Pwned: How Often Are Americans' Online Accounts Breached?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
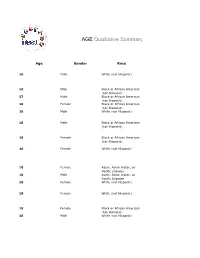
AGE Qualitative Summary
AGE Qualitative Summary Age Gender Race 16 Male White (not Hispanic) 16 Male Black or African American (not Hispanic) 17 Male Black or African American (not Hispanic) 18 Female Black or African American (not Hispanic) 18 Male White (not Hispanic) 18 Malel Blacklk or Africanf American (not Hispanic) 18 Female Black or African American (not Hispanic) 18 Female White (not Hispanic) 18 Female Asian, Asian Indian, or Pacific Islander 18 Male Asian, Asian Indian, or Pacific Islander 18 Female White (not Hispanic) 18 Female White (not Hispanic) 18 Female Black or African American (not Hispanic) 18 Male White (not Hispanic) 19 Male Hispanic (unspecified) 19 Female White (not Hispanic) 19 Female Asian, Asian Indian, or Pacific Islander 19 Male Asian, Asian Indian, or Pacific Islander 19 Male Asian, Asian Indian, or Pacific Islander 19 Female Native American or Alaskan Native 19 Female White (p(not Hispanic)) 19 Male Hispanic (unspecified) 19 Female Hispanic (unspecified) 19 Female White (not Hispanic) 19 Female White (not Hispanic) 19 Male Hispanic/Latino – White 19 Male Hispanic/Latino – White 19 Male Native American or Alaskan Native 19 Female Other 19 Male Hispanic/Latino – White 19 Male Asian, Asian Indian, or Pacific Islander 20 Female White (not Hispanic) 20 Female Other 20 Female Black or African American (not Hispanic) 20 Male Other 20 Male Native American or Alaskan Native 21 Female Don’t want to respond 21 Female White (not Hispanic) 21 Female White (not Hispanic) 21 Male Asian, Asian Indian, or Pacific Islander 21 Female White (not -

Volume 10, Number 1 Assembled 2017 May 2017
Volume 10, Number 1 Assembled 2017 May 2017 Editor In Chief Yesha Sivan Tel Aviv University The Coller Institute of Venture Issue Editor Victoria McArthur University of Toronto, Canada Coordinating Editor Tzafnat Shpak The JVWR is an academic journal. As such, it is dedicated to the open exchange of information. For this reason, JVWR is freely available to individuals and institutions. Copies of this journal or articles in this journal may be distributed for research or educational purposes only free of charge and without permission. However, the JVWR does not grant permission for use of any content in advertisements or advertising supplements or in any manner that would imply an endorsement of any product or service. All uses beyond research or educational purposes require the written permission of the JVWR. Authors who publish in the Journal of Virtual Worlds Research will release their articles under the Creative Commons Attribution No Derivative Works 3.0 United States (cc-by-nd) license. The Journal of Virtual Worlds Research is funded by its sponsors and contributions from readers. http://jvwresearch.org Internet Research in Online Environments for Children 1 Volume 10, Number 1 Assembled 2017 May, 2017 Internet Research in Online Environments for Children: Readability of Privacy and Terms of Use Policies; The Uses of (Non)Personal Data by Online Environments and Third- Party Advertisers Olesya Venger University of Nevada, Las Vegas Abstract Online environments encourage their prospects, including children and teens, to register and provide information about themselves in order to participate in online activities. Many sites' privacy and terms of use policies tend to provide hard-to-understand explanations about their data-using practices, contributing to a widespread confusion regarding the differences between what counts as non-personal versus personal data, and whether this data could be used for behavioral targeting or selling. -

