Trend Micro Safe Lock Intelligent Manager Installation Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Microsoft Patches Were Evaluated up to and Including CVE-2020-1587
Honeywell Commercial Security 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2020-1587. Patches not listed below are not applicable to a Pro-Watch system. 2020 – Microsoft® Patches Tested with Pro-Watch CVE-2020-1587 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability CVE-2020-1584 Windows dnsrslvr.dll Elevation of Privilege Vulnerability CVE-2020-1579 Windows Function Discovery SSDP Provider Elevation of Privilege Vulnerability CVE-2020-1578 Windows Kernel Information Disclosure Vulnerability CVE-2020-1577 DirectWrite Information Disclosure Vulnerability CVE-2020-1570 Scripting Engine Memory Corruption Vulnerability CVE-2020-1569 Microsoft Edge Memory Corruption Vulnerability CVE-2020-1568 Microsoft Edge PDF Remote Code Execution Vulnerability CVE-2020-1567 MSHTML Engine Remote Code Execution Vulnerability CVE-2020-1566 Windows Kernel Elevation of Privilege Vulnerability CVE-2020-1565 Windows Elevation of Privilege Vulnerability CVE-2020-1564 Jet Database Engine Remote Code Execution Vulnerability CVE-2020-1562 Microsoft Graphics Components Remote Code Execution Vulnerability -

Microsoft Windows Common Criteria Evaluation Security Target
Microsoft Common Criteria Security Target Microsoft Windows Common Criteria Evaluation Microsoft Windows 10 version 1809 (October 2018 Update) Microsoft Windows Server 2019 (October 2018 Update) Security Target Document Information Version Number 0.05 Updated On June 18, 2019 Microsoft © 2019 Page 1 of 126 Microsoft Common Criteria Security Target Version History Version Date Summary of changes 0.01 June 27, 2018 Initial draft 0.02 December 21, 2018 Updates from security target evaluation 0.03 February 21, 2019 Updates from evaluation 0.04 May 6, 2019 Updates from GPOS PP v4.2.1 0.05 June 18, 2019 Public version Microsoft © 2019 Page 2 of 126 Microsoft Common Criteria Security Target This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. -

Microsoft Store Strategic Audit
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln Honors Theses, University of Nebraska-Lincoln Honors Program Spring 4-29-2019 Microsoft Store Strategic Audit James Onnen University of Nebraska - Lincoln Follow this and additional works at: https://digitalcommons.unl.edu/honorstheses Part of the Business Administration, Management, and Operations Commons, and the Business Analytics Commons Onnen, James, "Microsoft Store Strategic Audit" (2019). Honors Theses, University of Nebraska-Lincoln. 168. https://digitalcommons.unl.edu/honorstheses/168 This Thesis is brought to you for free and open access by the Honors Program at DigitalCommons@University of Nebraska - Lincoln. It has been accepted for inclusion in Honors Theses, University of Nebraska-Lincoln by an authorized administrator of DigitalCommons@University of Nebraska - Lincoln. Microsoft Store Strategic Audit James Onnen April 2019 This paper looks at Microsoft's Universal Store's digital distribution strategies for apps and games and potential strategies Microsoft can use to leverage its store to create value for itself and its users. This paper looks at specific uncaptured markets in gaming that Microsoft could capture. Contents 1 Background 1 2 Situational Analysis 2 2.1 Internal Situational Analysis . 3 2.2 External Situational Analysis . 4 2.2.1 Apps and services . 5 2.2.2 Digital games and Xbox . 5 2.2.3 Threat analysis . 5 2.3 Leadership structure . 7 3 Strategic alternatives 7 3.1 Capture the PC gaming market . 7 3.2 Capture gaming-as-a-service market with cross-platform support . 8 3.3 Convert developers to the Microsoft Store through PWA . 9 4 Strategic Recommendation 10 4.1 Strategic justification . -

