Adware-Searchsuite
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Trojan Vs Rat Vs Rootkit Mayuri More1, Rajeshwari Gundla2, Siddharth Nanda3 1U.G
IJRECE VOL. 7 ISSUE 2 (APRIL- JUNE 2019) ISSN: 2393-9028 (PRINT) | ISSN: 2348-2281 (ONLINE) Trojan Vs Rat Vs Rootkit Mayuri More1, Rajeshwari Gundla2, Siddharth Nanda3 1U.G. Student, 2 Senior Faculty, 3Senior Faculty SOE, ADYPU, Lohegaon, Pune, Maharashtra, India1 IT, iNurture, Bengaluru, India2,3 Abstract - Malicious Software is Malware is a dangerous of RATs completely and prevent confidential data being software which harms computer systems. With the increase leaked. So Dan Jiang and Kazumasa Omote researchers in technology in today’s days, malwares are also increasing. have proposed an approach to detect RAT in the early stage This paper is based on Malware. We have discussed [10]. TROJAN, RAT, ROOTKIT in detail. Further, we have discussed the adverse effects of malware on the system as III. CLASSIFICATION well as society. Then we have listed some trusted tools to Rootkit vs Trojan vs Rat detect and remove malware. Rootkit - A rootkit is a malicious software that permits a legitimate user to have confidential access to a system and Keywords - Malware, Trojan, RAT, Rootkit, System, privileged areas of its software. A rootkit possibly contains Computer, Anti-malware a large number of malicious means for example banking credential stealers, keyloggers, antivirus disablers, password I. INTRODUCTION stealers and bots for DDoS attacks. This software stays Nowadays, this world is full of technology, but with the hidden in the computer and allocates the remote access of advantages of technology comes its disadvantages like the computer to the attacker[2]. hacking, corrupting the systems, stealing of data etc. These Types of Rootkit: malpractices are possible because of malware and viruses 1. -

A Crawler-Based Study of Spyware on the Web
A Crawler-based Study of Spyware on the Web Alexander Moshchuk, Tanya Bragin, Steven D. Gribble, and Henry M. Levy Department of Computer Science & Engineering University of Washington {anm, tbragin, gribble, levy}@cs.washington.edu Abstract servers [16]. The AOL scan mentioned above has provided simple summary statistics by directly examining desktop in- Malicious spyware poses a significant threat to desktop fections [2], while a recent set of papers have considered security and integrity. This paper examines that threat from user knowledge of spyware and its behavior [6, 29]. an Internet perspective. Using a crawler, we performed a In this paper we change perspective, examining the na- large-scale, longitudinal study of the Web, sampling both ture of the spyware threat not on the desktop but from an executables and conventional Web pages for malicious ob- Internet point of view. To do this, we conduct a large-scale jects. Our results show the extent of spyware content. For outward-looking study by crawling the Web, downloading example, in a May 2005 crawl of 18 million URLs, we found content from a large number of sites, and then analyzing it spyware in 13.4% of the 21,200 executables we identified. to determine whether it is malicious. In this way, we can At the same time, we found scripted “drive-by download” answer several important questions. For example: attacks in 5.9% of the Web pages we processed. Our analy- sis quantifies the density of spyware, the types of of threats, • How much spyware is on the Internet? and the most dangerous Web zones in which spyware is • Where is that spyware located (e.g., game sites, chil- likely to be encountered. -

Crimeware on the Net
Crimeware on the Net The “Behind the scenes” of the new web economy Iftach Ian Amit Director, Security Research – Finjan BlackHat Europe, Amsterdam 2008 Who Am I ? (iamit) • Iftach Ian Amit – In Hebrew it makes more sense… • Director Security Research @ Finjan • Various security consulting/integration gigs in the past – R&D – IT • A helping hand when needed… (IAF) 2 BlackHat Europe – Amsterdam 2008 Today’s Agenda • Terminology • Past vs. Present – 10,000 feet view • Business Impact • Key Characteristics – what does it look like? – Anti-Forensics techniques – Propagation methods • What is the motive (what are they looking for)? • Tying it all up – what does it look like when successful (video). • Anything in it for us to learn from? – Looking forward on extrusion testing methodologies 3 BlackHat Europe – Amsterdam 2008 Some Terminology • Crimeware – what we refer to most malware these days is actually crimeware – malware with specific goals for making $$$ for the attackers. • Attackers – not to be confused with malicious code writers, security researchers, hackers, crackers, etc… These guys are the Gordon Gecko‟s of the web security field. The buy low, and capitalize on the investment. • Smart (often mislead) guys write the crimeware and get paid to do so. 4 BlackHat Europe – Amsterdam 2008 How Do Cybercriminals Steal Business Data? Criminals’ activity in the cyberspace Federal Prosecutor: “Cybercrime Is Funding Organized Crime” 5 BlackHat Europe – Amsterdam 2008 The Business Impact Of Crimeware Criminals target sensitive business data -