In Re Nickelodeon Consumer Privacy Litig
No Shepard’s Signal™ As of: July 7, 2014 1:09 PM EDT In re Nickelodeon Consumer Privacy Litig. United States District Court for the District of New Jersey July 2, 2014, Decided; July 2, 2014, Filed MDL No. 2443 (SRC); Civil Action No. 12-07829; Civil Action No. 13-03755; Civil Action No. 13-03729; Civil Action No. 13-03757; Civil Action No. 13-03731; Civil Action No. 13-03756 Reporter: 2014 U.S. Dist. LEXIS 91286 IN RE NICKELODEON CONSUMER PRIVACY ATTORNEY, COUNSEL NOT ADMITTED TO LITIGATION. THIS DOCUMENT RELATES TO: THE USDC-NJ BAR, BARTIMUS FRICKLETON CONSOLIDATION ACTION. ROBERTSON & GORNY PC, LEAWOOD, KS; MARY D. WINTER, LEAD ATTORNEY, COUNSEL NOT Notice: NOT FOR PUBLICATION ADMITTED TO USDC-NJ BAR, BARTIMUS FRICKLETON ROBERTSON & GORNY, Core Terms [*2] JEFFERSON CITY, MO. video, user, privacy, intercept, wiretap, disclosure, For STEPHANIE FRYAR, Plaintiff in 13-3755 website, cookies, online, consumer, electronic (2:12-cv-07829-SRC-CLW), Plaintiff: Adam Q Voyles, communication, service provider, cause of action, register, LEAD ATTORNEY, MDL, Lubel Voyles LLP, Houston, gender, sites, personal information, unjust enrichment, TX. anonymous, intrusion, aggrieve, dismissal with prejudice, civil action, videotape, seclusion, watch, advertize, For T.M., Plaintiff in 13-3756 highball, internet, third-party (2:12-cv-07829-SRC-CLW), Plaintiff: KEVIN P. GREEN, LEAD ATTORNEY, THOMAS P. ROSENFELD, Counsel: [*1] For CAF AND CTF, MINOR CHILDREN COUNSEL NOT ADMITTED TO USDC-NJ BAR, BY THEIR FATHER, ANTHONY R. FIORE, JR., MP, A GOLDENBERG HELLER ANTOGNOLI & ROWLAND MINOR CHILD BY HIS FATHER, MICHAEL POND, PC, EDWARDSVILLE, IL; MARK C. GOLDENBERG, TP, A MINOR CHILD BY HER MOTHER, TIFFANY LEAD ATTORNEY, GOLDENBERG HELLER PARROT, AV, A MINOR CHILD BY HIS FATHER, ANTOGNOLI & ROWLAND PC, EDWARDSVILLE, PAUL VOGEL (2:12-cv-07829-SRC-CLW), Plaintiffs: IL. -

Reconciling Cultural Diversity and Free Trade in the Digital Age: a Cultural Analysis of the International Trade in Content Items Claire Wright
The University of Akron IdeaExchange@UAkron Akron Law Review Akron Law Journals July 2015 Reconciling Cultural Diversity and Free Trade in the Digital Age: A Cultural Analysis of the International Trade in Content Items Claire Wright Please take a moment to share how this work helps you through this survey. Your feedback will be important as we plan further development of our repository. Follow this and additional works at: http://ideaexchange.uakron.edu/akronlawreview Part of the International Law Commons, and the International Trade Law Commons Recommended Citation Wright, Claire (2008) "Reconciling Cultural Diversity and Free Trade in the Digital Age: A Cultural Analysis of the International Trade in Content Items," Akron Law Review: Vol. 41 : Iss. 2 , Article 3. Available at: http://ideaexchange.uakron.edu/akronlawreview/vol41/iss2/3 This Article is brought to you for free and open access by Akron Law Journals at IdeaExchange@UAkron, the institutional repository of The nivU ersity of Akron in Akron, Ohio, USA. It has been accepted for inclusion in Akron Law Review by an authorized administrator of IdeaExchange@UAkron. For more information, please contact [email protected], [email protected]. Wright: Reconciling Cultural Diversity and Free Trade WRIGHT_FINAL 3/23/2009 2:40 PM RECONCILING CULTURAL DIVERSITY AND FREE TRADE IN THE DIGITAL AGE: A CULTURAL ANALYSIS OF THE INTERNATIONAL TRADE IN CONTENT ITEMS Claire Wright* I. Introduction ....................................................................... 401 II. Background Information.................................................... 415 A. Cultural Diversity on the Global Level ....................... 415 B. International Media Conglomerates ............................ 420 C. Global Content Markets .............................................. 428 D. Digital Technology ..................................................... 432 III. Cultural Studies ................................................................. 439 A. Cultural Studies as a Discipline ................................. -

