Onrisc User Manual 2 Contents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Embedded Linux Systems with the Yocto Project™
OPEN SOURCE SOFTWARE DEVELOPMENT SERIES Embedded Linux Systems with the Yocto Project" FREE SAMPLE CHAPTER SHARE WITH OTHERS �f, � � � � Embedded Linux Systems with the Yocto ProjectTM This page intentionally left blank Embedded Linux Systems with the Yocto ProjectTM Rudolf J. Streif Boston • Columbus • Indianapolis • New York • San Francisco • Amsterdam • Cape Town Dubai • London • Madrid • Milan • Munich • Paris • Montreal • Toronto • Delhi • Mexico City São Paulo • Sidney • Hong Kong • Seoul • Singapore • Taipei • Tokyo Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the publisher was aware of a trademark claim, the designations have been printed with initial capital letters or in all capitals. The author and publisher have taken care in the preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information or programs contained herein. For information about buying this title in bulk quantities, or for special sales opportunities (which may include electronic versions; custom cover designs; and content particular to your business, training goals, marketing focus, or branding interests), please contact our corporate sales depart- ment at [email protected] or (800) 382-3419. For government sales inquiries, please contact [email protected]. For questions about sales outside the U.S., please contact [email protected]. Visit us on the Web: informit.com Cataloging-in-Publication Data is on file with the Library of Congress. -

An Introduction to Qt 4
AnAn IntroductionIntroduction toto QtQt 44 Jason Trent [email protected] OOuutltliinnee . Why Trolltech? . Why Qt? . Qt 4 Widgets, Datatypes, and Structures . Qt Designer . qmake . Qt without C++ . Demo WWhhyy TTrroolllltetecchh?? .. QQtt aanndd QQttooppiiaa CCoorree aarree OOppeenn SSoouurrccee .. SSuuppppoorrtteedd bbyy mmuullttii--mmiilllliioonn ddoollllaarr ccoommppaannyy WWhhyy QQt?t? .. MMuullttii--ppllaattffoorrmm – No “virtual machines” or emulation layers – Native compilation for Windows, X11, and Mac • Utilizes core OS technologies (Core, Aero, …) – Extensions - ActiveQt, Motif Migration WWhhyy QQt?t? Over 400 C++ Classes . Not just a GUI toolkit – File handling – Networking – Process handling – Threading – Database access – Event loop processing – XML processing – OpenGL integration – and beyond WWhhyy QQt?t? .. IInntteerrnnaattiioonnaalliizzaattiioonn – Built in support for Unicode and Translation • Language and font aware layouts • Bidirectional font support • Mixed-international interface .. SSeeee QQtt LLiinngguuiisstt ffoorr mmoorree WWhhyy QQt?t? .. NNoott jjuusstt mmuuttllii--ppllaattiiffoorrmm,, mmuullttii--aarrcchhiitteeccttuurree .. QQttooppiiaa CCoorree 44 SSeerriieess – Support for embedded devices • Cell phones, PDAs, etc… – Supports Qt4 widgets with little to no code change QQWWiiddggeett TThhee mmeeeekk mmaayy iinnhheerriitt tthhee eeaarrtthh…… ……bbuutt tthhee eeaarrtthh sshhaallll iinnhheerriitt QQWWiiddggeett QWidget QQtt 44 WWiiddggeetsts .. IInnhheerriitt tthhee aallll--ppoowweerrffuull QQWWiiddggeett .. IInncclluuddee:: -