SMM Rootkits
SMM Rootkits: A New Breed of OS Independent Malware Shawn Embleton Sherri Sparks Cliff Zou University of Central Florida University of Central Florida University of Central Florida [email protected] [email protected] [email protected] ABSTRACT 1. INTRODUCTION The emergence of hardware virtualization technology has led to A rootkit consists of a set of programs that work to subvert the development of OS independent malware such as the Virtual control of an Operating System from its legitimate users [16]. If Machine based rootkits (VMBRs). In this paper, we draw one were asked to classify viruses and worms by a single defining attention to a different but related threat that exists on many characteristic, the first word to come to mind would probably be commodity systems in operation today: The System Management replication. In contrast, the single defining characteristic of a Mode based rootkit (SMBR). System Management Mode (SMM) rootkit is stealth. Viruses reproduce, but rootkits hide. They hide is a relatively obscure mode on Intel processors used for low-level by compromising the communication conduit between an hardware control. It has its own private memory space and Operating System and its users. Secondary to hiding themselves, execution environment which is generally invisible to code rootkits are generally capable of gathering and manipulating running outside (e.g., the Operating System). Furthermore, SMM information on the target machine. They may, for example, log a code is completely non-preemptible, lacks any concept of victim user’s keystrokes to obtain passwords or manipulate the privilege level, and is immune to memory protection mechanisms. -
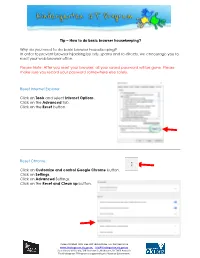
Tip – How to Do Basic Browser Housekeeping?
Tip – How to do basic browser housekeeping? Why do you need to do basic browser housekeeping? In order to prevent browser hijacking by ads, spams and re-directs, we encourage you to reset your web browser often. Please Note: After you reset your browser, all your saved password will be gone. Please make sure you record your password somewhere else safely. _______________________________________________________________________________________ Reset Internet Explorer Click on Tools and select Internet Options . Click on the Advanced tab. Click on the Reset button. _______________________________________________________________________________________ Reset Chrome Click on Customize and control Google Chrome button. Click on Settings . Click on Advanced Settings. Click on the Reset and Clean up button. Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Firefox In the address bar of the FireFox type in about:support and hit Enter. Click Refresh Firefox… button. A window will appear showing the details of this action. Click Refresh Firefox button. _______________________________________________________________________________________ Clear website data in Safari Click on Safari tab and select Preferences… Click Privacy tab. Click Manage Website Data… Click on Remove All . Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Edge Click on Settings and More button. -

COVID-19 Updates and Resources for Local Governments G Tuesday, March 23, 2021 Welcome Greeting
COVID-19 Updates and Resources for Local Governments g Tuesday, March 23, 2021 Welcome Greeting Kayla Rosen Departmental Analyst, Community Engagement and Finance, Department of Treasury 2 Tools and Resources for Local Governments: 11th Webinar Tuesday, March 23, 2021 – 2 p.m. – 3 p.m. I. Welcome & Introductions Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury I. Treasury Update a. CARES Act Grant b. FDCVT Grant c. Overviews of Recreational Marijuana Payments d. American Rescue Plan Eric Bussis, Chief Economist and Director of the Office of Revenue and Tax Analysis, Michigan Department of Treasury I. Cybersecurity for Local Governments Derek Larson, Acting Deputy Chief Security Officer, Department of Technology, Management and Budget (DTMB) I. Question and Answer II. Closing Remarks Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury 3 Welcome & Introductions Heather Frick Bureau Director, Bureau of Local Government and School Services, Department of Treasury 4 Treasury Local Government Funding Update Eric Bussis Chief Economist and Director Office of Revenue and Tax Analysis Michigan Department of Treasury 5 Treasury Update • CARES Act Grant • FDCVT Grant Agenda • Overviews of Recreational Marijuana Payments • American Rescue Plan 6 First Responder Hazard Pay Premiums Program (FRHPPP) • Payments made to 740 applicants, supporting approximately 37,500 first responders • 97 applications were selected for further federal -

