Abusing Firefox Extensions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
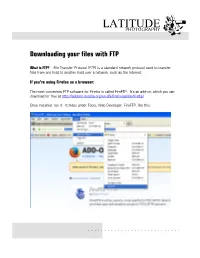
Connecting with FTP Server
LATITUDEPHOTOGRAPHY Downloading your files with FTP What is FTP?: File Transfer Protocol (FTP) is a standard network protocol used to transfer files from one host to another host over a network, such as the Internet. If you’re using Firefox as a browser: The most convenient FTP software for Firefox is called FireFTP. It’s an add-on, which you can download for free at http://addons.mozilla.org/en-US/firefox/addon/fireftp/ Once installed, run it. It hides under Tools, Web Developer, FireFTP, like this: . Firefox will start a new tab right in the browser. On the left, you will have to select QuickConnect from a dropdown list. And a window will popup. Fill in all the fields, with the your login information. Leave the Anonymous box uncheck. Press Connect. 1. Enter ftp.latitudephotography.com here 2. Enter your login name here 3. Password goes here 4. Click here to connect The FTP software will connect and look like this: YOUR Computer 5. Select folder YOUR project folder on the LATITUDE Server Don’t worry about this window The windows which you will use are the middle four. YOUR computer on the left, the LATITUDE computer on the right. If you are looking for High Resolution files from a shoot on January 11, 2013. In the right hand window double click the folder, in this case 2013-01-11. The folder will open and you will now have to select the “High Resolution JPG images” folder. You may also see a “High Resolution PNG images” or “RAW images” folders depending on the project. -

FTP Instructions for Shtetlinks
SFTP Instructions for KehilaLinks SFTP stands for Secure File Transfer Protocol and is a simple way of moving files from your computer to the KehilaLinks server. 1. SFTP Access a. Your KehilaLinks SFTP Username and Password will bring you directly into the folder assigned to your site. You will see an empty space when you enter the SFTP site; the folder is not visible. b. If you manage more than one KehilaLink site, you will be provided a single UserName and Password. This Logon will bring you to a listing of KehilaLinks site folders. Instructions for accessing multiple sites: i. When you logon, you will be on a site with multiple KehilaLink site folders. ii. Double click on the folder that you will be working with. You can then browse, download and upload as needed. Follow instructions in 2 below for downloading and uploading. iii. To go to another of the sites that you manage, return to the KehilaLinks site folders screen and select the next site that you will work on. iv. If you go to a site that you are not authorized for, you can browse the folder, but will get an error message when you try to upload. 2. You can use FTP software which can be downloaded free from such sites as www.download.com or www.cnet.com/ . I will not recommend one package over another. If you use FTP software, the URL to use to SFTP is Sftp.jewishgen.org You will be provided with a Login/Username and a Password. If the software requests a port number, this value is 22. -

Webfaction User Guide
WebFaction User Guide WebFaction is a service of Paragon Internet Group Limited CONTENTS 1 Introduction 3 1.1 Services..................................................3 1.2 The Complete System..........................................4 2 The Control Panel 5 2.1 Log in to the Control Panel.......................................5 2.2 Change Your Control Panel Password..................................5 2.3 What to Do About a Lost Password...................................6 2.4 Two-Step Login.............................................6 3 Finding Details About Your Server9 3.1 Finding Your Server’s Name.......................................9 3.2 Finding Your Server’s Operating System................................9 3.3 Finding Your Server’s IP Address.................................... 10 4 Accessing Your Data 11 4.1 Connecting with SSH.......................................... 11 4.2 Connecting with FTP........................................... 14 4.3 Changing Your FTP or SSH Password.................................. 14 4.4 Additional Users............................................. 15 4.5 Backups................................................. 16 5 Accounts 17 5.1 Plans and Services............................................ 17 5.2 Communicating with WebFaction.................................... 18 5.3 Payments................................................. 19 5.4 Affiliate Program............................................. 23 5.5 Canceling Your Account......................................... 24 6 Domains 25 6.1 Getting -

