Introduction to Networking I Isps and Internet Backbones: Tier-1 ISP
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PEERING: an AS for Us
PEERING: An AS for Us Brandon Schlinker1, Kyriakos Zarifis1, Italo Cunha2, Nick Feamster3, and Ethan Katz-Bassett1 1University of Southern California — 2Universidade Federal de Minas Gerais — 3Georgia Institute of Technology {bschlink, kyriakos, ethan.kb}@usc.edu — [email protected] — [email protected] ABSTRACT 29, 45]. BGP, the Internet’s interdomain routing protocol, Internet routing suffers from persistent and transient failures, can experience slow convergence [30] and persistent route circuitous routes, oscillations, and prefix hijacks. A ma- oscillations [17,54]. It lacks mechanisms to prevent spoof- jor impediment to progress is the lack of ways to conduct ing [5,27] and prefix hijacks [24,32,58]. Despite known impactful interdomain research. Most research is based ei- problems, little has changed with interdomain routing, and ther on passive observation of existing routes, keeping re- there has been little impactful research in recent years. searchers from assessing how the Internet will respond to This stagnancy in the face of known problems is in stark route or policy changes; or simulations, which are restricted contrast to the rapid innovation in other areas of network- by limitations in our understanding of topology and policy. ing. We are in an era of remarkable changes in networking We propose a new class of interdomain research: re- and its role in our lives, as mobile connectivity and stream- searchers can instantiate an AS of their choice, including ing video change how we use the Internet, and advances in its intradomain topology and interdomain interconnectivity, software defined networking and data centers change how and connect it with the “live” Internet to exchange routes we run networks. -

Interconnection
Interconnection 101 As cloud usage takes off, data production grows exponentially, content pushes closer to the edge, and end users demand data and applications at all hours from all locations, the ability to connect with a wide variety of players becomes ever more important. This report introduces interconnection, its key players and busi- ness models, and trends that could affect interconnection going forward. KEY FINDINGS Network-dense, interconnection-oriented facilities are not easy to replicate and are typically able to charge higher prices for colocation, as well as charging for cross-connects and, in some cases, access to public Internet exchange platforms and cloud platforms. Competition is increasing, however, and competitors are starting the long process of creating network-dense sites. At the same time, these sites are valuable and are being acquired, so the sector is consolidating. Having facili- ties in multiple markets does seem to provide some competitive advantage, particularly if the facilities are similar in look and feel and customers can monitor them all from a single portal and have them on the same contract. Mobility, the Internet of Things, services such as SaaS and IaaS (cloud), and content delivery all depend on net- work performance. In many cases, a key way to improve network performance is to push content, processing and peering closer to the edge of the Internet. This is likely to drive demand for facilities in smaller markets that offer interconnection options. We also see these trends continuing to drive demand for interconnection facilities in the larger markets as well. © 2015 451 RESEARCH, LLC AND/OR ITS AFFILIATES. -
Cologix Torix Case Study
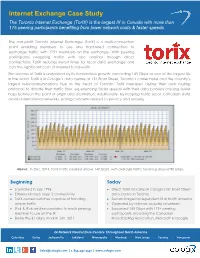
Internet Exchange Case Study The Toronto Internet Exchange (TorIX) is the largest IX in Canada with more than 175 peering participants benefiting from lower network costs & faster speeds The non-profit Toronto Internet Exchange (TorIX) is a multi-connection point enabling members to use one hardwired connection to exchange traffic with 175+ members on the exchange. With peering participants swapping traffic with one another through direct connections, TorIX reduces transit times for local data exchange and cuts the significant costs of Internet bandwidth. The success of TorIX is underlined by its tremendous growth, exceeding 145 Gbps as one of the largest IXs in the world. TorIX is in Cologix’s data centre at 151 Front Street, Toronto’s carrier hotel and the country’s largest telecommunications hub in the heart of Toronto. TorIX members define their own routing protocols to dictate their traffic flow, experiencing faster speeds with their data packets crossing fewer hops between the point of origin and destination. Additionally, by keeping traffic local, Canadian data avoids international networks, easing concerns related to privacy and security. Above: In Dec. 2014, TorIX traffic peaked above 140 Gbps, with average traffic hovering around 90 Gbps. Beginning Today Launched in July 1996 Direct TorIX on-ramp in Cologix’s151 Front Street Ethernet-based, layer 2 connectivity data centre in Toronto TorIX-owned switches capable of handling Second largest independent IX in North America ample traffic Operated by telecom industry volunteers IPv4 & IPv6 address provided to each peering Surpassed 145 Gbps with 175+ peering member to use on the IX participants, including the Canadian Broke the 61 Gbps mark in Jan. -