The Emergence of Exploit-As-A-Service
Manufacturing Compromise: The Emergence of Exploit-as-a-Service Chris Grier† Lucas Ballard2 Juan Caballerox Neha Chachra∗ Christian J. Dietrichq Kirill Levchenko∗ Panayiotis Mavrommatis2 Damon McCoyz Antonio Nappax Andreas Pitsillidis∗ Niels Provos2 M. Zubair Rafiquex Moheeb Abu Rajab2 Christian Rossowq Kurt Thomasy Vern Paxson† Stefan Savage∗ Geoffrey M. Voelker∗ y University of California, Berkeley ∗ University of California, San Diego 2 Google International Computer Science Institute x IMDEA Software Institute q University of Applied Sciences Gelsenkirchen z George Mason University ABSTRACT 1. INTRODUCTION We investigate the emergence of the exploit-as-a-service model for In this work we investigate the emergence of a new paradigm: the driveby browser compromise. In this regime, attackers pay for an exploit-as-a-service economy that surrounds browser compromise. exploit kit or service to do the “dirty work” of exploiting a vic- This model follows in the footsteps of a dramatic evolution in the tim’s browser, decoupling the complexities of browser and plugin world of for-profit malware over the last five years, where host com- vulnerabilities from the challenges of generating traffic to a web- promise is now decoupled from host monetization. Specifically, the site under the attacker’s control. Upon a successful exploit, these means by which a host initially falls under an attacker’s control are kits load and execute a binary provided by the attacker, effectively now independent of the means by which an(other) attacker abuses transferring control of a victim’s machine to the attacker. the host in order to realize a profit. This shift in behavior is exem- In order to understand the impact of the exploit-as-a-service plified by the pay-per-install model of malware distribution, where paradigm on the malware ecosystem, we perform a detailed anal- miscreants pay for compromised hosts via the underground econ- ysis of the prevalence of exploit kits, the families of malware in- omy [4, 41]. -

Spyware & Adware Products
AdwareAdware/Spyware/Spyware ProductsProducts && RecommendationsRecommendations UCLAUCLA OfficeOffice ofof InstructionalInstructional DevelopmentDevelopment MikeMike TakahashiTakahashi AgendaAgenda WhatWhat isis AdwareAdware/Spyware/Spyware KnownKnown AdwareAdware/Spyware/Spyware ProductsProducts AntiAnti AdwareAdware/Spyware/Spyware RemovalRemoval ProductProduct ComparisonsComparisons TipsTips && RecommendationsRecommendations AdwareAdware AdwareAdware cancan bebe softwaresoftware thatthat generatesgenerates advertisementsadvertisements suchsuch asas poppop--upup windowswindows oror hotlinkshotlinks onon webweb pages.pages. ItIt maymay addadd linkslinks toto youryour favoritesfavorites andand youryour desktop.desktop. ItIt cancan changechange youryour homehome pagepage andand youryour searchsearch engineengine toto sitessites thatthat earnearn incomeincome fromfrom variousvarious advertisers.advertisers. Source http://www.microsoft.com/windows/ie/community/columns/adware.mspx AdwareAdware ExamplesExamples What?!What?! MyMy computercomputer isis infected!infected! OrOr isis it?it? AdwareAdware ExamplesExamples WellWell--knownknown AdwareAdware ProgramsPrograms toto AvoidAvoid HotbarHotbar (Add(Add--ons)ons) Adds graphical skins to Browser and Email clients Adds toolbars and search button BlockCheckerBlockChecker ClipGenieClipGenie CometComet CursorCursor GatorGator WinFixerWinFixer StumbleUponStumbleUpon WeatherBugWeatherBug SpywareSpyware SpywareSpyware isis computercomputer softwaresoftware thatthat collectscollects -

Trojans and Malware on the Internet an Update
Attitude Adjustment: Trojans and Malware on the Internet An Update Sarah Gordon and David Chess IBM Thomas J. Watson Research Center Yorktown Heights, NY Abstract This paper continues our examination of Trojan horses on the Internet; their prevalence, technical structure and impact. It explores the type and scope of threats encountered on the Internet - throughout history until today. It examines user attitudes and considers ways in which those attitudes can actively affect your organization’s vulnerability to Trojanizations of various types. It discusses the status of hostile active content on the Internet, including threats from Java and ActiveX, and re-examines the impact of these types of threats to Internet users in the real world. Observations related to the role of the antivirus industry in solving the problem are considered. Throughout the paper, technical and policy based strategies for minimizing the risk of damage from various types of Trojan horses on the Internet are presented This paper represents an update and summary of our research from Where There's Smoke There's Mirrors: The Truth About Trojan Horses on the Internet, presented at the Eighth International Virus Bulletin Conference in Munich Germany, October 1998, and Attitude Adjustment: Trojans and Malware on the Internet, presented at the European Institute for Computer Antivirus Research in Aalborg, Denmark, March 1999. Significant portions of those works are included here in original form. Descriptors: fidonet, internet, password stealing trojan, trojanized system, trojanized application, user behavior, java, activex, security policy, trojan horse, computer virus Attitude Adjustment: Trojans and Malware on the Internet Trojans On the Internet… Ever since the city of Troy was sacked by way of the apparently innocuous but ultimately deadly Trojan horse, the term has been used to talk about something that appears to be beneficial, but which hides an attack within. -

