Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Trojan Vs Rat Vs Rootkit Mayuri More1, Rajeshwari Gundla2, Siddharth Nanda3 1U.G
IJRECE VOL. 7 ISSUE 2 (APRIL- JUNE 2019) ISSN: 2393-9028 (PRINT) | ISSN: 2348-2281 (ONLINE) Trojan Vs Rat Vs Rootkit Mayuri More1, Rajeshwari Gundla2, Siddharth Nanda3 1U.G. Student, 2 Senior Faculty, 3Senior Faculty SOE, ADYPU, Lohegaon, Pune, Maharashtra, India1 IT, iNurture, Bengaluru, India2,3 Abstract - Malicious Software is Malware is a dangerous of RATs completely and prevent confidential data being software which harms computer systems. With the increase leaked. So Dan Jiang and Kazumasa Omote researchers in technology in today’s days, malwares are also increasing. have proposed an approach to detect RAT in the early stage This paper is based on Malware. We have discussed [10]. TROJAN, RAT, ROOTKIT in detail. Further, we have discussed the adverse effects of malware on the system as III. CLASSIFICATION well as society. Then we have listed some trusted tools to Rootkit vs Trojan vs Rat detect and remove malware. Rootkit - A rootkit is a malicious software that permits a legitimate user to have confidential access to a system and Keywords - Malware, Trojan, RAT, Rootkit, System, privileged areas of its software. A rootkit possibly contains Computer, Anti-malware a large number of malicious means for example banking credential stealers, keyloggers, antivirus disablers, password I. INTRODUCTION stealers and bots for DDoS attacks. This software stays Nowadays, this world is full of technology, but with the hidden in the computer and allocates the remote access of advantages of technology comes its disadvantages like the computer to the attacker[2]. hacking, corrupting the systems, stealing of data etc. These Types of Rootkit: malpractices are possible because of malware and viruses 1. -

Computer Essentials – Session 1 – Step-By-Step Guide
Computer Essentials – Session 1 – Step-by-Step Guide Note: Completing the Mouse Tutorial and Mousercise exercise which are available on the Class Resources webpage constitutes the first part of this lesson. ABOUT PROGRAMS AND OPERATING SYSTEMS Any time a task is performed on a computer, it is done through a program. For the user, the program is the application – the tool – for accomplishing a task. For the computer, it is a set of instructions on knowing how to perform this task. Examples of programs include Internet Explorer and Microsoft Word. The most important program overall is the operating system, which manages all of the computer’s resources and decides how to treat input from the user. There are several different operating systems in circulation, such as Mac O/S and Linux. However, far and away, the most commonly-used operating system is Microsoft Windows. (Note that Microsoft is just the name of the company that makes Windows, and that there are several versions of Windows. In 2012 all the computers in the lab were updated to the version of Windows called Windows 7. If you have some experience with the older versions of Windows you will notice that things look a bit different on a computer running Windows 7. THE WINDOWS 7 ENVIRONMENT The Desktop The first thing you see when you log on to the computer is the DESKTOP. The Desktop is the display area you see when Windows opens. The following items are the most common items that can be found on the desktop: Mouse pointer Icons Shortcuts to Storage drives Notification Start Button Taskbar tray Show Desktop/Peek button Andrea Philo September 2012 Page 1 of 13 Montgomery County-Norristown Public Library Computer Essentials – Session 1 – Step-by-Step Guide Parts of the Windows 7 Desktop Icon: A picture representing a program or file or places to store files. -

Adware-Searchsuite
McAfee Labs Threat Advisory Adware-SearchSuite June 22, 2018 McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalent malware. This Threat Advisory contains behavioral information, characteristics and symptoms that may be used to mitigate or discover this threat, and suggestions for mitigation in addition to the coverage provided by the DATs. To receive a notification when a Threat Advisory is published by McAfee Labs, select to receive “Malware and Threat Reports” at the following URL: https://www.mcafee.com/enterprise/en-us/sns/preferences/sns-form.html Summary Detailed information about the threat, its propagation, characteristics and mitigation are in the following sections: Infection and Propagation Vectors Mitigation Characteristics and Symptoms Restart Mechanism McAfee Foundstone Services The Threat Intelligence Library contains the date that the above signatures were most recently updated. Please review the above mentioned Threat Library for the most up to date coverage information. Infection and Propagation Vectors Adware-SearchSuite is a "potentially unwanted program" (PUP). PUPs are any piece of software that a reasonably security- or privacy-minded computer user may want to be informed of and, in some cases, remove. PUPs are often made by a legitimate corporate entity for some beneficial purpose, but they alter the security state of the computer on which they are installed, or the privacy posture of the user of the system, such that most users will want to be aware of them. Mitigation Mitigating the threat at multiple levels like file, registry and URL could be achieved at various layers of McAfee products. Browse the product guidelines available here (click Knowledge Center, and select Product Documentation from the Support Content list) to mitigate the threats based on the behavior described in the Characteristics and symptoms section. -

A Crawler-Based Study of Spyware on the Web
A Crawler-based Study of Spyware on the Web Alexander Moshchuk, Tanya Bragin, Steven D. Gribble, and Henry M. Levy Department of Computer Science & Engineering University of Washington {anm, tbragin, gribble, levy}@cs.washington.edu Abstract servers [16]. The AOL scan mentioned above has provided simple summary statistics by directly examining desktop in- Malicious spyware poses a significant threat to desktop fections [2], while a recent set of papers have considered security and integrity. This paper examines that threat from user knowledge of spyware and its behavior [6, 29]. an Internet perspective. Using a crawler, we performed a In this paper we change perspective, examining the na- large-scale, longitudinal study of the Web, sampling both ture of the spyware threat not on the desktop but from an executables and conventional Web pages for malicious ob- Internet point of view. To do this, we conduct a large-scale jects. Our results show the extent of spyware content. For outward-looking study by crawling the Web, downloading example, in a May 2005 crawl of 18 million URLs, we found content from a large number of sites, and then analyzing it spyware in 13.4% of the 21,200 executables we identified. to determine whether it is malicious. In this way, we can At the same time, we found scripted “drive-by download” answer several important questions. For example: attacks in 5.9% of the Web pages we processed. Our analy- sis quantifies the density of spyware, the types of of threats, • How much spyware is on the Internet? and the most dangerous Web zones in which spyware is • Where is that spyware located (e.g., game sites, chil- likely to be encountered. -

Adding the Maine Prescription Monitoring System As a Favorite
Adding the Maine Prescription Monitoring System as a Favorite Beginning 1/1/17 all newly prescribed narcotic medications ordered when discharging a patient from the Emergency Department or an Inpatient department must be recorded in the Maine prescription monitoring system (Maine PMP). Follow these steps to access the Maine PMP site from the SeHR/Epic system and create shortcuts to the activity to simplify access. Access the Maine PMP site from hyperspace 1. Follow this path for the intial launch of the Maine PMP site: Epic>Help>Maine PMP Program Please note: the Maine PMP database is managed and maintained by the State of Maine and does NOT support single-sign on 2. Click Login to enter your Maine PMP user name and password a. If you know your user name and password, click Login b. To retrieve your user name click Retrieve User Name c. To retrieve your password click Retrieve Password Save the Maine PMP site as a favorite under the Epic button After accessing the site from the Epic menu path you can make the link a favorite under the Epic menu. 1. Click the Epic button, the Maine PMP program hyperlink will appear under your Recent activities, click the Star icon to save it as a favorite. After staring the activity it becomes a favorite stored under the Epic button Save the Maine PMP site as a Quick Button on your Epic Toolbar After accessing the site from the Epic menu path you may choose to make the Maine PMP hyperlink a quick button on your main Epic toolbar. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Nation-A Cyber Security Strategy Developed by Joshua Fatehnia 4Th May 2018 Version 1 Ref 113524
q Nation-A Cyber Security Strategy Developed by Joshua Fatehnia 4th May 2018 Version 1 ref 113524 Contents 1. Introduction ............................................................................................................................ 2 1.1. Cyber Warfare ................................................................................................................ 3 2. Vision ....................................................................................................................................... 5 2.1. Threats ............................................................................................................................ 5 2.2. Vulnerabilities ................................................................................................................ 7 3. Response ............................................................................................................................... 13 3.1. Cooperative Involvement ........................................................................................... 13 3.2. Prosecution and Forensic Computing ....................................................................... 13 3.3. Training and Education ............................................................................................... 15 3.4. Government Assurance ............................................................................................... 15 3.5. Redundancy Options .................................................................................................. -
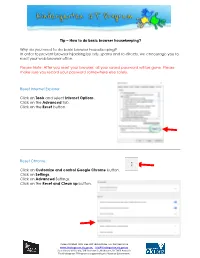
Tip – How to Do Basic Browser Housekeeping?
Tip – How to do basic browser housekeeping? Why do you need to do basic browser housekeeping? In order to prevent browser hijacking by ads, spams and re-directs, we encourage you to reset your web browser often. Please Note: After you reset your browser, all your saved password will be gone. Please make sure you record your password somewhere else safely. _______________________________________________________________________________________ Reset Internet Explorer Click on Tools and select Internet Options . Click on the Advanced tab. Click on the Reset button. _______________________________________________________________________________________ Reset Chrome Click on Customize and control Google Chrome button. Click on Settings . Click on Advanced Settings. Click on the Reset and Clean up button. Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Firefox In the address bar of the FireFox type in about:support and hit Enter. Click Refresh Firefox… button. A window will appear showing the details of this action. Click Refresh Firefox button. _______________________________________________________________________________________ Clear website data in Safari Click on Safari tab and select Preferences… Click Privacy tab. Click Manage Website Data… Click on Remove All . Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Edge Click on Settings and More button. -

COVID-19 Updates and Resources for Local Governments G Tuesday, March 23, 2021 Welcome Greeting
COVID-19 Updates and Resources for Local Governments g Tuesday, March 23, 2021 Welcome Greeting Kayla Rosen Departmental Analyst, Community Engagement and Finance, Department of Treasury 2 Tools and Resources for Local Governments: 11th Webinar Tuesday, March 23, 2021 – 2 p.m. – 3 p.m. I. Welcome & Introductions Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury I. Treasury Update a. CARES Act Grant b. FDCVT Grant c. Overviews of Recreational Marijuana Payments d. American Rescue Plan Eric Bussis, Chief Economist and Director of the Office of Revenue and Tax Analysis, Michigan Department of Treasury I. Cybersecurity for Local Governments Derek Larson, Acting Deputy Chief Security Officer, Department of Technology, Management and Budget (DTMB) I. Question and Answer II. Closing Remarks Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury 3 Welcome & Introductions Heather Frick Bureau Director, Bureau of Local Government and School Services, Department of Treasury 4 Treasury Local Government Funding Update Eric Bussis Chief Economist and Director Office of Revenue and Tax Analysis Michigan Department of Treasury 5 Treasury Update • CARES Act Grant • FDCVT Grant Agenda • Overviews of Recreational Marijuana Payments • American Rescue Plan 6 First Responder Hazard Pay Premiums Program (FRHPPP) • Payments made to 740 applicants, supporting approximately 37,500 first responders • 97 applications were selected for further federal -

The Emergence of Exploit-As-A-Service
Manufacturing Compromise: The Emergence of Exploit-as-a-Service Chris Grier† Lucas Ballard2 Juan Caballerox Neha Chachra∗ Christian J. Dietrichq Kirill Levchenko∗ Panayiotis Mavrommatis2 Damon McCoyz Antonio Nappax Andreas Pitsillidis∗ Niels Provos2 M. Zubair Rafiquex Moheeb Abu Rajab2 Christian Rossowq Kurt Thomasy Vern Paxson† Stefan Savage∗ Geoffrey M. Voelker∗ y University of California, Berkeley ∗ University of California, San Diego 2 Google International Computer Science Institute x IMDEA Software Institute q University of Applied Sciences Gelsenkirchen z George Mason University ABSTRACT 1. INTRODUCTION We investigate the emergence of the exploit-as-a-service model for In this work we investigate the emergence of a new paradigm: the driveby browser compromise. In this regime, attackers pay for an exploit-as-a-service economy that surrounds browser compromise. exploit kit or service to do the “dirty work” of exploiting a vic- This model follows in the footsteps of a dramatic evolution in the tim’s browser, decoupling the complexities of browser and plugin world of for-profit malware over the last five years, where host com- vulnerabilities from the challenges of generating traffic to a web- promise is now decoupled from host monetization. Specifically, the site under the attacker’s control. Upon a successful exploit, these means by which a host initially falls under an attacker’s control are kits load and execute a binary provided by the attacker, effectively now independent of the means by which an(other) attacker abuses transferring control of a victim’s machine to the attacker. the host in order to realize a profit. This shift in behavior is exem- In order to understand the impact of the exploit-as-a-service plified by the pay-per-install model of malware distribution, where paradigm on the malware ecosystem, we perform a detailed anal- miscreants pay for compromised hosts via the underground econ- ysis of the prevalence of exploit kits, the families of malware in- omy [4, 41]. -

Basic Computer Lesson
Table of Contents MICROSOFT WORD 1 ONE LINC What is MSWord? MSWord is a word-processing program that allows users to create, edit, and enhance text in a variety of formats. Word is a powerful word processor with sophisticated editing and formatting as well as graphic- enhancement capabilities. Word is a good program for novice users since it is relatively easy to learn and can be integrated with language learning. Word processing has become popular due to its wide range of personal, business, and other applications. ESL learners, like others, need word processing for job search, employment, and personal purposes. Word-processing skills have become the backbone of computer literacy skills. Features PARTS OF THE SCREEN The Word screen can be overwhelming for novice learners. The numerous bars on the screen such as toolbars, scroll bars, and status bar confuse learners who are using Word for the first time. It is important that learners become familiar with parts of the screen and understand the function of each toolbar but we recommend that the Standard and Formatting toolbars as well as the Status bar be hidden for LINC One level. Menu bar Title bar Minimize Restore Button Button Close Word Close current Rulers document Insertion Point (cursor) Vertical scroll bar Editing area Document Status bar Horizontal Views scroll bar A SOFTWARE GUIDE FOR LINC INSTRUCTORS 131 1 MICROSOFT WORD Hiding Standard toolbar, Formatting toolbar, and Status bar: • To hide the Standard toolbar, click View | Toolbars on the Menu bar. Check off Standard. LINC ONE LINC • To hide the Formatting toolbar, click View | Toolbars on the Menu bar. -

Spyware & Adware Products
AdwareAdware/Spyware/Spyware ProductsProducts && RecommendationsRecommendations UCLAUCLA OfficeOffice ofof InstructionalInstructional DevelopmentDevelopment MikeMike TakahashiTakahashi AgendaAgenda WhatWhat isis AdwareAdware/Spyware/Spyware KnownKnown AdwareAdware/Spyware/Spyware ProductsProducts AntiAnti AdwareAdware/Spyware/Spyware RemovalRemoval ProductProduct ComparisonsComparisons TipsTips && RecommendationsRecommendations AdwareAdware AdwareAdware cancan bebe softwaresoftware thatthat generatesgenerates advertisementsadvertisements suchsuch asas poppop--upup windowswindows oror hotlinkshotlinks onon webweb pages.pages. ItIt maymay addadd linkslinks toto youryour favoritesfavorites andand youryour desktop.desktop. ItIt cancan changechange youryour homehome pagepage andand youryour searchsearch engineengine toto sitessites thatthat earnearn incomeincome fromfrom variousvarious advertisers.advertisers. Source http://www.microsoft.com/windows/ie/community/columns/adware.mspx AdwareAdware ExamplesExamples What?!What?! MyMy computercomputer isis infected!infected! OrOr isis it?it? AdwareAdware ExamplesExamples WellWell--knownknown AdwareAdware ProgramsPrograms toto AvoidAvoid HotbarHotbar (Add(Add--ons)ons) Adds graphical skins to Browser and Email clients Adds toolbars and search button BlockCheckerBlockChecker ClipGenieClipGenie CometComet CursorCursor GatorGator WinFixerWinFixer StumbleUponStumbleUpon WeatherBugWeatherBug SpywareSpyware SpywareSpyware isis computercomputer softwaresoftware thatthat collectscollects