Resiliency Research Snapshot
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Brochure GIFAS Formation
formations et métiers Confrontée à la crise de la Covid-19 et à ses conséquences sur le trafc aérien mondial, la flière aéronautique et spatiale vit une situation sans précédent. La flière fait face et prépare l’avenir avec le soutien de l’Etat et des Régions en accélérant la recherche et la préparation de l’avion neutre en carbone, connecté et digital, dès le début de la prochaine décennie. Ce projet ambitieux est réalisable. Pour le mener à bien, il s’agit de faire évoluer les expertises d’aujourd’hui et anticiper les compétences clés de demain. Les entreprises de la flière se mobilisent donc sur la formation de leurs équipes actuelles et fu- tures. lls peuvent s’appuyer en cela sur un tissu d’établissements d’enseignement scolaire et supé- rieur qui dispensent des cursus dédiés à l’aéronautique et à l’espace. Cette brochure recense les établissements et les diplômes et titres préparés dans les différentes régions de France. Elle a vocation à informer les jeunes et leurs parents pour les aider dans leur choix d’orientation en matière de formation ou de reconversion professionnelle. Les formations indiquées sont également consultables sur aeroemploiformation.com, site portail de référence pour l’emploi et la formation du secteur aéronautique et spatial. GIFAS – Septembre 2020 sommaire L’INDUSTRIE AÉRONAUTIQUE ET SPATIALE P. 08 : Une flière d’excellence innovante, solidaire et dynamique P. 10 : Les secteurs d’activités et les entreprises P. 14 : Panorama des métiers P. 16 : S'informer et s'orienter LES OPÉRATEURS ET TECHNICIENS D’ATELIERS Du CAP au BAC PRO P. -

ISNCC 2021 Technical Program Committee
2021 ISNCC 2021 Technical Program Committee International Symposium on June 1 – 3, 2021, Dubaï – UAE ISNCCNetworks, Computers and Communications www.isncc-conf.org Technical Program Chairs Michele Luglio, University of Rome Tor Vergata, Rome, Italy Rim Moussa, University of Carthage, Tunisia Lidong Zhu, University of Electronic Science and Technology of China, China Wireless and Mobile Networks Dalei Wu, University of Tennessee at Chattanooga (UTC), USA Nawel Zangar, ESIEE, France Kaneko Megumi, National Institute of Informatics, Japan Francesco Zampognaro, University of Rome Tor Vergata, Rome, Italy Satellite Communication Networks Cesare Roseti, University of Rome Tor Vergata, Rome, Italy Mingchuan Yang, Harbin Institute of Technology, China Smart Communications Systems Khmaies Ouahada, University of Johannesburg, South Africa Andreas Pitsillides, University of Cyprus, Cyprus Yue Xiao, University of Electronic Science and Technology of China, China Artificial Intelligence and Machine Learning Serguei A. Mokhov, Concordia University, Canada Mohab Mangoud, University of Bahrain, Bahrain Jihene Rezgui, College Maisonneuve and University of Montreal, Canada Suat Ozdemir, Gazi University, Turkey Data Science and Big Data Systems Engineering Mohamed Reda Bouadjenek, University of Toronto, Canada Abderrahmane Maaradji, Queensland University of Technology, Australia Abdulsalam Yassine, University of Ottawa, Canada Blockchains and Finance Technology Manki Min, Louisiana Tech University, USA Imene Latrous, University of Chicoutimi, Canada Cloud, -

Romuald Gallet, Appointed Director of Executive Education of Institut Mines-Telecom Business School
Evry, October 20, 2020 Press Release Romuald Gallet, appointed Director of Executive Education of Institut Mines-Telecom Business School Developing executive education is a major challenge for Institut Mines-Telecom Business School. The school therefore creates a department dedicated to that activity, reporting directly to the Dean of the school, and it announces the recruitment of Romuald Gallet as Director since October 12, 2020. This recruitment is part of the 5-year strategic project adopted by the School Council in November 2019, aimed at significantly developing the revenues linked to executive education by 2024. After a career as an HR Consultant in the IT / Telecoms sector, Romuald Gallet joined INSEAD, first to structure the career center and then to lead the Executive Education activity for France, Benelux and Southern Europe. Romuald then developed a research center dedicated to family businesses at EDHEC, in charge of all projects related to the financing, the visibility of the structure, and the set-up of a dedicated executive education program. He then headed the school's corporate relations, before joining EMLYON as Director of Executive Education Development. He there worked on the repositioning of the brand, the overhaul of the portfolio and the adaptation to the new regulatory context related to professional education. Lawyer by education, Romuald is also an INSEAD graduate. "I am happy to welcome Romuald to my management team in order to achieve the school's ambitions in this area”, commented Denis Guibard, Dean of Institut Mines-Telecom Business School. “Romuald brings with him a deep expertise and great transformation and development dynamics. -