Rootkits, Part 1 of 3: the Growing Threat
White Paper | April 2006 Rootkits, Part 1 of 3: The Growing Threat www.mcafee.com White Paper | 2006 Page Table of Contents Key Findings 3 Abstract 3 A Brief History of Stealth Malware (a.k.a. Rootkits) 3 Rootkits, Malware, and Controversy 4 Rootkit Technology Trends 5 Works Cited 7 www.mcafee.com White Paper | 2006 Page Key Findings netstat, ls, and passwd. Because these same tools could be used by an attacker to hide any trace of intrusion, the term 1. In just three short years, the use of stealth techniques in rootkit became associated with stealth. When these same malicious software (malware) has grown by more than strategies were applied to the Windows environment, the 600 percent. rootkit name transferred with them. Today, rootkit is a term . From 000 to 005, rootkit complexity grew by more commonly used to describe malware—such as Trojans, than 400 percent, and year-over-year, Q1 2005 to 2006, worms, and viruses—that actively conceals its existence complexity has grown by more than 900 percent. and actions from users and other system processes. The share of Linux-based techniques has gone from The practice of hiding malware from the prying eyes of a high of roughly 71 percent of all malware stealth users and security products dates back to the very first PC 1 components in 001 to a negligible number in virus, Brain, which was released in 1986. Brain escaped 005, while the number of Windows®-based stealth detection by intercepting PC boot-sector interrogations and components has increased by ,00 percent in the same redirecting the read operations to elsewhere on the disk. -

An Adaptive Multi-Layer Botnet Detection Technique Using Machine Learning Classifiers
applied sciences Article An Adaptive Multi-Layer Botnet Detection Technique Using Machine Learning Classifiers Riaz Ullah Khan 1,* , Xiaosong Zhang 1, Rajesh Kumar 1 , Abubakar Sharif 1, Noorbakhsh Amiri Golilarz 1 and Mamoun Alazab 2 1 Center of Cyber Security, School of Computer Science & Engineering, University of Electronic Science and Technology of China, Chengdu 611731, China; [email protected] (X.Z.); [email protected] (R.K.); [email protected] (A.S.); [email protected] (N.A.G.) 2 College of Engineering, IT and Environment, Charles Darwin University, Casuarina 0810, Australia; [email protected] * Correspondence: [email protected]; Tel.: +86-155-2076-3595 Received: 19 March 2019; Accepted: 24 April 2019; Published: 11 June 2019 Abstract: In recent years, the botnets have been the most common threats to network security since it exploits multiple malicious codes like a worm, Trojans, Rootkit, etc. The botnets have been used to carry phishing links, to perform attacks and provide malicious services on the internet. It is challenging to identify Peer-to-peer (P2P) botnets as compared to Internet Relay Chat (IRC), Hypertext Transfer Protocol (HTTP) and other types of botnets because P2P traffic has typical features of the centralization and distribution. To resolve the issues of P2P botnet identification, we propose an effective multi-layer traffic classification method by applying machine learning classifiers on features of network traffic. Our work presents a framework based on decision trees which effectively detects P2P botnets. A decision tree algorithm is applied for feature selection to extract the most relevant features and ignore the irrelevant features. -

Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome
Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome Browser toolbars have been around for years, however, in the last couple of months they became a huge mess. Unfortunately, lots of free software comes with more or less unwanted add-ons or browser toolbars. These are quite annoying because they may: Change your homepage and your search engine without your permission or awareness Track your browsing activities and searches Display annoying ads and manipulate search results Take up a lot of (vertical) space inside the browser Slow down your browser and degrade your browsing experience Fight against each other and make normal add-on handling difficult or impossible Become difficult or even impossible for the average user to fully uninstall Toolbars are not technically not a virus, but they do exhibit plenty of malicious traits, such as rootkit capabilities to hook deep into the operating system, browser hijacking, and in general just interfering with the user experience. The industry generally refers to it as a “PUP,” or potentially unwanted program. Generally speaking, toolbars are ad-supported (users may see additional banner, search, pop-up, pop-under, interstitial and in-text link advertisements) cross web browser plugin for Internet Explorer, Firefox and Chrome, and distributed through various monetization platforms during installation. Very often users have no idea where did it come from, so it’s not surprising at all that most of them assume that the installed toolbar is a virus. For example, when you install iLivid Media Player, you will also agree to change your browser homepage to search.conduit.com, set your default search engine to Conduit Search, and install the AVG Search-Results Toolbar.