A First Large-Scale Analysis on Usage of MTA-STS
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Guidelines on Electronic Mail Security
Special Publication 800-45 Version 2 Guidelines on Electronic Mail Security Recommendations of the National Institute of Standards and Technology Miles Tracy Wayne Jansen Karen Scarfone Jason Butterfield NIST Special Publication 800-45 Guidelines on Electronic Mail Security Version 2 Recommendations of the National Institute of Standards and Technology Miles Tracy, Wayne Jansen, Karen Scarfone, and Jason Butterfield C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 February 2007 U .S. Department of Commerce Carlos M. Gutierrez, Secretary Technology Administration Robert C. Cresanti, Under Secretary of Commerce for Technology National Institute of Standards and Technology William Jeffrey, Director Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security, and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-45 Version 2 Natl. Inst. Stand. Technol. Spec. Publ. 800-45 Version 2, 139 pages (Feb. -
EAI Readiness in Tlds
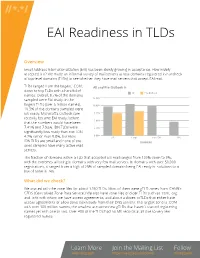
EAI Readiness in TLDs Overview Email Address Internationalization (EAI) has been slowly growing in acceptance. How widely accepted is it? We made an informal survey of mail servers across domains registered in hundreds of top-level domains (TLDs) to see whether they have mail servers that accept EAI mail. TLDs ranged from the largest, .COM, All and Pre-Outlook % down to tiny TLDs with a handful of All Pre-Outlook names. Overall, 9.7% of the domains sampled were EAI ready. In the 12.50% largest TLDs (over a million names), 10.00% 10.5% of the domains sampled were EAI ready. Microsoft’s Outlook.com 7.50% recently became EAI ready; before 5.00% that the numbers would have been 7.41% and 7.93%. IDN TLDs were 2.50% significantly less ready than non-IDN, 0.00% 4.7% rather than 9.8%, but most All Large non-IDN IDN IDN TLDs are small and none of the DOMAINS ones sampled have many active mail servers. The fraction of domains within a TLD that accepted EAI mail ranged from 100% down to 0%, with the extremes all being in domains with very few mail servers. In domains with over 50,000 registrations, it ranged from a high of 25% of sampled domains being EAI ready in .solutions to a low of none in .ren. What did we check? We started with the zone files for about 1250 TLDs. Most of them were gTLD zones from ICANN’s CZDS (Centralized Zone Data Service.) We also have zone files of older TLDs such as .com, .org, and .info with whom we have access agreements, and about a dozen ccTLDs that either have access agreements or allow zone downloads from their DNS servers. -

Lan Mail Software
Lan mail software click here to download CMailServer is an email server software for Windows, which provide web based email service. You can use it to setup your own Internet email server and provide e-mail service for your company and friends. In 'Options' of CMailServer, select 'Run As LAN Mail Server' and 'Single. SpamPal is designed as a personal mail filter that will run on same local to work with SpamPal, choose from the following list of email Lan Mail Server software. This article will tell you how to create LAN mail server step by step. such as Outlook, to send and receive mails, please refer to "Mail Client". It is possible to set up an email server on your local LAN, by