2008 NCTC Report on Terrorism
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
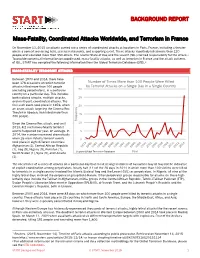
Mass-Fatality, Coordinated Attacks Worldwide, and Terrorism in France
BACKGROUND REPORT Mass-Fatality, Coordinated Attacks Worldwide, and Terrorism in France On November 13, 2015 assailants carried out a series of coordinated attacks at locations in Paris, France, including a theater where a concert was being held, several restaurants, and a sporting event. These attacks reportedly killed more than 120 people and wounded more than 350 others. The Islamic State of Iraq and the Levant (ISIL) claimed responsibility for the attack.1 To provide contextual information on coordinated, mass-fatality attacks, as well as terrorism in France and the attack patterns of ISIL, START has compiled the following information from the Global Terrorism Database (GTD).2 MASS-FATALITY TERRORIST ATTACKS Between 1970 and 2014, there have been 176 occasions on which terrorist Number of Times More than 100 People Were Killed attacks killed more than 100 people by Terrorist Attacks on a Single Day in a Single Country (excluding perpetrators), in a particular 30 country on a particular day. This includes both isolated attacks, multiple attacks, 25 and multi-part, coordinated attacks. The first such event took place in 1978, when 20 an arson attack targeting the Cinema Rex Theater in Abadan, Iran killed more than 15 400 people. Frequency Since the Cinema Rex attack, and until 10 2013, 4.2 such mass-fatality terrorist events happened per year, on average. In 5 2014, the number increased dramatically when 26 mass-fatality terrorist events 0 took place in eight different countries: Afghanistan (1), Central African Republic (1), Iraq (9), Nigeria (9), Pakistan (1), Source: Global Terrorism Database Year South Sudan (1), Syria (3), and Ukraine (1). -

Extremism and Terrorism
Pakistan: Extremism and Terrorism On April 21, 2021, a car bomb exploded in the parking lot of the Serena Hotel in Quetta, killing at least five and wounding 11. Chinese ambassador to Pakistan Nong Rong was staying in the hotel but was not present during the attack. Tehrik-e Taliban Pakistan (TTP) claimed responsibility. “It was a suicide attack in which our suicide bomber used his explosives-filled car in the hotel,” the TTP said in a text message to Reuters. (Sources: Reuters, Associated Press) On April 12, 2021, police in Lahore arrested Saad Rizvi, leader of the outlawed Islamist political party Tehreek-e-Labaik Pakistan (TLP). The arrest was reportedly to deter TLP supporters from further demanding the expulsion of France’s ambassador over the publication in France of cartoons featuring Islam’s Prophet Muhammad. Rizvi had claimed the government had reached an agreement with his party to expel the ambassador by April 20, while government officials claimed they agreed only to discuss the issue in parliament. In response to Rizvi’s arrest, TLP supporters blocked highways and clash with police across the country over the course of two days, killing at least four people and wounding dozens of others, including at least 60 police officers. On April 18, TLP supporters attacked a police station in Lahore while rallying in the city against Rizvi’s arrest. The protesters took hostage 11 officers. The protesters released the hostages the following day after negotiations with the government. Photos released of the hostages during the negotiations showed they had been tortured. (Sources: Voice of America, Associated Press) Overview Since its independence from British colonial rule in 1947, Pakistan has been divided along ethnic, religious, and sectarian lines, a condition which has been exploited by internal and external organizations to foster extremism and terrorism. -

Pakistan Army and Terrorism; an Unholy Alliance
Pakistan Army and Terrorism; an unholy alliance Pakistan has been known for its perennial support of the Taliban in Afghanistan and other terrorist organizations in Indian Administered Jammu and Kashmir. The dramatic events of the terrorist attacks on the twin towers in the United States (U.S) on the 11th of September 2001 also referred to as 9/11, shook the tectonic plates of world politics, pushing Pakistan into being a focal point of global politics. Pakistan became the key strategic partner of United States’ War on Terror; post the terrorist attacks, taking a complete U-turn in her traditional foreign policies towards Afghanistan and Indian Administered Jammu and Kashmir, albeit temporarily under international pressure for heavy monetary gains. The country, in which sectarian groups targeting minority communities (Shias, Sufis, Ahmadis etc.) and Kashmir- focused groups confined their operations to Indian Administered Kashmir and the rest of India, has become a victim of its own holy war as a consequence of the ‘unholy alliance’ between the Inter Intelligence Services (ISI), Pakistan’s powerful intelligence agency, military and self-styled religious scholars. This historic alliance has resulted in colossal rise of radical Islam being a factor in the country’s proclivity to Islamic fundamentalism. Jihadi Groups There are several kind of militant groups operating in and from Pakistan that can be distinguished by their sectarian background (Ahl-e-Hadith, Deobandi, Jamaat-e-Islami etc.), and their areas of operation (Afghanistan, India, Pakistan). Their objectives may vary from overthrowing the Pakistani government, seizure of Indian Administered Jammu and Kashmir or support of Afghan Taliban. -

EASO Country of Origin Information Report Pakistan Security Situation
European Asylum Support Office EASO Country of Origin Information Report Pakistan Security Situation October 2018 SUPPORT IS OUR MISSION European Asylum Support Office EASO Country of Origin Information Report Pakistan Security Situation October 2018 More information on the European Union is available on the Internet (http://europa.eu). ISBN: 978-92-9476-319-8 doi: 10.2847/639900 © European Asylum Support Office 2018 Reproduction is authorised, provided the source is acknowledged, unless otherwise stated. For third-party materials reproduced in this publication, reference is made to the copyrights statements of the respective third parties. Cover photo: FATA Faces FATA Voices, © FATA Reforms, url, CC BY-NC-SA 2.0 Neither EASO nor any person acting on its behalf may be held responsible for the use which may be made of the information contained herein. EASO COI REPORT PAKISTAN: SECURITY SITUATION — 3 Acknowledgements EASO would like to acknowledge the Belgian Center for Documentation and Research (Cedoca) in the Office of the Commissioner General for Refugees and Stateless Persons, as the drafter of this report. Furthermore, the following national asylum and migration departments have contributed by reviewing the report: The Netherlands, Immigration and Naturalization Service, Office for Country Information and Language Analysis Hungary, Office of Immigration and Nationality, Immigration and Asylum Office Documentation Centre Slovakia, Migration Office, Department of Documentation and Foreign Cooperation Sweden, Migration Agency, Lifos -

The Euphrates River: an Analysis of a Shared River System in the Middle East
/?2S THE EUPHRATES RIVER: AN ANALYSIS OF A SHARED RIVER SYSTEM IN THE MIDDLE EAST by ARNON MEDZINI THESIS SUBMITTED FOR THE DEGREE OF DOCTOR OF PHILOSOPHY SCHOOL OF ORIENTAL AND AFRICAN STUDIES UNIVERSITY OF LONDON September 1994 ProQuest Number: 11010336 All rights reserved INFORMATION TO ALL USERS The quality of this reproduction is dependent upon the quality of the copy submitted. In the unlikely event that the author did not send a com plete manuscript and there are missing pages, these will be noted. Also, if material had to be removed, a note will indicate the deletion. uest ProQuest 11010336 Published by ProQuest LLC(2018). Copyright of the Dissertation is held by the Author. All rights reserved. This work is protected against unauthorized copying under Title 17, United States C ode Microform Edition © ProQuest LLC. ProQuest LLC. 789 East Eisenhower Parkway P.O. Box 1346 Ann Arbor, Ml 48106- 1346 Abstract In a world where the amount of resources is constant and unchanging but where their use and exploitation is growing because of the rapid population growth, a rise in standards of living and the development of industrialization, the resource of water has become a critical issue in the foreign relations between different states. As a result of this many research scholars claim that, today, we are facing the beginning of the "Geopolitical era of water". The danger of conflict of water is especially severe in the Middle East which is characterized by the low level of precipitation and high temperatures. The Middle Eastern countries have been involved in a constant state of political tension and the gap between the growing number of inhabitants and the fixed supply of water and land has been a factor in contributing to this tension. -

