9Lesson 9: Internet Services and Tools for Business
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

THINC: a Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices
THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2011 c 2011 Ricardo A. Baratto This work may be used in accordance with Creative Commons, Attribution-NonCommercial-NoDerivs License. For more information about that license, see http://creativecommons.org/licenses/by-nc-nd/3.0/. For other uses, please contact the author. ABSTRACT THINC: A Virtual and Remote Display Architecture for Desktop Computing and Mobile Devices Ricardo A. Baratto THINC is a new virtual and remote display architecture for desktop computing. It has been designed to address the limitations and performance shortcomings of existing remote display technology, and to provide a building block around which novel desktop architectures can be built. THINC is architected around the notion of a virtual display device driver, a software-only component that behaves like a traditional device driver, but instead of managing specific hardware, enables desktop input and output to be intercepted, manipulated, and redirected at will. On top of this architecture, THINC introduces a simple, low-level, device-independent representation of display changes, and a number of novel optimizations and techniques to perform efficient interception and redirection of display output. This dissertation presents the design and implementation of THINC. It also intro- duces a number of novel systems which build upon THINC's architecture to provide new and improved desktop computing services. The contributions of this dissertation are as follows: • A high performance remote display system for LAN and WAN environments. -
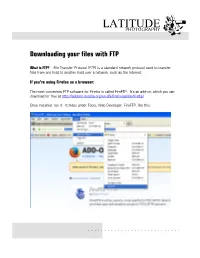
Connecting with FTP Server
LATITUDEPHOTOGRAPHY Downloading your files with FTP What is FTP?: File Transfer Protocol (FTP) is a standard network protocol used to transfer files from one host to another host over a network, such as the Internet. If you’re using Firefox as a browser: The most convenient FTP software for Firefox is called FireFTP. It’s an add-on, which you can download for free at http://addons.mozilla.org/en-US/firefox/addon/fireftp/ Once installed, run it. It hides under Tools, Web Developer, FireFTP, like this: . Firefox will start a new tab right in the browser. On the left, you will have to select QuickConnect from a dropdown list. And a window will popup. Fill in all the fields, with the your login information. Leave the Anonymous box uncheck. Press Connect. 1. Enter ftp.latitudephotography.com here 2. Enter your login name here 3. Password goes here 4. Click here to connect The FTP software will connect and look like this: YOUR Computer 5. Select folder YOUR project folder on the LATITUDE Server Don’t worry about this window The windows which you will use are the middle four. YOUR computer on the left, the LATITUDE computer on the right. If you are looking for High Resolution files from a shoot on January 11, 2013. In the right hand window double click the folder, in this case 2013-01-11. The folder will open and you will now have to select the “High Resolution JPG images” folder. You may also see a “High Resolution PNG images” or “RAW images” folders depending on the project. -

Third-Party License Acknowledgments
Symantec Privileged Access Manager Third-Party License Acknowledgments Version 3.4.3 Symantec Privileged Access Manager Third-Party License Acknowledgments Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. Copyright © 2021 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. 2 Symantec Privileged Access Manager Third-Party License Acknowledgments Contents Activation 1.1.1 ..................................................................................................................................... 7 Adal4j 1.1.2 ............................................................................................................................................ 7 AdoptOpenJDK 1.8.0_282-b08 ............................................................................................................ 7 Aespipe 2.4e aespipe ........................................................................................................................ -
Free Open Source Vnc
Free open source vnc click here to download TightVNC - VNC-Compatible Remote Control / Remote Desktop Software. free for both personal and commercial usage, with full source code available. TightVNC - VNC-Compatible Remote Control / Remote Desktop Software. It's completely free but it does not allow integration with closed-source products. UltraVNC: Remote desktop support software - Remote PC access - remote desktop connection software - VNC Compatibility - FileTransfer - Encryption plugins - Text chat - MS authentication. This leading-edge, cloud-based program offers Remote Monitoring & Management, Remote Access &. Popular open source Alternatives to VNC Connect for Linux, Windows, Mac, Self- Hosted, BSD and Free Open Source Mac Windows Linux Android iPhone. Download the original open source version of VNC® remote access technology. Undeniably, TeamViewer is the best VNC in the market. Without further ado, here are 8 free and some are open source VNC client/server. VNC remote access software, support server and viewer software for on demand remote computer support. Remote desktop support software for remote PC control. Free. All VNCs Start from the one piece of source (See History of VNC), and. TigerVNC is a high- performance, platform-neutral implementation of VNC (Virtual Network Computing), Besides the source code we also provide self-contained binaries for bit and bit Linux, installers for Current list of open bounties. VNC (Virtual Network Computing) software makes it possible to view and fully- interact with one computer from any other computer or mobile. Find other free open source alternatives for VNC. Open source is free to download and remember that open source is also a shareware and freeware alternative. -

FTP Instructions for Shtetlinks
SFTP Instructions for KehilaLinks SFTP stands for Secure File Transfer Protocol and is a simple way of moving files from your computer to the KehilaLinks server. 1. SFTP Access a. Your KehilaLinks SFTP Username and Password will bring you directly into the folder assigned to your site. You will see an empty space when you enter the SFTP site; the folder is not visible. b. If you manage more than one KehilaLink site, you will be provided a single UserName and Password. This Logon will bring you to a listing of KehilaLinks site folders. Instructions for accessing multiple sites: i. When you logon, you will be on a site with multiple KehilaLink site folders. ii. Double click on the folder that you will be working with. You can then browse, download and upload as needed. Follow instructions in 2 below for downloading and uploading. iii. To go to another of the sites that you manage, return to the KehilaLinks site folders screen and select the next site that you will work on. iv. If you go to a site that you are not authorized for, you can browse the folder, but will get an error message when you try to upload. 2. You can use FTP software which can be downloaded free from such sites as www.download.com or www.cnet.com/ . I will not recommend one package over another. If you use FTP software, the URL to use to SFTP is Sftp.jewishgen.org You will be provided with a Login/Username and a Password. If the software requests a port number, this value is 22. -

VNC User Guide 7 About This Guide
VNC® User Guide Version 5.3 December 2015 Trademarks RealVNC, VNC and RFB are trademarks of RealVNC Limited and are protected by trademark registrations and/or pending trademark applications in the European Union, United States of America and other jursidictions. Other trademarks are the property of their respective owners. Protected by UK patent 2481870; US patent 8760366 Copyright Copyright © RealVNC Limited, 2002-2015. All rights reserved. No part of this documentation may be reproduced in any form or by any means or be used to make any derivative work (including translation, transformation or adaptation) without explicit written consent of RealVNC. Confidentiality All information contained in this document is provided in commercial confidence for the sole purpose of use by an authorized user in conjunction with RealVNC products. The pages of this document shall not be copied, published, or disclosed wholly or in part to any party without RealVNC’s prior permission in writing, and shall be held in safe custody. These obligations shall not apply to information which is published or becomes known legitimately from some source other than RealVNC. Contact RealVNC Limited Betjeman House 104 Hills Road Cambridge CB2 1LQ United Kingdom www.realvnc.com Contents About This Guide 7 Chapter 1: Introduction 9 Principles of VNC remote control 10 Getting two computers ready to use 11 Connectivity and feature matrix 13 What to read next 17 Chapter 2: Getting Connected 19 Step 1: Ensure VNC Server is running on the host computer 20 Step 2: Start VNC -

Overview of a Password Vulnerability in Siemens Hmis
Gardiner, J. , & Rashid, A. (2020). Technical Report: Gone in 20 Seconds -- Overview of a Password Vulnerability in Siemens HMIs. Unpublished. https://arxiv.org/abs/2009.03961v1 Early version, also known as pre-print Link to publication record in Explore Bristol Research PDF-document This is the submitted manuscript (SM). It first appeared online via arXiv at https://arxiv.org/abs/2009.03961v1. Please refer to any applicable terms of use of the publisher. University of Bristol - Explore Bristol Research General rights This document is made available in accordance with publisher policies. Please cite only the published version using the reference above. Full terms of use are available: http://www.bristol.ac.uk/red/research-policy/pure/user-guides/ebr-terms/ Technical Report: Gone in 20 Seconds - Overview of a Password Vulnerability in Siemens HMIs Joseph Gardiner and Awais Rashid Bristol Cyber Security Group, University of Bristol Bristol, UK fjoe.gardiner,[email protected] Abstract— Siemens produce a range of industrial human Human machine interfaces (HMIs) primarily refer to a machine interface (HMI) screens which allow operators to both physical device which is designed to be installed in physical view information about and control physical processes. For proximity to a physical process. HMI screens are programmed scenarios where an operator cannot physically access the screen, Siemens provide the SM@rtServer features on HMIs, which to both provide a display of information relating to the when activated provides remote access either through their own physical process below, as well as allow operators to provide Sm@rtClient application, or through third party VNC client inputs to the control system to control and manage physical software. -

Webfaction User Guide
WebFaction User Guide WebFaction is a service of Paragon Internet Group Limited CONTENTS 1 Introduction 3 1.1 Services..................................................3 1.2 The Complete System..........................................4 2 The Control Panel 5 2.1 Log in to the Control Panel.......................................5 2.2 Change Your Control Panel Password..................................5 2.3 What to Do About a Lost Password...................................6 2.4 Two-Step Login.............................................6 3 Finding Details About Your Server9 3.1 Finding Your Server’s Name.......................................9 3.2 Finding Your Server’s Operating System................................9 3.3 Finding Your Server’s IP Address.................................... 10 4 Accessing Your Data 11 4.1 Connecting with SSH.......................................... 11 4.2 Connecting with FTP........................................... 14 4.3 Changing Your FTP or SSH Password.................................. 14 4.4 Additional Users............................................. 15 4.5 Backups................................................. 16 5 Accounts 17 5.1 Plans and Services............................................ 17 5.2 Communicating with WebFaction.................................... 18 5.3 Payments................................................. 19 5.4 Affiliate Program............................................. 23 5.5 Canceling Your Account......................................... 24 6 Domains 25 6.1 Getting -

Virtual GPU Software User Guide Is Organized As Follows: ‣ This Chapter Introduces the Capabilities and Features of NVIDIA Vgpu Software
Virtual GPU Software User Guide DU-06920-001 _v13.0 Revision 02 | August 2021 Table of Contents Chapter 1. Introduction to NVIDIA vGPU Software..............................................................1 1.1. How NVIDIA vGPU Software Is Used....................................................................................... 1 1.1.2. GPU Pass-Through.............................................................................................................1 1.1.3. Bare-Metal Deployment.....................................................................................................1 1.2. Primary Display Adapter Requirements for NVIDIA vGPU Software Deployments................2 1.3. NVIDIA vGPU Software Features............................................................................................. 3 1.3.1. GPU Instance Support on NVIDIA vGPU Software............................................................3 1.3.2. API Support on NVIDIA vGPU............................................................................................ 5 1.3.3. NVIDIA CUDA Toolkit and OpenCL Support on NVIDIA vGPU Software...........................5 1.3.4. Additional vWS Features....................................................................................................8 1.3.5. NVIDIA GPU Cloud (NGC) Containers Support on NVIDIA vGPU Software...................... 9 1.3.6. NVIDIA GPU Operator Support.......................................................................................... 9 1.4. How this Guide Is Organized..................................................................................................10 -

Connecting to the Rutgers Astrolab Server Remotely: VNC and File Transfer
Connecting to the Rutgers Astrolab Server Remotely: VNC and file transfer You will use the Rutgers “Astrolab” server to analyze images and spectra. This document describes how to connect to your “Virtual Network Computing” (VNC) desktop environment on Astrolab from your own PC or laptop. This environment has image display and analysis tools that you will use with your data. Once the initial analysis is complete, it is often useful to transfer intermediate or final results to your own computer for further analysis or to write up your report. The second part of this document describes some file transfer tools. You will be given your username and password on the Astrolab system. The former is usually your last name (removing spaces and punctuation, if any) and the latter is the last six digits of your student ID number (with leading zeros if appropriate). Each of you has a unique 2-digit VNC session number; this will be the same number throughout the semester. VNC Desktop The best option for connecting to your VNC desktop depends on the operating system of your computer. Using the web browser to connect to your desktop works for any operating system, but confines the desktop to your browser window. For Windows machines, the best option is probably the TightVNC program (there is a MacOS equivalent program, but it seems to be somewhat flaky for later versions of the operating system). For MacOS, the recent few versions have a VNC server built in and this seems to work well. If you have a generic Linux machine, you probably know enough to set up a VNC server, but consult with us if you are having problems connecting. -

Security Analysis of Browser Extension Concepts
Saarland University Faculty of Natural Sciences and Technology I Department of Computer Science Bachelor's thesis Security Analysis of Browser Extension Concepts A comparison of Internet Explorer 9, Safari 5, Firefox 8, and Chrome 14 submitted by Karsten Knuth submitted January 14, 2012 Supervisor Prof. Dr. Michael Backes Advisors Raphael Reischuk Sebastian Gerling Reviewers Prof. Dr. Michael Backes Dr. Matteo Maffei Statement in Lieu of an Oath I hereby confirm that I have written this thesis on my own and that I have not used any other media or materials than the ones referred to in this thesis. Saarbr¨ucken, January 14, 2012 Karsten Knuth Declaration of Consent I agree to make both versions of my thesis (with a passing grade) accessible to the public by having them added to the library of the Computer Science Department. Saarbr¨ucken, January 14, 2012 Karsten Knuth Acknowledgments First of all, I thank Professor Dr. Michael Backes for giving me the chance to write my bachelor's thesis at the Information Security & Cryptography chair. During the making of this thesis I have gotten a deeper look in a topic which I hope to be given the chance to follow up in my upcoming academic career. Furthermore, I thank my advisors Raphael Reischuk, Sebastian Gerling, and Philipp von Styp-Rekowsky for supporting me with words and deeds during the making of this thesis. In particular, I thank the first two for bearing with me since the release of my topic. My thanks also go to Lara Schneider and Michael Zeidler for offering me helpful advice. -

Remote Monitoring and Control of the R&S®RTO with a Web Browser
Browser as a server on the instrument. instrument. on the as a server used is (VNC) Computing Network Virtual technology cross-platform The common browser. web a standard through oscilloscope digital R&S ofthe monitoring or operation This application note describes remote | | | | Products: Note Application R&S the of Control and Monitoring Remote R&S R&S R&S R&S RTO1012 RTO1024 RTO1022 RTO1014 ® RTO with a Web a Web with RTO ® RTO Application Note Jochen Wolle July 2010-1ER01_0e Table of Contents Table of Contents 1 Introduction ............................................................................ 3 2 VNC Installation on the Instrument ...................................... 4 Optimizing the Screen Update Rate ...........................................................6 3 Changing the Instrument Screen Resolution ...................... 7 4 Starting the Soft Front Panel from the Browser.................. 8 1ER01_0e Rohde & Schwarz Remote Monitoring and Control with a Web Browser 2 Introduction 1 Introduction The LAN network interface of instruments opens a whole new field of applications in the area of remote monitoring and control. In contrast to the common IEEE-488 bus (GPIB), were the cable length was rather limited, the network interface virtually makes distance between instrument and operator boundless. Windows XP based R&S instruments already provide a solution for remote access by means of Remote Desktop. This solution however, is limited to one user and the measurement graphics is shown either on the instrument or on the remote display but not on both simultaneously. This application note describes an approach with VNC (Virtual Network Computing) that allows multiple clients to access the same instrument at the same time. The measurement graphics is still available on the instrument screen.