A Typology of Virtual Worlds: Historical Overview and Future Directions by Paul R
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Incommensurate Wor(L)Ds: Epistemic Rhetoric and Faceted Classification Of
Incommensurate Wor(l)ds: Epistemic Rhetoric and Faceted Classification of Communication Mechanics in Virtual Worlds by Sarah Smith-Robbins A Dissertation Submitted to the Graduate School in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy Dissertation Advisor: Dr. Rai Peterson Ball State University Muncie, IN March 28, 2011 Table of Contents Table of Contents ..................................................................................................................................... ii List of Tables ........................................................................................................................................... vi List of Figures ......................................................................................................................................... vii Abstract .................................................................................................................................................. ix Acknowledgements ................................................................................................................................. xi Chapter 1: Incommensurate Terms, Incommensurate Practices ............................................................... 1 Purpose of the Study ................................................................................................................................... 3 Significance of the Study ............................................................................................................................ -

Getting the Most out of Information Systems: a Manager's Guide (V
Getting the Most Out of Information Systems A Manager's Guide v. 1.0 This is the book Getting the Most Out of Information Systems: A Manager's Guide (v. 1.0). This book is licensed under a Creative Commons by-nc-sa 3.0 (http://creativecommons.org/licenses/by-nc-sa/ 3.0/) license. See the license for more details, but that basically means you can share this book as long as you credit the author (but see below), don't make money from it, and do make it available to everyone else under the same terms. This book was accessible as of December 29, 2012, and it was downloaded then by Andy Schmitz (http://lardbucket.org) in an effort to preserve the availability of this book. Normally, the author and publisher would be credited here. However, the publisher has asked for the customary Creative Commons attribution to the original publisher, authors, title, and book URI to be removed. Additionally, per the publisher's request, their name has been removed in some passages. More information is available on this project's attribution page (http://2012books.lardbucket.org/attribution.html?utm_source=header). For more information on the source of this book, or why it is available for free, please see the project's home page (http://2012books.lardbucket.org/). You can browse or download additional books there. ii Table of Contents About the Author .................................................................................................................. 1 Acknowledgments................................................................................................................ -
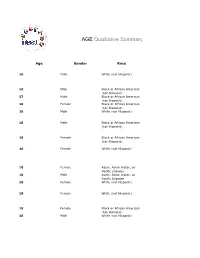
AGE Qualitative Summary
AGE Qualitative Summary Age Gender Race 16 Male White (not Hispanic) 16 Male Black or African American (not Hispanic) 17 Male Black or African American (not Hispanic) 18 Female Black or African American (not Hispanic) 18 Male White (not Hispanic) 18 Malel Blacklk or Africanf American (not Hispanic) 18 Female Black or African American (not Hispanic) 18 Female White (not Hispanic) 18 Female Asian, Asian Indian, or Pacific Islander 18 Male Asian, Asian Indian, or Pacific Islander 18 Female White (not Hispanic) 18 Female White (not Hispanic) 18 Female Black or African American (not Hispanic) 18 Male White (not Hispanic) 19 Male Hispanic (unspecified) 19 Female White (not Hispanic) 19 Female Asian, Asian Indian, or Pacific Islander 19 Male Asian, Asian Indian, or Pacific Islander 19 Male Asian, Asian Indian, or Pacific Islander 19 Female Native American or Alaskan Native 19 Female White (p(not Hispanic)) 19 Male Hispanic (unspecified) 19 Female Hispanic (unspecified) 19 Female White (not Hispanic) 19 Female White (not Hispanic) 19 Male Hispanic/Latino – White 19 Male Hispanic/Latino – White 19 Male Native American or Alaskan Native 19 Female Other 19 Male Hispanic/Latino – White 19 Male Asian, Asian Indian, or Pacific Islander 20 Female White (not Hispanic) 20 Female Other 20 Female Black or African American (not Hispanic) 20 Male Other 20 Male Native American or Alaskan Native 21 Female Don’t want to respond 21 Female White (not Hispanic) 21 Female White (not Hispanic) 21 Male Asian, Asian Indian, or Pacific Islander 21 Female White (not -

