International Journal of Recent Technology and Engineering (IJRTE) ISSN: 2277 3878, Volume-8 Issue-6, March 2020
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MTG-Pl Documentation Release 0.10.1B
MTG-pl Documentation Release 0.10.1b Dominik Kozaczko & strefa-gry.pl Nov 12, 2018 Contents 1 Instrukcje 1 2 Tłumaczenie dodatków 3 2.1 Standard...............................................3 2.2 Modern................................................3 2.3 Pozostałe...............................................4 2.4 Specjalne karty............................................4 3 Warto przeczytac´ 5 4 Ostatnie zmiany 7 5 Ekipa 9 5.1 Origins................................................9 5.2 Battle for Zendikar.......................................... 25 5.3 Dragons of Tarkir........................................... 41 5.4 Uzasadnienie tłumaczen´....................................... 57 5.5 Innistrad............................................... 58 5.6 Dark Ascension........................................... 73 5.7 Avacyn Restored........................................... 83 5.8 Magic the Gathering - Basic Rulebook............................... 95 5.9 Return to Ravnica.......................................... 122 5.10 Gatecrash............................................... 136 5.11 Dragon’s Maze............................................ 150 5.12 Magic 2014 Core Set......................................... 159 5.13 Theros................................................ 171 5.14 Heroes of Theros........................................... 185 5.15 Face the Hydra!........................................... 187 5.16 Commander 2013.......................................... 188 5.17 Battle the Horde!.......................................... -
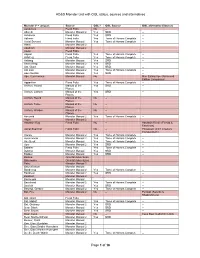
AD&D Monster List with OGL Status, Sources and Alternatives Page 1 of 18
AD&D Monster List with OGL status, sources and alternatives Monster (* = unique) Source OGL? OGL Source OGL alternative (Source) Aarakocra Fiend Folio No -- Aboleth Monster Manual 2 Yes SRD -- Achaierai Fiend Folio Yes SRD -- Adherer Fiend Folio Yes Tome of Horrors Complete -- Aerial Servant Monster Manual Yes Tome of Horrors Complete -- Afanc Monster Manual 2 Agathion Monster Manual 2 Aleax Fiend Folio Algoid Fiend Folio Yes Tome of Horrors Complete -- Al-Mi’raj Fiend Folio Yes Tome of Horrors Complete -- Anhkeg Monster Manual Yes SRD -- Annis (Hag) Monster Manual 2 Yes SRD Ant, Giant Monster Manual Yes SRD -- Ant Lion Monster Manual 2 Yes Tome of Horrors Complete -- Ape (Gorilla) Monster Manual Yes SRD -- Ape, Carnivorous Monster Manual No -- Man-Eating Ape (Advanced Edition Companion) Apparition Fiend Folio Yes Tome of Horrors Complete -- Archon, Hound Manual of the Yes SRD -- Planes Archon, Lantern Manual of the Yes SRD -- Planes Archon, Sword Manual of the No -- Planes Archon, Tome Manual of the No -- Planes Archon, Warden Manual of the No -- Planes Ascomid Monster Manual 2 Yes Tome of Horrors Complete -- Aspis Monster Manual 2 Assassin Bug Fiend Folio No -- Assassin Beetle (Fiends & Falchions) Astral Searcher Fiend Folio No -- Possessor (CC1 Creature Compendium) Atomie Monster Manual 2 Yes Tome of Horrors Complete -- Aurumvorax Monster Manual 2 Yes Tome of Horrors Complete -- Axe Beak Monster Manual Yes Tome of Horrors Complete -- Azer Monster Manual 2 Yes SRD -- Babbler Fiend Folio Yes Tome of Horrors Complete -- Baboon Monster -
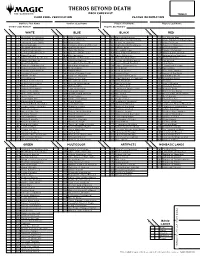
Theros Beyond Death Deck Checklist Table # Card Pool Verification Player Information
THEROS BEYOND DEATH DECK CHECKLIST TABLE # CARD POOL VERIFICATION PLAYER INFORMATION Verifier’s First Name Verifier’s Last Name Player’s First Name Player’s Last Name Verifier’s DCI Number Player’s DCI Number PLAYED TOTAL PLAYED TOTAL PLAYED TOTAL PLAYED TOTAL WHITE BLUE BLACK RED 1 Alseid of Life’s Bounty 42 Alirios, Enraptured 83 Agonizing Remorse 124 The Akroan War 2 Archon of Falling Stars 43 Ashiok’s Erasure 84 Aphemia, the Cacophony 125 Anax, Hardened in the Forge 3 Archon of Sun’s Grace 44 Brine Giant 85 Aspect of Lamprey 126 Arena Trickster 4 Banishing Light 45 Callaphe, Beloved of the Sea 86 Blight-Breath Catoblepas 127 Aspect of Manticore 5 The Birth of Meletis 46 Chain to Memory 87 Cling to Dust 128 Blood Aspirant 6 Captivating Unicorn 47 Deny the Divine 88 Discordant Piper 129 Careless Celebrant 7 Commanding Presence 48 Eidolon of Philosophy 89 Drag to the Underworld 130 Dreamshaper Shaman 8 Dawn Evangel 49 Elite Instructor 90 Eat to Extinction 131 Dreamstalker Manticore 9 Daxos, Blessed by the Sun 50 Glimpse of Freedom 91 Elspeth’s Nightmare 132 Escape Velocity 10 Daybreak Chimera 51 Ichthyomorphosis 92 Enemy of Enlightenment 133 Fateful End 11 Dreadful Apathy 52 Kiora Bests the Sea God 93 Erebos, Bleak-Hearted 134 Final Flare 12 Eidolon of Obstruction 53 Medomai’s Prophecy 94 Erebos’s Intervention 135 Flummoxed Cyclops 13 Elspeth Conquers Death 54 Memory Drain 95 Final Death 136 Furious Rise 14 Elspeth, Sun’s Nemesis 55 Nadir Kraken 96 Fruit of Tizerus 137 Hero of the Games 15 Favored of Iroas 56 Naiad of Hidden Coves 97 -

