FTP Instructions for Shtetlinks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IN-BROWSER BLITZ LITERATURE REVIEWS 1 Submitted to Meta
IN-BROWSER BLITZ LITERATURE REVIEWS 1 Submitted to Meta-Psychology. Participate in open peer review by commenting through hypothes.is directly on this preprint. The full editorial process of all articles under review at Meta-Psychology can be found following this link: https://tinyurl.com/mp-submissions You will find this preprint by searching for the first author's name. Writing a Psychological Blitz Literature Review with Nothing but a Browser Bogdan Cocoş1 1Department of Psychology, University of Bucharest Author Note Correspondence regarding this article should be addressed to Bogdan Cocoş, 90 Panduri Road, Sector 5, 050663, Bucharest, Romania. E-mail: [email protected] https://orcid.org/0000-0003-4098-7551 IN-BROWSER BLITZ LITERATURE REVIEWS 2 Abstract The ways so far of writing literature reviews represent valid, but not sufficient, landmarks, connected to the current technological context. In this sense, this article proposes a research method called blitz literature review, as a way to quickly, transparently, and repeatably consult key references in a particular area of interest, seen as a network composed of elements that are indispensable to such a process. The tutorial consists of six steps explained in detail, easy to follow and reproduce, accompanied by publicly available supplementary material. Finally, the possible implications of this research method are discussed, being brought to the fore a general recommendation regarding the optimization of the citizens’ involvement in the efforts and approaches of open scientific research. Keywords: blitz literature review, open access, open science, research methods IN-BROWSER BLITZ LITERATURE REVIEWS 3 Writing a Psychological Blitz Literature Review with Nothing but a Browser Context The term “blitz literature review” refers to an adaptation of the concept of literature review. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -
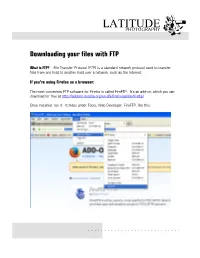
Connecting with FTP Server
LATITUDEPHOTOGRAPHY Downloading your files with FTP What is FTP?: File Transfer Protocol (FTP) is a standard network protocol used to transfer files from one host to another host over a network, such as the Internet. If you’re using Firefox as a browser: The most convenient FTP software for Firefox is called FireFTP. It’s an add-on, which you can download for free at http://addons.mozilla.org/en-US/firefox/addon/fireftp/ Once installed, run it. It hides under Tools, Web Developer, FireFTP, like this: . Firefox will start a new tab right in the browser. On the left, you will have to select QuickConnect from a dropdown list. And a window will popup. Fill in all the fields, with the your login information. Leave the Anonymous box uncheck. Press Connect. 1. Enter ftp.latitudephotography.com here 2. Enter your login name here 3. Password goes here 4. Click here to connect The FTP software will connect and look like this: YOUR Computer 5. Select folder YOUR project folder on the LATITUDE Server Don’t worry about this window The windows which you will use are the middle four. YOUR computer on the left, the LATITUDE computer on the right. If you are looking for High Resolution files from a shoot on January 11, 2013. In the right hand window double click the folder, in this case 2013-01-11. The folder will open and you will now have to select the “High Resolution JPG images” folder. You may also see a “High Resolution PNG images” or “RAW images” folders depending on the project. -

