Ubiquitous Client Side Customization of Web Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fall 2011 Section 5T1 Syllabus
GEORGE MASON UNIVERSITY COLLEGE OF EDUCATION AND HUMAN DEVELOPMENT Instructional Technology EDIT 772: Introduction to Web 2.0 / Social Software Tools (2 graduate credit hours) Fall 2011 COURSE DATES: meets online Aug 29, 2011 - Nov 04, 2011 and has a required synchronous meeting the last week of the class. INSTRUCTOR INFORMATION Name: Jane Bozarth, [email protected] / Google Voice 919 789 1611 Virtual Office Hours: Mondays, 6:30-7pm with notification and other times by appointment. COURSE DESCRIPTION The purpose of this course is to explore examples of emerging technology use commonly referred to as Web 2.0. The course focuses, from an e-learning perspective, on the pedagogical applications and implications of a particular group of Web 2.0 or social software tools that facilitate web-based social interaction, content generation, and resource aggregation. Examples of social software include content, media, or collaboration management frameworks such as blogs, wikis, Flickr, YouTube, RSS feed readers, and iTunes, relationship management frameworks such as Facebook and Ning, and distributed classification frameworks (or social bookmarking services), such as Delicious. Students will also be introduced to broader patterns of Web 2.0 technologies, such as rich Internet applications, mash-ups, widgets, and much more. Virtual worlds, augmented reality, mobile devices and gaming are not covered in this course. The course goals bridge three broad areas: to provide an engaging overview of cutting-edge social technologies, to identify and evaluate best educational practices for using these technologies, and to investigate the role of these technologies for online learning. Social software has the potential to transform teaching practices as it supports the creation of highly constructivist learning communities. -

PFC.Pdf (6005Mb)
APLICACIÓ RICA D’INTERNET PER A LA CONSULTA AMB TEXT I IMATGE AL REPOSITORI DE VÍDEOS DE LA CORPORACIÓ CATALANA DE MITJANS AUDIOVISUALS RAMON SALLA ROVIRA TUTORITZAT PER XAVIER GIRÓ I XAVIER VIVES 1 MOTIVACIÓ Fa més de dos anys vaig entrar a treballar a la Corporació Catalana de Mitjans Audiovisuals per donar suport a diferents projectes subvencionats a nivell estatal i europeu. El present document és la memòria del projecte final de carrera realitzat en aquesta empresa durant l’any 2009. La Corporació és una empresa catalana puntera en innovació en el camp dels mitjans de comunicació destinada al servei públic per transmetre informació i entreteniment amb la màxima qualitat possible. Entrar-hi a treballar ha suposat un revulsiu en la meva orientació com a enginyer i m’ha introduït a un sector, destinat a la producció, postproducció, emmagatzematge, cerca, indexació i distribució. Aquesta experiència ha estat, com a mínim, apassionant. El projecte i3media1, subvencionat per l’estat espanyol, pretén unir en un sol marc col·laboratiu empreses punteres del sector per tal d’impulsar els continguts intel·ligents, la personalització i els processos automàtics. Comptar dins d’aquest projecte amb el grup de recerca de processat de la imatge de la Universitat Politècnica de Barcelona (GPI) és una idoneïtat que em permet mantenir les arrels amb la meva universitat. Aquest fet, em porta a tirar endavant aquest projecte final de carrera que culmina la meva aspiració de ser enginyer i permet aportar el meu humil gra d’arena a l’ambiciós projecte del que tinc l’orgull i la sort de formar part. -