Data Analysis and Pattern Classification MASTER of SCIENCE
DATA ANALYSIS AND PATTERN CLASSIFICATION MASTER OF SCIENCE ACCREDITATION COURSE AIMS Program accredited by the French Ministry of Higher Education This MSc degree meets the needs of data processing and Research. contained in megabases. It is designed to provide the tools This program can lead to an enrollment in a PhD program. allowing processing of all types of real data captured by sensors used in the sectors of genomics, geolocalisation, KEY WORDS economics, telemedicine, biometrics, etc. Automatic classification, multi-sensor data, signal processing, At the end of the two-year program, students will be able to statistical models, data fusion, computer vision, data analysis, model real and noisy data, to retrieve information in very large content-based indexing and retrieval, multimedia databases. databases, and to conceive complex systems based on such techniques. SCHOOL PROPOSING THE MASTER Telecom SudParis PROGRAM 1st semester LOCATION >>Computer Science Telecom SudParis has a 12-acre campus situated 35 minutes >>Effective Communication from the center of Paris and 20 min away from the gorgeous >>Probability and Statistics “Forêt de Fontainebleau”, thus offering the advantages of both >>Optimization methods the city and the countryside. >>Application of Statistical methods STRONG POINTS OF THE SCHOOL >>French as a foreign language Telecom SudParis is one of the French leading Graduate 2nd semester Schools of Engineering in the field of Information Technology. >>Pattern Recognition & Biometrics More than 60 different nationalities are represented on its >>Signal Enhancement Methods campus. Telecom SudParis is a flagship in the French research >>Safety and secure Operational Systems environment. >>Advanced Statistical Techniques Strong links with industry have made it possible for Telecom >> SudParis to reach excellence in active pedagogy, project- Scientific Project >> based teaching and top-level research. -

Classement Par Filière.Pdf
Classement par spécialités ou filières dans l’école 2 Chimie Ce classement est très approximatif, en effet chaque école, sauf de rares exceptions, 7 UTC Amiens, 15 ISPA Alençon, 28 PHELMA Grenoble, offre une formation assez généraliste et des cours de Mathématiques, Physique, Mécanique, 41 Polytech Lille, 47 ITECH Lyon, 53 CPE Lyon, 63 ENSIC Nancy, 105 INSA Informatique, pour ne parler que des sciences, sont proposés. De plus, pour préparer les Rouen, 119 ENSIACET Toulouse, 128 ESPCI Paris étudiants aux demandes futures, les modules changent très souvent. Ainsi, pour un lecteur intéressé par une formation spécifique, il est conseillé de regarder des 3 Défense domaines voisins et d’affiner la recherche en consultant le site de chaque école visée. Armement Les numéros renvoient à la première liste. Les écoles qui avaient le symbole G pour 91 ENSTA Bretagne généraliste sont absentes pour le classement par spécialité. Ecoles militaires 4 Ecole de l’Air Salon-de-Provence, 89 NAVALE Brest, 97 St Cyr Guer, 158 X Palaiseau 1 Bâtiment, travaux publics Infrastructures militaires ENSIM( 123 ENSAM) Architecture 52 ENTPE, 133 ESTP, 112 INSA Strasbourg, 125 EIVP Paris 4 Electricité Bâtiment 3 Polytech Marseille, 12 ISA Pau, 18 ESITC Caen, 25 Polytech Annecy, Energie 52 ENTPE Lyon, 60 ESITC Caen, 70 ISTIA Angers, 123 ENSIM Angers, 64 ENSEM Nancy, 83 Polytech Tours, 85 ENSIP Poitiers 132 ESITC Cachan,133 ESTP Cachan Génie électrique Energie et bâtiment 5 ESIEE Amiens, 21 Polytech Clermont-Ferrand, 106 ESIGELEC Rouen, 3 Polytech Marseille, 5 ESIEE Amiens,12 -

VTC2011-Spring Final Program
The 73rd IEEE Vehicular Technology Conference Final Programme 15 - 18 May 2011 Budapest, Hungary Welcome from the General Chair Dear Colleagues, Allow me to commence by welcoming you to VTC It is my privilege to convey the community's 2011 Spring in the vibrant city of Budapest! I have gratitude to the conference patrons, namely to been faithfully attending VTC for the past two Ericsson, Huawei Technologies, HTE and Wiley- decades and I have a vivid recollection of this Blackwell. Needless to say that a lot of further dynamic period of spectacular growth across the volunteers contributed in numerous ways to the wireless communications industry. success of the conference. My hope is that you would enjoy the rich technical On a technical note, the advances of the past three blend of plenaries and panels presented by decades facilitated a 1000-fold throughput distinguished industrial and academic leaders improvement, but naturally, this was achieved at converging on Budapest from all over the globe. the cost of a substantially increased power These will also be complemented by tutorials, consumption. In the light of the escalating energy workshops and the regular technical sessions. prices this motivated the design of ‘green radios’, aiming for more power-efficient solutions – all in I am indebted to the entire organizing and technical all, an exciting era for our community. program committee, especially to the TPC Co- Chairs Drs Andrea Conti, Iain Collings and Wei My hope is that you, dear Colleague will enjoy the Chen for their generous support as well as to all the technical discussions, meeting old friends and Track Chairs for their dedication. -
Technical Program for IEEEGCC 2009
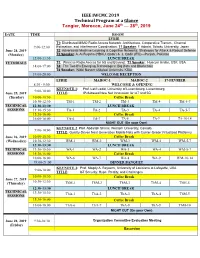
IEEE IWCMC 2019 Technical Program at a Glance Tangier, Morocco, June 24th — 28th, 2019 DATE TIME ROOM LYBIE T1: Distributed MIMO Radio Access Network: Architecture, Cooperative Transm., Channel 9:00-12:00 Estimation, and Interference Coordination; T1 Speaker: F. Adachi, Tohoku University, Japan June 24, 2019 T2: Adversarial Machine Learning & Cognitive Networks: Strategies for Attack & Robust Defense (Monday) T2 Speaker: A. Al-Fuqaha (HBKU, Qatar) & J. Qadir (ITU)—Punjab, Pakistan 12:00-13:30 LUNCH BREAK TUTORIALS T3: Wireless Radio Access for 5G and Beyond; T3 Speaker: Huseyin Arslan, USF, USA 14:00-17:00 T4: The Two B's Emerging Technologies: Big Data and Blockchain T4 Speaker: Nidal Nasser (Alfaisal University, KSA) 19:00-20:00 WELCOME RECEPTION i LYBIE MAROC-1 MAROC-2 17-FEVRIER 8:30 - 9:00 WELCOME & OPENING KEYNOTE 1: Prof. Latif Ladid, University of Luxembourg, Luxembourg 9:00-10:00 June 25, 2019 TITLE: IPv6-based New Net Innovation for IoT and 5G (Tuesday) 10:00-10:30 Coffee Break 10:30-12:30 TM-1 TM-2 TM-3 TM-4 TM-5-7 TECHNICAL 12:30-13:30 LUNCH BREAK SESSIONS 13:30-15:30 TA-1 TA-2 TA-3 TA-4 TA-5-7 15:30-16:00 Coffee Break 16:00-18:00 TA-6 TA-7 TA-8 TA-9 TA-10-14 NIGHT OUT (On your Own) KEYNOTE 2: Prof. Abdallah Shami, Western University, Canada 9:00-10:00 TITLE: Quality-Driven Next Generation Mobile Nets with Carrier-Grade Virtualized Platforms June 26, 2019 10:00-10:30 Coffee Break (Wednesday) 10:30-12:30 WM-1 WM-2 WM-3 WM-4 WM-5-7 12:30-13:30 LUNCH BREAK TECHNICAL 13:30-15:30 WA-1 WA-2 WA-3 WA-4 WM-5-7 SESSIONS 15:30-16:00 Coffee Break 16:00-18:00 WA-6 WA-7 WA-8 WA-9 WM-10-14 19:00-21:00 DINNER BANQUET KEYNOTE 3: Prof. -

Programme Par Institution
La Science près de chez vous Complexe sportif – Gymnase du Moulon Chemin de Moulon – Gif-sur-Yvette (91) du 8 au 16 octobre 2016 (Près de Supélec) PROGRAMME DES 14, 15 et 16 OCTOBRE 2016 Présentation par Institution AgroParisTech ATELIER DOOF : MIEUX COMPRENDRE POUR MIEUX CONCEVOIR LES ALIMENTS Se nourrir est une nécessité, mais nous ne savons pas toujours comment sont fabriqués les aliments, à partir de quels ingrédients, pour finalement obtenir quelles caractéristiques ? L’objectif de cet atelier est de faire découvrir les aliments de notre quotidien : produits transformés à base de viande ou de poisson, produits céréaliers, laitiers ou encore à base de fruits. Le surimi, qu’est-ce que c’est ? Pourquoi y a t’il des trous dans certains fromages ? Quel produit laitier est le plus riche en calcium ? Comment lire les étiquettes sur les emballages ? Suivez DOOF à la rencontre des aliments ! ATELIER DD : MIEUX CONCEVOIR LES ALIMENTS POUR MIEUX PRESERVER LA PLANETE Se nourrir est une nécessité, mais nous ne savons pas toujours comment sont fabriqués les aliments, à partir de quels ingrédients, loin ou près de chez nous ? Sont-ils transportés depuis l’autre bout du monde ? Est-ce qu’ils demandent beaucoup d’énergie pour être mélangés, chauffés, refroidis ? Comment savoir quel est l’impact sur la planète ? Quels sont les bons réflexes pour mieux conserver et moins gaspiller ? DD vous propose de tourner la Roue des Aliments pour en apprendre plus sur le cycle de vie de produits de tous les jours et mieux préserver la planète. SVAD : BEEF OR PASTA Ce projet est le fruit d’une rencontre entre un vidéaste, un animateur, un dessinateur d’une part, et un neurobiologiste du comportement alimentaire d’autre part. -

2013 IEEE 24Th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications
2013 IEEE 24th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC 2013) London, United Kingdom 8 - 11 September 2013 Pages 1-723 IEEE Catalog Number: CFP13PIM-POD ISBN: 978-1-4673-6233-7 1/5 Program APP1: Communication Systems & Applications - I Attainable User Throughput by Dense Wi-Fi Deployment at 5 GHz Du Ho Kang (Royal Institute of Technology (KTH), Sweden); Ki Won Sung (KTH Royal Institute of Technology, Sweden); Jens Zander (KTH Royal Institute of Technology, Sweden) pp. 3418-3422 Femtocell deployment in LTE-A networks: a sustainability, economical and capacity analysis Filipe Vaz (ISCTE-IUL / IT & Cisco Systems, Inc, Portugal); Pedro Sebastião (ISCTE, Instituto de Telecomunicações, Portugal); Luis Carlos BS Goncalves (ISCTE-IUL/Instituto de Telecomunicações & Instituto de Telecomunicações, Portugal); Américo Correia (Instituto de Telecomunicações, Portugal) pp. 3423-3427 Geo-Location Database with Support of Quality of Service for TV White Space Chin Choy Chai (Institute for Infocomm Research, Singapore); Ser Wah Oh (Institute for Infocomm Research, Singapore) pp. 3428-3433 The profitability analysis of the multi-band spectrum broker Marcin Parzy (Poznan University of Technology, Poland) pp. 3434-3438 The viability of providing mobile broadband with cognitive femtocells Ole Grøndalen (Telenor, Norway); Marrku Lähteenoja (Telenor, Norway); Per H. Lehne (Telenor Group Industrial Development, Norway); Richard MacKenzie (BT Research, United Kingdom) pp. 3439-3444 MAC1: Cross-Layer Design Energy Efficient Cross-Layer Design for Wireless Body Area Monitoring Networks in Healthcare Applications Alaa Awad (Cairo Univ, Egypt); Amr Mohamed (Qatar University & Qatar University Wireless Innovations Center, Qatar); Amr El-Sherif (Alexandria University, Egypt) pp. 1484-1489 Coding, diversity and ARQ in fading channels: a case-study performance comparison Anna Vanyan (ESME Sudria & LSS Supelec, France); Francesca Bassi (LSS-CNRS-Supelec, France); Aude Herry (ESME Sudria, France); Pierre Duhamel (Lss Supelec & CNRS, France) pp. -

Agroparistech Les Spécialités De Masters STVE
AgroParisTech Les spécialités de Masters STVE Sciences et Technologies du Vivant et de l’Environnement AgroParisTech 16, rue Claude Bernard 75231 Paris Cedex 05 www.agroparistech.fr Contact Direction de l'Enseignement et de la Vie Étudiante : Pascale Pottier [email protected] Tél : 01 44 08 37 02 L'ETABLISSEMENT / LES GRANDS DOMAINES DE COMPETENCE Confronté aux grands défis du développement durable de la planète, de l’alimentation des hommes, de la gestion des ressources naturelles et du respect de l’environnement, le XXIe siècle sera aussi marqué par l'importance majeure des innovations dans les sciences et technologies du vivant et de l’environnement. Avec 2000 étudiants dont 450 doctorants, 230 enseignants-chercheurs, associés à 450 chercheurs dans une trentaine d'unités de recherche couvrant un très large spectre disciplinaire, AgroParisTech est la plus grande école européenne dans le domaine des sciences et technologies du vivant et de l’environnement. En mobilisant les interfaces entre sciences et techniques et gestion des politiques publiques, AgroParisTech offre une très large gamme de parcours de formation aux ingénieurs, masters et docteurs et les adapte en permanence pour répondre aux évolutions des besoins de nos sociétés. Comme son nom l'indique, AgroParisTech est membre de ParisTech, Établissement Public de Coopération Scientifique, qui regroupe 12 prestigieuses grandes écoles d'ingénieurs et de management situées en région parisienne, dont l'Ecole Polytechnique. AgroParisTech s'organise autour de 5 grandes -

Europe and Africa
Destination Institution Program Brochure Austria Graz University of Technology U-wide, Architecture Brochure Austria University of Graz U-wide Brochure Austria University of Vienna U-wide Brochure Austria Vienna University of Economics and Business U-wide, Shaw College, Morningside College Brochure Austria Vienna University of Economics and Business Summer Belgium Katholieke Universiteit Leuven U-wide, Chung Chi College Brochure Czech Republic Prague University of Economics and Business U-wide, New Asia College, Wu Yee Sun College Brochure Denmark Aarhus University C.W. Chu College Brochure Denmark Aarhus University Summer Denmark Copenhagen Business School U-wide Brochure Denmark Copenhagen Business School MBA Denmark Copenhagen Business School Summer Denmark Technical University of Denmark U-wide, New Asia College, Shaw College, Morningside Brochure College, Lee Woo Sing College Denmark University of Copenhagen U-wide Brochure Finland University of Helsinki U-wide Finland University of Helsinki Summer Finland University of Oulu United College Brochure Finland University of Tampere U-wide, Shaw College, Lee Woo Sing College, Wu Yee Brochure Sun College France HEC Paris U-wide, MBA France Ecole Superieure des Sciences Economiques et Commerciales (ESSEC) MBA France Sciences Po U-wide France Institut Mines-Télécom Business School BA Brochure France Institut Mines-Télécom Business School Summer France TELECOM SudParis Engineering France EDHEC Business School France Universite Catholique de Lille (FGES (Faculté d'Economie, Gestion & Sciences)) -

Ecoles Ingénieurs Classées 2017- Spécialités-Voie Admission
APRES LA TSI, VOUS INTÉGREZ UNE ÉCOLE D’INGÉNIEURS… DANS QUEL DOMAINE ? Concours Centrale Supelec (CCS) (colonne 1) Ecoles Groupe Concours Polytechnique (CCP) (colonne 1) Admission sur banques de notes CCP (colonne 2) Ecoles sur dossier et entretien (colonne 3) Une école en italique demande des frais de scolarité supérieurs à 6000 € par an. Ce document ne tient pas compte des écoles sur dossier comme UTC, UTBM, ENI, INSA, … Ecoles Généralistes avec en général spécialisations en 2ème ou 3 ème année Ecole Polytechnique (2) ENSTA ParisTech (2) Centrale Lyon (5) Ponts ParisTech (1) Centrale Lille (5) ECAM Lyon (admissibilité CCS Centrale Marseille (5) Mines d'Albi (2) ou CCP + dossier) Centrale Nantes (10) Mines d'Alès (2) ECAM Strasbourg Centrale Paris (10) IMT/Mines de Douai (2) EIGSI La Rochelle Centrale Casablanca (2) IMT/Mines de Nantes (2) Mines ParisTech Paris (2) Mines de Nancy (2) ECAM Rennes (10) Mines de St Etienne (2) Enseignement - Recherche ENS Cachan (4) fonctionnaire Génie électrique Génie Mécanique ENS Rennes (2) Génie Civil Mécatronique (à Rennes) Mécanique - Génie Mécanique - Génie Industriel SIGMA Clermont-Ferd (8) ESTIA Bidart-Biarritz (30) Arts et Métiers (35) ESTP Paris (18) EPF (dossier + entretien) ISMANS Le Mans (20) ENSTA Bretagne (2) HEI Lille (dossier+entretien) ENSE3 Grenoble (3) ENI Tarbes (8) ISBS Créteil (BioSciences ENSEM Nancy (5) ENSISA Mulhouse (15) dossier) ENSIAME Valenciennes (16) ISTIL Lyon (GEIPI-Polytech) ISIFC Besançon (Biomédical ENSMA Poitiers (2) EIL – Côte d’Opale (15) dossier) ENSMM Besançon