Analyzing Information Flow in Javascript-Based Browser Extensions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Differential Fuzzing the Webassembly
Master’s Programme in Security and Cloud Computing Differential Fuzzing the WebAssembly Master’s Thesis Gilang Mentari Hamidy MASTER’S THESIS Aalto University - EURECOM MASTER’STHESIS 2020 Differential Fuzzing the WebAssembly Fuzzing Différentiel le WebAssembly Gilang Mentari Hamidy This thesis is a public document and does not contain any confidential information. Cette thèse est un document public et ne contient aucun information confidentielle. Thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Technology. Antibes, 27 July 2020 Supervisor: Prof. Davide Balzarotti, EURECOM Co-Supervisor: Prof. Jan-Erik Ekberg, Aalto University Copyright © 2020 Gilang Mentari Hamidy Aalto University - School of Science EURECOM Master’s Programme in Security and Cloud Computing Abstract Author Gilang Mentari Hamidy Title Differential Fuzzing the WebAssembly School School of Science Degree programme Master of Science Major Security and Cloud Computing (SECCLO) Code SCI3084 Supervisor Prof. Davide Balzarotti, EURECOM Prof. Jan-Erik Ekberg, Aalto University Level Master’s thesis Date 27 July 2020 Pages 133 Language English Abstract WebAssembly, colloquially known as Wasm, is a specification for an intermediate representation that is suitable for the web environment, particularly in the client-side. It provides a machine abstraction and hardware-agnostic instruction sets, where a high-level programming language can target the compilation to the Wasm instead of specific hardware architecture. The JavaScript engine implements the Wasm specification and recompiles the Wasm instruction to the target machine instruction where the program is executed. Technically, Wasm is similar to a popular virtual machine bytecode, such as Java Virtual Machine (JVM) or Microsoft Intermediate Language (MSIL). -
Mozilla Firefox Lower Version Free Download Firefox Release Notes
mozilla firefox lower version free download Firefox Release Notes. Release Notes tell you what’s new in Firefox. As always, we welcome your feedback. You can also file a bug in Bugzilla or see the system requirements of this release. Download Firefox — English (US) Your system may not meet the requirements for Firefox, but you can try one of these versions: Download Firefox — English (US) Download Firefox Download Firefox Download Firefox Download Firefox Download Firefox Download Firefox Download Firefox Download Firefox Firefox for Android Firefox for iOS. December 1, 2014. We'd also like to extend a special thank you to all of the new Mozillians who contributed to this release of Firefox! Default search engine changed to Yandex for Belarusian, Kazakh, and Russian locales. Improved search bar (en-US only) Firefox Hello real-time communication client. Easily switch themes/personas directly in the Customizing mode. Wikipedia search now uses HTTPS for secure searching (en-US only) Recover from a locked Firefox process in the "Firefox is already running" dialog on Windows. Fixed. CSS transitions start correctly when started at the same time as changes to display, position, overflow, and similar properties. Fullscreen video on Mac disables display sleep, and dimming, during playback. Various Yosemite visual fixes (see bug 1040250) Changed. Proprietary window.crypto properties/functions re-enabled (to be removed in Firefox 35) Firefox signed by Apple OS X version 2 signature. Developer. WebIDE: Create, edit, and test a new Web application from your browser. Highlight all nodes that match a given selector in the Style Editor and the Inspector's Rules panel. -

Brief Intro to Firebug Firebug at a Glance
Brief Intro to Firebug Firebug at a glance • One of the most popular web debugging tool with a collec6on of powerful tools to edit, debug and monitor HTML, CSS and JavaScript, etc. • Many rich features: • Inspect, Log, Profile • Debug, Analyze, Layout How to install • Get firebug: • Open Firefox, and go to hp://geirebug.com/ • Click Install Firebug, and follow the instruc6ons • Ways to launch Firebug • F12, or Firebug Buon • Right click an element on the page and inspect it with Firebug Firebug Panels • Console: An interac6ve JavaScript Console • HTML: HTML View • CSS: CSS View • Script: JavaScript Debugger • DOM: A list of DOM proper6es (defaults to window object) • Net: HTTP traffic monitoring • Cookies: Cookie View Tasks for HTML Panel • Open twiLer.com and log in with your account. Ac6vate Firebug. • Tasks with HTML Panel • 1. Which <div> tag corresponds to the navigaon bar at the top of the page? • 2. Change the text “Messages” in the navigaon bar to “Tweets” • 3. Find out which <div> tag corresponds to the dashboard which is the le` column of the page. Can you change the width of the dashboard to 200px? • 4. Try to figure out the URL of your profile picture at the top le` corner of the home page, and use this URL to open this picture in a new tab. • 5. Change your name next to your profile picture to something else, and change the text colour to blue. Inspect HTTP Traffic • Open twiLer.com and log in with your account. Ac6vate Firebug. • Tasks with Net Panel • 1. Which request takes the longest 6me to load? • 2. -

Rich Media Web Application Development I Week 1 Developing Rich Media Apps Today’S Topics
IGME-330 Rich Media Web Application Development I Week 1 Developing Rich Media Apps Today’s topics • Tools we’ll use – what’s the IDE we’ll be using? (hint: none) • This class is about “Rich Media” – we’ll need a “Rich client” – what’s that? • Rich media Plug-ins v. Native browser support for rich media • Who’s in charge of the HTML5 browser API? (hint: no one!) • Where did HTML5 come from? • What are the capabilities of an HTML5 browser? • Browser layout engines • JavaScript Engines Tools we’ll use • Browsers: • Google Chrome - assignments will be graded on Chrome • Safari • Firefox • Text Editor of your choice – no IDE necessary • Adobe Brackets (available in the labs) • Notepad++ on Windows (available in the labs) • BBEdit or TextWrangler on Mac • Others: Atom, Sublime • Documentation: • https://developer.mozilla.org/en-US/docs/Web/API/Document_Object_Model • https://developer.mozilla.org/en-US/docs/Web/API/Canvas_API/Tutorial • https://developer.mozilla.org/en-US/docs/Web/JavaScript/Guide What is a “Rich Client” • A traditional “web 1.0” application needs to refresh the entire page if there is even the smallest change to it. • A “rich client” application can update just part of the page without having to reload the entire page. This makes it act like a desktop application - see Gmail, Flickr, Facebook, ... Rich Client programming in a web browser • Two choices: • Use a plug-in like Flash, Silverlight, Java, or ActiveX • Use the built-in JavaScript functionality of modern web browsers to access the native DOM (Document Object Model) of HTML5 compliant web browsers. -

The Javascript Revolution
Top teams present at Segfault Tank on 4/21: 1 Duel: 6 (2 extra shifted from self votes) 2 Ambassador: 4 3 QuickSource: 3 4 ChalkBoard: 3 5 Fortuna Beer: 3 Bottom teams present in class this Thursday 4/16: 1 Scribble: 2 2 ClearViz: 2 3 AllInOne: 1 4 TripSplitter: 0 Shockers: Scribble & Fortuna Congrats on sneaky strategizing to get yourself to the top :) The moment of fruit: the class has spoken Shockers: Scribble & Fortuna Congrats on sneaky strategizing to get yourself to the top :) The moment of fruit: the class has spoken Top teams present at Segfault Tank on 4/21: 1 Duel: 6 (2 extra shifted from self votes) 2 Ambassador: 4 3 QuickSource: 3 4 ChalkBoard: 3 5 Fortuna Beer: 3 Bottom teams present in class this Thursday 4/16: 1 Scribble: 2 2 ClearViz: 2 3 AllInOne: 1 4 TripSplitter: 0 Congrats on sneaky strategizing to get yourself to the top :) The moment of fruit: the class has spoken Top teams present at Segfault Tank on 4/21: 1 Duel: 6 (2 extra shifted from self votes) 2 Ambassador: 4 3 QuickSource: 3 4 ChalkBoard: 3 5 Fortuna Beer: 3 Bottom teams present in class this Thursday 4/16: 1 Scribble: 2 2 ClearViz: 2 3 AllInOne: 1 4 TripSplitter: 0 Shockers: Scribble & Fortuna The moment of fruit: the class has spoken Top teams present at Segfault Tank on 4/21: 1 Duel: 6 (2 extra shifted from self votes) 2 Ambassador: 4 3 QuickSource: 3 4 ChalkBoard: 3 5 Fortuna Beer: 3 Bottom teams present in class this Thursday 4/16: 1 Scribble: 2 2 ClearViz: 2 3 AllInOne: 1 4 TripSplitter: 0 Shockers: Scribble & Fortuna Congrats on sneaky strategizing -

Flash Player and Linux
Flash Player and Linux Ed Costello Engineering Manager Adobe Flash Player Tinic Uro Sr. Software Engineer Adobe Flash Player 2007 Adobe Systems Incorporated. All Rights Reserved. Overview . History and Evolution of Flash Player . Flash Player 9 and Linux . On the Horizon 2 2007 Adobe Systems Incorporated. All Rights Reserved. Flash on the Web: Yesterday 3 2006 Adobe Systems Incorporated. All Rights Reserved. Flash on the Web: Today 4 2006 Adobe Systems Incorporated. All Rights Reserved. A Brief History of Flash Player Flash Flash Flash Flash Linux Player 5 Player 6 Player 7 Player 9 Feb 2001 Dec 2002 May 2004 Jan 2007 Win/ Flash Flash Flash Flash Flash Flash Flash Mac Player 3 Player 4 Player 5 Player 6 Player 7 Player 8 Player 9 Sep 1998 Jun 1999 Aug 2000 Mar 2002 Sep 2003 Aug 2005 Jun 2006 … Vector Animation Interactivity “RIAs” Developers Expressive Performance & Video & Standards Simple Actions, ActionScript Components, ActionScript Filters, ActionScript 3.0, Movie Clips, 1.0 Video (H.263) 2.0 Blend Modes, New virtual Motion Tween, (ECMAScript High-!delity machine MP3 ed. 3), text, Streaming Video (ON2) video 5 2007 Adobe Systems Incorporated. All Rights Reserved. Widest Reach . Ubiquitous, cross-platform, rich media and rich internet application runtime . Installed on 98% of internet- connected desktops1 . Consistently reaches 80% penetration within 12 months of release2 . Flash Player 9 reached 80%+ penetration in <9 months . YUM-savvy updater to support rapid/consistent Linux penetration 1. Source: Millward-Brown September 2006. Mature Market data. 2. Source: NPD plug-in penetration study 6 2007 Adobe Systems Incorporated. All Rights Reserved. -

Detecting Conflicts Among Declarative UI Extensions
Detecting Conflicts Among Declarative UI Extensions Benjamin S. Lerner Dan Grossman Brown University University of Washington [email protected] [email protected] Abstract shows a “Hello world” example written in XUL, a simple overlay We examine overlays, a flexible aspect-like mechanism for third- targeting it, and its composition with the base document. Appli- cations like Firefox use this ability heavily to modularize their UI party declarative extensions of declarative UIs. Overlays can be de- fined for any markup language and permit extensions to define new definitions into many smaller documents. Mozilla applications expose the overlay mechanism to third par- content that is dynamically woven into a base UI document. While powerful, overlays are inherently non-modular and may conflict ties and thereby enable a uniquely powerful extension mechanism. Such third party extensions can enhance or modify the program’s with each other, by defining duplicate or contradictory UI compo- nents. We construct an abstract language to capture core overlay se- base functionality in arbitrary ways; overlays are used to integrate mantics, and design an automatic analysis to detect inter-extension the extension’s UI into the existing UI. Moreover, end users can conflicts. We apply the analysis to a case study of Firefox exten- freely install extensions to customize their browser however they sions, finding several real-world bugs. Our analysis provides low- wish. This expressiveness has led to the widespread popularity level feedback to extension developers and high-level reports to end of Firefox extensions—hundreds of millions of users have down- users. Finally, we show how variants of overlays more expressive loaded extensions billions of times [13]. -