Peering Concepts and Definitions Terminology and Related Jargon
Peering Concepts and Definitions Terminology and Related Jargon Presentation Overview Brief On Peering Jargon Peering & Related Jargon BRIEF ON PEERING JARGON Brief On Peering Jargon A lot of terminologies used in the peering game. We shall look at the more common ones. Will be directly related to peering, as well as ancillary non-peering functions that support peering. PEERING & RELATED JARGON Peering & Related Jargon ASN (or AS - Autonomous System Number): . A unique number that identifies a collection/grouping of IP addresses or networks under the control of one entity on the Internet Bi-lateral (peering): . Peering relationships setup “directly” between two networks (see “Multi-lateral [peering]”). BGP (Border Gateway Protocol): . Routing protocol used on the Internet and at exchange points as the de-facto routing technique to share routing information (IPs and prefixes) between networks or between ASNs Peering & Related Jargon Carrier-neutral (data centre): . A facility where customers can purchase network services from “any” other networks within the facility. Cold-potato routing: . A situation where a network retains traffic on its network for as long as possible (see “Hot-potato routing”). Co-lo (co-location): . Typically a data centre where customers can house their network/service infrastructure. Peering & Related Jargon Dark fibre: . Fibre pairs offered by the owner, normally on a lease basis, without any equipment at each end of it to “activate” it (see “Lit fibre”). Data centre: . A purpose-built facility that provides space, power, cooling and network facilities to customers. Demarc (Demarcation): . Typically information about a co-lo customer, e.g., rack number, patch panel and port numbers, e.t.c. -

Peering Personals at TWNOG 4.0
Peering Personals at TWNOG 4.0 6 Dec. 2019 請注意, Peering Personal 場次將安排於下午時段的演講結束前進行, 請留意議程進行以 確保報告人當時在現場 Please note that Peering Personals will be done in the afternoon sessions so please check with Agenda and be on site. AS number 10133 (TPIX) and 17408 (Chief Telecom) Traffic profile Internet Exchange (Balanced) + ISP (Balanced) Traffic Volume TPIX: 160 Gbps ( https://www.tpix.net.tw/traffic.html ); Chief: 80 Gbps (2015- 10.7G; 2016- 25.9G; 2017- 58G; 2018- 96G) Peering Policy Open Peering Locations Taiwan: TPIX, Chief LY, Chief HD HK: HKIX, AMS-IX, EIE (HK1), Mega-i Europe: AMS-IX Message Biggest IX in Taiwan in both traffic and AS connected (59). Contact •[email protected] or •https://www.peeringdb.com/ix/823 •[email protected] or •https://www.peeringdb.com/net/8666 AS number 7527(JPIX) Traffic profile Internet Exchange (Balanced) Traffic Volume JPIX Tokyo 1.2T &JPIX Osaka 600G Peering Policy Open Peering Locations Tokyo: KDDI Otemachi, NTT Data Otemachi ,Comspace I, Equinix, Tokyo, AT Tokyo, COLT TDC1, NTT DATA Mitaka DC East, NTT COM Nexcenter DC, Meitetsucom DC (Nagoya),OCH DC (Okinawa), BBT New Otemachi DC Osaka: NTT Dojima Telepark, KDDI TELEHOUSE Osaka2, Equinix OS1,Meitetsucom DC (Nagoya), OBIS DC (Okayama) Site introduction: https://www.jpix.ad.jp/en/service_introduction.php Message Of connected ASN: Tokyo 211 Osaka 70 Remarks Our IX switch in Nagoya can offer both JPIX Tokyo vlan and Osaka one. Contact •[email protected] or [email protected] AS number 41095 Traffic profile 1:3 Balanced where content prevail Traffic Volume -

Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C
Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C. 20554 In the Maller of ) ) Global Crossing Limited and Level 3 ) Communications, Inc., Application for ) Consent to Transfer Control ofAuthority to ) Provide Global facilities-Based and Global ) IB Docket No. I 1-78 Resale International Telecommunications ) Services and ofDomestic Common Carrier ) Transmission Lines, Pursuant to Section 214 ) of the Communications Act, as Amended ) ) Level 3 Communications, Inc., Petition for ) Declaratory Ruling Under Section 31 0(b)(4) ) Ofthe Communications Act of 1934, as ) AJnended ) DECLARATION OF MARCELLUS NIXON I. My name is Marcellus I ixon. I am the Director ofIP Network Planning at XO Communications, LLC. (XO). My business address is 13865 Sunrise Valley Drive, Hcrndon, VA 20171. 2. I have bcen employed at XO since 2002, initially as an IP Network Engineer. I have been in my current position as Dircctor ofIP Network Planning since 2008. My career with IP nctworks began in the US Army. I have also held networking positions with the NASD and internet MCT. I hold a Bachelor ofInterdisciplinary Studies from the University of Virginia. 3. In my current position, I am responsible for all strategic aspects of IP network planning, and I am the peering coordinator for XO. In that capacity, I manage relationships with other Tier I and lower tier Internet Backbone Providers (lI3Ps), including detennining wbere peering occurs, evaluating network arcbitecture needs such as capacity requirements, routing requirements, and the impact of technological changes on the peering arrangement. I also am responsible for negotiating interconnection (peering) agreements. To date, I have negotiated on behalf ofXO forty-seven (47) peering agreements. -

Networking and the Internet
Networking and Today’s lecture the Internet History of the Internet How the Internet works Lecture 4 – COMPSCI111/111G S2 2018 Network protocols The telephone WWII and the Cold War 1876: first successful bi-directional Computer technology played an important role transmission of clear speech in code-breaking during WW2 by Alexander Bell and Thomas Watson Cold War between US and USSR led to a technology and arms race Peaked with the launch of Sputnik in 1957 1958: Advanced Research Projects Agency (ARPA) 1940: first successful transmission established of digital data through over telegraph wires by George Stibitz April 1969: construction of ARPANET begins, a packet-switching network Circuit-switching network Packet-switching network Nodes are connected physically via a central Data is broken into packets, which are then sent node on the best route in the network Used by the telephone network Each node on the route sends the packet onto its next destination, avoiding congested or broken Originally, switchboard operators had to nodes manually connect phone calls, today this is done electronically B A ARPANET ARPANET in 1977 October 1969: ARPANET is completed with four nodes 1973: Norway connects to ARPANET via satellite, followed by London via a terrestrial link ARPANET ARPANET to the Internet 1983: TCP/IP implemented in ARPANET Networks similar to ARPANET sprang up around the USA and in other countries 1990: ARPANET is formally decommissioned 1984: domain name system (DNS) implemented 1985: NSFNET was established 1989: Waikato University connects to NSFNET 1991: World Wide Web (WWW) created at CERN (European Organization for Nuclear Research) by Tim Berners-Lee 1995: NSFNET is retired WWW vs Internet Internet growth The Internet is a global system of interconnected computer networks. -

The Internet ! Based on Slides Originally Published by Thomas J
15-292 History of Computing The Internet ! Based on slides originally published by Thomas J. Cortina in 2004 for a course at Stony Brook University. Revised in 2013 by Thomas J. Cortina for a computing history course at Carnegie Mellon University. A Vision of Connecting the World – the Memex l Proposed by Vannevar Bush l first published in the essay "As We May Think" in Atlantic Monthly in 1945 and subsequently in Life Magazine. l "a device in which an individual stores all his books, records, and communications, and which is mechanized so that it may be consulted with exceeding speed and flexibility" l also indicated the idea that would become hypertext l Bush’s work was influential on all Internet pioneers The Memex The Impetus to Act l 1957 - U.S.S.R. launches Sputnik I into space l 1958 - U.S. Department of Defense responds by creating ARPA l Advanced Research Projects Agency l “mission is to maintain the technological superiority of the U.S. military” l “sponsoring revolutionary, high-payoff research that bridges the gap between fundamental discoveries and their military use.” l Name changed to DARPA (Defense) in 1972 ARPANET l The Advanced Research Projects Agency Network (ARPANET) was the world's first operational packet switching network. l Project launched in 1968. l Required development of IMPs (Interface Message Processors) by Bolt, Beranek and Newman (BBN) l IMPs would connect to each other over leased digital lines l IMPs would act as the interface to each individual host machine l Used packet switching concepts published by Leonard Kleinrock, most famous for his subsequent books on queuing theory Early work Baran (L) and Davies (R) l Paul Baran began working at the RAND corporation on secure communications technologies in 1959 l goal to enable a military communications network to withstand a nuclear attack. -

Mapping Peering Interconnections to a Facility
Mapping Peering Interconnections to a Facility Vasileios Giotsas Georgios Smaragdakis Bradley Huffaker CAIDA / UC San Diego MIT / TU Berlin CAIDA / UC San Diego [email protected] [email protected] bhuff[email protected] Matthew Luckie kc claffy University of Waikato CAIDA / UC San Diego [email protected] [email protected] ABSTRACT CCS Concepts Annotating Internet interconnections with robust phys- •Networks ! Network measurement; Physical topolo- ical coordinates at the level of a building facilitates net- gies; work management including interdomain troubleshoot- ing, but also has practical value for helping to locate Keywords points of attacks, congestion, or instability on the In- Interconnections; peering facilities; Internet mapping ternet. But, like most other aspects of Internet inter- connection, its geophysical locus is generally not pub- lic; the facility used for a given link must be inferred to 1. INTRODUCTION construct a macroscopic map of peering. We develop a Measuring and modeling the Internet topology at the methodology, called constrained facility search, to infer logical layer of network interconnection, i. e., autonomous the physical interconnection facility where an intercon- systems (AS) peering, has been an active area for nearly nection occurs among all possible candidates. We rely two decades. While AS-level mapping has been an im- on publicly available data about the presence of net- portant step to understanding the uncoordinated forma- works at different facilities, and execute traceroute mea- tion and resulting structure of the Internet, it abstracts surements from more than 8,500 available measurement a much richer Internet connectivity map. For example, servers scattered around the world to identify the tech- two networks may interconnect at multiple physical lo- nical approach used to establish an interconnection. -

Review of the Development and Reform of the Telecommunications Sector in China”, OECD Digital Economy Papers, No
Please cite this paper as: OECD (2003-03-13), “Review of the Development and Reform of the Telecommunications Sector in China”, OECD Digital Economy Papers, No. 69, OECD Publishing, Paris. http://dx.doi.org/10.1787/233204728762 OECD Digital Economy Papers No. 69 Review of the Development and Reform of the Telecommunications Sector in China OECD Unclassified DSTI/ICCP(2002)6/FINAL Organisation de Coopération et de Développement Economiques Organisation for Economic Co-operation and Development 13-Mar-2003 ___________________________________________________________________________________________ English text only DIRECTORATE FOR SCIENCE, TECHNOLOGY AND INDUSTRY COMMITTEE FOR INFORMATION, COMPUTER AND COMMUNICATIONS POLICY Unclassified DSTI/ICCP(2002)6/FINAL REVIEW OF THE DEVELOPMENT AND REFORM OF THE TELECOMMUNICATIONS SECTOR IN CHINA text only English JT00140818 Document complet disponible sur OLIS dans son format d'origine Complete document available on OLIS in its original format DSTI/ICCP(2002)6/FINAL FOREWORD The purpose of this report is to provide an overview of telecommunications development in China and to examine telecommunication policy developments and reform. The initial draft was examined by the Committee for Information, Computer and Communications Policy in March 2002. The report benefited from discussions with officials of the Chinese Ministry of Information Industry and several telecommunication service providers. The report was prepared by the Korea Information Society Development Institute (KISDI) under the direction of Dr. Inuk Chung. Mr. Dimitri Ypsilanti from the OECD Secretariat participated in the project. The report benefited from funding provided mainly by the Swedish government. KISDI also helped in the financing of the report. The report is published on the responsibility of the Secretary-General of the OECD. -

Competitive Effects of Internet Peering Policies
Competitive Effects of Internet Peering Policies by Paul Milgrom, Bridger Mitchell and Padmanabhan Srinagesh Reprinted from The Internet Upheaval, Ingo Vogelsang and Benjamin Compaine (eds), Cambridge: MIT Press (2000): 175-195. ABSTRACT This paper analyzes of two kinds of Internet interconnection arrangements: peering relationships between core Internet Service Providers (ISPs) and transit sales by core ISPs to other ISPs. Core backbone providers jointly produce an intermediate output -- full routing capability -- in an upstream market. All ISPs use this input to produce Internet-based services for end users in a downstream market. It is argued that a vertical market structure with relatively few core ISPs can be relatively efficient given the technological economies of scale and transaction costs arising from Internet addressing and routing. The analysis of costs identifies instances in which an incumbent core ISP’s refusal to peer with a rival or potential rival might promote economic efficiency. A separate bargaining analysis of peering relationships identifies conditions under which a core ISP might be able to use its larger size and associated network effects to refuse to peer with a rival, thus raising its rival’s costs and ultimately increasing prices to end users. An economic analysis of competitive harm arising from refusals to peer should consider cost-based, efficiency-enhancing justifications as well as attempts to raise rivals’ costs. Paul Milgrom Bridger Mitchell and Padmanabhan Srinagesh Department of Economics Charles River Associates Stanford University 285 Hamilton Avenue Stanford, CA 94305-6072 Palo Alto, CA 94301 2 1 Introduction This paper describes the technology and organization of Internet services markets and analyses how peering arrangements among core Internet Service Providers (ISPs) can affect efficiency and competition in these markets. -

Guidelines for the Secure Deployment of Ipv6
Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks NIST Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 December 2010 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Dr. Patrick D. Gallagher, Director GUIDELINES FOR THE SECURE DEPLOYMENT OF IPV6 Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-119 Natl. Inst. Stand. Technol. Spec. Publ. 800-119, 188 pages (Dec. 2010) Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately.