Homeland Security: Defending U.S. Airspace
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Voyeurisme, Intimitet Og Paranoia I Tv-Serien Homeland
Politik Nummer 1 | Årgang 20 | 2017 Drone-dronningen: Voyeurisme, intimitet og paranoia i tv-serien Homeland Andreas Immanuel Graae, Ph.d.-stipendiat, Litteraturvidenskab, Syddansk Universitet Kamikazepiloten: Min krop er et våben. Dronen: Mit våben har ingen krop.” - Chamayou 2015, 84 I hovedværket A Theory of the Drone (2015) trækker den franske filosof Grégoire Chamayou linjerne hårdt op mellem to typer krigere: Selvmordsbomberen og dronepiloten. Hvor selvmordsbomberen, herunder kamikazepiloten, med sin handling foretager den ultimative ofring af egen krop, markerer dronepiloten omvendt et totalt fravær af krop i kampzonen; de repræsenterer to politiske og affektive logikker, der ofte modstilles i den akademiske dronedebat såvel som i populærkulturelle repræsentationer af dronekrig.1 Opfattelsen af dronekrig som en grundlæggende kropsløs og virtuel affære understøttes af udbredte forestillinger og fordomme om droneoperationer som ren simulation eller ligefrem et computerspil, der producerer en ’PlayStation-mentalitet’ blandt piloterne (Chamayou 2015, 107; Gregory 2014, 9). Der skal ikke herske tvivl om, at de senere årtiers teknologiske fremskridt har øget militærindustriens interesse for simulationer, computergenerede modeller, netværk og algoritmer (Derian 2009). Men selvom skærmkrigerens manglende kropslige involvering i begivenhederne på slagmarken kan stilles op over for selvmordsbomberens ultimative kropslige offer, betyder det ikke nødvendigvis, at følelsesmæssig indlevelse og erfaring er totalt fraværende i dronekrig. Tværtimod tyder talrige rapporter om psykiske nedbrud og PTSD-diagnoser blandt dronepiloterne på væsentlig mental fordybelse og emotionel indlevelsesevne (Chamayou 2015, 106). 1 For eksempel tegner poprock-gruppen Muse i albummet Drones (2015) et dehumaniseret billede af dronekrig, hvor der er ”no recourse, and there is no one behind the wheel,” som det hedder på tracket ‘Reapers.’ 62 Politik Nummer 1 | Årgang 20 | 2017 Adskillige nyere film og tv-serier adresserer denne problematik i deres repræsentationer af dronekrig. -

Threnody Amy Fitzgerald Macalester College, [email protected]
Macalester College DigitalCommons@Macalester College English Honors Projects English Department 2012 Threnody Amy Fitzgerald Macalester College, [email protected] Follow this and additional works at: http://digitalcommons.macalester.edu/english_honors Part of the English Language and Literature Commons Recommended Citation Fitzgerald, Amy, "Threnody" (2012). English Honors Projects. Paper 21. http://digitalcommons.macalester.edu/english_honors/21 This Honors Project - Open Access is brought to you for free and open access by the English Department at DigitalCommons@Macalester College. It has been accepted for inclusion in English Honors Projects by an authorized administrator of DigitalCommons@Macalester College. For more information, please contact [email protected]. Threnody By Amy Fitzgerald English Department Honors Project, May 2012 Advisor: Peter Bognanni 1 Glossary of Words, Terms, and Institutions Commissie voor Oorlogspleegkinderen : Commission for War Foster Children; formed after World War II to relocate war orphans in the Netherlands, most of whom were Jewish (Dutch) Crèche : nursery (French origin) Fraulein : Miss (German) Hervormde Kweekschool : Reformed (religion) teacher’s training college Hollandsche Shouwberg : Dutch Theater Huppah : Jewish wedding canopy Kaddish : multipurpose Jewish prayer with several versions, including the Mourners’ Kaddish KP (full name Knokploeg): Assault Group, a Dutch resistance organization LO (full name Landelijke Organasatie voor Hulp aan Onderduikers): National Organization -