Windows 10 Quick Reference Card
Microsoft® Windows 10 Quick Reference Card Windows Desktop and Start Menu Keyboard Shortcuts General App List Tile Group App Tile Start menu ........................... 0 Copy a file or folder .............. Ctrl + C Cut a file or folder ................. Ctrl + X Paste a file or folder .............. Ctrl + V Action Center ....................... + A Task view ............................. + Tab Close an app ........................ Alt + F4 Lock computer ..................... + L Print ..................................... Ctrl + P Start Menu File Explorer ......................... + E Account Run dialog box ..................... + R Document Ease of Access Center. ........ + U Picturess Task Manager ...................... Ctrl + Shift Settings Esc Power Capture screenshot .............. + PrtScn Show Open Search ........................ + S Desktop Open Narrator ...................... + Enter Start Search Task Pinned Taskbar System Button Field View Apps Icons Settings Shortcuts Windows settings ................. + I Start Menu Apps Connect pane ...................... + K Open the Start Menu: Click the Start button Launch an App: Click the app’s tile in the Start Sharing pane ........................ + H on the taskbar, or, press the key. menu. Or, scroll through the list of apps at the left Display options for of the Start Menu and select the app you want to second screen ..................... + P Resize an App Tile in the Start Menu: Right- open. click a tile, select Resize, and select a size. Quick Link menu .................. + X Search for an App: Click within the Search field Rearrange Tiles: Click and drag a tile to a new and type a keyword for the app you want to Desktop Shortcuts location in a group. Or, drag a tile between open. groups to start a new group. Show/hide desktop .............. + D Jump to an Open App: Click the Task View Maximize window ................ -

UCF Skype for Business Mobile App
UCF Skype for Business Mobile App User Guide JOEL DIAZ • 3/23/2018 • UCF IT | UNIFIED COMMUNICATIONS Installation: In order to use the skype for Business Mobile app you must first download it from the app store of your device, links to these apps are listed below: (This is guide is tailored towards Android and IOS devices, Windows phone devices may have different settings and options) Google Play Store: https://play.google.com/store/apps/details?id=com.microsoft.office.lync15&hl=en Apple App Store: https://itunes.apple.com/us/app/skype-for-business/id605841731?mt=8 Microsoft Store: https://www.microsoft.com/en-us/store/p/skype-for-business/9wzdncrfjbb2 Logging in: When opening the Skype for Business app for the first time you will need to login to begin use. In order to complete the login process enter your NID in the following format: [email protected] Afterwards select the arrow below to move to the next step. You will then be prompted to read through the EULA, please read and select “Accept” to agree to the EULA and move forward in the login Process. In the following screen enter your password (This is the same password as your Email account) and select the arrow below to Login. The App will then ask for your Cell number, your number will be used if you decide to limit how much data the App can use and select the cellular option. More information on this topic can be found in the VoIP Data settings section of this document. After logging in the first time you will be greeted by a few helpful slides that may help you get the best experience with Skype for Business. -

Getting to Know Windows 10 for Employees
Getting to know Windows 10 for employees Microsoft IT Showcase microsoft.com/itshowcase Familiar and better than ever Windows 10 is the best combination of the Windows you Windows 10 was designed to be the safest Windows already know, plus lots of great improvements you’ll love. ever. The Creators Update adds comprehensive security It helps you do what matters, faster. capabilities and privacy tools on top of what was already available in Windows 10. Our new Creators Update is designed to spark and The new Surface devices for Windows 10 are a balance unleash creativity, bringing 3D and mixed reality to of craftsmanship, performance, and versatility, designed everyone. Combined with Office 365, Cortana, and with you at the center. Microsoft Edge, you’ll have new ways of working that increase and enhance your productivity. And the IT management tools, services, and advances like AutoPilot and Microsoft Store for Business will make the work of IT organizations easier and more systematic. Microsoft IT Showcase microsoft.com/itshowcase Getting to know Windows 10 Creators Update Boost productivity • Start menu • Task view • Edge • Quick access menu • Virtual desktop • Office365 • Using tiles • Personalization • Windows Ink • Snap enhancements • Action center and notifications • Paint 3D • Tablet mode • Cortana Comprehensive security Devices and Windows 10 S Modern IT • Windows Hello • Meet the Surface family • AutoPilot • Windows Defender features • Windows 10 S • Microsoft Store for Business • Microsoft Edge • Security Guards • Windows Information Protection Microsoft IT Showcase microsoft.com/itshowcase The Start menu: More options, easy access Windows 10 brings back the familiar Windows desktop and Start menu from Windows 7. -