Qt Framework
About Qt Qt is a framework to develop cross-platform applications. Currently, the supported platforms are Windows, Linux, macOS, Android, iOS, Embedded Linux and some others. Genarally, it means that the programmer may develop the code on one platform but compile, link and run it on another platform. But it also means that Qt needs help: to develop software it must cooperate with development tools on specific platforms, for example in case of Windows with Visual Studio. Qt is well-known for its tools for developing graphical user interfaces (GUI) , but it also provides powerful tools for threads, networking and communication (Bluetooth, serial port, web), 3D graphics, multimedia, SQL databases, etc. Qt has its own Integrated Development Environment (IDE): QtCreator. History: 1991: version 1.0 as cross-platform GUI programming toolkit was developed and implemented by TrollTech (Norway). 2005: version 4.0 was a big step ahead but the compatibility with older versions was lost. 2008: TrollTech was sold to Nokia. 2012: Nokia Qt division was sold to Digia (Finland). 2014: Digia transferred the Qt business to Qt Company. The latest Long Term Support (LTS) version is 5.12. Official website: https://www.qt.io/ Installation The link is https://www.qt.io/download. Select the non-commercial and open source version. It may be possible that you must register yourself creating a new passworded account. Select the latest stable release and the C/C++ development system(s) you are going to use. Tip: the Qt installer proposes to store the stuff in folder C:\Qt. To avoid later complications, agree. -
Connecting with FTP Server
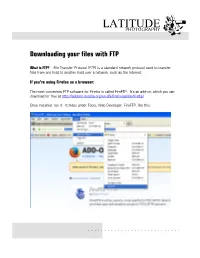
LATITUDEPHOTOGRAPHY Downloading your files with FTP What is FTP?: File Transfer Protocol (FTP) is a standard network protocol used to transfer files from one host to another host over a network, such as the Internet. If you’re using Firefox as a browser: The most convenient FTP software for Firefox is called FireFTP. It’s an add-on, which you can download for free at http://addons.mozilla.org/en-US/firefox/addon/fireftp/ Once installed, run it. It hides under Tools, Web Developer, FireFTP, like this: . Firefox will start a new tab right in the browser. On the left, you will have to select QuickConnect from a dropdown list. And a window will popup. Fill in all the fields, with the your login information. Leave the Anonymous box uncheck. Press Connect. 1. Enter ftp.latitudephotography.com here 2. Enter your login name here 3. Password goes here 4. Click here to connect The FTP software will connect and look like this: YOUR Computer 5. Select folder YOUR project folder on the LATITUDE Server Don’t worry about this window The windows which you will use are the middle four. YOUR computer on the left, the LATITUDE computer on the right. If you are looking for High Resolution files from a shoot on January 11, 2013. In the right hand window double click the folder, in this case 2013-01-11. The folder will open and you will now have to select the “High Resolution JPG images” folder. You may also see a “High Resolution PNG images” or “RAW images” folders depending on the project. -

FTP Instructions for Shtetlinks
SFTP Instructions for KehilaLinks SFTP stands for Secure File Transfer Protocol and is a simple way of moving files from your computer to the KehilaLinks server. 1. SFTP Access a. Your KehilaLinks SFTP Username and Password will bring you directly into the folder assigned to your site. You will see an empty space when you enter the SFTP site; the folder is not visible. b. If you manage more than one KehilaLink site, you will be provided a single UserName and Password. This Logon will bring you to a listing of KehilaLinks site folders. Instructions for accessing multiple sites: i. When you logon, you will be on a site with multiple KehilaLink site folders. ii. Double click on the folder that you will be working with. You can then browse, download and upload as needed. Follow instructions in 2 below for downloading and uploading. iii. To go to another of the sites that you manage, return to the KehilaLinks site folders screen and select the next site that you will work on. iv. If you go to a site that you are not authorized for, you can browse the folder, but will get an error message when you try to upload. 2. You can use FTP software which can be downloaded free from such sites as www.download.com or www.cnet.com/ . I will not recommend one package over another. If you use FTP software, the URL to use to SFTP is Sftp.jewishgen.org You will be provided with a Login/Username and a Password. If the software requests a port number, this value is 22. -

Netinfo 2009-06-11 Netinfo 2009-06-11
Netinfo 2009-06-11 Netinfo 2009-06-11 Microsoft släppte 2009-06-09 tio uppdateringar som täpper till 31 stycken säkerhetshål i bland annat Windows, Internet Explorer, Word, Excel, Windows Search. 18 av buggfixarna är märkta som kritiska och elva av dem är märkta som viktiga, uppdateringarna finns för både servrar och arbetsstationer. Säkerhetsuppdateringarna finns tillgängliga på Windows Update. Den viktigaste säkerhetsuppdateringen av de som släpptes är den för Internet Explorer 8. Netinfo 2009-06-11 Security Updates available for Adobe Reader and Acrobat Release date: June 9, 2009 Affected software versions Adobe Reader 9.1.1 and earlier versions Adobe Acrobat Standard, Pro, and Pro Extended 9.1.1 and earlier versions Severity rating Adobe categorizes this as a critical update and recommends that users apply the update for their product installations. These vulnerabilities would cause the application to crash and could potentially allow an attacker to take control of the affected system. Netinfo 2009-06-11 SystemRescueCd Description: SystemRescueCd is a Linux system on a bootable CD-ROM for repairing your system and recovering your data after a crash. It aims to provide an easy way to carry out admin tasks on your computer, such as creating and editing the partitions of the hard disk. It contains a lot of system tools (parted, partimage, fstools, ...) and basic tools (editors, midnight commander, network tools). It is very easy to use: just boot the CDROM. The kernel supports most of the important file systems (ext2/ext3/ext4, reiserfs, reiser4, btrfs, xfs, jfs, vfat, ntfs, iso9660), as well as network filesystems (samba and nfs). -