installing the Launch an email client like Microsoft Outlook on any computer. hMailServer - Free open source email server for Microsoft Windows. Local mail on LAN with no internet connection When I try to configure the Outlook client, I get connection to POP server ok, but fails on SMTP. Don't use the email client and the hMailServer Administration application at the my mail server from outside the lan, just within the lan, what should i do sir?. Free mail server for Microsoft Windows by MailEnable Standard Edition. Download free email server - simple software to install, easy to use, no spyware, it's free. Postmaster Email server software enhances email efficiency. Want to send and receive email from any node on LAN? Use Postmaster email servers!. I want to setup a Mail server in my LAN network, which is I want to send mail from my client systems to the Mail server (), and. -

Professional Manual
Professional Manual 1 Table of Contents 1. Table of Contents 1-8 2. Introduction 9 2.1. Introduction 9 2.2. Prerequisites 9-10 2.3. How Internet Email Works 10-11 2.4. What's New in Version 10 11-12 3. Overview 13 3.1. Overview 13 3.2. Structure of MailEnable 13-14 3.3. Administration 14-15 3.4. Email Delivery Flow 15-16 4. Installation 17 4.1. Installation Overview 17 4.2. Installation process 17-25 4.3. Upgrading 25 4.3.1. Upgrading Overview 25 4.3.2. Upgrading an existing web mail installation 25-26 4.3.3. Configuration repository location 26 4.3.4. Replace configuration files 26-27 4.4. Post-installation configuration 27 4.4.1. MailEnable Diagnostic Utility 27-29 4.4.2. Check and configure DNS settings 29 4.4.3. To set up PTR records under Microsoft's DNS Server 29-30 4.4.4. Check mail services 30 5. Administration 31 5.1. Administration Overview 31 5.2. Messaging Manager 31 5.2.1. Messaging Manager Overview 31-32 5.2.2. Messaging Manager - General 32 5.2.3. Messaging Manager - Administration 32-33 5.2.4. Messaging Manager - Security 33-34 1 ©2018 MailEnable Pty Ltd. All Rights Reserved. Professional Manual 5.2.5. Messaging Manager - Footers 34 5.3. Post office configuration 34 5.3.1. Post office configuration Overview 34-35 5.3.2. How to create a Post Office 35 5.3.3. Post office - General 35-36 5.3.4. -
Mailenable Email Server
MailEnable Email Server ﺟﺎﻣﻊ ﺗﺮﯾﻦ و ﻗﺪرﺗﻤﻨﺪﺗﺮﯾﻦ اﯾﻤﯿﻞ ﺳﺮور ﺟﻬﺎن ﻧﺼﺐ، ﻣﺪﯾﺮﯾﺖ و ﻧﮕﻬﺪاري ﺑﺴﯿﺎر آﺳﺎن اﻣﮑﺎن ﺗﻌﯿﯿﻦ ﻧﺤﻮه Authentication ﺑﺼﻮرت داﺧﻠﯽ ﯾﺎ ﺑﻬﺮه ﮔﯿﺮي از ﺗﮑﻨﻮﻟﻮژي .Net و ﺗﻠﻔﯿﻖ ﮐﺎﻣﻞ ﺑﺎ ﺳﺮوﯾﺴﻬﺎي ﻣﺎﯾﮑﺮوﺳﺎﻓﺖ اﮐﺘﯿﻮداﯾﺮﮐﺘﻮري ﺑﻪ ازاي ﻫﺮ ﮐﺎرﺑﺮ ﻣﺎﻧﻨﺪ اﮐﺘﯿﻮداﯾﺮﮐﺘﻮري و Mobile/Desktop Webmail Chat ActiveSync ﺑﺎ ﻗﺎﺑﻠﯿﺖ وﯾﺪﯾﻮ ﮐﻨﻔﺮاﻧﺲ راﻫﮑﺎرﻫﺎي ﭘﯿﺸﺮﻓﺘﻪ Migration اﺗﻮﻣﺎﺗﯿﮏ از اﯾﻤﯿﻞ ﺳﺮورﻫﺎي ﻗﺪﯾﻤﯽ ﮔﺮوﻫﯽ ﮐﻠﯿﻪ اﺑﺰارﻫﺎي ﻧﮕﻬﺪاري ﻣﺎﻧﻨﺪ Server monitoring ،Backup و اﻣﮑﺎن ارﺳﺎل و درﯾﺎﻓﺖ SMS ﺑﺎ اﺳﺘﻔﺎده از ﻣﻮدم GSM، ﮔﻮﺷﯽ و ﯾﺎ Remote monitoring ﺗﻌﺒﯿﻪ ﺷﺪه در ﺧﻮد ﻧﺮماﻓﺰار Gateway (ﺳﺎﻣﺎﻧﻪ ﭘﯿﺎﻣﮏ) راﻫﮑﺎرﻫﺎي ﭘﯿﺸﺮﻓﺘﻪ ﺑﮑﺎپ ﮔﯿﺮي ﺑﺪون ﻫﺮﮔﻮﻧﻪ اﺧﺘﻼل در ﺳﯿﺴﺘﻢ وبﻣﯿﻞ ﺑﺴﯿﺎر ﭘﯿﺸﺮﻓﺘﻪ ASP .Net ﺑﺎ اﻣﮑﺎﻧﺎت اﺷﺘﺮاكﮔﺬاري ﻓﺎﯾﻞ، داراي ﺳﺮوﯾﺲﻫﺎي File Sharing & Collaboration, و SMS ﺑﻪ اﻟﺼﺎق ﻫﻮﺷﻤﻨﺪ ﻓﺎﯾﻞ ، ارﺳﺎل SMS، ﺗﻘﻮﯾﻢ ﺑﻪ ﻫﻤﺮاه ﺗﻌﻄﯿﻼت ﺻﻮرت ﮐﺎﻣﻼ ﯾﮑﭙﺎرﭼﻪ ﮐﺸﻮرﻫﺎي ﻣﺨﺘﻠﻒ ﭘﺸﺘﯿﺒﺎﻧﯽ از دﯾﺘﺎﺑﯿﺲ MS SQL Server و MySQL ﻗﺎﺑﻠﯿﺖ ﯾﮑﭙﺎرﭼﻪ ﺳﺎزي ﮐﺎﻣﻞ ﺑﺎ Outlook Load Balancing و Clustering ﺳﺮوﯾﺴﻬﺎ اﺣﺮاز ﻫﻮﯾﺖ ﭼﻨﺪ ﻋﺎﻣﻠﯽ در وﺑﻤﯿﻞ( ﻣﺎﻧﻨﺪ اﺳﺘﻔﺎده از Google ﻣﺪﯾﺮﯾﺖ از ﻃﺮﯾﻖ ﮐﻨﺴﻮل MMC ، ﮐﻨﺴﻮل ﺗﺤﺖ وب و ﯾﺎ Authenticator ) ﺑﺮاي اﻓﺰاﯾﺶ اﻣﻨﯿﺖ Powershell داراي List Server ﺟﺎﻣﻊ و ﮐﺎﻣﻞ اﻣﮑﺎﻧﺎت اﻣﻨﯿﺘﯽ ﻣﺎﻧﻨﺪ ﻣﻘﺎﺑﻠﻪ ﺑﺎ وﯾﺮوس و اﺳﭙﻢ و IPS ﻣﻌﺮﻓﯽ: MailEnable ﻣﺤﺼﻮل اﺳﺘﺮاﻟﯿﺎ از ﺳﺎل 2002 در ﺣﻮزه اﯾﻤﯿﻞ ﺳﺮور ﻓﻌﺎﻟﯿﺖ دارد. MailEnable ﺑﺮ ﭘﺎﯾﻪ ﺗﮑﻨﻮﻟﻮژي Net. ﻃﺮاﺣﯽ ﺷﺪه و از ﺗﻤﺎﻣﯽ ﭘﺮوﺗﮑﻠﻬﺎي اﺳﺘﺎﻧﺪارد اﯾﻤﯿﻞ ﻣﺎﻧﻨﺪ SMTP,POP3, IMPA ﺑﻪ ﺻﻮرت SSL/TLS ﭘﺸﺘﯿﺒﺎﻧﯽ ﻣﯽﮐﻨﺪ. اﯾﻦ ﻣﺤﺼﻮل ﻫﻤﭽﻨﯿﻦ داراي List Server و آﻧﺘﯽ وﯾﺮوس و آﻧﺘﯽ اﺳﭙﻢ ﻣﯽﺑﺎﺷﺪ. MailEnable ﺑﺮاي ﮐﺎرﺑﺮان، داراي وﺑﻤﯿﻞ ﭘﯿﺸﺮﻓﺘﻪ ﻣﺨﺼﻮص ﭘﯽ ﺳﯽ و ﻣﻮﺑﺎﯾﻞ ﺑﻮده و از ActiveSync ﺑﻪ ﺻﻮرت ﮐﺎﻣﻞ ﭘﺸﺘﯿﺒﺎﻧﯽ ﻣﯽﮐﻨﺪ. -

Standard Manual
Standard Manual 1 Table of Contents 1. Table of Contents 1-5 2. Introduction 6 2.1. Introduction 6 2.2. Prerequisites 6-7 2.3. How Internet Email Works 7-8 2.4. What's New in Version 10 8-9 3. Overview 10 3.1. Overview 10 3.2. Structure of MailEnable 10-11 3.3. Administration 11-12 3.4. Email Delivery Flow 12-13 4. Installation 14 4.1. Installation Overview 14 4.2. Installation process 14-20 4.3. Upgrading 20 4.3.1. Upgrading Overview 20 4.3.2. Configuration repository location 20 4.3.3. Replace configuration files 20-21 4.4. Post-installation configuration 21 4.4.1. MailEnable Diagnostic Utility 21-23 4.4.2. Check and configure DNS settings 23 4.4.3. To set up PTR records under Microsoft's DNS Server 23 4.4.4. Check mail services 23-24 5. Administration 25 5.1. Administration Overview 25 5.2. Messaging Manager 25 5.2.1. Messaging Manager Overview 25-26 5.2.2. Messaging Manager - General 26 5.2.3. Messaging Manager - Administration 26-27 5.2.4. Messaging Manager - Security 27-28 5.3. Post office configuration 28 1 ©2018 MailEnable Pty Ltd. All Rights Reserved. Standard Manual 5.3.1. Post office configuration Overview 28 5.3.2. How to create a Post Office 28 5.3.3. Post office - General 28-30 5.3.4. Postoffice - Usage Notifications 30-31 5.3.5. Post office actions 31 5.3.5.1. Post office actions Overview 31-32 5.3.5.2. -

Parallels Plesk Panel 10.2, You Can Also Create Customer Accounts Without Subscriptions
Parallels® Panel Copyright Notice Parallels Holdings, Ltd. c/o Parallels International GmbH Vordergasse 59 CH-Schaffhausen Switzerland Phone: +41-526320-411 Fax: +41-52672-2010 Copyright © 1999-2011 Parallels Holdings, Ltd. and its affiliates. All rights reserved. This product is protected by United States and international copyright laws. The product’s underlying technology, patents, and trademarks are listed at http://www.parallels.com/trademarks. Microsoft, Windows, Windows Server, Windows NT, Windows Vista, and MS-DOS are registered trademarks of Microsoft Corporation. Linux is a registered trademark of Linus Torvalds. Mac is a registered trademark of Apple, Inc. All other marks and names mentioned herein may be trademarks of their respective owners. Contents Preface 8 Typographical Conventions ........................................................................................................... 8 Feedback ....................................................................................................................................... 9 Operating Inside Parallels Containers 10 What’s New in Parallels Plesk Panel 12 Panel 10.2 ................................................................................................................................... 12 Becoming Familiar with Parallels Plesk Panel 13 Server Administration Panel ........................................................................................................ 15 Control Panel in Standard Mode ................................................................................................ -
Enterprise Manual
Enterprise Manual 1 Table of Contents 1. Table of Contents 1-10 2. Introduction 11 2.1. Introduction 11 2.2. Prerequisites 11-12 2.3. How Internet Email Works 12-13 2.4. What's New in Version 10 13-14 3. Overview 15 3.1. Overview 15 3.2. Structure of MailEnable 15-16 3.3. Administration 16-17 3.4. Email Delivery Flow 17-18 4. Installation 19 4.1. Installation Overview 19 4.2. Installation process 19-28 4.3. Upgrading 28 4.3.1. Upgrading Overview 28 4.3.2. Upgrading an existing web mail installation 28-29 4.3.3. Configuration repository location 29 4.3.4. Replace configuration files 29-30 4.4. Post-installation configuration 30 4.4.1. MailEnable Diagnostic Utility 30-32 4.4.2. Check and configure DNS settings 32 4.4.3. To set up PTR records under Microsoft's DNS Server 32-33 4.4.4. Check mail services 33 5. Administration 34 5.1. Administration Overview 34 5.2. Messaging Manager 34 5.2.1. Messaging Manager Overview 34-35 5.2.2. Messaging Manager - General 35 5.2.3. Messaging Manager - Administration 35-38 5.2.4. Messaging Manager - Security 38-39 1 Enterprise Manual Enterprise Manual 5.2.5. Messaging Manager - Footers 39 5.2.6. Messaging Manager - Cluster 39-40 5.3. Post office configuration 40 5.3.1. Post office configuration Overview 40 5.3.2. How to create a Post Office 40-41 5.3.3. Post office - General 41-43 5.3.4. -
About Mailenable
MailEnable Página 1 de 87 Welcome to MailEnable Help MailEnable is a general purpose Mail Server designed for Microsoft Windows Server Operating Systems. This help file provides assistance on administraton functions, conceptual architecture, troubleshooting and general information. These are outlined under the following respective headings: How To... Concepts Troubleshooting and Additional Resources About MailEnable... About MailEnable MailEnable's mail server software provides a powerful, scalable hosted messaging platform for Microsoft Windows. MailEnable offers stability, unsurpassed flexibility and an extensive feature set which allows you to provide cost-effective mail services. Our contact details are below: Sales: [email protected] Support: available via our support ticket system Knowledge Base: http://www.mailenable.com/kb Web site: http://www.mailenable.com How To... Install, reinstall, and uninstall MailEnable Administer MailEnable Configure Mail Clients Configure DNS License MailEnable Troubleshoot MailEnable Install, reinstall, and uninstall MailEnable Install software file://C:\Users\Jose L. Rodriguez\AppData\Local\Temp\~hhF4DA.htm 20/08/2012 MailEnable Página 2 de 87 Run unattended setup Reinstall or uninstall software Hardware and software requirements Pre-requisite hardware MailEnable will run on virtually any computer capable of running Windows NT, 2000/2003 or .NET Operating Systems. Note: While the MailEnable product suite can be installed and has been tested on XP and workstation environments the company does not support these platforms. Pre-requisite software For Windows NT 4: - Service Pack 6a - IIS/Windows NT Option Pack 4 (Please refer to note below) - Microsoft Transaction Server, IIS - For Windows 2000/2003: - IIS (Please refer to note below) versions Note: In order to install either the Web Administration or Web Mail components of MailEnable, Microsoft Internet Information Server (IIS) will need to be installed.