Usage of the RX Family C/C++ Compiler V.1.00 Release 01 and Corrections in the User's Manual
R0C5RX00XSW01R-ERN100630 Notes on Usage of the RX Family C/C++ Compiler V.1.00 Release 01 and Corrections in the User's Manual There are notes on usage of the RX Family C/C++ compiler V.1.00 Release 01 and corrections to be made in the bundled user's manual (REJ10J2062-0100) as listed below. 1. Notes on Usage 1.1 Note on a Case of the C1804 Message [C/C++ Compiler] When the int_to_short option is specified and a file including a C standard header is compiled as C++ or EC++, the compiler may show the C1804(W) message. In this case, simply ignore the message because there are no problems. [NOTE] In compilation of C++ or EC++, the int_to_short option will be invalid. Data that are shared between C and C++ (EC++) program must be declared as the long or short type rather than as the int type. 1.2 Note on using MVTC or POPC instructions [Assembler] In the assembly language, the program counter (PC) cannot be specified for MVTC or POPC instructions. 1.3 Note on the delete Option for Linkage [Optimizing linkage editor] When a function symbol is removed by the delete option, its following function in the source program is not allowed to have a breakpoint at its function name on the editor in your debugging. If you would like to set a breakpoint at the function entrance, set the breakpoint via the Label window or at the prologue code of the function. 1.4 Notes of Paths Name and File Name [Optimizing linkage editor] In the specification of the optimizing linkage editor, the parentheses "(" and ")" signs for the path names and file names cannot be used because these signs are used for the option descriptions. -
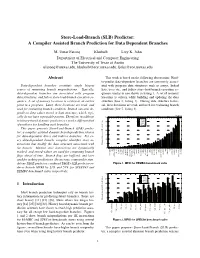
(SLB) Predictor: a Compiler Assisted Branch Prediction for Data Dependent Branches
Store-Load-Branch (SLB) Predictor: A Compiler Assisted Branch Prediction for Data Dependent Branches M. Umar Farooq Khubaib Lizy K. John Department of Electrical and Computer Engineering The University of Texas at Austin [email protected], [email protected], [email protected] Abstract This work is based on the following observation: Hard- to-predict data-dependent branches are commonly associ- Data-dependent branches constitute single biggest ated with program data structures such as arrays, linked source of remaining branch mispredictions. Typically, lists, trees etc., and follow store-load-branch execution se- data-dependent branches are associated with program quence similar to one shown in listing 1. A set of memory data structures, and follow store-load-branch execution se- locations is written while building and updating the data quence. A set of memory locations is written at an earlier structure (line 2, listing 1). During data structure traver- point in a program. Later, these locations are read, and sal, these locations are read, and used for evaluating branch used for evaluating branch condition. Branch outcome de- condition (line 7, listing 1). pends on data values stored in data structure, which, typi- 52 50 53 cally do not have repeatable pattern. Therefore, in addition 35 Gshare to history-based dynamic predictor, we need a different kind 30 YAGS BiMode of predictor for handling such branches. TAGE 25 This paper presents Store-Load-Branch (SLB) predic- 20 tor; a compiler-assisted dynamic branch prediction scheme for data-dependent direct and indirect branches. For ev- 15 ery data-dependent branch, compiler identifies store in- 10 5 structions that modify the data structure associated with Mispredictions per 1K instructions the branch. -
![Downloads/Kornau-Tim--Diplomarbeit--Rop.Pdf [34] Sebastian Krahmer](https://docslib.b-cdn.net/cover/8658/downloads-kornau-tim-diplomarbeit-rop-pdf-34-sebastian-krahmer-1798658.webp)
Downloads/Kornau-Tim--Diplomarbeit--Rop.Pdf [34] Sebastian Krahmer