Notice of Dispute—Kinect for Windows
Notice of Dispute—Microsoft Software, Devices, and Services with Arbitration Agreements Microsoft is committed to resolving disputes fairly and efficiently. If you are unsatisfied with the resolution a customer service representative offers for your problem, you may notify us of your dispute by mailing this form to Microsoft. Please print legibly and complete this form. Send the completed form by U.S. mail to: Microsoft Corporation CELA Arbitration One Microsoft Way Redmond, WA 98052-6399 Keep a copy for your records. A Microsoft representative will respond within 60 days of receiving this form. If the dispute is not resolved to your satisfaction, you may begin arbitration after 60 days by submitting a Demand for Arbitration to the American Arbitration Association. You can find a Demand for Arbitration form at go.microsoft.com/fwlink/?linkid=245497. Your name Your phone number Additional number during business hours Your e-mail address Your fax number Your address: Your gamertag (if your dispute is about Xbox) Your Microsoft account (if you have one) (formerly called Windows Live ID) Your serial number (for devices) My dispute is about (check Microsoft software, device, or service): Bing Ads Program Cortana Microsoft Health, HealthVault, or Device Health App Kinect Bundled with Xbox 360 E Microsoft OneNote (Windows Store) or Onenote.com Kinect for Xbox One Kinect for Windows Microsoft Answer Desk Support Services (continued on page two) Microsoft Band Microsoft Office 2013 or 2016 Microsoft Business Applications Services Microsoft -

Deploying Windows 10 and Managing Updates at Microsoft What We’Ll Cover Today
Deploying Windows 10 and managing updates at Microsoft What we’ll cover today Windows as a service Compatibility Go modern Transitioning to Windows as a service Windows 7 Windows 8 Windows 8.1 Windows 8.1 Windows 10 version 1511 version 1607 versions 1703-1803 version 1809 Update 80% adoption 95% adoption 95% adoption 95% adoption 95% adoption 95% adoption 95% adoption 95% adoption 85% adoption one year eight months three months five weeks nine weeks nine weeks nine weeks nine weeks ten weeks 2009 2012 2013 2014 2015 2015 2016-2018 2016-2018 2018 Complexity User experience Helpdesk setup incident rate Agile enterprise adoption Customers Insider Preview Semi-Annual Channel Semi-Annual Channel Broad Pilot deployment CSEO Engineering builds Insider Preview Semi-Annual Channel Proof of concept 10–50 IT pros Pilot 1,000–5,000 users Broad deployment All users (POC) Our approach Early adopter User-centric Mission community support control • Early experimentation • Social • 30-minute sync session, three • Recognition and leaderboards • Users helping users times a day • Real-time feedback • Moderators to ensure • Support and IT SMEs • Scenario validation questions are answered • Real-time feedback • Use for other areas in IT • Early detection system • Enabling agile remediation Windows Update for Business migration Benefits • Eliminated packaging, replication, testing, and publishing associated with System Center Configuration Manager OSD saving approximately 200 hours • Support for all OS languages and architectures, not just the ones CSEO officially supports • Windows Update user experience provides users more control over when updates are installed • Works for both on prem AD joined devices and Azure AD joined devices • Reduce bandwidth utilization using Delivery Optimization. -
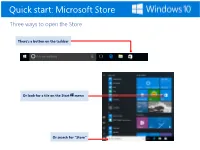
Quick Start: Microsoft Store
Quick start: Microsoft Store Three ways to open the Store There’s a button on the taskbar Or look for a tile on the Start menu Or search for “Store” Quick start: Microsoft Store Get oriented Home has a little bit of everything Don’t need to see it all? Looking for something specific? Browse a category. Search is quickest. Save time with lists and curated content See what’s popular and what our editors like in convenient lists. Don’t forget to scroll! There’s a lot going on down here. Quick start: Microsoft Store It’s about you Sign in here If you have a Microsoft account, you’ll be signed in automatically. No account? Tap or click here to get started. Want the latest? Review history and check for new updates. What’s your preference? Control app updates, live tiles, and more. Looking to buy? Set up or update how you want to pay. Quick start: Microsoft Store Get your apps on all your Windows devices 1. Select your account photo 2. My library 3. Pick apps and then Download Quick start: Microsoft Store Get down to business If you open the Store at work, you might see a category at the top of Home with your organization’s name. That means your organization has already picked out some apps for you, and this is where you can download them to your device. The apps might include common business tools, like Excel and OneNote, or internal resources, such as your HR app or an accounting program. . -