Webfaction User Guide
WebFaction User Guide WebFaction is a service of Paragon Internet Group Limited CONTENTS 1 Introduction 3 1.1 Services..................................................3 1.2 The Complete System..........................................4 2 The Control Panel 5 2.1 Log in to the Control Panel.......................................5 2.2 Change Your Control Panel Password..................................5 2.3 What to Do About a Lost Password...................................6 2.4 Two-Step Login.............................................6 3 Finding Details About Your Server9 3.1 Finding Your Server’s Name.......................................9 3.2 Finding Your Server’s Operating System................................9 3.3 Finding Your Server’s IP Address.................................... 10 4 Accessing Your Data 11 4.1 Connecting with SSH.......................................... 11 4.2 Connecting with FTP........................................... 14 4.3 Changing Your FTP or SSH Password.................................. 14 4.4 Additional Users............................................. 15 4.5 Backups................................................. 16 5 Accounts 17 5.1 Plans and Services............................................ 17 5.2 Communicating with WebFaction.................................... 18 5.3 Payments................................................. 19 5.4 Affiliate Program............................................. 23 5.5 Canceling Your Account......................................... 24 6 Domains 25 6.1 Getting -
11 Fastest Internet Browser for Mac
Fast Web Browser For Mac Chrome Web Browser For Mac Best Browsers Mac Fastest Mac Browser Fast Web Browser For Mac Shortcut Whenever something pops into your mind, you open your browser to do research on it. The browser is an old fashion way of searching for things on the internet, whether you want to buy an accessory or search for a home remedy for common ailments. Chrome Web Browser For Mac With more than 300 million users worldwide, Opera is one of the most secure and used web browsers that is quite compatible with Mac. A few of the features are pop-up blocker, free VPN, fast browsing, unit converters, bookmarks that make it what it is today. Also, the web browser for Mac filters out the website with phishing & malware. The browser gives users a fast browsing experience, powerful rendering, control options, and a lot more customization settings and options. According to the majority of users, this is undoubtedly the fastest web browser for Mac. So, give Google Chrome a try in your MAC and check whether you like it or not. Fast, easy-to-use tools for browsing From password check, dark mode, and the Google address bar, Chrome helps you get things done and stay safe online. Our Top 10 Fastest Web Browsers 2020, cannot be completed without mentioning, Maxthon. It is both a lightweight & private Windows 10 Internet browser. Packed with standard features found in other Best Web browsers, Maxthon offers an advanced bunch of features and tools too that sets it apart. As it is the fastest web browser for Mac and allows you to browse securely, you must give it a try for Mac. -

Giant List of Web Browsers
Giant List of Web Browsers The majority of the world uses a default or big tech browsers but there are many alternatives out there which may be a better choice. Take a look through our list & see if there is something you like the look of. All links open in new windows. Caveat emptor old friend & happy surfing. 1. 32bit https://www.electrasoft.com/32bw.htm 2. 360 Security https://browser.360.cn/se/en.html 3. Avant http://www.avantbrowser.com 4. Avast/SafeZone https://www.avast.com/en-us/secure-browser 5. Basilisk https://www.basilisk-browser.org 6. Bento https://bentobrowser.com 7. Bitty http://www.bitty.com 8. Blisk https://blisk.io 9. Brave https://brave.com 10. BriskBard https://www.briskbard.com 11. Chrome https://www.google.com/chrome 12. Chromium https://www.chromium.org/Home 13. Citrio http://citrio.com 14. Cliqz https://cliqz.com 15. C?c C?c https://coccoc.com 16. Comodo IceDragon https://www.comodo.com/home/browsers-toolbars/icedragon-browser.php 17. Comodo Dragon https://www.comodo.com/home/browsers-toolbars/browser.php 18. Coowon http://coowon.com 19. Crusta https://sourceforge.net/projects/crustabrowser 20. Dillo https://www.dillo.org 21. Dolphin http://dolphin.com 22. Dooble https://textbrowser.github.io/dooble 23. Edge https://www.microsoft.com/en-us/windows/microsoft-edge 24. ELinks http://elinks.or.cz 25. Epic https://www.epicbrowser.com 26. Epiphany https://projects-old.gnome.org/epiphany 27. Falkon https://www.falkon.org 28. Firefox https://www.mozilla.org/en-US/firefox/new 29. -