CFI CaRE: Hardware-supported Call and Return Enforcement for Commercial Microcontrollers Thomas Nyman Jan-Erik Ekberg Lucas Davi N. Asokan Aalto University, Finland Trustonic, Finland University of Aalto University, Finland [email protected] [email protected] Duisburg-Essen, [email protected] Trustonic, Finland Germany thomas.nyman@ lucas.davi@wiwinf. trustonic.com uni-due.de ABSTRACT CFI (Section 3.1) is a well-explored technique for resisting With the increasing scale of deployment of Internet of Things (IoT), the code-reuse attacks such as Return-Oriented Programming concerns about IoT security have become more urgent. In particular, (ROP) [47] that allow attackers in control of data memory to subvert memory corruption attacks play a predominant role as they allow the control flow of a program. CFI commonly takes the formof remote compromise of IoT devices. Control-flow integrity (CFI) is inlined enforcement, where CFI checks are inserted at points in the a promising and generic defense technique against these attacks. program code where control flow changes occur. For legacy applica- However, given the nature of IoT deployments, existing protection tions CFI checks must be introduced by instrumenting the pre-built mechanisms for traditional computing environments (including CFI) binary. Such binary instrumentation necessarily modifies the mem- need to be adapted to the IoT setting. In this paper, we describe ory layout of the code, requiring memory addresses referenced by the challenges of enabling CFI on microcontroller (MCU) based the program to be adjusted accordingly [28]. This is typically done IoT devices. We then present CaRE, the first interrupt-aware CFI through load-time dynamic binary rewriting software [14, 39]. -

PL/I for AIX: Programming Guide
IBM PL/I for AIX Programming Guide Ve r s i o n 2.0.0 SC18-9328-00 IBM PL/I for AIX Programming Guide Ve r s i o n 2.0.0 SC18-9328-00 Note! Before using this information and the product it supports, be sure to read the general information under “Notices” on page 309. Second Edition (June 2004) This edition applies to IBM PL/I for AIX 2.0.0, 5724-H45, and to any subsequent releases until otherwise indicated in new editions or technical newsletters. Make sure you are using the correct edition for the level of the product. Order publications through your IBM representative or the IBM branch office serving your locality. Publications are not stocked at the address below. A form for readers’ comments is provided at the back of this publication. If the form has been removed, address your comments to: IBM Corporation, Department HHX/H1 555 Bailey Ave San Jose, CA, 95141-1099 United States of America When you send information to IBM, you grant IBM a nonexclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. ©International Business Machines Corporation 1998,2004. All rights reserved. Contents Figures . vii COMPILE . .47 COPYRIGHT . .48 CURRENCY . .48 Part 1. Introducing PL/I on your DEFAULT . .48 workstation . .1 EXIT. .54 EXTRN . .54 Chapter 1. About this book . .3 FLAG . .55 FLOATINMATH. .55 Chapter 2. How to read the syntax GONUMBER . .56 GRAPHIC . .56 diagrams . .5 IMPRECISE . .56 INCAFTER . .57 Chapter 3. -

Jump Tables Via Function Pointer Arrays in C/C++ Jump Tables, Also Called Branch Tables, Are an Efficient Means of Handling Similar Events in Software
Jump Tables via Function Pointer Arrays in C/C++ Jump tables, also called branch tables, are an efficient means of handling similar events in software. Here’s a look at the use of arrays of function pointers in C/C++ as jump tables. Examination of assembly language code that has been crafted by an expert will usually reveal extensive use of function “branch tables.” Branch tables (a.k.a., jump tables) are used because they offer a unique blend of compactness and execution speed, particularly on microprocessors that support indexed addressing. When one examines typical C/C++ code, however, the branch table (i.e., an array