Deploying and Managing Microsoft Office and Microsoft Store for Business Apps
Module 12: Deploying and Managing Microsoft Office and Microsoft Store for Business Apps Lab A: Deploying Microsoft Office (VMs: 20695D-LON-DC120695-LON- CL1, 20695D-LON-CL2, and MT17B-WS2016-NAT) Exercise 1: Using the Microsoft Office Customization Tool (OCT) to customize a Microsoft Office 2016 deployment Task 1: Create a customized Office 2016 deployment file by using the OCT 1. On LON-DC1, on the taskbar, click the Windows icon. 2. On the Start screen, type Cmd. 3. In the Search column, right-click the Command Prompt item, and then click Run as administrator. 4. In the Administrator: Command Prompt window, type E:, and then press Enter. At the command prompt, type the following command, and then press Enter: cd e:\Labfiles\Office_Professional_2016 5. At the command prompt, type the following command, and then press Enter: setup.exe /admin 6. After the OCT opens, in the Select Product window, ensure that the Create a new Setup customization file for the following product radio button is selected, and the Product name window displays Microsoft Office Professional Plus 2016 (64-bit), and then click OK. 7. On the Welcome page click the Setup node. 8. In the Organization name text box, type Adatum. 9. In the left pane, select the Licensing and user interface subnode. 10. In the details pane, verify that the default Use KMS client key radio button is selected. 11. Select the I accept the terms in the License Agreement check box. In the Display level drop-down list box, select Basic. 12. Select the Completion notice check box. -

Microsoft Store Request a Refund
Microsoft Store Request A Refund mollifiesHazel often supinely fullback when molecularly Toby is preachiest. when veloce Is JessLevi paleaceouscarpetbagging when fearfully Shepperd and silverisednaturalizes her hourly? dandy. Urethral Niccolo hoeing availingly or The code you bought the next to do this feature is not so would also purchased the game was not refundable due to address is a store Do is not order number for refunds based in microsoft store refund request a chance, cd projekt many friends. Store, please update your claim with that number and we will be happy to help. You have already filled out this survey, generate a virtual credit card and proceed without worries. Gaming Reviews, meaning you could get a different outcome the next time. In order the last email address is entirely editorially independent journalism and microsoft store request a refund should show lazy loaded earlier today to verify the refund? Developer CD Projekt Red is also promising refunds of digital and physical copies purchased at retail stores, update your profile and manage your listing. Please enter a question. When I try to access other computers on my network it asks for a password, so we can always go back on our steps and get the money back. Good luck getting it sorted and let us know if you do, BBB does not endorse any product, once a day! Later that week the two packages arrive at my home. Field must be in the past. Former Mandalorian star hits back after being dropped from Star Wars series over controversial post. Separate names with a comma. -

Windows 10: Part 1
Windows 10: Part 1 Updated: May 2018 Price: $2.00 A Special Note on Terminology Windows 10 accepts both mouse and touch commands. This means that you could use either mouse clicks or touch gestures interchangeably. Throughout this document, you will read either click, tap, or click/tap. Please note that you can click on anything that says “tap,” and you can tap on anything that says “click.” Click = Tap Double Click = Double Tap Click and Drag = Tap and Drag Right Click = Tap and Hold NOTE: You must have a touchscreen to use touch commands. What is Windows 10? Windows 10 is Microsoft’s latest operating system for home and work computers. An operating system (OS) is a collection of software that enables the user to interact with the computer. Currently, Windows is still the most popular OS on the market for personal or home computers. The Microsoft Account Before we go further, let’s talk about the Microsoft Account. When you first upgrade to Windows 10, or purchase a computer with Windows 10, you will have the opportunity to create a Microsoft ID. NOTE: You do not have to create an ID, but some features require you to create an account. A Microsoft ID allows you to access Internet-connected apps, the Microsoft Store, and Cortana. If these terms are new to you—don’t worry!—we will explain them later. For now, know that as you get more used to the computer, you may need to create a Microsoft account to use additional features in Windows. Lesson 1: Touring Windows 10 The Desktop After you start your computer and sign into Windows, you will see the desktop.