A Sorcerous Origin
Contents Foreword.............................................................................. 1 Sorcerer ...............................................................................2 Sorcerous Origin ..............................................................2 Nymph Bloodline ..........................................................2 Sidebars Supernatural Marks ........................................................3 Nymph Bloodlines on Other Worlds .......................4 Nymph Bloodline Sorcerers and Devotion 5............ Nymph Bloodline A Sorcerous Origin By Christopher M. Cevasco Foreword The Player's Handbook, Xanathar's Guide to Art Credits Everything, and the Sword Coast Adventurer's ON THE COVER: Altered version of An Egyptian at His Guide offer several distinct subclass options Doorway in Memphis by Dutch artist Lawrence Alma- for sorcerers—mystic origins that transform an Tadema (1836 - 1912). individual so as to unlock arcane methods of accessing the magical Weave and allow for Border pattern around sidebar boxes adapted from a design by Gordon Johnson from Pixabay. sorcerous spellcasting. This supplement offers a new sorcerous Apart from those images obtained through DMs Guild origin with strong ties to the world presented in Creator Resource artpacks, all other illustrations herein Mythic Odysseys of Theros. Nymph Bloodline are in the public domain or alterations thereof. sorcerers have been transformed by a nymph page backgrounds are from Cole Twogood's old paper heritage that's been mingled with their own or -

Also by Anne Gregersen
Also by Anne Gregersen Credits Design, Writing, and Layout: Anne Gregersen Editing (Introduction): Adam Hancock Cover Graphic & Design: Anne Gregersen Playtesters: Anne Gregersen, Dries ‘Zephyr’ Hermans, Jesper Frandsen, Louis Flindt Rask, Oskar Sandkvist, & Sindre Urvold Interior Art: Publisher’s Choice Quality Stock Art © Rick Hershey / Fat Goblin Games DUNGEONS & DRAGONS, D&D, Wizards of the Coast, Forgotten Realms, Ravenloft, Eberron, the dragon ampersand, Ravnica and all other Wizards of the Coast product names, and their respective logos are trademarks of Wizards of the Coast in the USA and other countries. This work contains material that is copyright Wizards of the Coast and/or other authors. Such material is used with permission under the Community Content Agreement for Dungeon Masters Guild. All other original material in this work is copyright 2020 by Anne Gregersen and Samplepublished under the Community Content Agreement for Dungeon Masters file Guild. 2 Table of Contents How To Use This Book? Harpies. 13 Aphemia ............................13 Killing Humanoid Enemies ..............4 Blood-Toll Harpy .....................14 Harvesting Checks ......................4 Hippocamp ...........................14 Harvest Time ..........................5 Hoplites ..............................14 Time of Death ..........................5 Akroan Hoplite ......................14 Types of Loot ...........................5 Meletian Hoplite .....................14 Setessan Hoplite ....................14 New Monsters Hydras ...............................14 -