of funtion pointers) is a much rarer beast. The purpose of this article is to examine why branch tables are not used by C/C++ programmers and to make the case for their extensive use. Real world examples of their use are included. Function pointers In talking to C/C++ programmers about this topic, three reasons are usually cited for not using function pointers. They are: • They are dangerous • A good optimizing compiler will generate a jump table from a switch statement, so let the compiler do the work • They are too difficult to code and maintain Are function pointers dangerous? This school of thought comes about, because code that indexes into a table and then calls a function based on the index has the capability to end up just about anywhere. For instance, consider the following code fragment: void (*pf[])(void) = {fna, fnb, fnc, …, fnz}; void test(const INT jump_index) { /* Call the function specified by jump_index */ pf[jump_index](); } FREDERICK, MD 21702 USA • +1 301-551-5138 • WWW.RMBCONSULTING.US The above code declares pf[] to be an array of pointers to functions, each of which takes no arguments and returns void. -

LC-2 Programmer's Reference and User Guide
LC-2 Programmer’s Reference and User Guide University of Michigan EECS 100 Matt Postiff Copyright (C) Matt Postiff 1995-1999. All rights reserved. Written permission of the author is required for duplication of this document. Table of Contents Table of Contents . i List of Tables . iii List of Figures . v Chapter 1 Introduction to the LC-2 . 1 1.1 Notational Conventions . 3 Chapter 2 LC-2 Programmer’s Reference . 7 2.1 LC-2 Programming Model. 9 2.2 Instruction Set . 10 2.3 Summary of Instruction Formats and Semantics. 28 2.4 Addressing Modes . 31 2.5 Branching Modes. 32 2.6 The LC-2 System Calls . 33 2.7 The LC-2 Hardware Registers . 34 2.8 The LC-2 Memory Map. 35 Chapter 3 LC-2 Machine- and Assembly-Programming . 37 3.1 Introduction to Program Execution in the LC-2 . 39 3.2 The LC-2 Instruction Encoding . 40 3.3 Condition Codes in the LC-2 Processor. 41 3.3.1 Condition Field in the Instruction Encoding. 41 3.4 Keyboard Input and Console Output . 42 3.5 Programming the LC-2 in Machine Language . 43 3.5.1 Machine-Language File Formats . 43 3.6 Programming the LC-2 in Assembly Language . 46 3.6.1 Introduction. 46 3.6.2 LC-2 Assembly Language . 46 3.6.3 The Assembly Process . 49 3.6.4 Some Examples. 49 Chapter 4 LC-2 Programming Tools Guide. 51 4.1 The convert Program . 53 4.2 The assemble Program. 54 4.2.1 The Listing File. -

Control Flow
Control Flow Stephen A. Edwards Columbia University Fall 2012 Control Flow “Time is Nature’s way of preventing everything from happening at once.” Scott identifies seven manifestations of this: 1. Sequencing foo(); bar(); 2. Selection if (a) foo(); 3. Iteration while (i<10) foo(i); 4. Procedures foo(10,20); 5. Recursion foo(int i) { foo(i-1); } 6. Concurrency foo() bar() jj 7. Nondeterminism do a -> foo(); [] b -> bar(); Ordering Within Expressions What code does a compiler generate for a = b + c + d; Most likely something like tmp = b + c; a = tmp + d; (Assumes left-to-right evaluation of expressions.) Order of Evaluation Why would you care? Expression evaluation can have side-effects. Floating-point numbers don’t behave like numbers. GCC returned 25. Sun’s C compiler returned 20. C says expression evaluation order is implementation-dependent. Side-effects int x = 0; int foo() { x += 5; return x; } int bar() { int a = foo() + x + foo(); return a; } What does bar() return? Side-effects int x = 0; int foo() { x += 5; return x; } int bar() { int a = foo() + x + foo(); return a; } What does bar() return? GCC returned 25. Sun’s C compiler returned 20. C says expression evaluation order is implementation-dependent. Side-effects Java prescribes left-to-right evaluation. class Foo { static int x; static int foo() { x += 5; return x; } public static void main(String args[]) { int a = foo() + x + foo(); System.out.println(a); } } Always prints 20. Number Behavior Basic number axioms: a x a if and only if x 0 Additive identity Å Æ Æ (a b) c a (b c) Associative Å Å Æ Å Å a(b c) ab ac Distributive Å Æ Å Misbehaving Floating-Point Numbers 1e20 + 1e-20 = 1e20 1e-20 1e20 ¿ (1 + 9e-7) + 9e-7 1 + (9e-7 + 9e-7) 6Æ 9e-7 1, so it is discarded, however, 1.8e-6 is large enough ¿ 1.00001(1.000001 1) 1.00001 1.000001 1.00001 1 ¡ 6Æ ¢ ¡ ¢ 1.00001 1.000001 1.00001100001 requires too much intermediate ¢ Æ precision. -

