Volume 3 Issue 5.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

List of Participating Universities of the HUMAP
List of Participating Universities of the HUMAP (As of April, 2015) Japan Ashiya University (Taiwan) Kai Nan University (Hyogo) Himeji Dokkyo University National Kaohsiung First University of Science and Technology (25) Hyogo University National Taichung University Hyogo University of Teacher Education National Taipei University Kansai University of International Studies National Taiwan University of Arts Kobe City College of Nursing National Taiwan Ocean University Kobe City University of Foreign Studies National Yunlin University of Science and Technology Kobe College Providence University Kobe Design University Shu-Te University Kobe Gakuin University Southern Taiwan University of Technology Kobe International University Tunghai University Kobe Pharmaceutical University Indonesia Airlangga Univeresity Kobe Shinwa Women's University (11) Bung Hatta University Kobe Shoin Women's University Darma Persada University Kobe University Gadjah Mada University Kobe Women's University Hasanuddin University Konan University Institut Teknologi Bandung Konan Women's University Institut Teknologi Sepuluh Nopember Koshien University Satya Wacana Christian University Kwansei Gakuin University Syiah Kuala University Mukogawa Women's University Udayana University Otemae University University of Indonesia Sonoda Women's University Korea Ajou University University of Hyogo* (29) Cheju National University University of Marketing and Distribution Sciences Chosun University Dong-A University Australia Australian Maritime College Dong Seo University (11) Curtin -

Education, Libraries and Lis Education in the Republic of South Korea
Library Progress(International). Vol.36(No.2)2016:P.99-116 DOI 10.5958/2320-317X.2016.00009.X Print version ISSN 0970 1052 Online version ISSN 2320 317X EDUCATION, LIBRARIES AND LIS EDUCATION IN THE REPUBLIC OF SOUTH KOREA Younghee Noh* and M P Satija** *Professor & Head, Department of Library &Information Science, Konkuk University, Chungju, South Korea **Dr M P Satija, Professor (Rtd.), Dept. of Library and Information Science, Guru Nanak Dev University, Amritsar, India Received on 20 September 2016: Accepted on 22 November 2016 ABSTRACT Briefly describes the geography, economic and education culture of South Korea. Explains its higher education system which has a very high GER. States that education has significantly contributed to its high economic growth in a very short period starting from 1960s. Dwells on the state of public, academic and special libraries. Public libraries are quite a developed lot due to socially active programs like “Citizen Action for Reading Culture”. Lastly it explains the origin and development of LIS education from graduate to doctoral programmes in South Korea since 1950s. Appendixes give data about all types of libraries, LIS schools, Procedure for Ph.D. and curricula for master and graduate programs. Keywords: Higher education- South Korea, Korean Library Association, Libraries-South Korea, Library education-South Korea , South Korea. INTRODUCTION The Country and its Culture Geographically entire Korea is a mountainous peninsula between the yellow sea and the Korean straits which has is south eastern border with Manchuria. The peninsula covers an area of more than 85000 square miles of which South Korea, a sovereign nation since 1948, comprises of 38000 square miles. -

Schedule of Accreditations, by Year and University
Comprehensive University Accreditation System Schedule of Accreditations, by Year and University Korean Council for University Education Center for University Accreditation 2nd Cycle Accreditations (2001-2006) Table 1a: General Accreditations, by Year Conducted Section(s) of University Evaluated # of Year Universities Undergraduate Colleges Undergraduate Colleges Only Graduate Schools Only Evaluated & Graduate Schools 2001 Kyungpook National University 1 2002 Chonbuk National University Chonnam National University 4 Chungnam National University Pusan National University 2003 Cheju National University Mokpo National University Chungbuk National University Daegu University Daejeon University 9 Kangwon National University Korea National Sport University Sunchon National University Yonsei University (Seoul campus) 2004 Ajou University Dankook University (Cheonan campus) Mokpo National University 41 1 Name changed from Kyungsan University to Daegu Haany University in May 2003. 1 Andong National University Hanyang University (Ansan campus) Catholic University of Daegu Yonsei University (Wonju campus) Catholic University of Korea Changwon National University Chosun University Daegu Haany University1 Dankook University (Seoul campus) Dong-A University Dong-eui University Dongseo University Ewha Womans University Gyeongsang National University Hallym University Hanshin University Hansung University Hanyang University Hoseo University Inha University Inje University Jeonju University Konkuk University Korea -

Gwangju-Jeonnam KOTESOL Chapter Reports the Archive
Gwangju-Jeonnam KOTESOL Chapter Reports The Archive Contents Chapter Reports 2004 – 2011 KOTESOL in Action, The English Connection (TEC) Chapter Reports 2011 – 2013 KOTESOL Chapter News, TEC News Gwangju-Jeonnam Chapter Presidents 2004 Spring – 2005 November Maria Lisak 2005 November – 2006 March Scott Jackson 2006 March – 2008 March 15 Dr. Yeon-seong Park 2008 March 15 – 2009 November Adriane Moser Geronimo 2009 November – 2016 November Dr. David E. Shaffer 2016 November – 2017 November William Mulligan 2017 November – 2018 November Lindsay Herron 2018 November – Bryan Hale regions, and would then spread out to JEOLLA CHAPTER SEOUL CHAPTER those areas without a KOTESOL presence. At a later stage, we will cultivate speaking links with sister organizations and by Allison Bill by Tory Thorkelson governmental entities. To this end Dr. Robert Dickey has expressed interest in Perhaps the title for this section should As winter approaches, The Seoul chapter KTT giving presentations in the southern be Jeonbuk/Jeonnam Chapters (plural). By is gearing up for our regional conference part of the nation, possibly as early as the time you are reading this TEC, a in May, 2004. After a hiatus of 3 months January. Paul Mead has also expressed decision should have been made about for summer vacation, the YL SIG and the interest in doing this for the Pusan area, whether or not to split Jeolla Chapter into 11th KOTESOL International Conference, and Dr. Steve Garrigues will speak under two chapters: a Jeonju-Jeonbuk Chapter our monthly meetings resumed with a the KTT banner to a group in Taegu. So, in the north and a Gwangju-Jeonnam presentation on November 15th by our new we are off to a good start in 2004! Chapter in the south. -
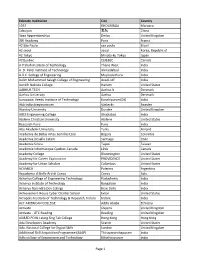
List AWS Educate Institutions
Educate Institution City Country 1337 KHOURIBGA Morocco 1daoyun 无锡 China 3aaa Apprenticeships Derby United Kingdom 3W Academy Paris France 42 São Paulo sao paulo Brazil 42 seoul seoul Korea, Republic of 42 Tokyo Minato-ku Tokyo Japan 42Quebec QUEBEC Canada A P Shah Institute of Technology Thane West India A. D. Patel Institute of Technology Ahmedabad India A.V.C. College of Engineering Mayiladuthurai India Aalim Muhammed Salegh College of Engineering Avadi-IAF India Aaniiih Nakoda College Harlem United States AARHUS TECH Aarhus N Denmark Aarhus University Aarhus Denmark Aarupadai Veedu Institute of Technology Kanchipuram(Dt) India Abb Industrigymansium Västerås Sweden Abertay University Dundee United Kingdom ABES Engineering College Ghaziabad India Abilene Christian University Abilene United States Research Pune Pune India Abo Akademi University Turku Finland Academia de Bellas Artes Semillas Ltda Bogota Colombia Academia Desafio Latam Santiago Chile Academia Sinica Taipei Taiwan Academie Informatique Quebec-Canada Lévis Canada Academy College Bloomington United States Academy for Career Exploration PROVIDENCE United States Academy for Urban Scholars Columbus United States ACAMICA Palermo Argentina Accademia di Belle Arti di Cuneo Cuneo Italy Achariya College of Engineering Technology Puducherry India Acharya Institute of Technology Bangalore India Acharya Narendra Dev College New Delhi India Achievement House Cyber Charter School Exton United States Acropolis Institute of Technology & Research, Indore Indore India ACT AMERICAN COLLEGE -

A Companion Publication to the English Connection Winter 2012
TTEECC NNeewwss A Companion Publication to The English Connection Winter 2012, Volume 2, Number 4 TEC News 2 (4) Winter 2012 TEC NEWS TEC NEWS Words from the First Vice-President ............................ 3 CCoonntteennttss Featured Chapter.......................................................... 4 Featured SIG ................................................................. 5 Featured Member .…….…….…..…………………..…7 Perspectives on the KOTESOL Int’l Conference 1 ......... 9 Perspectives on the KOTESOL Int’l Conference 2 ...... 10 JALT 2012 Conference Report ...................................... 11 PAC-FEELTA 2012 Conference Report .......................... 13 ETA-ROC 2012 Conference Report ............................... 15 MEXTESOL 2012 Conference Views ............................. 17 KOTESOL Chapter News ............................................. 19 Special Interest Group News ...................................... 25 KOTESOL Members in the News ................................ 27 KOTESOL Events Calendar ........................................... 31 Korea-Wide Events ...................................................... 31 2012-13 International ELT Conference Calendar .......... 32 The KOTESOL Directory .............................................. 34 Editorial Team TEC News Editor: Dr. David E. Shaffer Associate Editor: Maria Pinto In Association with The English Connection – Editor-in-Chief William Mulligan TEC News, published quarterly, is the online companion publication of The English Connection (TEC), the official -

Books KOREAN FOLK TALES for CHILDREN SERIES
Books on KOREA Winter 2018-19 kodansha europe www.kodansha.eu Kodansha Europe is a wholly-owned subsidiary of Kodansha Ltd. of Tokyo, Japan. In addition to the English-language titles published within the group, we also represent a number of other publishers from other parts of Asia, as well as Africa. In this catalogue you will find all our English language books on all aspects of Korea currently available from Hollym Corp., as well as the variety of publishers exported under the umbrella of Kong & Park. These include selected titles from Jimoondang, Longtail Books, Yonsei University Press, The Academy of Korean Studies Press, Cum Libro, Bookhouse and, of course, Kong & Park. While this catalogue is semi-annual (Spring and Autumn), it is also updated if required in between. It is currently only available in PDF format. We welcome interest from anyone with books about Korea in English seeking distribution and trade representation in the U.K., continental Europe, Africa, the Middle East and Southeast Asia who feels that their books or products may fit our portfolio. You can reach us via our website, or by email at: [email protected] PRICES CORRECT AT JULY 31ST, 2018 Our books are imported and paid for in foreign currency. Owing to the continuing volatility of GBP in the currency markets, prices may be subject to further change over the course of the next 12 months: up or down. The PDF of this catalogue will be updated accordingly. FOREIGN RIGHTS Rights enquiries for all our Korean books should be directed to the original publisher. -

THE IEEE 18Th INTERNATIONAL CONFERENCE on ADVANCED COMMUNICATIONS TECHNOLOGY "Information and Communications for Safe and Secure Life!"
THE IEEE 18th INTERNATIONAL CONFERENCE ON ADVANCED COMMUNICATIONS TECHNOLOGY "Information and Communications for Safe and Secure Life!" Phoenix Park, PyeonhChang, PROCEEDING Republic of Korea IEEE Catalog Number: CFP16561-CDR Jan. 31 ~ Feb. 3, 2016 ISBN: 978-89-968650-7-0 ISSN: 1738-9445 Organizer Global IT Research Institute (GiRI) Sponsors IEEE Communication Society (IEEE ComSOc) Gangwon Convention & Visitors Bureau National Information Society Agency (NIA) Electronics and Telecommunications Research Institute (ETRI) Korean Institute of Communication Sciences(KICS) IEEK Communication Society(IEEK ComSoc) Korean Institute of Information Scientists and Engineers(KIISE) Open Standards and Internet Association(OSIA) Korea Institute of Information Security & Crytology 2 Indexes Messages ......................................................................................................... 5 Objectives ......................................................................................................... 7 Committees ....................................................................................................... 8 Session Overview ........................................................................................... 18 Tutorial .............................................................................................................. 20 Plenary Keynote Speech ................................................................................ 21 Technical Sessions ........................................................................................... -

Korean Council for University Education Bringing Change and Innovation to Universities 2015-2016 Contents
RM 2015-10-667 Korean Council for University Education bringing change and innovation to universities 2015-2016 Contents Part 1 Introduction to the Korean Council for University Education (KCUE) KCUE’s function and role ● Overview of KCUE ● Key Projects KCUE’s key projects ● University Admission System ● Institutional Accreditation ● Information Disclosure of Higher Education Institution Part 2 Overview of Higher Education in Korea Part 3 List of Member Universities Part 4 KCUE’s MOUs Part I Introduction to the Korean Council for University Education (KCUE) KCUE’s function and role Overview of KCUE ■ The Korean Council for University Education (KCUE), as a consultation body and an intermediary between the government and the universities, seeks to promote sound development of universities through autonomous rule and mutual cooperation in the universities to bring together and represent the collective voices of universities to the government and the National Assembly; and to conduct projects commissioned by the government. That is, through the process of building consensus and cooperation between universities, the KCUE helps Korean universities make progress in their pursuit of achieving greater autonomy and fulfilling their responsibilities in response to the expectations from the government and the public. ■ The KCUE serves as a buffer between universities and the government by faithfully representing the universities’ needs and guiding the right direction for future policy development. In addition, the KCUE conducts projects commissioned by the government and supports universities. Furthermore, the KCUE submits opinions to the National Assembly in regard to enactment and amendment of laws related to university education. The KCUE periodically receives parliamentary audits of overall projects and its implementation to ensure its role as a public institution. -

Open Dissertation Kim.Pdf
The Pennsylvania State University The Graduate School THE EXPANSION OF SCIENCE PRODUCTION AT KOREAN UNIVERSITIES, 1970–2017 A Dissertation in Educational Theory and Policy by Hyerim Kim © 2019 Hyerim Kim Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy August 2019 The dissertation of Hyerim Kim was reviewed and approved* by the following: David P. Baker Professor of Education and Sociology Dissertation Advisor Chair of Committee Soo-yong Byun Associate Professor of Education Maryellen Schaub Associate Professor of Education Education and Public Policy Liying Luo Assistant Professor of Sociology and Demography Katerina Bodovski Associate Professor of Education Chair of Graduate Program, Educational Theory and Policy *Signatures are on file in the Graduate School. ii ABSTRACT Since 1970, when Korean researchers published the first journal article from their country to be cataloged in the Science Citation Index Expanded (SCIE), science production has exponentially expanded among Korean universities. This rapid growth was not driven by a few specific institutions. Rather, it was possible because virtually all universities with STEM programs, regardless of their institutional mission, participated in scholarly publishing. Meanwhile, the Korean government implemented a special research funding initiative, Brain Korea 21, in 1999 to stimulate science production among universities. Using multilevel linear regression models, this dissertation examines the effect of the BK 21 program; it finds that BK 21 had a positive effect on publications, but that its effect turned insignificant when more comparable groups of universities were examined. This research also demonstrates that the scientific collaboration network in Korea has moved from one strongly dominated by a few specific actors to one with more actors participating more equally and significantly. -

Course Analysis of Library and Information Science in Korea
information Article Course Analysis of Library and Information Science in Korea Yelim Mo, Euntaek Seon, Goun Park and Haklae Kim * The Department of Library and Information Science, Chung-Ang University, 84 Heukseok-ro, Heukseok-dong, Dongjak-gu, Seoul 06974, Korea; [email protected] (Y.M.); [email protected] (E.S.); [email protected] (G.P.) * Correspondence: [email protected] Received: 23 October 2019; Accepted: 25 December 2019; Published: 27 December 2019 Abstract: Curriculums play a key role in implementing the educational goals and directions of a university. Universities regularly update their curriculums to actively respond to internal and external environmental changes. Korean universities face challenges, including a steady decline in enrollment and demand-oriented convergence education. Because of the nature of convergence science, library and information science should respond more actively to new challenges. This study analyzes the current status of library and information science courses according to subjects and universities. Data was collected from the websites of each university, and various methods such as text analysis, frequency analysis, and network analysis were applied to investigate current status of LIS in Korea. Keywords: library and information sciences; course; curriculum; data analysis 1. Introduction Library and information science (LIS) is the study of the theory and practice of processing, retrieving, collecting, distributing, using, manipulating, and accumulating information resources through a link with information technology (IT) [1]. In general, LIS consists of library science, which is the starting point of the study; bibliography, which focuses on the analysis and interpretation of books; records management, which focuses on the management and preservation of records; information science, which focuses on information access and processing; and knowledge organization, which is about document indexing and classification performed in libraries. -

The Effect of Life Satisfaction on the Silver Generation's Spa Recognition
Original Article J Cosmet Med 2020;4(1):17-22 https://doi.org/10.25056/JCM.2020.4.1.17 pISSN 2508-8831, eISSN 2586-0585 The effect of life satisfaction on the silver generation’s spa recognition and preferences Ga Hui Park, PhD1 , Eun-Ju Kang, PhD2 , Seung-Hee Seo, PhD2 1Department of Beauty Science, Gwangju University, Gwangju, Rep. of Korea, 2Department of Cosmetology, Dongshin University, Naju, Rep. of Korea Background: Although the spa industry is becoming increasingly popular as it is integrated and combined with the aesthetic, cosmetic, medical, food, apparel, and amusement park industries, research and development on spas for the silver generation is still lacking. Objective: The present study aimed to analyze satisfaction with life (SwL), spa perception, and spa program preferences of the silver generation with the objective of using the findings to develop spa programs that are actually needed by the growing elderly population, and provide basic data for the revitalization of the spa market. Methods: The study population consisted of people aged 60 years and older—also known as the silver generation—who were visitors at tourist sites in Damyang-gun, Jeollanam-do (South Korea). Results: The results showed that the silver generation’s self-esteem was highly correlated with their spa perception, while those with high SwL reported a high number of responses for “body massage/body treatment.” Regarding the appropriate cost of a single program, “Korean Won (KRW) 30,000–49,999” was the most common response among respondents with high SwL and “less than KRW 30,000” was the most common response among respondents with low SwL.