An Analysis of Palestinian and Native American Literature
INDIGENOUS CONTINUANCE THROUGH HOMELAND: AN ANALYSIS OF PALESTINIAN AND NATIVE AMERICAN LITERATURE ________________________________________ A Thesis Presented to The Honors Tutorial College Ohio University ________________________________________ In Partial Fulfillment of the Requirements for Graduation from the Honors Tutorial College with the degree of Bachelor of Arts in English ________________________________________ by Alana E. Dakin June 2012 Dakin 2 This thesis has been approved by The Honors Tutorial College and the Department of English ____________________ Dr. George Hartley Professor, English Thesis Advisor ____________________ Dr. Carey Snyder Honors Tutorial College, Director of Studies English ____________________ Dr. Jeremy Webster Dean, Honors Tutorial College Dakin 3 CHAPTER ONE Land is more than just the ground on which we stand. Land is what provides us with the plants and animals that give us sustenance, the resources to build our shelters, and a place to rest our heads at night. It is the source of the most sublime beauty and the most complete destruction. Land is more than just dirt and rock; it is a part of the cycle of life and death that is at the very core of the cultures and beliefs of human civilizations across the centuries. As human beings began to navigate the surface of the earth thousands of years ago they learned the nuances of the land and the creatures that inhabited it, and they began to relate this knowledge to their fellow man. At the beginning this knowledge may have been transmitted as a simple sound or gesture: a cry of warning or an eager nod of the head. But as time went on, humans began to string together these sounds and bits of knowledge into words, and then into story, and sometimes into song. -

Civil Defense and Homeland Security: a Short History of National Preparedness Efforts
Civil Defense and Homeland Security: A Short History of National Preparedness Efforts September 2006 Homeland Security National Preparedness Task Force 1 Civil Defense and Homeland Security: A Short History of National Preparedness Efforts September 2006 Homeland Security National Preparedness Task Force 2 ABOUT THIS REPORT This report is the result of a requirement by the Director of the Department of Homeland Security’s National Preparedness Task Force to examine the history of national preparedness efforts in the United States. The report provides a concise and accessible historical overview of U.S. national preparedness efforts since World War I, identifying and analyzing key policy efforts, drivers of change, and lessons learned. While the report provides much critical information, it is not meant to be a substitute for more comprehensive historical and analytical treatments. It is hoped that the report will be an informative and useful resource for policymakers, those individuals interested in the history of what is today known as homeland security, and homeland security stakeholders responsible for the development and implementation of effective national preparedness policies and programs. 3 Introduction the Nation’s diverse communities, be carefully planned, capable of quickly providing From the air raid warning and plane spotting pertinent information to the populace about activities of the Office of Civil Defense in the imminent threats, and able to convey risk 1940s, to the Duck and Cover film strips and without creating unnecessary alarm. backyard shelters of the 1950s, to today’s all- hazards preparedness programs led by the The following narrative identifies some of the Department of Homeland Security, Federal key trends, drivers of change, and lessons strategies to enhance the nation’s learned in the history of U.S. -

As She Knows It
BY VICKI GLEMBOCKI ’93, ’02 MFA LIB THE END OF THE WORLD as she knows it When it comes to surviving a zombie apocalypse, GILLIAN ALBINSKI knows firsthand what to eat, how to make weapons, what to do with undead blood, and how to make anything out of tinfoil. They’re useful skills—both for staying alive at the end of days, and for being the prop master on one of the most-watched shows on TV, The Walking Dead. TK TK PENNPENN STATER STATER MAGAZINE MAGAZINE 47 THE END OF THE WORLD STARSTRUCK A fan of TWD since it debuted in 2010, Albinski says she arrived on set last August and “I suddenly got all giggly fan-girl.” mist, in real time, dressing a deer that a client had brought in. And there was IT WAS CLOSE TO MIDNIGHT lots of blood. Albinski, 48, jumped up, tossed her when Gillian Albinski pulled down the deserted, supplies in her van, and headed to the shop, an hour-and-a-half drive from tree-lined road that led to Senoia, a small town just Senoia where TWD is filmed, praying she’d get there before the blood coag- south of Atlanta. In the back of her minivan, she ulated. She figured she’d set up her experiment in the parking lot: pour the had several two-by-fours, a butane lighter, a bucket, blood in the bucket, dip in the wood, light it on fire, repeat and repeat and and a sealed Rubbermaid pitcher filled with deer blood. wrapped in barbed wire that’s the weapon of choice of repeat, and take tons of photos. -