A Web Desktop Or Webtop Is a Desktop Environment Embedded in a Web Browser Or Similar Client Application
II BASIC THEORY II.1 What is Web Desktop? A web desktop or webtop is a desktop environment embedded in a web browser or similar client application. A webtop integrates web applications, web services, client-server applications, application servers, and applications on the local client into a desktop environment using the desktop metaphor. Web desktops provide an environment similar to that of Windows, Mac, or a graphical user interface on Unix and Linux systems. It is a virtual desktop running in a web browser. In a webtop the applications, data, files, configuration, settings, and access privileges reside remotely over the network. Much of the computing takes place remotely. The browser is primarily used for display and input purposes. II.2 History In the context of a web desktop, the term Webtop was first introduced by the Santa Cruz Operation (SCO) in 1994 for a web-based interface to their UNIX operating system. Andy Bovingdon and Ronald Joe Record, who both explored the concepts in different directions, are often credited as the inventors. II.3 About eyeOS eyeOS is an open source web desktop written in mainly PHP, XML, and JavaScript. It acts as a platform for web applications written using the eyeOS Toolkit. It includes a Desktop environment with 67 applications and system utilities. It is accessible by portable devices via internet. III.3 eyeOS Implementation III.3.1 Advantages of eyeOS • Convenience: A personalized desktop on every supported client device • Mobility: Access your desktop anywhere there is a supported client device • Session Management: Server-side session management allows roaming users to access restored sessions from anywhere III.3.2 Limitations Security: Due to the fact that all data is transferred over the internet, it might be possible for a hacker to intercept the connection and read data. -
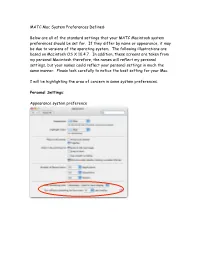
MATC Mac System Preferences Defined
MATC Mac System Preferences Defined: Below are all of the standard settings that your MATC Macintosh system preferences should be set for. If they differ by name or appearance, it may be due to versions of the operating system. The following illustrations are based on Macintosh OS X 10.4.7. In addition, these screens are taken from my personal Macintosh therefore, the names will reflect my personal settings, but your names could reflect your personal settings in much the same manner. Please look carefully to notice the best setting for your Mac. I will be highlighting the area of concern in some system preferences. Personal Settings: Appearance system preference MATC Macintosh Standard System Preferences Dashboard and Expose Desktop and Screen Saver Page 2 MATC Macintosh Standard System Preferences Dock International See edit list on the next page. Page 3 MATC Macintosh Standard System Preferences Edit list for the language list. Please keep English checked and active. Formats Page 4 MATC Macintosh Standard System Preferences Input Menu. This is where the keyboard viewer is located. Security-No Master Password! Page 5 MATC Macintosh Standard System Preferences Spotlight Page 6 MATC Macintosh Standard System Preferences Hardware Settings Bluetooth Settings Bluetooth Devices Page 7 MATC Macintosh Standard System Preferences Bluetooth Sharing CD’s and DVD’s Displays Show displays in menu bar for easy access to changing the display resolutions. Page 8 MATC Macintosh Standard System Preferences Energy Saver. Set the computer to never sleep everywhere! Energy Saver-Laptop Battery Settings Page 9 MATC Macintosh Standard System Preferences Keyboard and Mouse Trackpad-for Laptop users Notice the new feature for new Macintosh Laptop Users! Page 10 MATC Macintosh Standard System Preferences Mouse-Mighty Mouse users Bluetooth Settings Page 11 MATC Macintosh Standard System Preferences Keyboard Shortcuts Print and Fax Main The printers will be personalized for each person and each Mac. -

Review of Service Composition Interfaces
Sanna Kotkaluoto, Juha Leino, Antti Oulasvirta, Peter Peltonen, Kari‐Jouko Räihä and Seppo Törmä Review of Service Composition Interfaces DEPARTMENT OF COMPUTER SCIENCES UNIVERSITY OF TAMPERE D‐2009‐7 TAMPERE 2009 UNIVERSITY OF TAMPERE DEPARTMENT OF COMPUTER SCIENCES SERIES OF PUBLICATIONS D – NET PUBLICATIONS D‐2009‐7, OCTOBER 2009 Sanna Kotkaluoto, Juha Leino, Antti Oulasvirta, Peter Peltonen, Kari‐Jouko Räihä and Seppo Törmä Review of Service Composition Interfaces DEPARTMENT OF COMPUTER SCIENCES FIN‐33014 UNIVERSITY OF TAMPERE ISBN 978‐951‐44‐7896‐3 ISSN 1795‐4274 Preface This report was produced in the LUCRE project. LUCRE stands for Local and User-Created Services. The project is part of the Flexible Services research programme, one of the programmes of the Strategic Centre for Science, Technology and Innovation in the ICT field (TIVIT) and funded by Tekes (the Finnish Funding Agency for Technology and Innovation) and the participating organizations. The Flexible Service Programme creates service business activity for global markets. The programme has the aim of creating a Web of Services. The programme creates new types of ecosystems, in which the producers of services, the people that convey the service and the users all work together in unison. As part of such ecosystems, LUCRE will develop an easy-to-use, visual service creation platform to support the creation of context aware mobile services. The goal is to support user-driven open innovation: the end- users (people, local businesses, communities) will be provided with tools to compose new services or to modify existing ones. The service creation platform will build on the technology of existing mashup tools, widget frameworks, and publish/subscribe mechanisms. -

Challenging the Dominant Design of Educational Systems. Scott Wilson University of Bolton, [email protected]
University of Bolton UBIR: University of Bolton Institutional Repository Educational Cybernetics: Journal Articles (Peer- Institute for Educational Cybernetics Reviewed) 2007 Personal Learning Environments : challenging the dominant design of educational systems. Scott Wilson University of Bolton, [email protected] Oleg Liber University of Bolton, [email protected] Mark Johnson University of Bolton, [email protected] Philip Beauvoir University of Bolton, [email protected] Paul Sharples University of Bolton, [email protected] See next page for additional authors Digital Commons Citation Wilson, Scott; Liber, Oleg; Johnson, Mark; Beauvoir, Philip; Sharples, Paul; and Milligan, Colin. "Personal Learning Environments : challenging the dominant design of educational systems.." (2007). Educational Cybernetics: Journal Articles (Peer-Reviewed). Paper 9. http://digitalcommons.bolton.ac.uk/iec_journalspr/9 This Article is brought to you for free and open access by the Institute for Educational Cybernetics at UBIR: University of Bolton Institutional Repository. It has been accepted for inclusion in Educational Cybernetics: Journal Articles (Peer-Reviewed) by an authorized administrator of UBIR: University of Bolton Institutional Repository. For more information, please contact [email protected]. Authors Scott Wilson, Oleg Liber, Mark Johnson, Philip Beauvoir, Paul Sharples, and Colin Milligan This article is available at UBIR: University of Bolton Institutional Repository: http://digitalcommons.bolton.ac.uk/iec_journalspr/9 Methodologies and scenarios Personal Learning Environments: Challenging the dominant design of educational systems Scott Wilson, Prof. Oleg Liber, Mark Johnson, Phil Beauvoir, Paul Sharples & Colin Milligan University of Bolton, UK; Scott.Bradley.Wilson@gmail. com, [email protected], [email protected], [email protected], [email protected], colin. -

Digital Infrastructure Moonshot for Africa
Connecting Africa Through Broadband A strategy for doubling connectivity by 2021 and reaching universal access by 2030 Running footer 1 Connecting Africa Through Broadband A strategy for doubling connectivity by 2021 and reaching universal access by 2030 Broadband Commission Working Group on Broadband for All: A “Digital Infrastructure Moonshot” for Africa October 2019 Table of Contents Foreword .............................................................................................................................................8 Acknowledgements ........................................................................................................................ 12 Executive Summary ........................................................................................................................ 14 Abbreviations ....................................................................................................................................22 1. Introduction ...............................................................................................................................24 2. Snapshot of Africa’s Digital Infrastructure ...........................................................................34 3. Mission, Vision, and Principles for Digital Transformation in Africa ...............................46 4. Investment Requirements for 2021 and 2030 Digital Infrastructure Targets ..............56 5. Policy and Regulatory Frameworks to Enable Digital Transformation ..........................68 6. Digital Skills -