System Rescue CD Als Rettungs-Stick
PRAXIS SYSTEM-RESCUE-STICK System Rescue CD als Rettungs-Stick Die System Rescue CD 2.2.0 macht Ihren USB-Stick zum universellen Datenretter. Nach einem System-Crash sichert der Stick wichtige Dateien noch auf CD, USB-Festplatte oder einen FTP-Speicher. ie System Rescue CD 2.2.0 ist Das HP-Tool erkennt automatisch ei- D eine auf Linux basierende nen angesteckten USB-Stick und Notfall-CD (kos tenlos, www.sysresc zeigt ihn unter “Device“ an. Falls er cd.org und auf ). Das kompakte nicht automatisch erscheint, dann Rettungssystem lässt sich in wenigen wählen Sie ihn im Auswahlmenü ma- Minuten auf einem bootfähigen nuell aus. Anschliessend aktivieren USB-Stick installieren, enthält zahl- Sie bei “File system“ das Dateisystem reiche Rettungs-Tools und sichert “FAT32“. Deaktivieren Sie alle “For- wichtige Daten auf beliebigen mat options“ und beginnen Sie dann Speichermedien (Bild A). die Formatierung des Sticks mit “Start, Ja“. Rettungs-Stick erstellen Tipp: Wenn Sie einen U3-Stick ver- wenden wollen, dann entfernen Sie Ein komfortables Windows-Tool führt zuvor den U3-Launcher mit dem Tool Sie Schritt für Schritt durch die Konfi- U3 Launchpad Removal (kostenlos, guration und Installation Ihres Sys - http://u3.sandisk.com und auf ). tem-Rescue-Sticks. System Rescue CD 2.2.0: Die Rettungs-CD mit grafischer Oberfläche bootet auch USB-Installer starten USB-Stick vorbereiten vom USB-Stick (Bild A) Die Installation der System Rescue Sichern Sie zunächst alle Daten Ihres CD 2.2.0 auf einem USB-Stick über- USB-Sticks, da diese sonst während der For- Support/SoftwareDescription.jsp?swItem=ob- nimmt der System Rescue CD USB Installer matierung des Datenträgers verloren gehen. -

Pyqt for Autodesk Maya 2015 64Bit
PyQt for Autodesk Maya 2015 64bit Written by Cyrille Fauvel – Autodesk Developer Network (April 2013) Updated by Vijaya Prakash – Autodesk Developer Network (April 2014) Additional Qt instructions available here - http://around-the-corner.typepad.com/adn/2014/04/building-sip-and-pyqt-for-maya-2015.html Building SIP, and PyQt for Maya 2015 PyQt [http://www.riverbankcomputing.co.uk] is a python binding to the Qt library. Because Maya uses Qt internally, you can use the PyQt modules in Maya python scripts to create custom UI. PyQt does not have the same licensing as Maya, Qt, or Python. Please consult the PyQt website for information about licensing for PyQt. Download PyQt: http://www.riverbankcomputing.com/static/Downloads/PyQt4/ Download SIP: http://www.riverbankcomputing.com/software/sip/download The following are instructions for building a copy of the PyQt modules that have been known to work with Maya. Maya 2015 uses Qt4.8.5 which is binary compatible with the latest version of PyQt - 4.10.4 / SIP - 4.15.5 (at time of writing, April 2014). However, you do not have to use these versions if you prefer using an older version, all you need is to use a version compatible with Qt4.8.5. Note that it’s important to use the Maya modified version of the Qt source code. A copy of the customized Qt 4.8.5 source is available from Autodesk's Open Source web-site (http://www.autodesk.com/lgplsource) and includes text files describing how to configure, build and install Qt for each platform supported by Maya. -

Webfaction User Guide
WebFaction User Guide WebFaction is a service of Paragon Internet Group Limited CONTENTS 1 Introduction 3 1.1 Services..................................................3 1.2 The Complete System..........................................4 2 The Control Panel 5 2.1 Log in to the Control Panel.......................................5 2.2 Change Your Control Panel Password..................................5 2.3 What to Do About a Lost Password...................................6 2.4 Two-Step Login.............................................6 3 Finding Details About Your Server9 3.1 Finding Your Server’s Name.......................................9 3.2 Finding Your Server’s Operating System................................9 3.3 Finding Your Server’s IP Address.................................... 10 4 Accessing Your Data 11 4.1 Connecting with SSH.......................................... 11 4.2 Connecting with FTP........................................... 14 4.3 Changing Your FTP or SSH Password.................................. 14 4.4 Additional Users............................................. 15 4.5 Backups................................................. 16 5 Accounts 17 5.1 Plans and Services............................................ 17 5.2 Communicating with WebFaction.................................... 18 5.3 Payments................................................. 19 5.4 Affiliate Program............................................. 23 5.5 Canceling Your Account......................................... 24 6 Domains 25 6.1 Getting -