A Governor's Guide to Homeland Security
A GOVERNOR’S GUIDE TO HOMELAND SECURITY THE NATIONAL GOVERNORS ASSOCIATION (NGA), founded in 1908, is the instrument through which the nation’s governors collectively influence the development and implementation of national policy and apply creative leadership to state issues. Its members are the governors of the 50 states, three territories and two commonwealths. The NGA Center for Best Practices is the nation’s only dedicated consulting firm for governors and their key policy staff. The NGA Center’s mission is to develop and implement innovative solutions to public policy challenges. Through the staff of the NGA Center, governors and their policy advisors can: • Quickly learn about what works, what doesn’t and what lessons can be learned from other governors grappling with the same problems; • Obtain specialized assistance in designing and implementing new programs or improving the effectiveness of current programs; • Receive up-to-date, comprehensive information about what is happening in other state capitals and in Washington, D.C., so governors are aware of cutting-edge policies; and • Learn about emerging national trends and their implications for states, so governors can prepare to meet future demands. For more information about NGA and the Center for Best Practices, please visit www.nga.org. A GOVERNOR’S GUIDE TO HOMELAND SECURITY NGA Center for Best Practices Homeland Security & Public Safety Division FEBRUARY 2019 Acknowledgements A Governor’s Guide to Homeland Security was produced by the Homeland Security & Public Safety Division of the National Governors Association Center for Best Practices (NGA Center) including Maggie Brunner, Reza Zomorrodian, David Forscey, Michael Garcia, Mary Catherine Ott, and Jeff McLeod. -
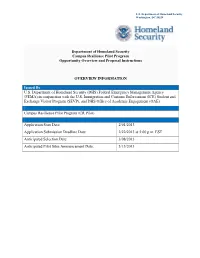
CR Pilot Program Announcement
U.S. Department of Homeland Security Washington, DC 20528 Department of Homeland Security Campus Resilience Pilot Program Opportunity Overview and Proposal Instructions OVERVIEW INFORMATION Issued By U.S. Department of Homeland Security (DHS) Federal Emergency Management Agency (FEMA) in conjunction with the U.S. Immigration and Customs Enforcement (ICE) Student and Exchange Visitor Program (SEVP), and DHS Office of Academic Engagement (OAE). Opportunity Announcement Title Campus Resilience Pilot Program (CR Pilot) Key Dates and Time Application Start Date: 2/01/2013 Application Submission Deadline Date: 2/22/2013 at 5:00 p.m. EST Anticipated Selection Date: 3/08/2013 Anticipated Pilot Sites Announcement Date: 3/15/2013 DHS CAMPUS RESILIENCE PILOT PROGRAM PROPOSAL SUBMISSION PROCESS & ELIGIBILITY Opportunity Category Select the applicable opportunity category: Discretionary Mandatory Competitive Non-competitive Sole Source (Requires Awarding Office Pre-Approval and Explanation) CR Pilot sites will be selected based on evaluation criteria described in Section V. Proposal Submission Process Completed proposals should be emailed to [email protected] by 5:00 p.m. EST on Friday, February 22, 2013. Only electronic submissions will be accepted. Please reference “Campus Resilience Pilot Program” in the subject line. The file size limit is 5MB. Please submit in Adobe Acrobat or Microsoft Word formats. An email acknowledgement of received submission will be sent upon receipt. Eligible Applicants The following entities are eligible to apply for participation in the CR Pilot: • Not-for-profit accredited public and state controlled institutions of higher education • Not-for-profit accredited private institutions of higher education Additional information should be provided under Full Announcement, Section III, Eligibility Criteria. -

Texas Homeland Security Strategic Plan 2021-2025
TEXAS HOMELAND SECURITY STRATEGIC PLAN 2021-2025 LETTER FROM THE GOVERNOR Fellow Texans: Over the past five years, we have experienced a wide range of homeland security threats and hazards, from a global pandemic that threatens Texans’ health and economic well-being to the devastation of Hurricane Harvey and other natural disasters to the tragic mass shootings that claimed innocent lives in Sutherland Springs, Santa Fe, El Paso, and Midland-Odessa. We also recall the multi-site bombing campaign in Austin, the cybersecurity attack on over 20 local agencies, a border security crisis that overwhelmed federal capabilities, actual and threatened violence in our cities, and countless other incidents that tested the capabilities of our first responders and the resilience of our communities. In addition, Texas continues to see significant threats from international cartels, gangs, domestic terrorists, and cyber criminals. In this environment, it is essential that we actively assess and manage risks and work together as a team, with state and local governments, the private sector, and individuals, to enhance our preparedness and protect our communities. The Texas Homeland Security Strategic Plan 2021-2025 lays out Texas’ long-term vision to prevent and respond to attacks and disasters. It will serve as a guide in building, sustaining, and employing a wide variety of homeland security capabilities. As we build upon the state’s successes in implementing our homeland security strategy, we must be prepared to make adjustments based on changes in the threat landscape. By fostering a continuous process of learning and improving, we can work together to ensure that Texas is employing the most effective and innovative tactics to keep our communities safe. -

Pledge Allegiance”: Gendered Surveillance, Crime Television, and Homeland
This is a repository copy of “Pledge Allegiance”: Gendered Surveillance, Crime Television, and Homeland. White Rose Research Online URL for this paper: http://eprints.whiterose.ac.uk/150191/ Version: Published Version Article: Steenberg, L and Tasker, Y (2015) “Pledge Allegiance”: Gendered Surveillance, Crime Television, and Homeland. Cinema Journal, 54 (4). pp. 132-138. ISSN 0009-7101 https://doi.org/10.1353/cj.2015.0042 This article is protected by copyright. Reproduced in accordance with the publisher's self-archiving policy. Reuse Items deposited in White Rose Research Online are protected by copyright, with all rights reserved unless indicated otherwise. They may be downloaded and/or printed for private study, or other acts as permitted by national copyright laws. The publisher or other rights holders may allow further reproduction and re-use of the full text version. This is indicated by the licence information on the White Rose Research Online record for the item. Takedown If you consider content in White Rose Research Online to be in breach of UK law, please notify us by emailing [email protected] including the URL of the record and the reason for the withdrawal request. [email protected] https://eprints.whiterose.ac.uk/ Cinema Journal 54 i No. 4 I Summer 2015 "Pledge Allegiance": Gendered Surveillance, Crime Television, and H o m e la n d by Lindsay Steenber g and Yvonne Tasker lthough there are numerous intertexts for the series, here we situate Homeland (Showtime, 2011—) in the generic context of American crime television. Homeland draws on and develops two of this genre’s most highly visible tropes: constant vigilance regardingA national borders (for which the phrase “homeland security” comes to serve as cultural shorthand) and the vital yet precariously placed female investigator. -

INTRODUCTION • the Following Presentation Describes the Design and Content of the VA
INTRODUCTION • The following presentation describes the design and content of the VA. State Vaccination Campaign Plan Seminar and Tabletop Exercise. Emphasis is required to illustrate that this was a State‐Level Series to Roll‐Out the State Vaccination Campaign Plan and to exercise the State's ability to operationalize and implement. VDH has designed guidance and a plan template for use at the Local Health District (LHD) Level. • Additionally, a TABLETOP‐IN‐A‐BOX Exercise is forthcoming, also for use at the LHD level. • Our VDEM partners have asked that we include the following for consideration at the local EM level: "There are several types of resources that may be necessary to successfully conduct COVID Vaccination Point of Dispensing (POD). Items to consider include (but are not limited to) tents, tables, chairs, internet access, generators, fuel, electric cords, etc. If these items, or others, are needed, local health directors will need to coordinate with the local emergency manager as well as VDH / VDEM regional personnel. Virginia COVID-19 Vaccination Seminar Virginia Department of Health (VDH) Oct 8, 2020 Purpose & Objectives Purpose: To provide an opportunity for Virginia Emergency Support Team partners to: review the Commonwealth of Virginia COVID-19 Draft Vaccination Campaign Plan, examine and discuss support needed to execute the current vaccination strategy when a vaccine becomes available, and discuss equity in vaccine allocation decisions and identify any gaps not noted in the plan and any decisions that would require senior leadership input. Objectives: • Increase stakeholder knowledge of the current COVID 19 Vaccination Campaign Plan and their roles to support execution of the plan upon arrival of COVID vaccines in the Commonwealth. -

Q&A with SECAF Heather Wilson 10
USAF AI Transformation 32 | A Better Bomber Vector 50 | Reaper Rewards 38 Q&A With SECAF Heather Wilson 10 POWERBlock 4 adds brains and brawn to the UP F-35.26 March 2019 $8 Published by the Air Force Association Join us at the AFA Air Warfare Symposium, booth 815. THOSE BORN TO FLY LIVE TO WALK AWAY ACES 5®: Protects aircrew of all sizes Protecting aircrew of all sizes is a mission that drives us relentlessly forward. It’s why our ACES 5® ejection seat meets the exacting standards of MIL-HDBK-516C. It’s why we’ve equipped it with advanced restraint systems, innovative technologies to stabilize the seat and better protect the head and neck, and an improved recovery parachute for safer descents. Learn more about the most advanced protection for your aircrew. collinsaerospace.com/aces5 ©2019 Collins Aerospace, a United Technologies company. All rights reserved. UTC Aerospace Systems and Rockwell Collins are now Collins Aerospace. Collins_ACES 5_AD__AirForceMag.indd 1 2/1/19 9:01 AM STAFF Publisher Larry O. Spencer March 2019. Vol. 102, No. 2 Editor in Chief Tobias Naegele Managing Editor Juliette Kelsey Chagnon Editorial Director John A. Tirpak News Editor Amy McCullough Photo: SSgt. Mosier Photo: Jeremy Assistant DEPARTMENTS FEATURES An MQ-9 in Managing Editor Southwest Asia. Chequita Wood 2 Editorial: 10 Q&A With the Secretary See p. 38. Delayed Senior Designer An exclusive interview with Secretary of the Air Force Dashton Parham Gratification Heather Wilson. By Tobias Pentagon Editor Naegele Brian W. Everstine Does the 26 Keeping the F-35 Ahead of the Bad Guys Digital Platforms argument for By John A. -

National Incident Management System (NIMS)
December 18, 2008 Dear NIMS Stakeholders: Homeland Security Presidential Directive (HSPD)-5, Management of Domestic Incidents, directed the development and administration of the National Incident Management System (NIMS). Originally issued on March 1, 2004, by the Department of Homeland Security (DHS), NIMS provides a consistent nationwide template to enable Federal, State, 1 tribal, and local2 governments, nongovernmental organizations (NGOs), and the private sector to work together to prevent, protect against, respond to, recover from, and mitigate the effects of incidents, regardless of cause, size, location, or complexity. HSPD-5 also required DHS to establish a mechanism for ongoing coordination to provide strategic direction for, and oversight of, NIMS. The National Integration Center (NIC)’s Incident Management Systems Integration Division (IMSI)—formerly the NIMS Integration Center—was established to support both routine maintenance and the continuous refinement of NIMS. Since 2006, the NIMS document has been revised to incorporate best practices and lessons learned from recent incidents. The NIMS revision also clarifies concepts and principles, and refines processes and terminology throughout the document. A wide range of feedback was incorporated while maintaining the core concepts of NIMS and no major policy changes were made to the document during the revision. Below is a summary of changes to the NIMS document: . Eliminated redundancy; . Reorganized document to emphasize that NIMS is more than the Incident Command System (ICS); . Clarified ICS concepts; . Increased emphasis on planning and added guidance on mutual aid; . Clarified roles of private sector, NGOs, and chief elected and appointed officials; 1 As defined in the Homeland Security Act of 2002, P.L.