Lecture Notes Companion CPSC 213 2Nd Edition DRAFT Oct28
Lecture Notes Companion CPSC 213 2nd Edition DRAFT Oct28 Mike Feeley University of British Columbia February 13, 2012 2 Contents 1 Introduction to the Computer Systems 7 1.1 JavaandC................................................. 8 1.2 The Compiler . 8 2 Execution of a Program 9 2.1 The Plan . 9 2.2 Introduction to a Simple CPU . 10 2.2.1 The CPU . 10 2.2.2 The Memory . 12 2.2.3 The Anatomy of a Cycle . 14 2.3 Instruction Set Architectures . 16 2.3.1 Simple Machine ISA Constraints . 16 2.3.2 Instruction Set Styles (RISC vs CISC) . 16 2.3.3 Types of Opcodes . 17 2.3.4 Addressing Modes . 18 2.3.5 Assembly Language . 18 2.3.6 The SM213 ISA . 20 2.4 Variables . 20 2.4.1 Classifying Variables . 20 2.4.2 SM213 Instructions for Accessing Variables . 21 2.4.3 Static Variables . 21 2.4.4 Dynamic Arrays . 24 2.4.5 Instance Variables . 26 2.4.6 Java References and C Pointers . 32 3 2.5 Dynamic Allocation and Deallocation . 32 2.5.1 Pointers and References . 32 2.5.2 Allocating and Deallocating Dynamic Objects . 32 2.5.3 Type Safety and Explicit Deallocation . 32 2.5.4 The Dangling Pointer Problem and Other Bugs With Using Pointers in C . 33 2.5.5 Memory Leaks . 33 2.5.6 Java Reference Objects . 34 2.5.7 Garbage Collection . 34 2.6 ALU Instructions . 34 2.6.1 SM213 Instructions for Doing Math . 34 2.7 Control Flow . 35 2.7.1 SM213 Instructions for Static Control Flow . -

Instruction Set Assembly Guide for Armv7 and Earlier Arm® Architectures Version 2.0
Instruction Set Assembly Guide for Armv7 and earlier Arm® architectures Version 2.0 Reference Guide Copyright © 2018, 2019 Arm Limited or its affiliates. All rights reserved. 100076_0200_00_en Instruction Set Assembly Guide for Armv7 and earlier Arm® architectures Instruction Set Assembly Guide for Armv7 and earlier Arm® architectures Reference Guide Copyright © 2018, 2019 Arm Limited or its affiliates. All rights reserved. Release Information Document History Issue Date Confidentiality Change 0100-00 25 October 2018 Non-Confidential First Release 0200-00 09 October 2019 Non-Confidential Second Release. The title and scope of the document has changed. Non-Confidential Proprietary Notice This document is protected by copyright and other related rights and the practice or implementation of the information contained in this document may be protected by one or more patents or pending patent applications. No part of this document may be reproduced in any form by any means without the express prior written permission of Arm. No license, express or implied, by estoppel or otherwise to any intellectual property rights is granted by this document unless specifically stated. Your access to the information in this document is conditional upon your acceptance that you will not use or permit others to use the information for the purposes of determining whether implementations infringe any third party patents. THIS DOCUMENT IS PROVIDED “AS IS”. ARM PROVIDES NO REPRESENTATIONS AND NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTABILITY, SATISFACTORY QUALITY, NON-INFRINGEMENT OR FITNESS FOR A PARTICULAR PURPOSE WITH RESPECT TO THE DOCUMENT. For the avoidance of doubt, Arm makes no representation with respect to, and has undertaken no analysis to identify or understand the scope and content of, third party patents, copyrights, trade secrets, or other rights.