The Root of All Evil? – Rootkits Revealed
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Trojan Vs Rat Vs Rootkit Mayuri More1, Rajeshwari Gundla2, Siddharth Nanda3 1U.G
IJRECE VOL. 7 ISSUE 2 (APRIL- JUNE 2019) ISSN: 2393-9028 (PRINT) | ISSN: 2348-2281 (ONLINE) Trojan Vs Rat Vs Rootkit Mayuri More1, Rajeshwari Gundla2, Siddharth Nanda3 1U.G. Student, 2 Senior Faculty, 3Senior Faculty SOE, ADYPU, Lohegaon, Pune, Maharashtra, India1 IT, iNurture, Bengaluru, India2,3 Abstract - Malicious Software is Malware is a dangerous of RATs completely and prevent confidential data being software which harms computer systems. With the increase leaked. So Dan Jiang and Kazumasa Omote researchers in technology in today’s days, malwares are also increasing. have proposed an approach to detect RAT in the early stage This paper is based on Malware. We have discussed [10]. TROJAN, RAT, ROOTKIT in detail. Further, we have discussed the adverse effects of malware on the system as III. CLASSIFICATION well as society. Then we have listed some trusted tools to Rootkit vs Trojan vs Rat detect and remove malware. Rootkit - A rootkit is a malicious software that permits a legitimate user to have confidential access to a system and Keywords - Malware, Trojan, RAT, Rootkit, System, privileged areas of its software. A rootkit possibly contains Computer, Anti-malware a large number of malicious means for example banking credential stealers, keyloggers, antivirus disablers, password I. INTRODUCTION stealers and bots for DDoS attacks. This software stays Nowadays, this world is full of technology, but with the hidden in the computer and allocates the remote access of advantages of technology comes its disadvantages like the computer to the attacker[2]. hacking, corrupting the systems, stealing of data etc. These Types of Rootkit: malpractices are possible because of malware and viruses 1. -

Cross-Platform Analysis of Indirect File Leaks in Android and Ios Applications
Cross-Platform Analysis of Indirect File Leaks in Android and iOS Applications Daoyuan Wu and Rocky K. C. Chang Department of Computing, The Hong Kong Polytechnic University fcsdwu, [email protected] This paper was published in IEEE Mobile Security Technologies 2015 [47] with the original title of “Indirect File Leaks in Mobile Applications”. Victim App Abstract—Today, much of our sensitive information is stored inside mobile applications (apps), such as the browsing histories and chatting logs. To safeguard these privacy files, modern mobile Other systems, notably Android and iOS, use sandboxes to isolate apps’ components file zones from one another. However, we show in this paper that these private files can still be leaked by indirectly exploiting components that are trusted by the victim apps. In particular, Adversary Deputy Trusted we devise new indirect file leak (IFL) attacks that exploit browser (a) (d) parties interfaces, command interpreters, and embedded app servers to leak data from very popular apps, such as Evernote and QQ. Unlike the previous attacks, we demonstrate that these IFLs can Private files affect both Android and iOS. Moreover, our IFL methods allow (s) an adversary to launch the attacks remotely, without implanting malicious apps in victim’s smartphones. We finally compare the impacts of four different types of IFL attacks on Android and Fig. 1. A high-level IFL model. iOS, and propose several mitigation methods. four IFL attacks affect both Android and iOS. We summarize these attacks below. I. INTRODUCTION • sopIFL attacks bypass the same-origin policy (SOP), Mobile applications (apps) are gaining significant popularity which is enforced to protect resources originating from in today’s mobile cloud computing era [3], [4]. -

Information Disclosure Mechanism for Technological Protection Measures in China
Journal of Intellectual Property Rights Vol 17, November 2012, pp 532-538 Information Disclosure Mechanism for Technological Protection Measures in China Lili Zhao† Center for China Information Security Law, Xi’an Jiao tong University, Shaanxi Xi’an, P R China 710 049 Received 12 February 2012, revised 21 May 2012 With increasing cases of digital works being copied and pirated, technological protection measures have been greatly favoured by copyright owners for protecting the intellectual property in their digital works, while ensuring that these works can be used and disseminated. However, when any copyright owner or supplier fails to disclose the information of technological protection measures appropriately or effectively, damages such as privacy violations, security breaches and unfair competition may be caused to the public. Therefore, it is necessary to establish an information disclosure mechanism for technological protection measures, make the labeling obligation with regard to technological protection measures by copyright owners apparent and warning to security risks obligatory by legislation; effectively guarding against information security threats from the technological protection measures. Keywords: Technological protection measures, TPM, information disclosure, label and warning The advance of digital technologies make many information security, it is necessary to integrate such acts things become possible, including the copy and in a standardized, normalized and legal manner. dissemination of commercially valuable digital works Therefore, to further prevent copyright owners from through global digital network. Particularly, among using insecure or untested software, protect information the copyright owners of entertainment industry, security and prohibit the abuse of TPMs; disclosure technological protection measures (TPMs) have been obligations should be established for the right holders of regarded as a necessary creation to help digital works TPMs in the form of legislation. -

Adware-Searchsuite
McAfee Labs Threat Advisory Adware-SearchSuite June 22, 2018 McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalent malware. This Threat Advisory contains behavioral information, characteristics and symptoms that may be used to mitigate or discover this threat, and suggestions for mitigation in addition to the coverage provided by the DATs. To receive a notification when a Threat Advisory is published by McAfee Labs, select to receive “Malware and Threat Reports” at the following URL: https://www.mcafee.com/enterprise/en-us/sns/preferences/sns-form.html Summary Detailed information about the threat, its propagation, characteristics and mitigation are in the following sections: Infection and Propagation Vectors Mitigation Characteristics and Symptoms Restart Mechanism McAfee Foundstone Services The Threat Intelligence Library contains the date that the above signatures were most recently updated. Please review the above mentioned Threat Library for the most up to date coverage information. Infection and Propagation Vectors Adware-SearchSuite is a "potentially unwanted program" (PUP). PUPs are any piece of software that a reasonably security- or privacy-minded computer user may want to be informed of and, in some cases, remove. PUPs are often made by a legitimate corporate entity for some beneficial purpose, but they alter the security state of the computer on which they are installed, or the privacy posture of the user of the system, such that most users will want to be aware of them. Mitigation Mitigating the threat at multiple levels like file, registry and URL could be achieved at various layers of McAfee products. Browse the product guidelines available here (click Knowledge Center, and select Product Documentation from the Support Content list) to mitigate the threats based on the behavior described in the Characteristics and symptoms section. -

UPLC™ Universal Power-Line Carrier
UPLC™ Universal Power-Line Carrier CU4I-VER02 Installation Guide AMETEK Power Instruments 4050 N.W. 121st Avenue Coral Springs, FL 33065 1–800–785–7274 www.pulsartech.com THE BRIGHT STAR IN UTILITY COMMUNICATIONS March 2006 Trademarks All terms mentioned in this book that are known to be trademarks or service marks are listed below. In addition, terms suspected of being trademarks or service marks have been appropriately capital- ized. Ametek cannot attest to the accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark or service mark. This publication includes fonts and/or images from CorelDRAW which are protected by the copyright laws of the U.S., Canada and elsewhere. Used under license. IBM and PC are registered trademarks of the International Business Machines Corporation. ST is a registered trademark of AT&T Windows is a registered trademark of Microsoft Corp. Universal Power-Line Carrier Installation Guide ESD WARNING! YOU MUST BE PROPERLY GROUNDED, TO PREVENT DAMAGE FROM STATIC ELECTRICITY, BEFORE HANDLING ANY AND ALL MODULES OR EQUIPMENT FROM AMETEK. All semiconductor components used, are sensitive to and can be damaged by the discharge of static electricity. Be sure to observe all Electrostatic Discharge (ESD) precautions when handling modules or individual components. March 2006 Page i Important Change Notification This document supercedes the preliminary version of the UPLC Installation Guide. The following list shows the most recent publication date for the new information. A publication date in bold type indicates changes to that information since the previous publication. -
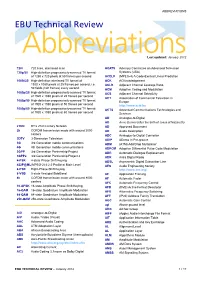
ABBREVIATIONS EBU Technical Review
ABBREVIATIONS EBU Technical Review AbbreviationsLast updated: January 2012 720i 720 lines, interlaced scan ACATS Advisory Committee on Advanced Television 720p/50 High-definition progressively-scanned TV format Systems (USA) of 1280 x 720 pixels at 50 frames per second ACELP (MPEG-4) A Code-Excited Linear Prediction 1080i/25 High-definition interlaced TV format of ACK ACKnowledgement 1920 x 1080 pixels at 25 frames per second, i.e. ACLR Adjacent Channel Leakage Ratio 50 fields (half frames) every second ACM Adaptive Coding and Modulation 1080p/25 High-definition progressively-scanned TV format ACS Adjacent Channel Selectivity of 1920 x 1080 pixels at 25 frames per second ACT Association of Commercial Television in 1080p/50 High-definition progressively-scanned TV format Europe of 1920 x 1080 pixels at 50 frames per second http://www.acte.be 1080p/60 High-definition progressively-scanned TV format ACTS Advanced Communications Technologies and of 1920 x 1080 pixels at 60 frames per second Services AD Analogue-to-Digital AD Anno Domini (after the birth of Jesus of Nazareth) 21CN BT’s 21st Century Network AD Approved Document 2k COFDM transmission mode with around 2000 AD Audio Description carriers ADC Analogue-to-Digital Converter 3DTV 3-Dimension Television ADIP ADress In Pre-groove 3G 3rd Generation mobile communications ADM (ATM) Add/Drop Multiplexer 4G 4th Generation mobile communications ADPCM Adaptive Differential Pulse Code Modulation 3GPP 3rd Generation Partnership Project ADR Automatic Dialogue Replacement 3GPP2 3rd Generation Partnership -

Crimeware on the Net
Crimeware on the Net The “Behind the scenes” of the new web economy Iftach Ian Amit Director, Security Research – Finjan BlackHat Europe, Amsterdam 2008 Who Am I ? (iamit) • Iftach Ian Amit – In Hebrew it makes more sense… • Director Security Research @ Finjan • Various security consulting/integration gigs in the past – R&D – IT • A helping hand when needed… (IAF) 2 BlackHat Europe – Amsterdam 2008 Today’s Agenda • Terminology • Past vs. Present – 10,000 feet view • Business Impact • Key Characteristics – what does it look like? – Anti-Forensics techniques – Propagation methods • What is the motive (what are they looking for)? • Tying it all up – what does it look like when successful (video). • Anything in it for us to learn from? – Looking forward on extrusion testing methodologies 3 BlackHat Europe – Amsterdam 2008 Some Terminology • Crimeware – what we refer to most malware these days is actually crimeware – malware with specific goals for making $$$ for the attackers. • Attackers – not to be confused with malicious code writers, security researchers, hackers, crackers, etc… These guys are the Gordon Gecko‟s of the web security field. The buy low, and capitalize on the investment. • Smart (often mislead) guys write the crimeware and get paid to do so. 4 BlackHat Europe – Amsterdam 2008 How Do Cybercriminals Steal Business Data? Criminals’ activity in the cyberspace Federal Prosecutor: “Cybercrime Is Funding Organized Crime” 5 BlackHat Europe – Amsterdam 2008 The Business Impact Of Crimeware Criminals target sensitive business data -

SMM Rootkits
SMM Rootkits: A New Breed of OS Independent Malware Shawn Embleton Sherri Sparks Cliff Zou University of Central Florida University of Central Florida University of Central Florida [email protected] [email protected] [email protected] ABSTRACT 1. INTRODUCTION The emergence of hardware virtualization technology has led to A rootkit consists of a set of programs that work to subvert the development of OS independent malware such as the Virtual control of an Operating System from its legitimate users [16]. If Machine based rootkits (VMBRs). In this paper, we draw one were asked to classify viruses and worms by a single defining attention to a different but related threat that exists on many characteristic, the first word to come to mind would probably be commodity systems in operation today: The System Management replication. In contrast, the single defining characteristic of a Mode based rootkit (SMBR). System Management Mode (SMM) rootkit is stealth. Viruses reproduce, but rootkits hide. They hide is a relatively obscure mode on Intel processors used for low-level by compromising the communication conduit between an hardware control. It has its own private memory space and Operating System and its users. Secondary to hiding themselves, execution environment which is generally invisible to code rootkits are generally capable of gathering and manipulating running outside (e.g., the Operating System). Furthermore, SMM information on the target machine. They may, for example, log a code is completely non-preemptible, lacks any concept of victim user’s keystrokes to obtain passwords or manipulate the privilege level, and is immune to memory protection mechanisms. -

Intellectual Property Part 2 Pornography
Intellectual Property Part 2 Pornography By Jeremy Parmenter What is pornography Pornography is the explicit portrayal of sexual subject matter Can be found as books, magazines, videos The web has images, tube sites, and pay sites scattered with porn Statistics 12% of total websites are pornography websites 25% of total daily search engine requests are pornographic requests 42.7% of internet users who view pornography 34% internet users receive unwanted exposure to sexual material $4.9 billion in internet pornography sales 11 years old is the average age of first internet exposure to pornography Innovations ● Richard Gordon created an e-commerce start up in mid- 90s that was used on many sites, most notably selling Pamela Anderson/Tommey Lee sex tape ● Danni Ashe founded Danni's Hard Drive with one of the first streaming video without requiring a plug-in ● Adult content sites were one of the first to use traffic optimization by linking to similar sites ● Live chat during the early days of the web ● Pornographic companies were known to give away broadband devices to promote faster connections Negative Impacts ● Between 2001-2002 adult-oriented spam rose 450% ● Malware such as Trojans and video codecs occur most often on porn sites ● Domain hijacking, using fake documents and information to steal a site ● Pop-ups preventing users from leaving the site or infecting their computer ● Browser hijacking adware or spyware manipulating the browser to change home page or search engine to a bogus site, including pay-per-click adult site ● Accessibility -

Nujj University of California, Berkeley School of Information Karen Hsu
Nujj University of California, Berkeley School of Information Karen Hsu Kesava Mallela Alana Pechon Nujj • Table of Contents Abstract 1 Introduction 2 Problem Statement 2 Objective 2 Literature Review 3 Competitive Analysis 4 Comparison matrix 4 Competition 5 Hypothesis 6 Use Case Scenarios 7 Overall System Design 10 Server-side 12 Design 12 Implementation 12 Twitter and Nujj 14 Client-side 15 Design 17 Implementation 17 Future Work 18 Extended Functionality in Future Implementations 18 Acknowledgements 19 Abstract Nujj is a location based service for mobile device users that enables users to tie electronic notes to physical locations. It is intended as an initial exploration into some of the many scenarios made possible by the rapidly increasing ubiquity of location-aware mobile devices. It should be noted that this does not limit the user to a device with a GPS embedded; location data can now also be gleaned through methods such as cell tower triangulation and WiFi IP address lookup. Within this report, both social and technical considerations associated with exposing a user’s location are discussed. The system envisioned addresses privacy concerns, as well as attempts to overcome the poor rate of adoption of current location based services already competing in the marketplace. Although several possible use cases are offered, it is the authors’ firm belief that a well-designed location- based service should not attempt to anticipate all, or even most, of the potential ways that users will find to take advantage of it. Rather, the service should be focused on building a system that is sufficiently robust yet flexible to allow users to pursue their own ideas. -

Lessons from the Sony CD DRM Episode
Lessons from the Sony CD DRM Episode J. Alex Halderman and Edward W. Felten Center for Information Technology Policy Department of Computer Science Princeton University Abstract system called XCP that had been installed when he in- In the fall of 2005, problems discovered in two Sony- serted a Sony-BMG music CD into his computer’s CD BMG compact disc copy protection systems, XCP and drive. MediaMax, triggered a public uproar that ultimately led News of Russinovich’s discovery circulated rapidly on to class-action litigation and the recall of millions of the Internet, and further revelations soon followed, from discs. We present an in-depth analysis of these technolo- us,1 from Russinovich, and from others. It was discov- gies, including their design, implementation, and deploy- ered that the XCP rootkit makes users’ systems more ment. The systems are surprisingly complex and suffer vulnerable to attacks, that both CD DRM schemes install from a diverse array of flaws that weaken their content risky software components without obtaining informed protection and expose users to serious security and pri- consent from users, that both systems covertly transmit vacy risks. Their complexity, and their failure, makes usage information back to the vendor or the music label, them an interesting case study of digital rights manage- and that none of the protected discs include tools for unin- ment that carries valuable lessons for content companies, stalling the software. (For these reasons, both XCP and DRM vendors, policymakers, end users, and the security MediaMax seem to meet the consensus definition of spy- community. ware.) These and other findings outraged many users. -

Windows Internals, Sixth Edition, Part 2
spine = 1.2” Part 2 About the Authors Mark Russinovich is a Technical Fellow in ® the Windows Azure™ group at Microsoft. Windows Internals He is coauthor of Windows Sysinternals SIXTH EDITION Administrator’s Reference, co-creator of the Sysinternals tools available from Microsoft Windows ® The definitive guide—fully updated for Windows 7 TechNet, and coauthor of the Windows Internals and Windows Server 2008 R2 book series. Delve inside Windows architecture and internals—and see how core David A. Solomon is coauthor of the Windows Internals book series and has taught components work behind the scenes. Led by a team of internationally his Windows internals class to thousands of renowned internals experts, this classic guide has been fully updated Windows developers and IT professionals worldwide, SIXTH for Windows 7 and Windows Server® 2008 R2—and now presents its including Microsoft staff. He is a regular speaker 6EDITION coverage in two volumes. at Microsoft conferences, including TechNet As always, you get critical, insider perspectives on how Windows and PDC. operates. And through hands-on experiments, you’ll experience its Alex Ionescu is a chief software architect and internal behavior firsthand—knowledge you can apply to improve consultant expert in low-level system software, application design, debugging, system performance, and support. kernel development, security training, and Internals reverse engineering. He teaches Windows internals courses with David Solomon, and is ® In Part 2, you will: active in the security research community.