Studio Showcase
Contacts: Holly Rockwood Tricia Gugler EA Corporate Communications EA Investor Relations 650-628-7323 650-628-7327 [email protected] [email protected] EA SPOTLIGHTS SLATE OF NEW TITLES AND INITIATIVES AT ANNUAL SUMMER SHOWCASE EVENT REDWOOD CITY, Calif., August 14, 2008 -- Following an award-winning presence at E3 in July, Electronic Arts Inc. (NASDAQ: ERTS) today unveiled new games that will entertain the core and reach for more, scheduled to launch this holiday and in 2009. The new games presented on stage at a press conference during EA’s annual Studio Showcase include The Godfather® II, Need for Speed™ Undercover, SCRABBLE on the iPhone™ featuring WiFi play capability, and a brand new property, Henry Hatsworth in the Puzzling Adventure. EA Partners also announced publishing agreements with two of the world’s most creative independent studios, Epic Games and Grasshopper Manufacture. “Today’s event is a key inflection point that shows the industry the breadth and depth of EA’s portfolio,” said Jeff Karp, Senior Vice President and General Manager of North American Publishing for Electronic Arts. “We continue to raise the bar with each opportunity to show new titles throughout the summer and fall line up of global industry events. It’s been exciting to see consumer and critical reaction to our expansive slate, and we look forward to receiving feedback with the debut of today’s new titles.” The new titles and relationships unveiled on stage at today’s Studio Showcase press conference include: • Need for Speed Undercover – Need for Speed Undercover takes the franchise back to its roots and re-introduces break-neck cop chases, the world’s hottest cars and spectacular highway battles. -

Volume 10, Number 1 Assembled 2017 May 2017
Volume 10, Number 1 Assembled 2017 May 2017 Editor In Chief Yesha Sivan Tel Aviv University The Coller Institute of Venture Issue Editor Victoria McArthur University of Toronto, Canada Coordinating Editor Tzafnat Shpak The JVWR is an academic journal. As such, it is dedicated to the open exchange of information. For this reason, JVWR is freely available to individuals and institutions. Copies of this journal or articles in this journal may be distributed for research or educational purposes only free of charge and without permission. However, the JVWR does not grant permission for use of any content in advertisements or advertising supplements or in any manner that would imply an endorsement of any product or service. All uses beyond research or educational purposes require the written permission of the JVWR. Authors who publish in the Journal of Virtual Worlds Research will release their articles under the Creative Commons Attribution No Derivative Works 3.0 United States (cc-by-nd) license. The Journal of Virtual Worlds Research is funded by its sponsors and contributions from readers. http://jvwresearch.org Internet Research in Online Environments for Children 1 Volume 10, Number 1 Assembled 2017 May, 2017 Internet Research in Online Environments for Children: Readability of Privacy and Terms of Use Policies; The Uses of (Non)Personal Data by Online Environments and Third- Party Advertisers Olesya Venger University of Nevada, Las Vegas Abstract Online environments encourage their prospects, including children and teens, to register and provide information about themselves in order to participate in online activities. Many sites' privacy and terms of use policies tend to provide hard-to-understand explanations about their data-using practices, contributing to a widespread confusion regarding the differences between what counts as non-personal versus personal data, and whether this data could be used for behavioral targeting or selling. -

In Re Nickelodeon Consumer Privacy Litig
No Shepard’s Signal™ As of: July 7, 2014 1:09 PM EDT In re Nickelodeon Consumer Privacy Litig. United States District Court for the District of New Jersey July 2, 2014, Decided; July 2, 2014, Filed MDL No. 2443 (SRC); Civil Action No. 12-07829; Civil Action No. 13-03755; Civil Action No. 13-03729; Civil Action No. 13-03757; Civil Action No. 13-03731; Civil Action No. 13-03756 Reporter: 2014 U.S. Dist. LEXIS 91286 IN RE NICKELODEON CONSUMER PRIVACY ATTORNEY, COUNSEL NOT ADMITTED TO LITIGATION. THIS DOCUMENT RELATES TO: THE USDC-NJ BAR, BARTIMUS FRICKLETON CONSOLIDATION ACTION. ROBERTSON & GORNY PC, LEAWOOD, KS; MARY D. WINTER, LEAD ATTORNEY, COUNSEL NOT Notice: NOT FOR PUBLICATION ADMITTED TO USDC-NJ BAR, BARTIMUS FRICKLETON ROBERTSON & GORNY, Core Terms [*2] JEFFERSON CITY, MO. video, user, privacy, intercept, wiretap, disclosure, For STEPHANIE FRYAR, Plaintiff in 13-3755 website, cookies, online, consumer, electronic (2:12-cv-07829-SRC-CLW), Plaintiff: Adam Q Voyles, communication, service provider, cause of action, register, LEAD ATTORNEY, MDL, Lubel Voyles LLP, Houston, gender, sites, personal information, unjust enrichment, TX. anonymous, intrusion, aggrieve, dismissal with prejudice, civil action, videotape, seclusion, watch, advertize, For T.M., Plaintiff in 13-3756 highball, internet, third-party (2:12-cv-07829-SRC-CLW), Plaintiff: KEVIN P. GREEN, LEAD ATTORNEY, THOMAS P. ROSENFELD, Counsel: [*1] For CAF AND CTF, MINOR CHILDREN COUNSEL NOT ADMITTED TO USDC-NJ BAR, BY THEIR FATHER, ANTHONY R. FIORE, JR., MP, A GOLDENBERG HELLER ANTOGNOLI & ROWLAND MINOR CHILD BY HIS FATHER, MICHAEL POND, PC, EDWARDSVILLE, IL; MARK C. GOLDENBERG, TP, A MINOR CHILD BY HER MOTHER, TIFFANY LEAD ATTORNEY, GOLDENBERG HELLER PARROT, AV, A MINOR CHILD BY HIS FATHER, ANTOGNOLI & ROWLAND PC, EDWARDSVILLE, PAUL VOGEL (2:12-cv-07829-SRC-CLW), Plaintiffs: IL. -