Behavioural Analysis of Tracing JIT Compiler Embedded in the Methodical Accelerator Design Software
Scuola Politecnica e delle Scienze di Base Corso di Laurea Magistrale in Ingegneria Informatica Tesi di laurea magistrale in Calcolatori Elettronici II Behavioural Analysis of Tracing JIT Compiler Embedded in the Methodical Accelerator Design Software Anno Accademico 2018/2019 CERN-THESIS-2019-152 //2019 relatori Ch.mo prof. Nicola Mazzocca Ch.mo prof. Pasquale Arpaia correlatore Ing. Laurent Deniau PhD candidato Dario d’Andrea matr. M63000695 Acknowledgements Firstly, I would like to thank my supervisor at CERN, Laurent Deniau, for his daily support and his useful suggestions throughout the work described in this thesis. I would like to express my gratitude to both my university supervisors, Nicola Mazzocca and Pasquale Arpaia, for their helpfulness during this work and for their support during the past years at university. I feel privileged of being allowed to work with such inspiring mentors. This thesis would not have been possible without the help from the community of the LuaJIT project including all the useful insights contained in its mailing list, specially by its author, Mike Pall, who worked for many years accomplishing an amazing job. A special acknowledgement should be addressed to my family. I thank my father Guido and my mother Leda who guided me with love during my education and my life. I am grateful to my brother Fabio, my grandmother Tina, and my uncle Nicola, for their support during the past years. I also want to remember my uncle Bruno who inspired me for my academic career. I wish to express my deepest gratitude to Alicia for her unconditional encour- agement. -

Empirical Studies of Javascript-‐ Based Web Applicaxon
Empirical Studies of JavaScript- based Web Applica8on Reliability Karthik Pa@abiraman1 Frolin Ocariza1 Kar.k Bajaj1 Ali Mesbah1 Benjamin Zorn2 1 University of Bri.sh Columbia (UBC), 2MicrosoE Research (MSR) Web 2.0 Applicaons Copyright: Karthik Paabiraman, 2014 Web 2.0 Applicaon: Amazon.com Menu Amazon’s Third party Search bar Web 2.0 applicaons allow rich UI funconality within a single web page own ad gadget ad Func8on Copyright: Karthik Paabiraman, 2014 Modern Web Applicaons: JavaScript • JavaScript: Implementaon of ECMAScript standard – Client-Side JavaScript: used to develop web apps • Executes in client’s browser – send AJAX messages • Responsible for web applicaon’s core func.onality • Not easy to write code in – has many “evil” features 4 Copyright: Karthik Paabiraman, 2014 JavaScript: History Brief History of JavaScript (Source: TomBarker.com) JavaScript (JS) had to “look like Java” only less so, be Java’s dumb kid brother or boy-hostage sidekick. Plus, I had to be done in ten days or something worse than JS would have happened – Brendan Eich (Inventor of JavaScript) Copyright: Karthik Paabiraman, 2014 • • 10000 20000 30000 40000 50000 60000 70000 80000 90000 Thousands of lines of code, oEen > 10,000 97 of the 0 Google YouTube Yahoo Baidu QQ MSN Amazon JavaScript: Prevalence Sina WordPress Alexa Ebay LinkedIn Bing MicrosoE Yandex 163 top 100 websites use JavaScript Copyright: Karthik Paabiraman, 2014 mail.ru PayPal FC2 Flickr IMDb Lines of code Apple Livedoor BBC Sohu go.com Soso Youku AOL CNN MediaFire ESPN MySpace MegaUpload Mozilla 4shared Adobe About LiveJournal Tumblr goDaddy CNET YieldManager Sogou Zedo Ifeng Pirate Bay ImageShack Weather NY Times Nelix JavaScript: “good” or “Evil” ? Vs Eval Calls (Source: Richards et al. -
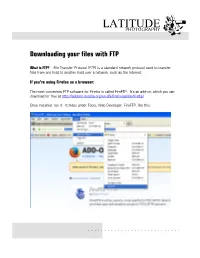
Connecting with FTP Server
LATITUDEPHOTOGRAPHY Downloading your files with FTP What is FTP?: File Transfer Protocol (FTP) is a standard network protocol used to transfer files from one host to another host over a network, such as the Internet. If you’re using Firefox as a browser: The most convenient FTP software for Firefox is called FireFTP. It’s an add-on, which you can download for free at http://addons.mozilla.org/en-US/firefox/addon/fireftp/ Once installed, run it. It hides under Tools, Web Developer, FireFTP, like this: . Firefox will start a new tab right in the browser. On the left, you will have to select QuickConnect from a dropdown list. And a window will popup. Fill in all the fields, with the your login information. Leave the Anonymous box uncheck. Press Connect. 1. Enter ftp.latitudephotography.com here 2. Enter your login name here 3. Password goes here 4. Click here to connect The FTP software will connect and look like this: YOUR Computer 5. Select folder YOUR project folder on the LATITUDE Server Don’t worry about this window The windows which you will use are the middle four. YOUR computer on the left, the LATITUDE computer on the right. If you are looking for High Resolution files from a shoot on January 11, 2013. In the right hand window double click the folder, in this case 2013-01-11. The folder will open and you will now have to select the “High Resolution JPG images” folder. You may also see a “High Resolution PNG images” or “RAW images” folders depending on the project. -

FTP Instructions for Shtetlinks
SFTP Instructions for KehilaLinks SFTP stands for Secure File Transfer Protocol and is a simple way of moving files from your computer to the KehilaLinks server. 1. SFTP Access a. Your KehilaLinks SFTP Username and Password will bring you directly into the folder assigned to your site. You will see an empty space when you enter the SFTP site; the folder is not visible. b. If you manage more than one KehilaLink site, you will be provided a single UserName and Password. This Logon will bring you to a listing of KehilaLinks site folders. Instructions for accessing multiple sites: i. When you logon, you will be on a site with multiple KehilaLink site folders. ii. Double click on the folder that you will be working with. You can then browse, download and upload as needed. Follow instructions in 2 below for downloading and uploading. iii. To go to another of the sites that you manage, return to the KehilaLinks site folders screen and select the next site that you will work on. iv. If you go to a site that you are not authorized for, you can browse the folder, but will get an error message when you try to upload. 2. You can use FTP software which can be downloaded free from such sites as www.download.com or www.cnet.com/ . I will not recommend one package over another. If you use FTP software, the URL to use to SFTP is Sftp.jewishgen.org You will be provided with a Login/Username and a Password. If the software requests a port number, this value is 22. -

Development Production Line the Short Story
Development Production Line The Short Story Jene Jasper Copyright © 2007-2018 freedumbytes.dev.net (Free Dumb Bytes) Published 3 July 2018 4.0-beta Edition While every precaution has been taken in the preparation of this installation manual, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein. This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License. To get an idea of the Development Production Line take a look at the following Application Integration overview and Maven vs SonarQube Quality Assurance reports comparison. 1. Operating System ......................................................................................................... 1 1.1. Windows ........................................................................................................... 1 1.1.1. Resources ................................................................................................ 1 1.1.2. Desktop .................................................................................................. 1 1.1.3. Explorer .................................................................................................. 1 1.1.4. Windows 7 Start Menu ................................................................................ 2 1.1.5. Task Manager replacement ........................................................................... 3 1.1.6. Resource Monitor .....................................................................................