Security Analysis of Browser Extension Concepts
Saarland University Faculty of Natural Sciences and Technology I Department of Computer Science Bachelor's thesis Security Analysis of Browser Extension Concepts A comparison of Internet Explorer 9, Safari 5, Firefox 8, and Chrome 14 submitted by Karsten Knuth submitted January 14, 2012 Supervisor Prof. Dr. Michael Backes Advisors Raphael Reischuk Sebastian Gerling Reviewers Prof. Dr. Michael Backes Dr. Matteo Maffei Statement in Lieu of an Oath I hereby confirm that I have written this thesis on my own and that I have not used any other media or materials than the ones referred to in this thesis. Saarbr¨ucken, January 14, 2012 Karsten Knuth Declaration of Consent I agree to make both versions of my thesis (with a passing grade) accessible to the public by having them added to the library of the Computer Science Department. Saarbr¨ucken, January 14, 2012 Karsten Knuth Acknowledgments First of all, I thank Professor Dr. Michael Backes for giving me the chance to write my bachelor's thesis at the Information Security & Cryptography chair. During the making of this thesis I have gotten a deeper look in a topic which I hope to be given the chance to follow up in my upcoming academic career. Furthermore, I thank my advisors Raphael Reischuk, Sebastian Gerling, and Philipp von Styp-Rekowsky for supporting me with words and deeds during the making of this thesis. In particular, I thank the first two for bearing with me since the release of my topic. My thanks also go to Lara Schneider and Michael Zeidler for offering me helpful advice. -

Firefox Hacks Is Ideal for Power Users Who Want to Maximize The
Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader Firefox Hacks is ideal for power users who want to maximize the • Reviews effectiveness of Firefox, the next-generation web browser that is quickly • Errata gaining in popularity. This highly-focused book offers all the valuable tips • Academic and tools you need to enjoy a superior and safer browsing experience. Learn how to customize its deployment, appearance, features, and functionality. Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader • Reviews • Errata • Academic Copyright Credits About the Author Contributors Acknowledgments Preface Why Firefox Hacks? How to Use This Book How This Book Is Organized Conventions Used in This Book Using Code Examples Safari® Enabled How to Contact Us Got a Hack? Chapter 1. Firefox Basics Section 1.1. Hacks 1-10 Section 1.2. Get Oriented Hack 1. Ten Ways to Display a Web Page Hack 2. Ten Ways to Navigate to a Web Page Hack 3. Find Stuff Hack 4. Identify and Use Toolbar Icons Hack 5. Use Keyboard Shortcuts Hack 6. Make Firefox Look Different Hack 7. Stop Once-Only Dialogs Safely Hack 8. Flush and Clear Absolutely Everything Hack 9. Make Firefox Go Fast Hack 10. Start Up from the Command Line Chapter 2. Security Section 2.1. Hacks 11-21 Hack 11. Drop Miscellaneous Security Blocks Hack 12. Raise Security to Protect Dummies Hack 13. Stop All Secret Network Activity Hack 14. -

1 How to FTP to LIONS Contents
How To FTP To LIONS Page 1 1 How To FTP To LIONS — last modified 2017/09/18 14:15:17 — Contents 1 How To FTP To LIONS1 1.1 Abstract.....................................1 1.2 Some FTP Terminology............................1 1.3 How to use FTP................................1 1.3.1 Graphical FTP clients........................2 1.3.2 Command line FTP..........................2 1.4 Useful FTP Commands.............................6 1.5 Web FTP Tutorial...............................7 1.1 Abstract This document explains how to use the File Transfer Protocol (FTP), one of the standard methods for copying files from one machine onto another across the Internet. FTPis in common use for downloading data/programs from servers and uploading Web sites. Please note that this document assumes you are completely familiar with using your computer and operating system, and that you know and understand files, folders (di- rectories), Web sites, URLs, and usernames/passwords. 1.2 Some FTP Terminology When using FTP, there are two software packages which are involved: The FTP Server - this is software that is running on the remote site that you are trying to send files to or retrieve files from. The FTP Client - this is software that you run on your local desktop to communicate with the FTP Server. There are two ways to let the FTP server know who you are: “Authenticated” login - when the FTP client asks for your user name and password, you enter your LIONS user name and password. Once both are validated, you are given read and write access to files on the server. Date: 2017/09/18 14:15:17 Revision: 1.1 How To FTP To LIONS Page 2 “Anonymous” login - this is read-only access to certain public areas on the FTP server, usually located in the directory “/pub”. -

