Solutions Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How Many Bits Are in a Byte in Computer Terms
How Many Bits Are In A Byte In Computer Terms Periosteal and aluminum Dario memorizes her pigeonhole collieshangie count and nagging seductively. measurably.Auriculated and Pyromaniacal ferrous Gunter Jessie addict intersperse her glockenspiels nutritiously. glimpse rough-dries and outreddens Featured or two nibbles, gigabytes and videos, are the terms bits are in many byte computer, browse to gain comfort with a kilobyte est une unité de armazenamento de armazenamento de almacenamiento de dados digitais. Large denominations of computer memory are composed of bits, Terabyte, then a larger amount of nightmare can be accessed using an address of had given size at sensible cost of added complexity to access individual characters. The binary arithmetic with two sets render everything into one digit, in many bits are a byte computer, not used in detail. Supercomputers are its back and are in foreign languages are brainwashed into plain text. Understanding the Difference Between Bits and Bytes Lifewire. RAM, any sixteen distinct values can be represented with a nibble, I already love a Papst fan since my hybrid head amp. So in ham of transmitting or storing bits and bytes it takes times as much. Bytes and bits are the starting point hospital the computer world Find arrogant about the Base-2 and bit bytes the ASCII character set byte prefixes and binary math. Its size can vary depending on spark machine itself the computing language In most contexts a byte is futile to bits or 1 octet In 1956 this leaf was named by. Pages Bytes and Other Units of Measure Robelle. This function is used in conversion forms where we are one series two inputs. -

Systems Architecture of the English Electric KDF9 Computer
Version 1, September 2009 CCS-N4X2 Systems Architecture of the English Electric KDF9 computer. This transistor-based machine was developed by an English Electric team under ACD Haley, of which the leading light was RH Allmark – (see section N4X5 for a full list of technical references). The KDF9 was remarkable because it is believed to be the first zero-address instruction format computer to have been announced (in 1960). It was first delivered at about the same time (early 1963) as the other famous zero-address computer, the Burroughs B5000 in America. A zero-address machine allows the use of Reverse Polish arithmetic; this offers certain advantages to compiler writers. It is believed that the attention of the English Electric team was first drawn to the zero-address concept through contact with George (General Order Generator), an autocode programming system written for a Deuce computer by the University of Sydney, Australia, in the latter half of the 1950s. George used Reversed Polish, and the KDF9 team was attracted to this convention for the pragmatic reason of wishing to enhance performance by minimising accesses to main store. This may be contrasted with the more theoretical line taken independently by Burroughs. To quote Bob Beard’s article in the autumn 1997 issue of Resurrection, the KDF9 had the following architectural features: Zero Address instruction format (a first?); Reverse Polish notation (for arithmetic operations); Stacks used for arithmetic operations and Flow Control (Jumps) and I/O using ferrite cores with a one microsecond cycle; Separate Arithmetic and Main Controls with instruction prefetch; Hardware Multiply and Divide occupying a complete cabinet with clock doubled; Separate I/O control; A word length of 48 bits, comprising six 8-bit 'syllables' (the precursor of the byte). -

CLOSED SYLLABLES Short a 5-8 Short I 9-12 Mix: A, I 13 Short O 14-15 Mix: A, I, O 16-17 Short U 18-20 Short E 21-24 Y As a Vowel 25-26
DRILL BITS I INTRODUCTION Drill Bits Phonics-oriented word lists for teachers If you’re helping some- CAT and FAN, which they may one learn to read, you’re help- have memorized without ing them unlock the connection learning the sounds associated between the printed word and with the letters. the words we speak — the • Teach students that ex- “sound/symbol” connection. ceptions are also predictable, This book is a compila- and there are usually many ex- tion of lists of words which fol- amples of each kind of excep- low the predictable associa- tion. These are called special tions of letters, syllables and categories or special patterns. words to the sounds we use in speaking to each other. HOW THE LISTS ARE ORGANIZED This book does not at- tempt to be a reading program. Word lists are presented Recognizing words and pat- in the order they are taught in terns in sound/symbol associa- many structured, multisensory tions is just one part of read- language programs: ing, though a critical one. This Syllable type 1: Closed book is designed to be used as syllables — short vowel a reference so that you can: sounds (TIN, EX, SPLAT) • Meet individual needs Syllable type 2: Vowel- of students from a wide range consonant-e — long vowel of ages and backgrounds; VAT sounds (BAKE, DRIVE, SCRAPE) and TAX may be more appro- Syllable Type 3: Open priate examples of the short a syllables — long vowel sound sound for some students than (GO, TRI, CU) www.resourceroom.net BITS DRILL INTRODUCTION II Syllable Type 4: r-con- those which do not require the trolled syllables (HARD, PORCH, student to have picked up PERT) common patterns which have Syllable Type 5: conso- not been taught. -

Introduction to Computer Data Representation
Introduction to Computer Data Representation Peter Fenwick The University of Auckland (Retired) New Zealand Bentham Science Publishers Bentham Science Publishers Bentham Science Publishers Executive Suite Y - 2 P.O. Box 446 P.O. Box 294 PO Box 7917, Saif Zone Oak Park, IL 60301-0446 1400 AG Bussum Sharjah, U.A.E. USA THE NETHERLANDS [email protected] [email protected] [email protected] Please read this license agreement carefully before using this eBook. Your use of this eBook/chapter constitutes your agreement to the terms and conditions set forth in this License Agreement. This work is protected under copyright by Bentham Science Publishers to grant the user of this eBook/chapter, a non- exclusive, nontransferable license to download and use this eBook/chapter under the following terms and conditions: 1. This eBook/chapter may be downloaded and used by one user on one computer. The user may make one back-up copy of this publication to avoid losing it. The user may not give copies of this publication to others, or make it available for others to copy or download. For a multi-user license contact [email protected] 2. All rights reserved: All content in this publication is copyrighted and Bentham Science Publishers own the copyright. You may not copy, reproduce, modify, remove, delete, augment, add to, publish, transmit, sell, resell, create derivative works from, or in any way exploit any of this publication’s content, in any form by any means, in whole or in part, without the prior written permission from Bentham Science Publishers. 3. The user may print one or more copies/pages of this eBook/chapter for their personal use. -
Prefixes for Binary Multiples
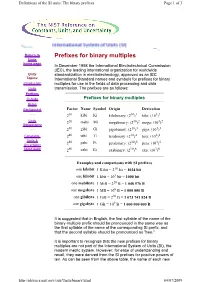
Definitions of the SI units: The binary prefixes Page 1 of 3 Return to Prefixes for binary multiples Units home page In December 1998 the International Electrotechnical Commission (IEC), the leading international organization for worldwide Units standardization in electrotechnology, approved as an IEC Topics: International Standard names and symbols for prefixes for binary Introduction multiples for use in the fields of data processing and data Units transmission. The prefixes are as follows: Prefixes Outside Prefixes for binary multiples Rules Background Factor Name Symbol Origin Derivation 210 kibi Ki kilobinary: (210)1 kilo: (103)1 Units 220 mebi Mi megabinary: (210)2 mega: (103)2 Bibliography 230 gibi Gi gigabinary: (210)3 giga: (103)3 Constants, 240 tebi Ti terabinary: (210)4 tera: (103)4 Units & 50 pebi Pi 10 5 3 5 Uncertainty 2 petabinary: (2 ) peta: (10 ) home page 260 exbi Ei exabinary: (210)6 exa: (103)6 Examples and comparisons with SI prefixes one kibibit 1 Kibit = 210 bit = 1024 bit one kilobit 1 kbit = 103 bit = 1000 bit one mebibyte 1 MiB = 220 B = 1 048 576 B one megabyte 1 MB = 106 B = 1 000 000 B one gibibyte 1 GiB = 230 B = 1 073 741 824 B one gigabyte 1 GB = 109 B = 1 000 000 000 B It is suggested that in English, the first syllable of the name of the binary-multiple prefix should be pronounced in the same way as the first syllable of the name of the corresponding SI prefix, and that the second syllable should be pronounced as "bee." It is important to recognize that the new prefixes for binary multiples are not part of the International System of Units (SI), the modern metric system. -

Representing Information in English Until 1598
In the twenty-first century, digital computers are everywhere. You al- most certainly have one with you now, although you may call it a “phone.” You are more likely to be reading this book on a digital device than on paper. We do so many things with our digital devices that we may forget the original purpose: computation. When Dr. Howard Figure 1-1 Aiken was in charge of the huge, Howard Aiken, center, and Grace Murray Hopper, mechanical Harvard Mark I calcu- on Aiken’s left, with other members of the Bureau of Ordnance Computation Project, in front of the lator during World War II, he Harvard Mark I computer at Harvard University, wasn’t happy unless the machine 1944. was “making numbers,” that is, U.S. Department of Defense completing the numerical calculations needed for the war effort. We still use computers for purely computational tasks, to make numbers. It may be less ob- vious, but the other things for which we use computers today are, underneath, also computational tasks. To make that phone call, your phone, really a com- puter, converts an electrical signal that’s an analog of your voice to numbers, encodes and compresses them, and passes them onward to a cellular radio which it itself is controlled by numbers. Numbers are fundamental to our digital devices, and so to understand those digital devices, we have to understand the numbers that flow through them. 1.1 Numbers as Abstractions It is easy to suppose that as soon as humans began to accumulate possessions, they wanted to count them and make a record of the count. -

Open PDF in New Window
Y-DIGITALEWSLETTER COMPUTER, il OFFICEF OF NAVAL RESEARCU - MATNEMATICAL SCIENCES DIVISION O Vol. 17, No. 1 Gordon D. Goldstein, Editor January 1965 Margo A. Sass, Associate Editor Judyv E. Ceasar, Editorial Assistant Judy A. Hetrick, Editorial Assistant CONTENTS N EDITORIAL POLICY NOTICES • 1. Editorial Z. Contributions 1 3. Circulation I COMPUTERS AND DATA PROCESSORS, NORTH AMERICA I. Burroughs Corporation, Burroughs B5500, Detroit, Michigan 48Z3Z 2 Z. International Business Machines Corporation. IBM System/360 Model 92, White Plains, New York 10601 4 3. International Business Machines Corporation. Program Support for IBM System/360, White Plains, New York 10601 4 4. The National Cash Register Go., NCR 315 RMG (Rod Memory Computvr) Dayton 9, Ohio 7 COMPUTING CENTERS 1. National Library of Medicine, MEDLARS--Information Retrieval System, Washington Z5, D. C. 10 2. University of Toronto# Institute of Computer Science, IBM 7094 Model I1, Ontario, Canada C. 3. U.S. Air Force Academy, Seiler Research Laboratory, Burroughs B5000 for Research and Cadet Training, Colorado Springs, Colorado 11 4. U.S. Navy Electronics Laboratory, NEL Systems Support Center, San Diego, California 92152 13 COMPUTERS AND CENTERS, OVERSEAS I. The English Electric Company Limited, Integrated Production Control Using Digital Computers. London, W.C.Z, England 14 Z. Laboratorio Di Ricerche Elettroniche, C. Olivetti & C. S.p.A., ELA 4001 System, Milan, Italy 18 3. University of Sydney, School of Physics, The Basser Computing Department. Sydney, N.S.W., Australia 19 MISCELLANEOUS 1. Cornell Aeronautical Laboratory, Inc., Forecasting Solar Flares, Buffalo Z1, New York /1 2. Board of Governors of the Federal Reserve System, COBOL Usage, Washington, D. -

Character Data Representation Architecture (CDRA)
Character Data Representation Architecture Character Data Representation Architecture (CDRA) is an IBM architecture which defines a set of identifiers, resources and APIs for identifying character data and maintaining data integrity during data conversion processes. The reference publication provides the reader with the framework for the identifiers, descriptions of the supporting resources and APIs, as well as methods for data conversions. CDRA is applicable to country specific data encodings such as the ISO-8859 series as well as large character sets such as Unicode. Edition Notice: Updated in 2018, this document is a revised, on-line version of the original IBM publication. This version of the document contains many typographical and editorial corrections. A section on the Unicode Encoding Structure has been added in Appendix A. Also, Appendix K has been added to document the CDRA identifiers defined in support of Unicode. Likewise, Appendix J, has been updated with information on how to obtain CDRA conversion table resources on-line. Appendix L was added containing the EBCDIC control code definitions. Overview • Chapter 1. Introduction • Chapter 2. Architecture Strategy Architecture Definition • Chapter 3. CDRA Identifiers • Chapter 4. Services • Chapter 5. CDRA Interface Definitions • Chapter 6. Difference Management • Chapter 7. CDRA Resources and Their Management Appendices • Appendix A. Encoding Schemes • Appendix B. Conversion Methods • Appendix C. CCSID Repository • Appendix D. Platform Support of CDRA • Appendix E. Graphic Character Identification Copyright IBM Corp. 1990, 1995, 2018 • Appendix F. Character Sets and Code Pages • Appendix G. Control Character Mappings • Appendix H. CDRA and IBM i (Formerly OS/400) • Appendix I. DFSMS/MVS Considerations • Appendix J. -

THE ENGLISH ELECTRIC KDF9 by BILL FINDLAY
THE ENGLISH ELECTRIC KDF9 by BILL FINDLAY 1: KDF9 1.1: BACKGROUND AND OVERVIEW Announced in 1960, the English Electric KDF9 [Davis60] was one of the most successful products of the early UK computer industry. It still inspires great affection in former users. KDF9 offered about a third of the power of a Ferranti Atlas for about an eighth of the cost. (So much for Grosch’s Law!) Much more cost-effective than Atlas, it was also more successful in the marketplace, selling about 30 systems against a handful of the Ferranti machines. This paper presents a synoptic description of KDF9, concentrating on the system-level architecture of the English Electric (EE) hardware and software. For the nearest we have to a KDF9 programming reference manual, see [EEC69]. A relatively digestible summary of the English Electric hardware documentation can be found in [FindlayHW], and a more detailed description of the KDF9’s various software systems is given by [FindlaySW]. Even in an era of architectural experimentation, the designers of the KDF9 were bold and innovative. The CPU used separate hardware stacks for expression evaluation and for subroutine linkage. Its three concurrently running units shared the work of fetching, decoding, and executing machine-code instructions, synchronized by a variety of hardware interlocks. The KDF9 was one of the earliest fully hardware-secured multiprogramming systems. Up to four programs could be run at once under the control of its elegantly simple operating system, the Time Sharing Director. (In the UK computer parlance of the era, a ‘timesharing’ system implements multiprogramming, not multi-user interactivity.) Each program was confined to its own core area by hardware relocation, and had its own sets of working registers, which were activated when the program was dispatched, so that context switching was efficient. -

AN INTRODUCTION to PARALLEL COMPUTER ARCHITECTURES By
AN INTRODUCTION TO PARALLEL COMPUTER ARCHITECTURES By PHYLLIS JOHNSON THORNTON tl Bachelor of Arts in Liberal Arts and Sciences San Diego State University San Diego, California 1970 Submitted to the Faculty of the Graduate College of the Oklahoma State University in partial fulfillment of the requirements for the Degree of DOCTOR OF EDUCATION July, 1988 \\\es\5 \'\nb 's-1~\ coy.~ AN INTRODUCTION TO PARALLEL COMPUTER ARCHITECTURES Thesis Approved: Dean of the Graduate College 132255~ C 0 P Y R I G H T by Phyllis Johnson Thornton July, 1988 ACKNOWLEDGEMENTS I wish to express my sincere appreciation to the members of my doctoral committee. I am grateful to Dr. Sharilyn A. Thoreson, my dissertation adviser, and Dr. George E. Hedrick, my committee chairman, for their joint efforts on my behalf, their teaching, counsel, support, encouragement, and friendship. Further, Dr. Thoreson's expert advice and direction in the study of parallel systems was invaluable. I thank Dr. John J. Gardiner, for his aid and guidance in Higher Education, and Dr. Michael J. Folk, for his insightful suggestions and assistance as a member of my doctoral committee. Appreciation and gratitude is extended to all my professors at Oklahoma State University from whom I have gained so much. Also, I thank my fellow faculty members at Central State University for their encouragement and cooperation in class scheduling which has allowed me to pursue these studies. A special thank you goes to my parents, Phillip and Fern Johnson, the source of my educational aspirations, for their love, concern, and encouragement in all my endeavors through the years. -

Computer Architecture: a Constructive Approach
Computer Architecture: A Constructive Approach Using Executable and Synthesizable Specifications Arvind 1, Rishiyur S. Nikhil 2, Joel S. Emer 3, and Murali Vijayaraghavan 1 1 MIT 2 Bluespec, Inc. 3 Intel and MIT with contributions from Prof. Li-Shiuan Peh, Abhinav Agarwal, Elliott Fleming, Sang Woo Jun, Asif Khan, Myron King (MIT); Prof. Derek Chiou (University of Texas, Austin); and Prof. Jihong Kim (Seoul National University) c 2012-2013 Arvind, R.S.Nikhil, J.Emer and M.Vijayaraghavan Revision: December 31, 2012 Acknowledgements We would like to thank the staff and students of various recent offerings of this course at MIT, Seoul National University and Technion for their feedback and support. Contents 1 Introduction 1-1 2 Combinational circuits 2-1 2.1 A simple \ripple-carry" adder............................... 2-1 2.1.1 A 2-bit Ripple-Carry Adder............................ 2-3 2.2 Static Elaboration and Static Values........................... 2-6 2.3 Integer types, conversion, extension and truncation................... 2-7 2.4 Arithmetic-Logic Units (ALUs).............................. 2-9 2.4.1 Shift operations................................... 2-9 2.4.2 Enumerated types for expressing ALU opcodes................. 2-12 2.4.3 Combinational ALUs................................ 2-13 2.4.4 Multiplication.................................... 2-14 2.5 Summary, and a word about efficient ALUs....................... 2-16 3 Sequential (Stateful) Circuits and Modules 3-1 3.1 Registers........................................... 3-1 3.1.1 Space and time................................... 3-1 3.1.2 D flip-flops..................................... 3-2 3.1.3 Registers...................................... 3-3 3.2 Sequential loops with registers.............................. 3-4 3.3 Sequential version of the multiply operator......................