Game Developer Index 2010 Foreword
SWEDISH GAME INDUSTRY’S REPORTS 2011 Game Developer Index 2010 Foreword It’s hard to imagine an industry where change is so rapid as in the games industry. Just a few years ago massive online games like World of Warcraft dominated, then came the breakthrough for party games like Singstar and Guitar Hero. Three years ago, Nintendo turned the gaming world upside-down with the Wii and motion controls, and shortly thereafter came the Facebook games and Farmville which garnered over 100 million users. Today, apps for both the iPhone and Android dominate the evolution. Technology, business models, game design and marketing changing almost every year, and above all the public seem to quickly embrace and follow all these trends. Where will tomorrow’s earnings come from? How can one make even better games for the new platforms? How will the relationship between creator and audience change? These and many other issues are discussed intensively at conferences, forums and in specialist press. Swedish success isn’t lacking in the new channels, with Minecraft’s unprecedented success or Battlefield Heroes to name two examples. Independent Games Festival in San Francisco has had Swedish winners for four consecutive years and most recently we won eight out of 22 prizes. It has been touted for two decades that digital distribution would outsell traditional box sales and it looks like that shift is finally happening. Although approximately 85% of sales still goes through physical channels, there is now a decline for the first time since one began tracking data. The transformation of games as a product to games as a service seems to be here. -

Children on Virtual Worlds September 08
Children on virtual worlds September 08 What parents should know 2 Children on virtual worlds: What parents should know About ENISA The European Network and Information Security Agency (ENISA) is an EU agency created to advance the functioning of the internal market. ENISA is a centre of excellence for the European Member States and European institutions in network and information security, giving advice and recommendations and acting as a switchboard of information for good practices. Moreover, the agency facilitates contacts between the European institutions, the Member States and private business and industry actors. Contact details: For contacting ENISA or for general enquiries on information security awareness matters, please use the following details: e-mail: Isabella Santa, Senior Expert Awareness Raising — [email protected] Internet: http://www.enisa.europa.eu/ Legal notice Notice must be taken that this publication represents the views and interpretations of the authors and editors, unless stated otherwise. This publication should not be construed to be an action of ENISA or the ENISA bodies unless adopted pursuant to the ENISA Regulation (EC) No 460/2004. This publication does not necessarily represent state-of the-art and it might be updated from time to time. Third-party sources are quoted as appropriate. ENISA is not responsible for the content of the external sources including external websites referenced in this publication. This publication is intended for educational and information purposes only. Neither ENISA nor any person acting on its behalf is responsible for the use that might be made of the information contained in this publication. Reproduction is authorised provided the source is acknowledged. -

EA Games Frank Gibeau, President
EA Games Frank Gibeau, President 1 Safe Harbor Statement Some statements set forth in this presentation, including estimates and targets relating to future financial results (e.g., revenue, profitability, margins), operating plans, business strategies, objectives for future operations, and industry growth rates contain forward-looking statements that are subject to change. Statements including words such as "anticipate", "believe", “estimate”, "expect" or “target” and statements in the future tense are forward- looking statements. These forward-looking statements are subject to risks and uncertainties that could cause actual events or actual future results to differ materially from the expectations set forth in the forward-looking statements. Some of the factors which could cause the Company’s results to differ materially from its expectations include the following: timely development and release of Electronic Arts’ products; competition in the interactive entertainment industry; the Company’s ability to successfully implement its Label structure and related reorganization plans; the consumer demand for, and the availability of an adequate supply of console hardware units (including the Xbox 360, the PLAYSTATION3, and the Wii); consumer demand for software for legacy consoles, particularly the PlayStation 2; the Company’s ability to predict consumer preferences among competing hardware platforms; the Company’s ability to realize the anticipated benefits of its acquisition of VG Holding Corp. and other acquisitions and strategic transactions -

Pwned: How Often Are Americans' Online Accounts Breached?
Pwned: How Often Are Americans’ Online Accounts Breached?∗ Ken Cor† Gaurav Sood‡ February 19, 2019 Abstract News about massive online breaches is increasingly common. But there has been little good data on how exposed people are because of these breaches. We combine data from a large, representative sample of adult Americans (n = 5,000) with data from Have I Been Pwned to estimate the lower bound of the average number of breached online accounts per person. We find that at least 82.84% of Americans have had their accounts breached. And, on average, Americans’ accounts have been breached at least three times. The better educated, the middle-aged, women, and Whites are more likely to have had their accounts breached than the complementary groups. arXiv:1808.01883v3 [cs.CY] 18 Feb 2019 https://github.com/ ∗Data and scripts behind the analysis presented here can be downloaded from themains/pwned. †Ken can be reached at: [email protected] ‡Gaurav can be reached at: [email protected] On the Internet, nobody knows you’re a dog. So the adage goes. But increasingly, others know that you like dog food and hate cats. Many of us have made our peace with this new reality. A slew of massive account breaches in recent years (McCandless 2017),1 however, threaten to pull the rug under all illusions of anonymity. n this note, we shed light on this threat. Using a unique dataset, we estimate the lower bound of the average number of breached online accounts per person. To answer how exposed Americans are due to online breaches, we merge data from a large representative sample from YouGov (n = 5,000) with data from Have I Been Pwned (HIBP). -

In the Digital Games Medium
Georgia State University ScholarWorks @ Georgia State University Communication Theses Department of Communication 7-15-2009 L337 Soccer Moms: Conceptions of "Hardcore" and "Casual" in the Digital Games Medium Steven Andrew Boyer Follow this and additional works at: https://scholarworks.gsu.edu/communication_theses Recommended Citation Boyer, Steven Andrew, "L337 Soccer Moms: Conceptions of "Hardcore" and "Casual" in the Digital Games Medium." Thesis, Georgia State University, 2009. https://scholarworks.gsu.edu/communication_theses/53 This Thesis is brought to you for free and open access by the Department of Communication at ScholarWorks @ Georgia State University. It has been accepted for inclusion in Communication Theses by an authorized administrator of ScholarWorks @ Georgia State University. For more information, please contact [email protected]. L337 SOCCER MOMS CONCEPTIONS OF “HARDCORE” AND “CASUAL” IN THE DIGITAL GAMES MEDIUM by STEVEN BOYER Under the Direction of Ted Friedman ABSTRACT As digital games have become increasingly significant in the entertainment media landscape, the terms “casual” and “hardcore” have become the primary ways to describe gaming audiences, genres, and gameplay. However, these terms are saturated with outdated stereotypes involving gender, age, and class. Focusing on industrial discourse, this thesis examines this dichotomy, emphasizing areas of discontinuity and overlap to question why these terms have become so ubiquitous in gaming discourse and what functions they fulfill for a variety of groups including the industry, advertisers, and audience members. Ultimately, I suggest that these terms need to be replaced in order to move beyond restrictive stereotypes, proposing a new framework for digital games that takes into consideration user motivation, personal investment, and historical specificity. -

PDF Lecture Notes
AN INTRODUCTION TO Stylized Rendering in Games Morgan McGuire NVIDIA and Williams College July 26, 2010 SIGGRAPH 2010 Los Angeles, CA Edited July 25, 2010 1 Course Overview Games like Prince of Persia and Battlefield Heroes deliver artistic visions beyond standard photo-realistic 3D. In this course, game developers teach the challenges of creating distinctive visual styles for interactive environments and some of their own solutions. Topics include the art pipeline, rendering algorithms, and integrating visuals with gameplay. Why stylized rendering? As they matured, the visual arts (painting, sculpture, photography, and architecture) all developed new visual-abstraction mechanisms to go beyond "realism". Recent advances in visual effects have put film and games into this transitional state. In a sense, we're like artists at the end of the Renaissance: we've nearly mastered photorealism, but are only at the beginning of our discoveries about expression and perception. Some effects are subtle, like the color shifts and post-processing in Mirror's Edge. Others, such as the graphic-novel look of Prince of Persia, dominate the entire rendering style. In games, real-time and interactive constraints require more efficient and robust solutions than are employed elsewhere in computer graphics. And to be successful, a stylized renderer must integrate with appropriately stylized models, animation, and audio to form a coherent virtual world and ultimately enhance game play. These notes are Copyright 2010 Morgan McGuire All Rights Reserved The credited game screen shots included are copyrighted by their respective publishers, and the game titles are trademarks of their respective publishers and/or developers.