* His Is the Original Ubuntuguide. You Are Free to Copy This Guide but Not to Sell It Or Any Derivative of It. Copyright Of
* his is the original Ubuntuguide. You are free to copy this guide but not to sell it or any derivative of it. Copyright of the names Ubuntuguide and Ubuntu Guide reside solely with this site. This guide is neither sold nor distributed in any other medium. Beware of copies that are for sale or are similarly named; they are neither endorsed nor sanctioned by this guide. Ubuntuguide is not associated with Canonical Ltd nor with any commercial enterprise. * Ubuntu allows a user to accomplish tasks from either a menu-driven Graphical User Interface (GUI) or from a text-based command-line interface (CLI). In Ubuntu, the command-line-interface terminal is called Terminal, which is started: Applications -> Accessories -> Terminal. Text inside the grey dotted box like this should be put into the command-line Terminal. * Many changes to the operating system can only be done by a User with Administrative privileges. 'sudo' elevates a User's privileges to the Administrator level temporarily (i.e. when installing programs or making changes to the system). Example: sudo bash * 'gksudo' should be used instead of 'sudo' when opening a Graphical Application through the "Run Command" dialog box. Example: gksudo gedit /etc/apt/sources.list * "man" command can be used to find help manual for a command. For example, "man sudo" will display the manual page for the "sudo" command: man sudo * While "apt-get" and "aptitude" are fast ways of installing programs/packages, you can also use the Synaptic Package Manager, a GUI method for installing programs/packages. Most (but not all) programs/packages available with apt-get install will also be available from the Synaptic Package Manager. -

C4C Lubuntu 16.04.4 Respin User Guide & Manual
C4C Lubuntu 16.04.4 ReSpin User Guide & Manual C4C Lubuntu 16.04.4 ReSpin User Guide & Manual About Your Christian Operating System The C4C Lubuntu 16.04.4 ReSpin User Guide & Manual is Copyright © 2018 Computers4Christians. Computers4Christians accepts no responsibility for the accuracy, or use, of the information presented in the guide for any purpose and makes no commitment as to support for the computers, computer equipment and/or software, files or data it gives away. Only the Bible is infallible. TABLE OF CONTENTS C4C Lubuntu 16.04.4 ReSpin User Guide & Manual Table of Contents ABOUT , C4C, Statement of Faith, Disclaimer/Copyright Information.............................................3 Artistic License 2.0.................................................................................................................... 4 Christian Purpose [and Objectives], Secular Purpose, Linux, Chapters......................................6 Biblical Purpose, Why Free, Witness..........................................................................................7 C4C Lubuntu ReSpin................................................................................................................. 8 BEGIN........................................................................................................................................... 9 Update (Apt, Software Updater, Apt-url, GDebi, LSC, Snap, Synaptic).....................................13 Deleting Files (Empty Trash, Shift+Delete)..............................................................................18 -

Zoology.Ufl.Edu/Zgsa/Gradforum.Html
Introduction to Webdesign Grad Forum October 17th 2008 François Michonneau > What's a website? › HTML: HyperText Markup Language > What's a website? › Server › Web Browser » Computer: where files » Mozilla Firefox are stored » MS Internet Explorer » Software: handles » Safari request from users » Opera server user > What can you put on a web page? › Text › Images › For everything else, you need plug-ins » Adobe PDF » Adobe Flash » Java » ... › Static vs dynamic > What is an URL? › URL: Uniform Resource Locator › Structure of an URL » http://zoology.ufl.edu/zgsa/gradforum.html > What is an URL? › Structure of an URL » http://zoology.ufl.edu/zgsa/gradforum.html Main domain > What is an URL? › Structure of an URL » http://zoology.ufl.edu/zgsa/gradforum.html Sub domain > What happens when you type an URL? › Structure of an URL » http://zoology.ufl.edu/zgsa/gradforum.html Directory File > What is an URL? › Structure of an URL » http://zoology.ufl.edu/zgsa/gradforum.html Protocol > What is an URL? › Structure of an URL » http://zoology.ufl.edu/zgsa/gradforum.html What is your Where is the Which file on this computer computer? computer? supposed to do with this file? Physical location http://64.233.187.99/ equivalent to http://www.google.com > What is an URL? › Case sensitivity » http://zoology.ufl.edu/zgsa/gradforum.html Case insensitive Case sensitive http://ZOolOgY.UFl.EDU/zgsa/gradforum.html > Fonts › Fonts MUST be on the hard-disk of your visitors › Three types of fonts » Serif: Times New Roman, Georgia » Sans-serif: Arial, Verdana, Trebuchet » Monospace: Courier › Use styles to provide alternative fonts > Colors › Use contrast › Be sober, things to avoid: ex1, ex2, ex3 › No blinking/animations › About 10% of men are colorblind.. -
![CIT190 [1993 1401]: Course Syllabus - Teaching/Learning Contract for CIT 190](https://docslib.b-cdn.net/cover/5036/cit190-1993-1401-course-syllabus-teaching-learning-contract-for-cit-190-5275036.webp)
CIT190 [1993 1401]: Course Syllabus - Teaching/Learning Contract for CIT 190
CIT190 [1993 1401]: Course syllabus - teaching/learning contract for CIT 190 https://elearn.nmc.edu/mod/page/view.php?id=671932 CIT 190 JavaScript Programming Syllabus: Fall 2013 Instructor contact information Name: Jeff Straw Phone: (231) 995-1908 Office: JB121 email: [email protected] Blog: http://jstraw.blogspot.com/ Fall 2013 office hours are in my office (JB121) except where noted: Mon and Wed 9:00 - 9:30 am Mon and Wed 11:15 - 11:45 am Mon and Wed 2:30 - 3:00 pm in JB202 Tue 2:30 - 3:10 pm in JB217 Tue 4:10 - 5:00 pm in JB217 Thu 2:30 - 3:00 pm Other times are available by arrangement. Appointments are not necessary but are always welcome - I often help another student in my office, in a classroom, or in the JB204 lab during office and lab hours. Please email or leave a voice message if you have trouble reaching me. Learning outcomes Successful students will: Recognize and understand JavaScript syntax and semantics (foundational knowledge) Design, develop, test, and document c ustom JavaScript scripts (application) Integrate JavaScript automation scripts into a variety of predefined and new business and personal web sites (integration) Discover personal interest in becoming a web site developer (human dimension: self) Discover power of JavaScript to communicate passion and to add appeal to web sites (caring) Learn to trust oneself to discover web programming techniques and solutions (learning how to learn) Prerequisites CIT 190 is a web programming course. You are expected to have successfully completed two NMC programming-related courses: 1. -