Annual Report 2007 Annual Report Russia
UNITED STATES COMMISSION ON INTERNATIONAL RELIGIOUS FREEDOM Annual Report 2007 Annual Report RUSSIA UNITED STATES COMMISSION ON INTERNATIONAL RELIGIOUS FREEDOM Annual Report MAY 2007 U.S. Commission on International Religious Freedom 800 North Capitol Street, NW Suite 790 Washington, DC 20002 202-523-3240 202-523-5020 (fax) www.uscirf.gov UNITED STATES COMMISSION ON INTERNATIONAL RELIGIOUS FREEDOM Commissioners Chair Felice D. Gaer Vice Chairs Michael Cromartie Dr. Elizabeth H. Prodromou Nina Shea Dr. Khaled M. Abou El Fadl Preeta D. Bansal Archbishop Charles J. Chaput Dr. Richard D. Land Bishop Ricardo Ramirez John V. Hanford, III, ex officio, non-voting member Executive Director Joseph R. Crapa UNITED STATES COMMISSION ON INTERNATIONAL RELIGIOUS FREEDOM Staff Tad Stahnke, Deputy Director for Policy David Dettoni, Deputy Director for Outreach Judith Ingram, Director of Communications Holly Smithson, Director of Government Affairs Carmelita Hines, Director of Administration Patricia Carley, Associate Director for Policy Angela Stephens, Assistant Communications Director Dwight Bashir, Senior Policy Analyst Catherine Cosman, Senior Policy Analyst Deborah DuCre, Receptionist Scott Flipse, Senior Policy Analyst Julia Kirby, Middle East Researcher Mindy Larmore, East Asia Researcher Tiffany Lynch, Research Assistant Jacqueline A. Mitchell, Executive Assistant Allison Salyer, Legislative Assistant Stephen R. Snow, Senior Policy Analyst Christopher Swift, Researcher UNITED STATES COMMIssION ON INTERNATIONAL RELIGIOUS FREEDOM Washington, DC, May 1, 2007 The PRESIDENT The White House DEAR MR. PRESIDENT: On behalf of the United States Commission on International Religious Freedom, I am transmitting to you the annual report, prepared in compliance with section 202(a)(2) of the International Religious Freedom Act of 1998, 22 U.S.C. -

Isis in the Southwest Baghdad Belts
ALI DAHLIN BACKGROUNDER NOVEMBER 24, 2014 ISIS IN THE SOUTHWEST BAGHDAD BELTS hroughout September and October 2014, the Islamic State of Iraq and al-Sham (ISIS) moved to Tconsolidate its control of terrain in al-Anbar province, closing the gap in its Euphrates control between Haditha and Ramadi. While ISIS does not yet control either city, ISIS seized the midway point between at Hit on October 2, 2014.1 This backgrounder will examine ISIS forces southwest of Baghdad, which have recently been the focus of a counter-offensive by the ISF. The expulsion of ISIS forces southwest of Baghdad may generate a strategic advantage for the ISF; but it may also initially heighten the threat to Baghdad. The southwestern Baghdad Belts have been an ISIS stronghold of this terrain to ISIS, it is necessary to estimate the remaining for some time. ISIS reestablished itself in 2013 within the strength of ISIS forces between south of Amiriyat al-Fallujah and historic “Triangle of Death” comprised of a cluster of cities 20 km northern Babil. It is unclear at this time whether ISIS attacks south of Baghdad, including Mahmudiyah, Latifiyah, and on Amiriyat al-Fallujah in April 2014 were purely defensive Yusifiyah. Shi’a militia groups have had control of these areas measures to protect Fallujah, or whether they were offensive since 2013, whereas ISIS has been present in the countryside, measures to consolidate territory in the northern “outer” ring. particularly in the Karaghuli tribal areas, including Jurf Closer examination of ISIS activities from January 2014 to al-Sakhar. ISIS presence in this area allowed the group to October 2014 reveal that there are separate ISIS sub- launch VBIED attacks in southwestern Baghdad in 2013, as well as to project influence over populated areas to the west in Anbar province.2 These towns, including Jurf al-Sakhar, Farisiyah, Fadhiliyah, Abu Ghraib, and Amiriyat al-Fallujah, link ISIS in northern Babil with ISIS in Anbar. -

Worldwide Attacks Against Dams
Worldwide Attacks Against Dams A Historical Threat Resource for Owners and Operators 2012 i ii Preface This product is a compilation of information related to incidents that occurred at dams or related infrastructure world-wide. The information was gathered using domestic and foreign open-source resources as well as other relevant analytical products and databases. This document presents a summary of real-world events associated with physical attacks on dams, hydroelectric generation facilities and other related infrastructure between 2001 and 2011. By providing an historical perspective and describing previous attacks, this product provides the reader with a deeper and broader understanding of potential adversarial actions against dams and related infrastructure, thus enhancing the ability of Dams Sector-Specific Agency (SSA) partners to identify, prepare, and protect against potential threats. The U.S. Department of Homeland Security (DHS) National Protection and Programs Directorate’s Office of Infrastructure Protection (NPPD/IP),which serves as the Dams Sector- Specific Agency (SSA), acknowledges the following members of the Dams Sector Threat Analysis Task Group who reviewed and provided input for this document: Jeff Millenor – Bonneville Power Authority John Albert – Dominion Power Eric Martinson – Lower Colorado River Authority Richard Deriso – Federal Bureau of Investigation Larry Hamilton – Federal Bureau of Investigation Marc Plante – Federal Bureau of Investigation Michael Strong – Federal Bureau of Investigation Keith Winter – Federal Bureau of Investigation Linne Willis – Federal Bureau of Investigation Frank Calcagno – Federal Energy Regulatory Commission Robert Parker – Tennessee Valley Authority Michael Bowen – U.S. Department of Homeland Security, NPPD/IP Cassie Gaeto – U.S. Department of Homeland Security, Office of Intelligence and Analysis Mark Calkins – U.S. -

Using Collective Memory to Bulid Authenticity Case Study (Al-Adhamiya and Al-Kadhmiya Districts in Baghdad-Iraq)
International Journal of Civil Engineering and Technology (IJCIET) Volume 9, Issue 10, October 2018, pp. 1–11, Article ID: IJCIET_09_10_001 Available online at http://iaeme.com/Home/issue/IJCIET?Volume=9&Issue=10 ISSN Print: 0976-6308 and ISSN Online: 0976-6316 ©IAEME Publication Scopus Indexed USING COLLECTIVE MEMORY TO BULID AUTHENTICITY CASE STUDY (AL-ADHAMIYA AND AL-KADHMIYA DISTRICTS IN BAGHDAD-IRAQ) Malk Jamal Hamzah Postgraduate Student, Center of Urban and Regional Planning for Postgraduate Studies University of Baghdad, Baghdad, Iraq Mustafa Abduljalil Ebraheem Assistant Professor, Center of Urban and Regional Planning for Postgraduate Studies University of Baghdad, Baghdad, Iraq ABSTRACT The importance of the authenticity in the world is increasing by matching it with the sustainability of the cities, besides using it as clean economy investments, from reflecting the cultural, aesthetic, vernacular, and moral related to any city as investment chance, from that this subject takes its importance. One of important thing in the forming of urban fabric were the events are related to that fabric, from these events the urban fabric get its meaning and authenticity, so we are facing in most Iraqis cities problem of neglecting the effecting of either positive or negative events to increase our cities authenticity, this will be done by defending on collective memory of residents and visitors to these cities, by trying to creating mental map for each city depending on the collective memory of people. The research goal is to find out the -

Who Are the Insurgents? Sunni Arab Rebels in Iraq
UNITED STATES INSTITUTE OF PEACE www.usip.org SPECIAL REPORT 1200 17th Street NW • Washington, DC 20036 • 202.457.1700 • fax 202.429.6063 ABOUT THE REPORT “Who Are the Insurgents?” offers insight into the breadth of Sunni Arab groups actively participating Who Are the Insurgents? in the insurrection in Iraq and specifically examines the three broad categories of insurgents: secular/ ideological, tribal, and Islamist. With the exception Sunni Arab Rebels in Iraq of the ultraradical Salafi and Wahhabi Islamists, this report finds, many rebels across these three classifications share common interests and do not sit so comfortably in any one grouping or category. This presents specific problems—and Summary opportunities—for U.S. and coalition forces that, • Building a profile of a typical anti-coalition Sunni Arab insurgent in Iraq is a daunting if handled correctly, could eventually lead to a rapprochement with some of the insurgents. task. Demographic information about the insurgents is fragmented, and the rebels themselves are marked more by their heterogeneity than by their homogeneity. Draw- The report’s author, Amatzia Baram, is a professor ing from a wide array of sources, however, we can try to piece together a view of their of Middle Eastern history at the University of Haifa, primary motivations for taking up arms against the U.S.-led occupation. Israel. He is a prolific writer and editor of several books and dozens of scholarly articles on Saddam • Sunni insurgents generally claim one of three primary identity-based impetuses Hussein and Iraqi politics and history. He testified for their anti-American and antigovernment violence: Ba’th Party membership or about Saddam Hussein and weapons of mass affiliation with Saddam’s regime, adherence to Islam, or tribal interests, values, and destruction in September 2002 before the House norms. -

After Mumbai: Time to Strengthen U.S.–India Counterterrorism Cooperation Lisa Curtis
No. 2217 December 9, 2008 After Mumbai: Time to Strengthen U.S.–India Counterterrorism Cooperation Lisa Curtis As the United States and India seek to build a stronger partnership and take full advantage of the diplomatic opening created by the U.S.–India civil Talking Points nuclear deal, one of the areas with the greatest poten- • The November terrorist attacks in Mumbai tial benefit to both sides is counterterrorism coopera- highlight the urgent need for U.S.–Indian tion. The multiple terrorist attacks in Mumbai cooperation to counter regional and global between November 26 and November 29, 2008, that terrorist threats. killed about 170 people, including six Americans, • Both New Delhi and Washington stand to gain have highlighted the urgent need for these two coun- considerably from improving counterterrorism tries to work together more closely to counter cooperation and must overcome lingering dis- regional and global terrorist threats. trust that stems largely from U.S. reluctance to pursue Pakistani terrorist groups with the same Despite general convergence of American and zeal that it shows in pursuing al-Qaeda. Indian views on the need to contain terrorism, the two countries have failed in the past to work together as • The U.S. and India should expand cooperation closely as they could to minimize terrorist threats, on sharing intelligence and promoting democracy and religious pluralism to disrupt largely because of differing geostrategic perceptions, terrorist recruitment. They should improve Indian reluctance to deepen the intelligence relation- cooperation on maritime security, cyber secu- ship, and U.S. bureaucratic resistance to elevating rity, energy security, and nuclear nonprolifer- counterterrorism cooperation beyond a certain level. -

Extreme Stress and Investor Behavior: Evidence from a Natural Experiment
Extreme stress and investor behavior: Evidence from a natural experiment Vikas Agarwal, Georgia State University Pulak Ghosh, Indian Institute of Management Bangalore Haibei Zhao, Lehigh University August 2019 Abstract We use the 2008 Mumbai terrorist attacks as a natural experiment to examine how exposure to extreme stress affects financial decision making, as measured by investors’ stock trading activity and performance. We find that Mumbai investors trade less, perform worse, take longer time to react to corporate news announcement, are less likely to initiate trades on new stocks, and perform worse on familiar stocks compared with other traders. Collectively, our findings are most consistent with impairment of cognitive ability after exposure to prolonged and extreme stress. JEL Classification: D10, G11, G14, G41 Keywords: individual investors, stress, cognitive ability, trading, violence Vikas Agarwal is from J. Mack Robinson College of Business, Georgia State University. Email: [email protected]. Vikas Agarwal is also a Research Fellow at the Centre for Financial Research (CFR), University of Cologne. Pulak Ghosh is from Decision Sciences and Center of Public Policy, Indian Institute of Management Bangalore. Email: [email protected]. Haibei Zhao is from College of Business, Lehigh University. Email: [email protected]. We thank Shashwat Alok, Yakov Amihud, Ashok Banerjee, Brad Barber, Gennaro Bernile, Asaf Bernstein, Paul Brockman, Zhi Da, Eliezer Fich, Anand Goel, Clifton Green, Jiekun Huang, Xing Huang, Narasimhan Jegadeesh, Lawrence Jin, Kose John, Terrance Odean, Lin Peng, Sugata Ray, Stephan Siegel, Rosy Xu, Pradeep Yadav, Yesha Yadav, Sterling Yan, and seminar participants at Cornell University, Tilburg University, Washington University in St.