Security Analysis of Browser Extension Concepts
Saarland University Faculty of Natural Sciences and Technology I Department of Computer Science Bachelor's thesis Security Analysis of Browser Extension Concepts A comparison of Internet Explorer 9, Safari 5, Firefox 8, and Chrome 14 submitted by Karsten Knuth submitted January 14, 2012 Supervisor Prof. Dr. Michael Backes Advisors Raphael Reischuk Sebastian Gerling Reviewers Prof. Dr. Michael Backes Dr. Matteo Maffei Statement in Lieu of an Oath I hereby confirm that I have written this thesis on my own and that I have not used any other media or materials than the ones referred to in this thesis. Saarbr¨ucken, January 14, 2012 Karsten Knuth Declaration of Consent I agree to make both versions of my thesis (with a passing grade) accessible to the public by having them added to the library of the Computer Science Department. Saarbr¨ucken, January 14, 2012 Karsten Knuth Acknowledgments First of all, I thank Professor Dr. Michael Backes for giving me the chance to write my bachelor's thesis at the Information Security & Cryptography chair. During the making of this thesis I have gotten a deeper look in a topic which I hope to be given the chance to follow up in my upcoming academic career. Furthermore, I thank my advisors Raphael Reischuk, Sebastian Gerling, and Philipp von Styp-Rekowsky for supporting me with words and deeds during the making of this thesis. In particular, I thank the first two for bearing with me since the release of my topic. My thanks also go to Lara Schneider and Michael Zeidler for offering me helpful advice. -

Web Browsers
WEB BROWSERS Page 1 INTRODUCTION • A Web browser acts as an interface between the user and Web server • Software application that resides on a computer and is used to locate and display Web pages. • Web user access information from web servers, through a client program called browser. • A web browser is a software application for retrieving, presenting, and traversing information resources on the World Wide Web Page 2 FEATURES • All major web browsers allow the user to open multiple information resources at the same time, either in different browser windows or in different tabs of the same window • A refresh and stop buttons for refreshing and stopping the loading of current documents • Home button that gets you to your home page • Major browsers also include pop-up blockers to prevent unwanted windows from "popping up" without the user's consent Page 3 COMPONENTS OF WEB BROWSER 1. User Interface • this includes the address bar, back/forward button , bookmarking menu etc 1. Rendering Engine • Rendering, that is display of the requested contents on the browser screen. • By default the rendering engine can display HTML and XML documents and images Page 4 HISTROY • The history of the Web browser dates back in to the late 1980s, when a variety of technologies laid the foundation for the first Web browser, WorldWideWeb, by Tim Berners-Lee in 1991. • Microsoft responded with its browser Internet Explorer in 1995 initiating the industry's first browser war • Opera first appeared in 1996; although it have only 2% browser usage share as of April 2010, it has a substantial share of the fast-growing mobile phone Web browser market, being preinstalled on over 40 million phones. -

Why Websites Can Change Without Warning
Why Websites Can Change Without Warning WHY WOULD MY WEBSITE LOOK DIFFERENT WITHOUT NOTICE? HISTORY: Your website is a series of files & databases. Websites used to be “static” because there were only a few ways to view them. Now we have a complex system, and telling your webmaster what device, operating system and browser is crucial, here’s why: TERMINOLOGY: You have a desktop or mobile “device”. Desktop computers and mobile devices have “operating systems” which are software. To see your website, you’ll pull up a “browser” which is also software, to surf the Internet. Your website is a series of files that needs to be 100% compatible with all devices, operating systems and browsers. Your website is built on WordPress and gets a weekly check up (sometimes more often) to see if any changes have occured. Your site could also be attacked with bad files, links, spam, comments and other annoying internet pests! Or other components will suddenly need updating which is nothing out of the ordinary. WHAT DOES IT LOOK LIKE IF SOMETHING HAS CHANGED? Any update to the following can make your website look differently: There are 85 operating systems (OS) that can update (without warning). And any of the most popular roughly 7 browsers also update regularly which can affect your site visually and other ways. (Lists below) Now, with an OS or browser update, your site’s 18 website components likely will need updating too. Once website updates are implemented, there are currently about 21 mobile devices, and 141 desktop devices that need to be viewed for compatibility. -

Firefox Hacks Is Ideal for Power Users Who Want to Maximize The
Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader Firefox Hacks is ideal for power users who want to maximize the • Reviews effectiveness of Firefox, the next-generation web browser that is quickly • Errata gaining in popularity. This highly-focused book offers all the valuable tips • Academic and tools you need to enjoy a superior and safer browsing experience. Learn how to customize its deployment, appearance, features, and functionality. Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader • Reviews • Errata • Academic Copyright Credits About the Author Contributors Acknowledgments Preface Why Firefox Hacks? How to Use This Book How This Book Is Organized Conventions Used in This Book Using Code Examples Safari® Enabled How to Contact Us Got a Hack? Chapter 1. Firefox Basics Section 1.1. Hacks 1-10 Section 1.2. Get Oriented Hack 1. Ten Ways to Display a Web Page Hack 2. Ten Ways to Navigate to a Web Page Hack 3. Find Stuff Hack 4. Identify and Use Toolbar Icons Hack 5. Use Keyboard Shortcuts Hack 6. Make Firefox Look Different Hack 7. Stop Once-Only Dialogs Safely Hack 8. Flush and Clear Absolutely Everything Hack 9. Make Firefox Go Fast Hack 10. Start Up from the Command Line Chapter 2. Security Section 2.1. Hacks 11-21 Hack 11. Drop Miscellaneous Security Blocks Hack 12. Raise Security to Protect Dummies Hack 13. Stop All Secret Network Activity Hack 14. -

Software Management Full Installers Guide
Software Management Full Installers Guide Supported Platforms and Applications | Q1 2020 Software Management Full Installers Guide Release 9.5 | Q1 2020 www.kaseya.com 2 Software Management Full Installers Guide Release 9.5 | Q1 2020 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya’s “Click-Accept” EULATOS as updated from time to time by Kaseya at http://www.kaseya.com/legal.aspx. If Customer does not agree with the Agreement, please do not install, use or purchase any Software and Services from Kaseya as continued use of the Software or Services indicates Customer’s acceptance of the Agreement. www.kaseya.com Software Management Full Installers 3 Guide Release 9.5 | Q1 2020 Contents Installers Available 4 www.kaseya.com 4 Software Management Full Installers Guide Release 9.5 | Q1 2020 Installers Available Title Vendor URL 7-Zip File Archiver (Full Install) for Igor Pavlov http://www.7-zip.org/ Windows Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (Full Install) for Mac Systems, Inc OS X Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (de-DE) (Full Install) Systems, Inc for Windows Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (en-US) (Full Install) Systems, Inc for Windows Adobe Acrobat Reader DC Adobe http://acrobat.adobe.com/us/en/products/pdf-reader.html (Continuous) (es-ES) (Full Install) Systems, Inc for Windows -

Interfaz USB De Red Para Acceso Seguro Basada En Raspberry Pi
Escola Tècnica Superior d’Enginyeria Informàtica Universitat Politècnica de València Interfaz USB de red para acceso seguro basada en Raspberry Pi Trabajo Fin de Grado Grado en Ingeniería Informática Autor: Jornet Calomarde, Raúl Tutor: Ripoll Ripoll, José Ismael Curso 2017-2018 Interfaz USB de red para acceso seguro basada en Raspberry Pi 2 Resumen El proyecto aborda el desarrollo de un dispositivo hardware basado en «Raspberry Pi Zero W» que sirve de punto de acceso a red y que proporciona diversas herramientas orientadas a la seguridad, tales como: firewall, control de intrusos, configuración de seguridad inalámbrica, proxies o auditoría de no- dos. La conectividad del dispositivo con el ordenador personal se establecerá únicamente mediante un cable USB a micro USB y será compatible con la mayoría de sistemas. El proyecto estará basado íntegramente en Raspbian (con posibles modificaciones del kernel) y he- rramientas libres y será publicado con una licencia GPL3. Palabras clave Periférico, Seguridad, Red, "Raspberry Pi", Hardware, GNU/Linux 3 Interfaz USB de red para acceso seguro basada en Raspberry Pi 4 Índice 1. Introducción...........................................................................................................................................7 1.1. Motivación......................................................................................................................................7 1.2. Objetivos........................................................................................................................................7