Analyzing Information Flow in Javascript-Based Browser Extensions
Please do not remove this page Analyzing Information Flow in Javascript-based Browser Extensions Dhawan, Mohan; Ganapathy, Vinod https://scholarship.libraries.rutgers.edu/discovery/delivery/01RUT_INST:ResearchRepository/12643416230004646?l#13643522920004646 Dhawan, M., & Ganapathy, V. (2009). Analyzing Information Flow in Javascript-based Browser Extensions. Rutgers University. https://doi.org/10.7282/T3TT4VCM This work is protected by copyright. You are free to use this resource, with proper attribution, for research and educational purposes. Other uses, such as reproduction or publication, may require the permission of the copyright holder. Downloaded On 2021/09/25 16:45:03 -0400 Rutgers University DCS Technical Report 648, April 2009 Analyzing Information Flow in JavaScript-based Browser Extensions Mohan Dhawan and Vinod Ganapathy Department of Computer Science Rutgers, The State University of New Jersey Abstract Flash players, ActiveX), browser helper objects (BHOs, e.g., toolbars) and add-ons. JavaScript-based browser extensions (JSEs) enhance This paper concerns JavaScript-based browser ex- the core functionality of web browsers by improving tensions (JSEs). Such extensions are written primarily their look and feel, and are widely available for com- in JavaScript, and are widely available and immensely modity browsers. To enable a rich set of functionalities, popular (as “add-ons”) for Firefox [4] and related tools, browsers typically execute JSEs with elevated privileges. such as Thunderbird. Notable examples of JSEs for For example, unlike JavaScript code in a web applica- Firefox include Greasemonkey [5], which allows user- tion, code in a JSE is not constrained by the same-origin defined scripts to customize how web pages are ren- policy. -

Hacking Firefox : More Than 150 Hacks, Mods, and Customizations
01_596500 ffirs.qxd 6/30/05 2:34 PM Page iii Hacking Firefox™ More Than 150 Hacks, Mods, and Customizations Mel Reyes 01_596500 ffirs.qxd 6/30/05 2:34 PM Page ii 01_596500 ffirs.qxd 6/30/05 2:34 PM Page i Hacking Firefox™ 01_596500 ffirs.qxd 6/30/05 2:34 PM Page ii 01_596500 ffirs.qxd 6/30/05 2:34 PM Page iii Hacking Firefox™ More Than 150 Hacks, Mods, and Customizations Mel Reyes 01_596500 ffirs.qxd 6/30/05 2:34 PM Page iv Hacking Firefox™: More Than 150 Hacks, Mods, and Customizations Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2005 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN-13: 978-0-7645-9650-6 ISBN-10: 0-7645-9650-0 Manufactured in the United States of America 10987654321 1B/SR/QX/QV/IN No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permission should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions.