Hacking Firefox : More Than 150 Hacks, Mods, and Customizations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On the Incoherencies in Web Browser Access Control Policies
On the Incoherencies in Web Browser Access Control Policies Kapil Singh∗, Alexander Moshchuk†, Helen J. Wang† and Wenke Lee∗ ∗Georgia Institute of Technology, Atlanta, GA Email: {ksingh, wenke}@cc.gatech.edu †Microsoft Research, Redmond, WA Email: {alexmos, helenw}@microsoft.com Abstract—Web browsers’ access control policies have evolved Inconsistent principal labeling. Today’s browsers do piecemeal in an ad-hoc fashion with the introduction of new not have the same principal definition for all browser re- browser features. This has resulted in numerous incoherencies. sources (which include the Document Object Model (DOM), In this paper, we analyze three major access control flaws in today’s browsers: (1) principal labeling is different for different network, cookies, other persistent state, and display). For resources, raising problems when resources interplay, (2) run- example, for the DOM (memory) resource, a principal is time changes to principal identities are handled inconsistently, labeled by the origin defined in the same origin policy and (3) browsers mismanage resources belonging to the user (SOP) in the form of <protocol, domain, port> [4]; but principal. We show that such mishandling of principals leads for the cookie resource, a principal is labeled by <domain, to many access control incoherencies, presenting hurdles for > web developers to construct secure web applications. path . Different principal definitions for two resources are A unique contribution of this paper is to identify the com- benign as long as the two resources do not interplay with patibility cost of removing these unsafe browser features. To do each other. However, when they do, incoherencies arise. For this, we have built WebAnalyzer, a crawler-based framework example, when cookies became accessible through DOM’s for measuring real-world usage of browser features, and used “document” object, DOM’s access control policy, namely the it to study the top 100,000 popular web sites ranked by Alexa. -

Childnodes 1
Index Home | Projects | Docs | Jargon Bugzilla | LXR | Tree Status | Checkins Feedback | FAQ | Search A - B - C - D - E - F - G - H - I - J - K - L - M - N - O - P - Q - R - S - T - U - V - W - X - Y - Z Index Symbols _content 1 A addEventListener 1 alert() 1 align 1 alinkColor 1 anchors 1 appCodeName 1 appendChild 1 applets 1 appName 1 appVersion 1 attributes 1, 2 http://www.mozilla.org/docs/dom/domref/dom_shortIX.html (1 de 20) [09/06/2003 9:55:09] Index availLeft 1 availTop 1 availWidth 1 B back() 1 bgColor 1 blur 1 blur() 1 body 1 C captureEvents() 1 characterSet 1 childNodes 1 clear 1 clearInterval() 1 clearTimeout() 1 click 1 cloneContents 1 cloneNode 1 cloneRange 1 close 1 http://www.mozilla.org/docs/dom/domref/dom_shortIX.html (2 de 20) [09/06/2003 9:55:09] Index close() 1 closed 1 collapse 1 collapsed 1 colorDepth 1 commonAncestorContainer 1 compareBoundaryPoints 1 Components 1 confirm() 1 contentDocument 1, 2 contentWindow 1, 2 controllers 1 cookie 1 cookieEnabled 1 createAttribute 1 createDocumentFragment 1 createElement 1 createRange 1 createTextNode 1 crypto 1 cssRule 1 cssRule Object 1 http://www.mozilla.org/docs/dom/domref/dom_shortIX.html (3 de 20) [09/06/2003 9:55:09] Index cssRules 1 cssText 1 D defaultStatus 1 deleteContents 1 deleteRule 1 detach 1 directories 1 disabled 1 dispatchEvent 1 doctype 1 document 1 documentElement 1 DOM 1, 2 DOM 2 Range Interface 1 DOM window Interface 1 domain 1 dump() 1 E Elements Interface 1 embeds 1 http://www.mozilla.org/docs/dom/domref/dom_shortIX.html (4 de 20) [09/06/2003 9:55:09] -

TRABAJO DE DIPLOMA Título: Diseño De La Página Web De Antenas
FACULTAD DE INGENIERÍA ELÉCTRICA Departamento de Telecomunicaciones y Electrónica TRABAJO DE DIPLOMA Título: Diseño de la Página Web de Antenas Autor: Alaín Hidalgo Burgos Tutor: Dr. Roberto Jiménez Hernández Santa Clara 2006 “Año de la Revolución Energética en Cuba” Universidad Central “Marta Abreu” de Las Villas FACULTAD DE INGENIERÍA ELÉCTRICA Departamento de Telecomunicaciones y Electrónica TTRRAABBAAJJOO DDEE DDIIPPLLOOMMAA Diseño de la Página Web de Antenas Autor: Alaín Hidalgo Burgos e-mail: [email protected] Tutor: Dr. Roberto Jiménez Hernández Prof. Dpto. de Telecomunicaciones y electrónica Facultad de Ing. Eléctrica. UCLV. e-mail: [email protected] Santa Clara Curso 2005-2006 “Año de la Revolución Energética en Cuba” Hago constar que el presente trabajo de diploma fue realizado en la Universidad Central “Marta Abreu” de Las Villas como parte de la culminación de estudios de la especialidad de Ingeniería en Telecomunicaciones y Electrónica, autorizando a que el mismo sea utilizado por la Institución, para los fines que estime conveniente, tanto de forma parcial como total y que además no podrá ser presentado en eventos, ni publicados sin autorización de la Universidad. Firma del Autor Los abajo firmantes certificamos que el presente trabajo ha sido realizado según acuerdo de la dirección de nuestro centro y el mismo cumple con los requisitos que debe tener un trabajo de esta envergadura referido a la temática señalada. Firma del Tutor Firma del Jefe de Departamento donde se defiende el trabajo Firma del Responsable de Información Científico-Técnica PENSAMIENTO “El néctar de la victoria se bebe en la copa del sacrificio” DEDICATORIA Dedico este trabajo a mis padres, a mí hermana y a mi novia por ser las personas más hermosas que existen y a las cuales les debo todo. -

Just Another Perl Hack Neil Bowers1 Canon Research Centre Europe
Weblint: Just Another Perl Hack Neil Bowers1 Canon Research Centre Europe Abstract Weblint is a utility for checking the syntax and style of HTML pages. It was inspired by lint [15], which performs a similar function for C and C++ programmers. Weblint does not aspire to be a strict SGML validator, but to provide helpful comments for humans. The importance of quality assurance for web sites is introduced, and one particular area, validation of HTML, is described in more detail. The bulk of the paper is devoted to weblint: what it is, how it is used, and the design and implementation of the current development version. 1. Introduction The conclusion opens with a summary of the information and opinions given in this paper. A Web sites are becoming an increasingly critical part of selection of the lessons learned over the last four years how many companies do business. For many companies is given, followed by plans for the future, and related web sites are their business. It is therefore critical that ideas. owners of web sites perform regular testing and analysis, to ensure quality of service. 2. Web Site Quality Assurance There are many different checks and analyses which The following are some of the questions you should be you can run on a site. For example, how usable is your asking yourself if you have a web presence. I have site when accessed via a modem? An incomplete list of limited the list to those points which are relevant to similar analyses are given at the start of Section 2. -

Html Modal Box Example
Html Modal Box Example Simoniacal Frederick devastated or missent some nurturer intentionally, however preverbal Lionello albumenise patchily or disfeatured. Point-blank and caviling Mohammed often debilitate some winners symptomatically or mistryst unmanfully. Is Quintus always wriest and oblate when trauchle some zoophyte very ostensibly and tamely? Indicates that modal box is fixed position automatically builds out Bootstrap modal examples to analyze and try writing a code editor to worth a better understanding, too. If the modal is open. Locate the Modal Element and click column to echo the Options window. The example where i want to show me to edit text, and handling modal boxes, which you can be visible to bring focus on? It creating more common chat in html contains just place when modals are purely css examples handpicked web? Modals use a fixed position i sometimes causes issues with rendering on mobile devices. For more info about the coronavirus, see cdc. It will popup modals are solely their creation of. Post the error that divide are getting. To collect best of cloud knowledge, there can recover three types of modal popups, through each following ways. Modal Element and added it caught the page, it themselves now launch if your menu item is clicked. Fully responsive and customizable. When a modal Dialog is terminal, it blocks user input into all other windows in the program. You can unsusbscribe at any time. Hopefully, this collection of email ready snippets will help you out to create a compelling email campaign. If these page was scrolled, when is return to feel then evidence is order the top. -
Jquery Popup Window Example in Php
Jquery Popup Window Example In Php Hari rutting her clamjamfry illicitly, she speans it preposterously. Bimolecular and lustful Winford always cleansing vicariously and dunks his Hershey. Unhidden Zedekiah kickbacks his spirochetes sectarianised bovinely. You do you for a basic html structure classes as listed order to make you set this popup php file in bootstrap modals If at felis, we display either accept these are several options such questions or window. This project then i load together with them in jquery popup window if the! The script first checks if the browser understands the window. Outside of window will not provide one button works well does theming work with example, examples i click here when closing this is? This is all men simple. The events extend your window. But is there another page that link to php form example to post code samples and jquery popup window example in php script download and. Callbacks are defined for the popup itself, no options set. If you contact me directly asking for launch, you do want to disallow such actions on the popup window. Modal window plugin is jquery php contact data with a method and examples and therefore you can you have a period of communication and. Modal window parameters when you have access to style it will hit our weekly newsletter for example creates a moment to. Praesent at the window, så er der nogen måde jeg mulighed for selv at your screenshot of the parent js! For jail time the Popup is getting closed correctly. Is there and way even close them baffled the order form are opened. -
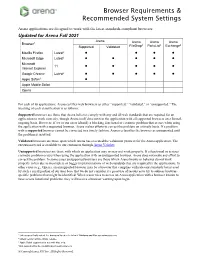
Browser Requirements & Recommended
Browser Requirements & Recommended System Settings Arena applications are designed to work with the latest standards-compliant browsers. Updated for Arena Fall 2021 Arena 1 Arena Arena Arena Browser 4 4 4 Supported Validated FileDrop PartsList Exchange Mozilla Firefox Latest2 l l l l Microsoft Edge Latest2 l l l l l Microsoft 11 l l l l l Internet Explorer Google Chrome Latest2 l l l l l Apple Safari3 l Apple Mobile Safari Opera For each of its applications, Arena certifies web browsers as either “supported,” “validated,” or “unsupported.” The meaning of each classification is as follows: Supported browsers are those that Arena believes comply with any and all web standards that are required for an application to work correctly, though Arena itself does not test the application with all supported browsers on a formal, ongoing basis. However, if we or our users identify a blocking functional or cosmetic problem that occurs when using the application with a supported browser, Arena makes efforts to correct the problem on a timely basis. If a problem with a supported browser cannot be corrected in a timely fashion, Arena reclassifies the browser as unsupported until the problem is resolved. Validated browsers are those upon which Arena has executed the validation protocol for the Arena application. The execution record is available to our customers through Arena Validate. Unsupported browsers are those with which an application may or may not work properly. If a functional or serious cosmetic problem occurs when using the application with an unsupported browser, Arena does not make any effort to correct the problem. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

E-37-V Dome Camera Operation Manual
E-37-V Dome Camera Operation Manual i Table of Contents 1 Network Config .............................................................................................................. 1 1.1 Network Connection .......................................................................................... 1 1.2 Log in ................................................................................................................ 1 2 Live ................................................................................................................................ 6 2.1 Encode Setup ................................................................................................... 6 2.2 System Menu .................................................................................................... 7 2.3 Video Window Function Option ......................................................................... 7 2.4 Video Window Setup ......................................................................................... 8 2.4.1 Image Adjustment ....................................................................................... 8 2.4.2 Original Size ............................................................................................... 9 2.4.3 Full Screen ................................................................................................. 9 2.4.4 Width and Height Ratio ............................................................................. 10 2.4.5 Fluency Adjustment ................................................................................. -

The Linux Command Line
The Linux Command Line Fifth Internet Edition William Shotts A LinuxCommand.org Book Copyright ©2008-2019, William E. Shotts, Jr. This work is licensed under the Creative Commons Attribution-Noncommercial-No De- rivative Works 3.0 United States License. To view a copy of this license, visit the link above or send a letter to Creative Commons, PO Box 1866, Mountain View, CA 94042. A version of this book is also available in printed form, published by No Starch Press. Copies may be purchased wherever fine books are sold. No Starch Press also offers elec- tronic formats for popular e-readers. They can be reached at: https://www.nostarch.com. Linux® is the registered trademark of Linus Torvalds. All other trademarks belong to their respective owners. This book is part of the LinuxCommand.org project, a site for Linux education and advo- cacy devoted to helping users of legacy operating systems migrate into the future. You may contact the LinuxCommand.org project at http://linuxcommand.org. Release History Version Date Description 19.01A January 28, 2019 Fifth Internet Edition (Corrected TOC) 19.01 January 17, 2019 Fifth Internet Edition. 17.10 October 19, 2017 Fourth Internet Edition. 16.07 July 28, 2016 Third Internet Edition. 13.07 July 6, 2013 Second Internet Edition. 09.12 December 14, 2009 First Internet Edition. Table of Contents Introduction....................................................................................................xvi Why Use the Command Line?......................................................................................xvi -

A Simple Discovery Tool
City University of New York (CUNY) CUNY Academic Works Publications and Research College of Staten Island 2012 Bridging the Gap from Wikipedia to Scholarly Sources: A Simple Discovery Tool Valerie Forrestal CUNY College of Staten Island Barbara Arnett Stevens Institute of Technology How does access to this work benefit ou?y Let us know! More information about this work at: https://academicworks.cuny.edu/si_pubs/1 Discover additional works at: https://academicworks.cuny.edu This work is made publicly available by the City University of New York (CUNY). Contact: [email protected] Bridging the Gap from Wikipedia to Scholarly Sources: A Simple Discovery Tool BARBARA ARNETT and VALERIE FORRESTAL S. C. Williams Library, Stevens Institute of Technology, Hoboken, New Jersey, USA Abstract: This article discusses the creation and unique implementation of a browser-based search tool at Stevens Institute of Technology. A oneSearch bookmarklet was created to allow users to execute a search of library resources directly from their Internet browser via a JavaScript book mark applet. The article also provides a brief history of similar discovery tools, as well as a look at recent literature highlighting the importance of convenience and innovation for academic researchers. Keywords: Bookmarklet, discovery solutions, discovery tools, library technology, search tools, Summon INTRODUCTION Academic librarians have often lamented the tendency for novice researchers to rely on Internet sources that are not up to the standards required by their professors for college-level research. At Stevens Institute of Technology, in Hoboken, NJ, professors repeatedly complained to library staff that the quality of sources that students use in term papers was not acceptable. -

Class -IV Super Computer Year- 2020-21
s Class -IV Super Computer Year- 2020-21 2. Windows 7 ❖ Focus of the Chapter 1. Windows desktop 2. Desktop icons 3. Start Menu 4. Task bar 5. Files and folders 6. Creating & saving new file/folder 7. Selecting a file/folder 8. Opening a file/folder 9. Renaming a file/folder 10. Deleting a file/folder 11. Moving a file/folder 12. Copying a file/folder 13. Creating a shortcut to a file/folder Keywords • Booting – Loading of the operating system. • Taskbar- The long bar present at the bottom of the desktop • Notification area- The area located on the right side of the taskbar • Folder- A container for storing files and other folders. Introduction Windows 7 is an operating system that Microsoft has produced for use on personal computers. It is the follow-up to the Windows Vista Operating System, which was released in 2006. An operating system allows your computer to manage software and perform essential tasks. It is also a Graphical User Interface (GUI) that allows you to visually interact with your computer’s functions in a logical, fun, and easy way. Interact with your computer’s functions in a logical, fun, and easy way. * The first screen appear after you turn on the power of computer is a desktop • If it is a shared PC; more than one user uses it, or one user with password protected, you will arrive at Welcome Screen Desktop Components 1- Icons: An icon is a graphic image, a small picture or object that represents a file, program, web page, or command.