Web 2.0 Et Bibliothèques
Web 2.0 et bibliothèques LOUKEM Mohamed El Hadi1 - ALIOUALI Nadia2 Division Recherche & Développement en Science de l’Information CERIST, 5, rue des trois frères Aissou, Ben-Aknoun, Alger, Algérie [email protected] , 2 [email protected] Résumé : Le monde de l’information connaît un contexte de transformations intenses. La dématérialisation de l’information et l’accès via internet participent à rendre les bibliothèques de moins en moins visibles et incitent l’usager à se détourner des médiateurs traditionnels d’informations. Le web 2.0 est un nouveau genre collaboratif en ligne. Nombreuses sont les bibliothèques qui expérimentent aujourd’hui son lot d’usages informationnels. L’objectif est d’améliorer leurs moyens de communication afin de se positionner comme un membre actif des communautés développées et œuvrer pour l’échange et le partage d’information. Le succès du web 2.0 nécessite une analyse afin de tenter de définir un concept fortement employé depuis quelques années mais, il est très difficile de déterminer les frontières tant théoriques que techniques. Nous proposons dans cet article une synthèse sur ce phénomène, ses usages et son impact sur les bibliothèques. Mots : clés : web social; web 2.0; outils du web social; usages; bibliothèque. Introduction L’émergence du web 2.0 est apparue comme un nouveau bouleversement majeur. Symbolisé par quelques applications phares, comme Youtube, Wikipedia, MySpace ou encore les blogs, le web 2.0 regroupe en réalité un ensemble de pratiques considérées comme nouvelles. Toutes sont basées sur le retour de l’usager au cœur des dynamiques de production et d’échange de contenu. -

Google Acks First Edition
RflCKSl Google acks First Edition Philipp Lenssen O'REILLT BEIJING • CAMBRIDGE • FARNHAM • KÖLN • PARIS • SEBASTOPOL • TAIPEI • TOKYO :;:;; »p;;;» mmm ;*. ^ P;i?|p:*: JK*S,. FOREWORD xi PREFACE xiii Google's Apps—a Google Office, or a Google OS? xiii How to Use This Book xiv HowThis Book Is Organized xiv Conventions Used in This Book xvi Acknowledgments xvi We'd Like to Hear from You xvii CHAPTER Ol: MEETTHE GOOGLE DOCS FAMILY 2 HACK oi: How to Get Your Google Account 2 HACK 02: Collaborate with OthersThrough Google Docs 5 HACK 03: Make a Desktop Icon to Create a New Document 9 HACK 04: Embed a Dynamic Chart into a Google Document or a Web Page 12 HACK 05: Share Documents with a Group 16 HACK 06: Automatically Open Local Files with Google 17 HACK 07: Google Docs on the Run 19 HACK 08: Back Up All Your Google Docs Files 21 HACK 09: Beyond Google: Create Documents with Zoho, EditGrid, and more 23 CHAPTER 2: THE GOOGLE DOCS FAMILY: GOOGLE DOCUMENTS 28 HACK 10: Let Others Subscribe to Your Document Changes 28 HACK U: Blog with Google Docs 31 HACKI2: Insert Special Characters Into Your Documents 34 HACK 13: Search and ReplaceText Using Regulär Expressions 35 HACK 14: "Google Docs Light" for Web Research: Google Notebook 39 HACKI5: Convert a Word File Intoa PDF with Google Docs 42 HACK 16: Write a JavaScript Bookmarklet to Transmogrify Your Documents 44 HACK 17: Remove Formatting Before PastingText Into a Document 47 HACK 18: Prettify Your Document with Inline Styles 47 v CHAPTER 3: THE GOOGLE DOCS FAMILY: GOOGLE SPREADSHEETS 52 HACK 19: Add -

Mapping Web Personal Learning Environments
Mapping Web Personal Learning Environments Matthias Palmér1,Stéphane Sire2,Evgeny Bogdanov2, Denis Gillet2 and Fridolin Wild3 1 Royal Institute of Technology (KTH), Stockholm, Sweden, [email protected] 2 École Polytechnique Fédérale de Lausanne (EPFL), Lausanne, Switzerland, {stephane.sire, evgeny.bogdanov, denis.gillet}@epfl.ch 3 The Open University, Milton Keynes, United Kingdom, [email protected] Abstract.A recent trend in web development is to build platforms which are carefully designed to host a plurality of software components (sometimes called widgets or plugins) which can be organized or combined (mashed-up) at user's convenience to create personalized environments. The same holds true for the web development of educational applications. The degree of personalization can depend on the role of users such as in traditional virtual learning environment, where the components are chosen by a teacher in the context of a course. Or, it can be more opened as in a so-called personalized learning environment (PLE). It now exists a wide array of available web platforms exhibiting different functionalities but all built on the same concept of aggregating components together to support different tasks and scenarios. There is now an overlap between the development of PLE and the more generic developments in web 2.0 applications such as social network sites. This article shows that 6 more or less independent dimensions allow to map the functionalities of these platforms: the screen dimensionmaps the visual integration, the data dimension mapsthe portability of data, the temporal dimension mapsthe coupling between participants, the social dimension maps thegrouping of users, the activity dimension mapsthe structuring of end users’ interactions with the environment, and the runtime dimensionmaps the flexibility in accessing the system from different end points. -

Lista Ofrecida Por Mashe De Forobeta. Visita Mi Blog Como Agradecimiento :P Y Pon E Me Gusta En Forobeta!
Lista ofrecida por mashe de forobeta. Visita mi blog como agradecimiento :P Y pon e Me Gusta en Forobeta! http://mashet.com/ Seguime en Twitter si queres tambien y avisame que sos de Forobeta y voy a evalu ar si te sigo o no.. >>@mashet NO ABUSEN Y SIGAN LOS CONSEJOS DEL THREAD! http://blog.newsarama.com/2009/04/09/supernaturalcrimefightinghasanewname anditssolomonstone/ http://htmlgiant.com/?p=7408 http://mootools.net/blog/2009/04/01/anewnameformootools/ http://freemovement.wordpress.com/2009/02/11/rlctochangename/ http://www.mattheaton.com/?p=14 http://www.webhostingsearch.com/blog/noavailabledomainnames068 http://findportablesolarpower.com/updatesandnews/worldresponsesearthhour2009 / http://www.neuescurriculum.org/nc/?p=12 http://www.ybointeractive.com/blog/2008/09/18/thewrongwaytochooseadomain name/ http://www.marcozehe.de/2008/02/29/easyariatip1usingariarequired/ http://www.universetoday.com/2009/03/16/europesclimatesatellitefailstoleave pad/ http://blogs.sjr.com/editor/index.php/2009/03/27/touchinganerveresponsesto acolumn/ http://blog.privcom.gc.ca/index.php/2008/03/18/yourcreativejuicesrequired/ http://www.taiaiake.com/27 http://www.deadmilkmen.com/2007/08/24/leaveusaloan/ http://www.techgadgets.in/household/2007/06/roboamassagingchairresponsesto yourvoice/ http://blog.swishzone.com/?p=1095 http://www.lorenzogil.com/blog/2009/01/18/mappinginheritancetoardbmswithst ormandlazrdelegates/ http://www.venganza.org/about/openletter/responses/ http://www.middleclassforum.org/?p=405 http://flavio.castelli.name/qjson_qt_json_library http://www.razorit.com/designers_central/howtochooseadomainnameforapree -

Mac OS X Support Essentials V10.6
APPLE CERTIFIED SUPPORT PROFESSIONAL V10.6 MASSARIC AT GMAIL DOT COM NOTEBOOK PAGE 1 OF 43 APPLE CERTIFIED SUPPORT PROFESSIONAL V10.6 MASSARIC AT GMAIL DOT COM Apple Certified Support Professional v10.6 9 Disclaimer 9 Installation and Initial Setup 10 1. What Utilities are available when booted from the Mac OS X Install DVD? 10 2. What are the minimum hardware requirement for installing Mac OS X v10.6? 10 3. What four preparation steps must you take before installing Mac OS X? 10 4. What are the advantages and disadvantages of using a single-partition drive with Mac OS X? How about a multiple-partition drive? 11 5. Which packages are installed by default when installing Mac OS X? 11 6. Where can you locate the System Version Number, Build Number, Serial Number? What is the significance of these numbers? 11 7. How do the four System Preferences categories differ? 12 8. How do you ensure that you have the latest Apple Software? 12 User Accounts 13 9. What are the five types of user accounts in Mac OS X? How are they different? 13 10. What are account attributes 13 11. How can you limit a user account? 14 12. What are some security risks associated with each type of user account? 14 13. What default folders make up a user’s home folder 15 14. What three types of resources contention can occur when fast use switching is enabled? 15 15. What security risk can occur when fast user switching is enabled? 15 16. What does a keychain do? 15 17.