COMEDY CENTRAL Roasters Revealed ... Rivers in for a Rippin'
COMEDY CENTRAL Roasters Revealed ... Rivers in for a Rippin' Roasters Include Brad Garrett, Carl Reiner, Gilbert Gottfried, Greg Giraldo, Jeffrey Ross, Lily Tomlin, Mario Cantone, Richard Belzer, Robin Quivers And Whitney Cummings "COMEDY CENTRAL Roast Of Joan Rivers" Premieres On Sunday, August 9 At 10:00 P.M. ET/PT NEW YORK, July 14 -- COMEDY CENTRAL is paying homage to the illustrious career of comedic icon and this year's Roastee Joan Rivers with a cavalcade of high caliber comedians who have a propensity for butchering barbs. The network announced today an all-star roster of Roasters who, along with Roast Master Kathy Griffin, are sure to keep the jabs sharp, quick and precise. The "COMEDY CENTRAL Roast Of Joan Rivers" tapes in Los Angeles at CBS Studios -- Radford on Sunday, July 26. The "COMEDY CENTRAL Roast Of Joan Rivers" airs on Sunday, August 9 at 10:00 p.m. ET/PT. This year's Roasters include Roast Master Kathy Griffin, Brad Garrett, Carl Reiner, Gilbert Gottfried, Greg Giraldo, Jeffrey Ross, Lily Tomlin, Mario Cantone, Richard Belzer, Robin Quivers and Whitney Cummings. Additional Roasters and talent will be announced. The "COMEDY CENTRAL Roast Of Joan Rivers" will be executive produced by Joel Gallen from Tenth Planet Productions, who also executive produced and directed the "COMEDY CENTRAL Roast Of Larry The Cable Guy," "COMEDY CENTRAL Roast Of Bob Saget," "COMEDY CENTRAL Roast Of Flavor-Flav," the Emmy-nominated "COMEDY CENTRAL Roast Of William Shatner" and the "COMEDY CENTRAL Roast Of Pamela Anderson." Larry Thompson will serve as co-executive producer. Elizabeth Porter is the executive in charge for the network. -

MTV Networks Launches the 'Comedy Tribe,' Its Newest Vertical Ad Network
MTV Networks Launches the 'Comedy Tribe,' Its Newest Vertical Ad Network Exclusive Ad Repping Partnership with JibJab.com Offers Advertisers Greater Scale and Extensive Sponsorship Opportunities NEW YORK, Jan. 26 -- MTV Networks (MTVN), a division of Viacom (NYSE: VIA, VIA.B), today expanded its "Tribes" vertical ad network initiative with the launch of the humor-focused Comedy Tribe, anchored by ComedyCentral.com. Among the launch publishers in the new vertical ad network is JibJab.com, the nationally-recognized producer of premium video content and digital greetings, which has signed an exclusive ad repping agreement with MTVN. "Tribes have proven to be a powerful tool to offer our advertisers greater scale and connect them with relevant and engaged consumers online," said Heather Hopkins, Senior Vice President and General Manager of Tribes. "With the launch of the Comedy Tribe and the partnership with JibJab, we're able to offer advertisers access to even more consumers as well as high levels of targetability, accountability, and deep brand integrations across some of the most popular and premium comedy sites on the Web." Under its agreement with JibJab, MTVN will serve as the exclusive sales force for all advertising inventory on the site, as well as JibJab's popular brand integrations and custom sponsorships. During 2008, JibJab.com received 105 million visits and the company currently has over 6.3 million registered members. "JibJab has extensive reach but has always struggled to get mindshare with a large number of big brands," said JibJab's CEO, Gregg Spiridellis. "We believe working with the best comedy ad sales team in the world at MTV Networks will give us an opportunity to educate brands about our audience and premium content offerings at a scale that was never before possible." "We knew that JibJab's proven ability to create highly engaging, viral branded entertainment would be of enormous value to our advertisers," said Hopkins. -

Open Final Thesis 1 6.Pdf
THE PENNSYLAVNIA STATE UNIVERSTIY SCHREYERS HONORS COLLEGE COLLEGE OF ENGINEERING, DESIGN TECHNOLOGY AND PROFESSIONAL PROGRAMS HOW AND WHY PRODUCTS GO VIRAL NICOLE KELNER Spring 2015 A thesis submitted in partial fulfillment of the requirements for a baccalaureate degree in Advertising/Public Relations with honors in Engineering Entrepreneurship Reviewed and approved* by the following: Elizabeth Kisenwether Assistant Professor of Engineering Design Thesis Supervisor and Honors Advisor Robert Beaury Director, Engineering Entrepreneurship Minor Faculty Reader * Signatures are on file in the Schreyer Honors College. i ABSTRACT What makes a product a hit or a failure? This simple question has been a mystery for hundreds of years, but with the recent growth in access to social media and the Internet, the way that products gain popularity has shifted significantly. Word-of-mouth and local news are no longer the only methods a consumer can hear about a product fad. Rather Twitter, Facebook, Pinterest, YouTube, and Instagram are now contributors to creation of a hit product. This thesis studies and analyzes a few of the most successful products and services that have gained popularity instantly and rapidly spread to be “viral” products over the past 30 years. For the purposes of this thesis, this widespread and often rapid product adoption process is known as virality. The upcoming chapters review and analyze the contributing factors and techniques that allow any given product to go viral. Through examining case studies from present day and the 1980’s, it will draw comparisons that can apply to future viral marketing efforts. It will compare how present day social media and technology play a role in the spreading of product information, benefits and disadvantages compared to past decades. -

Genius Brands International's Hit Preschool Series, Rainbow
April 23, 2019 Genius Brands International’s Hit Preschool Series, Rainbow Rangers, to Launch Across Latin America on Nickelodeon’s Nick Jr. Channel and Its Noggin Mobile Streaming App 52 x 11’ Episodes of Season One of the CG-Animated Adventure Preschool Series Will Premiere On-Air and Via Mobile Across Latin America in Summer 2019 BEVERLY HILLS, Calif. , April 23, 2019 (GLOBE NEWSWIRE) -- On the heels of the recent news that Nickelodeon has greenlit season two of Genius Brands International’s “Genius Brands” (Nasdaq:GNUS) flagship animated series, Rainbow Rangers, Nickelodeon Latin America has licensed season one (52 x 11’) of the series to debut in August on the Nick Jr. channel, and available to stream beginning in June on its NOGGIN preschool mobile app. Rainbow Rangers will be dubbed in Spanish and Brazilian Portuguese. Nickelodeon Latin America has licensed season one (52 x 11’) of Genius Brands International’s hit preschool series, Rainbow Rangers, to debut in August on the Nick Jr. channel, and available to stream beginning in June on its NOGGIN preschool mobile app. The series currently airs in the U.S. on Nick Jr. Rainbow Rangers is a rescue-based series following the adventures of seven girls who are Earth’s first responders, protecting people, animals, resources, and the natural beauty of our world. Rainbow Rangers is a rescue-based series following the adventures of seven girls who are Earth’s first responders, protecting people, animals, resources, and the natural beauty of our world. Since premiering on Nickelodeon’s Nick Jr. in the U.S. -

Puzzles)(Puzzles)
Important Health Warning About Playing Video Games Table of Contents Photosensitive Seizures A very small percentage of people may experience a seizure when exposed to certain TThankhank YYouou ............................................................ 2 visual images, including fl ashing lights or patterns that may appear in video games. Even people who have no history of seizures or epilepsy may have an undiagnosed condition that can cause these “photosensitive epileptic seizures” while watching OOperatingperating EEnvironmentnvironment .................... 4 video games. These seizures may have a variety of symptoms, including lightheadedness, IInstallationnstallation ........................................................ 5 altered vision, eye or face twitching, jerking or shaking of arms or legs, disorientation, confusion, or momentary loss of awareness. Seizures may also cause loss of consciousness or convulsions that can lead to injury from falling down or striking GGameame OperationOperation .......................................... 6 nearby objects. Immediately stop playing and consult a doctor if you experience any of these GGameame ControlsControls ................................................ 7 symptoms. Parents should watch for or ask their children about the above symptoms—children and teenagers are more likely than adults to experience these seizures. The risk of photosensitive epileptic seizures may be reduced by taking YYourour NNeopeteopet .................................................... 8 the following precautions: -

A Typology of Virtual Worlds: Historical Overview and Future Directions by Paul R
Vol. 1. No. 1 ISSN: 1941-8477 “Virtual Worlds Research: Past, Present & Future” July 2008 A Typology of Virtual Worlds: Historical Overview and Future Directions By Paul R. Messinger,School Business, University of Alberta; Eleni Stroulia, Department of Computing Science, University of Alberta; Kelly Lyons,Faculty of Information Studies, University of Toronto. Abstract Virtual worlds constitute a growing space for collaborative play, learning, work, and e-commerce. To promote study of this emerging realm of activity, we suggest a typology adapted from C. Porter’s (2004) typology of virtual communities. The five elements of the proposed typology include (1) purpose (content of interaction), (2) place (location of interaction), (3) platform (design of interaction), (4) population (participants in the interaction), and (5) profit model (return on interaction). We argue that this five-element typology facilitates identification of (a) the historic antecedents of virtual worlds in gaming and social networking, (b) future applications of virtual worlds for society, education, and business; and (c) topics for future research. Keywords: virtual worlds, typology, electronic gaming, online social networking. This work is copyrighted under the Creative Commons Attribution-No Derivative Works 3.0 United States License by the Journal of Virtual Worlds Research. Journal of Virtual Worlds Research:-Typology of Virtual Worlds 2 A Typology of Virtual Worlds: Historical Overview and Future Directions By Paul R. Messinger,School Business, University of Alberta; Eleni Stroulia, Department of Computing Science, University of Alberta; Kelly Lyons,Faculty of Information Studies, University of Toronto. Virtual worlds are playing an increasingly important role in the lives of many adults, teens, and children. -

Broadcasters and the Broadcasters and the Internet
Broadcasters and the Broadcasters and the Internet Internet EBU Members’ Internet Presence Distribution Strategies Online Consumption Trends Social Networking and Video Sharing Communities November 2007 European Broadcasting Union Strategic Information Service (SIS) L’Ancienne-Route 17A CH-1218 Grand-Saconnex Switzerland Phone +41 (0) 22 717 21 11 Fax +41 (0)22 747 40 00 www.ebu.ch/sis European Broadcasting Union l Strategic Information Service Broadcasters and the Internet EBU Members' Internet Presence Distribution Strategies Online Consumption Trends Social Networking and Video Sharing Communities November 2007 The Report Staff This report was produced by the Strategic Information Service of the EBU. Editor: Alexander Shulzycki Production Editor: Anna-Sara Stalvik Principal Researcher: Anna-Sara Stalvik Special appreciation to: Danish Radio and Television (DR) Swedish Television (SVT) Swedish Radio (SR) Cover Design: Philippe Juttens European Broadcasting Union Telephone: +41 22 717 2111 Address: L'Ancienne-Route 17A, 1218 Geneva, Switzerland SIS web-site: www.ebu.ch/director_general/sis.php SIS contact e-mail: [email protected] BROADCASTERS AND THE INTERNET TABLE OF CONTENTS INTRODUCTION.............................................................................................................. 1 OVERVIEW .............................................................................................................................1 1. The general Internet landscape: usage, websites, advertising ............................................ -

(March 2012) the Expansion of Viacom's Network
BROADCAST INTEGRATION SERVICES UPGRADES VIACOM CONTENT SERVICES LONG ISLAND ORIGINATION FACILITY BOOSTS WORKFLOW AND CHANNEL CAPACITY Union City, NJ (March 2012) The expansion of ViacoM’s network operations center is a step closer to completion with the successful transition of a first group of program play- out channels to new higher quality, more reliable sever/automation workflows. Broadcast Integration Services (BIS) — the forward- thinking media technology design, engineering and installation firm based in Union City, NJ tasked with engineering and installing the enhanced systems — announced that they have successfully launched 40 channels of outbound programming from the new TOC Technical Operations Center. The additional capacity supports a range of new and enhanced content origination systems for MTV Networks' family of domestic and International services, among them such popular brands as MTV, VH1, Nickelodeon, TV Land, and the EPIX Network. BIS is adding play-out channels, HD-SDI routing, monitor & control systems, multi- viewer capabilities and virtual control room environments to Viacom's rapidly growing origination center in Hauppauge, NY. When completed, the project will support over 64 channels. "It's great that our distribution services are in such high demand; the tough part is adding capacity without disrupting what's already working," said Mike McMackin, senior director, engineering & project management for Viacom/MTV Networks. "BIS has done an exceptional job of engineering, installing and moving our services to the