1 Australian Synchrotron
EPICS Qt Update Paul Martin 1 Australian Synchrotron • 3GeV, 216m circumference synchrotron • 8 Beamlines • 12 Software Engineers • IMBL – Worlds Widest Beam - MRT Clinical Program – Safety Critical • Melbourne, Australia • Nearest other facilities: Taiwan, Thailand, Japan • 16th Most Urbanized Country • World’s most livable cities • Hosting ICALEPCS in 2015 2 Qt • Qt is a cross-platform application and UI framework for developers using C++ – Windows,OS X, Linux, Embedded Linux, Android, iOS, vxWorks, Win CE, Amiga OS • Open Source (LPGL v2.1) Qt Designer • Trolltech -> Nokia -> Digia, • Development tools: Qt Creator, Qt Designer, Qmake, Qt Linguist, Qt Assistant, Integration into Visual Studio • Rich set of Widgets and other classes (1000+), Qwt (125+) • Very Good Documentation, help, examples • All Qt Objects contain powerful object communication Qt Creator mechanism (Signal+Slots) • GUI Layout widgets • Qt Project: www.qt-project.org 3 EPICS Qt – Team • Started 2009 – Anthony Owen, Andrew Rhyder, Glenn Jackson • Joined 2011 – Andy Starritt • Joined 2012 – Ricardo Fernandez • Joined 2013 – Zai Wang (1 year contract) 4 EPICS Qt – Rapid GUI Development • Adds Channel Access to standard Qt Widgets and Data Classes • Rapid GUI Dev – Drag and Drop EPICS aware components in Qt Designer • Macro Substitutions for PV names and other GUI functions Qt Designer Channel Access running at design time .ui file – presented using QEGui on any platform (windows / linux) 5 EPICS Qt – Other App Types QCaString Qt Creator QCaInteger QCaFloating QCaByteArray -

Kdesrc-Build Script Manual
kdesrc-build Script Manual Michael Pyne Carlos Woelz kdesrc-build Script Manual 2 Contents 1 Introduction 8 1.1 A brief introduction to kdesrc-build . .8 1.1.1 What is kdesrc-build? . .8 1.1.2 kdesrc-build operation ‘in a nutshell’ . .8 1.2 Documentation Overview . .9 2 Getting Started 10 2.1 Preparing the System to Build KDE . 10 2.1.1 Setup a new user account . 10 2.1.2 Ensure your system is ready to build KDE software . 10 2.1.3 Setup kdesrc-build . 12 2.1.3.1 Install kdesrc-build . 12 2.1.3.2 Prepare the configuration file . 12 2.1.3.2.1 Manual setup of configuration file . 12 2.2 Setting the Configuration Data . 13 2.3 Using the kdesrc-build script . 14 2.3.1 Loading project metadata . 14 2.3.2 Previewing what will happen when kdesrc-build runs . 14 2.3.3 Resolving build failures . 15 2.4 Building specific modules . 16 2.5 Setting the Environment to Run Your KDEPlasma Desktop . 17 2.5.1 Automatically installing a login driver . 18 2.5.1.1 Adding xsession support for distributions . 18 2.5.1.2 Manually adding support for xsession . 18 2.5.2 Setting up the environment manually . 19 2.6 Module Organization and selection . 19 2.6.1 KDE Software Organization . 19 2.6.2 Selecting modules to build . 19 2.6.3 Module Sets . 20 2.6.3.1 The basic module set concept . 20 2.6.3.2 Special Support for KDE module sets . -

Security Analysis of Browser Extension Concepts
Saarland University Faculty of Natural Sciences and Technology I Department of Computer Science Bachelor's thesis Security Analysis of Browser Extension Concepts A comparison of Internet Explorer 9, Safari 5, Firefox 8, and Chrome 14 submitted by Karsten Knuth submitted January 14, 2012 Supervisor Prof. Dr. Michael Backes Advisors Raphael Reischuk Sebastian Gerling Reviewers Prof. Dr. Michael Backes Dr. Matteo Maffei Statement in Lieu of an Oath I hereby confirm that I have written this thesis on my own and that I have not used any other media or materials than the ones referred to in this thesis. Saarbr¨ucken, January 14, 2012 Karsten Knuth Declaration of Consent I agree to make both versions of my thesis (with a passing grade) accessible to the public by having them added to the library of the Computer Science Department. Saarbr¨ucken, January 14, 2012 Karsten Knuth Acknowledgments First of all, I thank Professor Dr. Michael Backes for giving me the chance to write my bachelor's thesis at the Information Security & Cryptography chair. During the making of this thesis I have gotten a deeper look in a topic which I hope to be given the chance to follow up in my upcoming academic career. Furthermore, I thank my advisors Raphael Reischuk, Sebastian Gerling, and Philipp von Styp-Rekowsky for supporting me with words and deeds during the making of this thesis. In particular, I thank the first two for bearing with me since the release of my topic. My thanks also go to Lara Schneider and Michael Zeidler for offering me helpful advice.