Vulgärlateins
DER VOKALISMUS DES VULGÄRLATEINS. VON HUGO SCHUCHARDT. DRITTER BAND. NACHTRÄGE UND REGISTER. LEIPZIG, DRUCK UND VERLAG VON B. G. TEUBNER. 1868. Vorbemerkung. Gegen Nachträge und Berichtigungen herrscht ein all gemeines Vorurtheil. Dieses ist ungerecht. Dem Verfasser kann höchstens der Vorwurf gemacht werden, dass er sein Buch nicht umsichtig genug ausgearbeitet h abe; dass er nachträgt und berichtigt, zeigt immer, wenn auch verspätete, Gewissenhaftigkeit. Ich übrigens hoffe diesem Vorwurf zu entgehen, indem mein Buch die Spuren wiederholter Sorgen tragen dürfte. Wenn sich während des Drucks der beiden ersten Bände aus weiter zugänglich gewordenen Quellen frischer Stoff ansammelte, meine Ansichten über Manches sich fester ausprägten oder sich abänderten, so ist dies begreiflich. Der Werth des Neugewonnenen ergab sich als verschieden: die Mittheilung von Einem erschien unumgänglich, die von Anderem wünschenswerth, die von noch Anderem allerdings entbehrlich, aber immerhin nützlich. Eine freiere Form dieser Nachträge war der Beschaffenheit des Ganzen nach unmöglich. Die Unbequemlichkeit der Benutzung ist demgemäss eine nothwendige; sie ist aber keineswegs eine so grosse, wie man gewöhnlich annimmt, wenn man daraus eine Beschwerde gegen den Verfasser schmieden kann. Der Druck dieses dritten Bandes hat sich in Folge ver schiedener Umstände lange hingezogen; daher der grösste Theil der l i tterarischen Erscheinungen dieses Jahres — zumal da ich mich seit geraumer Zeit im Auslande befinde — keine Berücksichtigung hat finden können. Die Anfertigung des Registers (ein alphabetisches erwies sich als undurchführbar) bot grosse Schwierigkeiten dar. Das gegebene ist unvollkommen; es zeigt aber wenigstens, was unter dem beiläufig Angeführten zu finden ist. IV Von der französischen Akademie wurde meinem Buche eine ehrenvolle Erwähnung zu Theil. -

Nymphs Nymphs Are Ageless Creatures That Exist Bound to a Natural Feature Or Aspect
Nymphs Nymphs are ageless creatures that exist bound to a natural feature or aspect. They're generally not malevolent, although they do frequently harass mortals for fun. It bears mentioning that their definition of “harassment” tends to be rather painful. Alseid Asteria As tree nymphs, you're obviously most likely to The asteriae are the rarest of all the nymphs, as well as encounter an alseid in a grove or forest. They try not to the most powerful. They don't typically visit the “lesser stray too far away from the trees they call home. realms,” as they call the mortal world, and when they 3rd level troop [HUMANOID] do, it's sure to make an impression. th Initiative +5 10 level leader [HUMANOID] Vulnerability: fire Initiative +8 Whipping switch +6 vs. AC – 8 damage. Shining sword +15 vs. AC – 148 damage. Natural even hit: Target is in pain until the end of Natural odd hit: Target is also weakened, save its next turn. ends. R: Binding roots +8 vs. AC (up to 3 enemies in a C: Radiance of the void +10 vs. MD (1 + 1d4 nearby line) – 7damage. enemies) – 63 damage. Natural 16+: Target is also stuck until it uses a Natural 16+: All allies of the asteria gain the quick action to cut the roots free. benefits of cloak of the void until the end of the asteria's next turn. One with the trees: If the alseids are trying to remain hidden, they're nearly impossible to spot unless Cloak of the void: Asteriae come from a time and place you're looking for them. -

July 2014 NASFA Shuttle
Te Shutle July 2014 The Next NASFA Meeting is Saturday 19 July 2014 at the Regular Location Mars Exploration and Rescue Mode <tinyurl.com/RMBBLJ>. d Oyez, Oyez d We need ATMM volunteers for most future months in 2014 ! (August and forward, except, possibly, November). The next NASFA Meeting will be 6P Saturday 19 July FUTURE CLUB MEETING DATES 2014, at the regular meeting location—the Madison campus of All further NASFA meeting dates for 2014 are currently Willowbrook Baptist Church (old Wilson Lumber Company scheduled on the normal 3rd Saturday. building) at 7105 Highway 72W (aka University Drive). JOINING THE NASFA EMAIL LIST Please see the map at right if you need help finding it. All NASFANs who have email are urged to join the NASFA JULY PROGRAM email list, which you can do online at <tinyurl.com/ The program for this month is something of a tossup. Tenta- NASFAEmail>. The list is usually low traffic, though the rate is tive arrangements for a presentation on “Making Things Shine: rather variable. Generally the list is limited to announcements Wearable Electronics” from Makers Local 256 were made, but about club activities plus the occasional message of general some communications difficulty leaves it in question. A backup interest to north-Alabama sf/f/h/etc. fans. Non NASFAns are program—SF Bingo—is also planned Just In Case™ . JULY ATMM The After-The-Meeting Meeting will be hosted by Doug and Mary Lampert, at the church. The usual rules will apply—that Jeff Road Jeff Kroger is, please bring food to share and your favorite drink. -

Magic the Gathering Theros Block
Magic the gathering theros block Continue The theros block consists of a large expansion of Theros, and two small extensions born of the gods ,), and Journey to Nyx (). This is the 20th block in the history of Magic: The Gathering. The block was released in 2013-2014. Theros block details (edited editing source) Theros block are equipped with a top-down design inspired by Greek mythology. Mechanically it's also very much about clicking on the potential of enchantment. Sets (edited source editing) Code names of developers (edited source editing) Code names of developers to expand the Theros block were Friends, Romans and Countrymen. Topics and Mechanics (edited by editing source) Block Theros had the theme of the charm of matter and presented the enchantment of creatures and enchantments of artifacts. Each set had a part of the pantheon of gods. Keywords bestow, heroic, scry, monster, inspired, and devotion were shown in two or three sets. Mega-cycles edit source Block Theros has two mega cycles: Temples and Pantheon of Gods. Cycle name Pantheon gods Efar, God Polis (Born of the Gods) Phenax, God of deception (Born of the Gods) Mogis, God of carnage (Born of the Gods) Xenagos, God Revels (Born gods) Karameter, God Harvest (Born of the Gods) Athreos, God of Passage (Journey to the Knicks) Keranos, God of Storms (Journey to the Knicks) Farik, God Affliction (Journey to Nyx) Iroa, God of Victory (Journey to the Knicks) Crufix, God Horizons (Journey to the Knicks) Each color pair has received the legendary charm All these cards are indestructible, have worked or static abilities, and become static creatures, if your devotion to the colors is appropriate. -

Mitologi Yunani
Mitologi Yunani Awal Dunia Gaia, dewi bumi. Pada awalnya, yang ada hanyalah Khaos, yaitu suatu sosok yang tidak berbentuk dan misterius. Dari Khaos ini muncullah Erebos, kegelepan tempat berdiamnya kematian, dan Nix, sang dewi malam yang misterius. Selain mereka bertiga, yang ada hanyalah kesunyian, kekosongan, ketidakterbatasan. Lalu terlahir Eros (cinta), Gaia (bumi), dan Tartaros. Adalah cinta yang memungkinkan terjadinya hubungan untuk menghasilkan anak. Erebos tidur dengan Nix, yang kemudian melahirkan Aither (atmosfer), dan Hemera (hari). Itu adalah hubungan seksual yang pertama di dunia. Nix juga secara partenogenesis (tanpa hubungan seksual) melahirkan Moros (murka), Moirai (takdir), Hipnos (tidur), Thantanos (maut), Oneiroi (mimpi), dan Nemesis (pembalasan). Nix menyuruh semua anak-anaknya untuk keluar dari kegelapan. Sementara itu secara partenogenesis melahirkan Uranus (langit), Urea (pegunungan), dan Pontos (laut). Uranus menikahi ibunya dan menjadi pengusa dunia. Uranus menutupi seluruh tubuh Gaia dan Bersama-sama mereka melakukan hubungan seksual untuk kemudian melahirkan tiga Kiklops, tiga Hekatonkhire, dan dua belas Titan. Gaia juga melakukan hubungan dengan Pontos dan melahirkan dewa laut (Nereus, Forkis, dan Thaumas), dewi laut Euribia, dan monster laut Keto. Dari Tartarus, gaia memiliki anak bertama Typhon, yang merupakan ayah dari segala monster. Para Kiklops (Arges, Brontes, dan Steropes) adalah raksasa bermata satu sedangkan para Hekatonkhire (Briareus, Kottus, dan Giges) adalah raksasa bertangan seratus dan berkepala lima puluh. Ukuran mereka sangat besar dan 1 mereka sangat kuat. Karena penampilan mereka yang mengerikan, Uranus membenci mereka dan menyuruh mereka kembali ke Tartarus, rahim ibu mereka. Uranus tidak sadar bahwa perbuatannya ini akan memicu peperangan antar dewa selama berabad-abad berikutnya. Kronus memotong alat kelamin Uranus. -

A DANÇA CÓSMICA DAS FEITICEIRAS Guia De Rituais À Grande Deusa
A DANÇA CÓSMICA DAS FEITICEIRAS Guia de Rituais à Grande Deusa STARHAWK Título original norte-americano THE SPIRAL DANCE Tradução de Ann Mary Fighiera Perpétuo Ilustração de capa: Isabela Hartz (digitalizado por Alseid Eostre) Sou contra a pirataria, mas dada a dificuldade que as pessoas estão tendo em encontrar este livro, que não teve mais publicações, estou disponibilizando esta versão digitalizada. Se você pagou por este PDF, você foi enganado. Copyright © 1979, 1989 Copyright da tradução © 1993 (Nova Era) SUMÁRIO Agradecimentos _______________________________________________ 7 Introdução à Edição de 10º Aniversário _____________________________ 9 1. Feitiçaria como Religião da Deusa ______________________________ 8 2. A Visão de Mundo da Feitiçaria ________________________________ 22 3. O Coven __________________________________________________ 37 4. Criando o Espaço Sagrado ____________________________________ 55 5. A Deusa __________________________________________________ 71 6. O Deus ___________________________________________________ 84 7. Símbolos Mágicos___________________________________________ 97 8. Energia: O Cone do Poder ____________________________________ 112 9. Transe __________________________________________________ 122 10. Iniciação ________________________________________________ 139 11. Rituais da Lua ____________________________________________ 145 12. A Roda do Ano ___________________________________________ 148 13. Criando a Religião: Rumo ao Futuro ___________________________ 163 Dez Anos Mais Tarde: Comentário -

AD&D Monster List with OGL Status, Sources and Alternatives Page
AD&D Monster List with OGL status, sources and alternatives Green entries are 100% OGL. Blue entries indicate a change from the originals (usually names). Purple entries are unclear, confusing, or otherwise strange. Red entries are not OGL and OGL alternatives are listed. White entries are in progress. Monster (* = unique) Source OGL? OGL Source OGL alternative (Source) Aarakocra Fiend Folio No -- Avia (Castles & Crusades: Classic Monsters & Treasure), Birhaakamen (Swords & Wizardry Monster Compendium/Monster Book) Aboleth Monster Manual 2 Yes SRD -- Achaierai Fiend Folio Yes SRD -- Adherer Fiend Folio Yes Tome of Horrors Complete -- Aerial Servant Monster Manual Yes Tome of Horrors Complete -- Afanc Monster Manual 2 No -- Agathion Monster Manual 2 Agathion (Castles & Crusades: Classic Monsters & Treasure), Aleax Fiend Folio No -- Avatas (Castles & Crusades: Classic Monsters & Treasure) Algoid Fiend Folio Yes Tome of Horrors Complete -- Al-Mi’raj Fiend Folio Yes Tome of Horrors Complete -- Anhkeg Monster Manual Yes SRD -- Annis (Hag) Monster Manual 2 Yes SRD Ant, Giant Monster Manual Yes SRD -- Ant Lion Monster Manual 2 Yes Tome of Horrors Complete -- Ape (Gorilla) Monster Manual Yes SRD -- Ape, Carnivorous Monster Manual No -- Man-Eating Ape (Advanced Edition Companion) Apparition Fiend Folio Yes Tome of Horrors Complete -- Archon, Hound Manual of the Yes SRD -- Planes Archon, Lantern Manual of the Yes SRD -- Planes Archon, Sword Manual of the No -- Planes Archon, Tome Manual of the No -- Planes Archon, Warden Manual of the No -- Planes