PRISM Vol 1 Issue 3.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Congressional Record United States Th of America PROCEEDINGS and DEBATES of the 104 CONGRESS, FIRST SESSION
E PL UR UM IB N U U S Congressional Record United States th of America PROCEEDINGS AND DEBATES OF THE 104 CONGRESS, FIRST SESSION Vol. 141 WASHINGTON, FRIDAY, APRIL 7, 1995 No. 65 House of Representatives The House met at 11 a.m. and was PLEDGE OF ALLEGIANCE DESIGNATING THE HONORABLE called to order by the Speaker pro tem- The SPEAKER pro tempore. Will the FRANK WOLF AS SPEAKER PRO pore [Mr. BURTON of Indiana]. TEMPORE TO SIGN ENROLLED gentleman from New York [Mr. SOLO- BILLS AND JOINT RESOLUTIONS f MON] come forward and lead the House in the Pledge of Allegiance. THROUGH MAY 1, 1995 DESIGNATION OF SPEAKER PRO Mr. SOLOMON led the Pledge of Alle- The SPEAKER pro tempore laid be- TEMPORE giance as follows: fore the House the following commu- The SPEAKER pro tempore laid be- I pledge allegiance to the Flag of the nication from the Speaker of the House fore the House the following commu- United States of America, and to the Repub- of Representatives: nication from the Speaker. lic for which it stands, one nation under God, WASHINGTON, DC, indivisible, with liberty and justice for all. April 7, 1995. WASHINGTON, DC, I hereby designate the Honorable FRANK R. April 7, 1995. f WOLF to act as Speaker pro tempore to sign I hereby designate the Honorable DAN BUR- enrolled bills and joint resolutions through TON to act as Speaker pro tempore on this MESSAGE FROM THE SENATE May 1, 1995. day. NEWT GINGRICH, NEWT GINGRICH, A message from the Senate by Mr. Speaker of the House of Representatives. -

25 Handbook of Bibliography on Diaspora and Transnationalism.Pdf
BIBLIOGRAPH Y A Hand-book on Diaspora and Transnationalism FIRST EDITION April 2013 Compiled By Monika Bisht Rakesh Ranjan Sadananda Sahoo Draft Copy for Reader’s Comments Global Research Forum on Diaspora and Transnationalism www.grfdt.org Bibleography Preface Large scale international mobility of the people since colonial times has been one of the most important historical phenomenon in the human history. This has impacted upon the social, cultural, political and economic landscape of the entire globe. Though academic interest goes back little early, the phenomenon got the world wide attention as late as 1990s. We have witnessed more proactive engagement of various organizations at national and international level such as UN bodies. There was also growing research interest in the areas. Large number of institutions got engaged in research on diaspora-international migration-refugee-transnationalism. Wide range of research and publications in these areas gave a new thrust to the entire issue and hence advancing further research. The recent emphasis on diaspora’s development role further accentuated the attention of policy makers towards diaspora. The most underemphasized perhaps, the role of diaspora and transnational actors in the overall development process through capacity building, resource mobilization, knowledge sharing etc. are growing areas of development debate in national as well as international forums. There have been policy initiatives at both national and international level to engage diaspora more meaningfully since last one decade. There is a need for more wholistic understanding of the enrite phenomena to facilitate researchers and stakeholders engaged in the various issues related to diaspora and transnationalism. Similarly, we find the areas such as social, political and cultural vis a vis diaspora also attracting more interest in recent times as forces of globalization intensified in multi direction. -

Indian Leaders on Tibet.Pmd
C. Rajagopalachari, the last Governor-General of India, on Tibet Brutal Colonialism in Tibet IT is difficult to find suitable words to express the sympathy that I feel in respect of this movement - of what I may call in a different sense - a movement for the liberation of Tibet. The issue of Tibet is not a question of legalistic exploration as to the sovereignty of Tibet but a question of human rights which must be decided on the plane of justice and humanity and not on the basis of any legal puzzle. Sovereignty and Suzerainty are terms which have varied from time to time in respect of their content. Whatever legal jargon might have been used from time to time, in respect of the relation between Tibet and China, in particular, and the outer world, in general, no one can doubt the fact that Tibetan people have a right to rule themselves. His Holiness the Dalai Lama in his message had made things quite clear and pointed out how even on a legalistic plane there can be no doubt about the rights of the Tibetan people to rule themselves irrespective of any belonging to other nationalities. This invasion of Tibet which terminated in His Holiness taking refuge in Indian territory is brutal colonialism. There can, therefore, be no second thoughts in the matter. All Indian people wants Tibet to be released from the grip of China. 1 Dr. Rajendra Prasad, the first President of Indian Republic, on Tibet (Excerpts from his last public speech, Gandhi Maidan, Patna, 24 October, 1962.) FREEDOM is the most sacred boon. -

Dragon Magazine
DRAGON 1 Publisher: Mike Cook Editor-in-Chief: Kim Mohan Shorter and stronger Editorial staff: Marilyn Favaro Roger Raupp If this isnt one of the first places you Patrick L. Price turn to when a new issue comes out, you Mary Kirchoff may have already noticed that TSR, Inc. Roger Moore Vol. VIII, No. 2 August 1983 Business manager: Mary Parkinson has a new name shorter and more Office staff: Sharon Walton accurate, since TSR is more than a SPECIAL ATTRACTION Mary Cossman hobby-gaming company. The name Layout designer: Kristine L. Bartyzel change is the most immediately visible The DRAGON® magazine index . 45 Contributing editor: Ed Greenwood effect of several changes the company has Covering more than seven years National advertising representative: undergone lately. in the space of six pages Robert Dewey To the limit of this space, heres some 1409 Pebblecreek Glenview IL 60025 information about the changes, mostly Phone (312)998-6237 expressed in terms of how I think they OTHER FEATURES will affect the audience we reach. For a This issues contributing artists: specific answer to that, see the notice Clyde Caldwell Phil Foglio across the bottom of page 4: Ares maga- The ecology of the beholder . 6 Roger Raupp Mary Hanson- Jeff Easley Roberts zine and DRAGON® magazine are going The Nine Hells, Part II . 22 Dave Trampier Edward B. Wagner to stay out of each others turf from now From Malbolge through Nessus Larry Elmore on, giving the readers of each magazine more of what they read it for. Saved by the cavalry! . 56 DRAGON Magazine (ISSN 0279-6848) is pub- I mention that change here as an lished monthly for a subscription price of $24 per example of what has happened, some- Army in BOOT HILL® game terms year by Dragon Publishing, a division of TSR, Inc. -

Growing a Modern VICTORY GARDEN Everyone Is Looking for Ways They Can Help During the Current COVID-19 Outbreak
Cornell Cooperative Extension April 2020 of Jefferson County Growing a Modern VICTORY GARDEN Everyone is looking for ways they can help during the current COVID-19 outbreak. Planting a garden can be one way for your family to get healthy, fresh vegetables, save money, potentially help others through food donations, get exercise, and relieve stress. Consider these historic facts on Victory Gardens: • World War I: In 1917 home gardeners mobilized and the first Victory Gardens were planted. In 1918, more than 5.2 million gardens were INSIDE THIS GUIDE cultivated. Page 2. No Room for a Garden? Never Fear, Container Gardens are • World War II: In 1944, an estimated 20 million Victory Gardens Here! produced 8 million tons of food. This was 40% of all the fruits and Page 4. Traditional Vegetable Gardens, i.e. Gardening in the vegetables consumed in the U.S. Earth The current COVID-19 situation Page 5. Cool and Warm Season has sparked renewed interest in Vegetables- AKA, When Can I plant? food gardening. Many people are considering vegetable Page 8. Vegetable Transplants gardens as a way to increase Page 9. Everybody Loves Tomatoes! personal food security. This Page 11. Backyard Fruit Production- spring will see first time Some Things to Consider gardens, expansion of current Page 13. Fruits and Nuts You Can Grow in Northern New York gardens, and the re-start of long Page 14. Water, Weeds and Woes dormant food gardens. Page 15. Resources For those current and past Attachment: Cornell Recommended gardeners I don’t expect this information will tell you more than you Vegetable Varieties for New already know, although you may pick up some new tips. -

Information to Users
INFORMATION TO USERS This manuscript has been reproduced from the microfilm master. UMI films the text directly from the original or copy submitted. Thus, some thesis and dissertation copies are in typewriter face, while others may be from any type of computer printer. The quality of this reproduction is dependent upon the qualify of the copy submitted. Broken or indistinct print, colored or poor quality illustrations and photographs, print bleedthrough, substandard margins, and improper alignment can adversely affect reproduction. In the unlikely event that the author did not send UMI a complete manuscript and there are missing pages, these will be noted. Also, if unauthorized copyright material had to be removed, a note will indicate the deletion. Oversize materials (e.g., maps, drawings, charts) are reproduced by sectioning the original, beginning at the upper left-hand corner and continuing from left to right in equal sections with small overlaps. Each original is also photographed in one exposure and is included in reduced form atthe back of the book. Photographs included in the original manuscript have been reproduced xerographically in this copy. Higher quality 6" x 9" black and white photographic prints are available for any photographs or illustrations appearing in this copy for an additional charge. Contact UMI directly to order. University Microfilms International A Bell & Howell Information Company 300 North Zeeb Road, Ann Arbor, Ml 48106-1346 USA .313/761-4700 800/521-0600 Order Number 00-12,166 The use of leisure and its relation to social stratification Clarke, Alfred Carpenter, Ph.D. Ohio State University, 1955 UMI 300 N. -

Selected List of Vegetable Varieties for Gardeners in New York State
Selected List of Vegetable Varieties for Gardeners in New York State 2021 (Revised 11/20) Vegetable varieties listed in this report should be well adapted for New York State community, school and home gardens. It is recognized that varieties not listed here may be satisfactory or even perform better under certain conditions. We encourage gardens to rate the varieties at: vegvariety.cce.cornell.edu Visit our Vegetable Varieties for Gardeners in New York State website for detailed descriptions and some seed sources of more than 7,000 vegetable varieties including those listed in this report. Compare varieties, read ratings and reviews by fellow gardeners, and offer your own observations of which varieties perform best in your garden. Note: Future reports will be largely based on variety ratings from this site. vegvariety.cce.cornell.edu Cornell Garden-Based Learning Horticulture School of Integrative Plant Sciences Cornell University Ithaca, NY 14853-0327 www.gardening.cornell.edu Selected List of Vegetable Varieties for Gardeners in NYS – A. Helmholdt – page 2 of 8 Key to Notation At least 4 NY gardeners’ ratings averaging # New varieties to this year’s list * >3.5 stars at: vegvariety.cce.cornell.edu Downy mildew resistant or A Alternaria stem resistant DM tolerant Tolerance to Bean Common Mosaic Powdery mildew resistant or BCMV PM Virus BV1 & NY15 tolerant Bacterial leaf spot resistant strains 1, 2, BLS R Rust resistant and 3 are noted CTV Tolerance to citrus tristeza virus SE Sugar enhanced F Fusarium resistant SH2 Supersweet LBR Late -

SW Monthly Onlinecover
Werk Thoroughbred Consultants, Inc. presents WTC’s STAKES & MAIDEN WINNERS MONTHLY October, 2009 Featuring a monthly recap of the winners of unrestricted stakes races in North America and Europe, which includes our WTC “Best of Sale” selections and Mating Recommendations. Also included is a list of all maiden winners for the month sorted by sire. Published by Werk Thoroughbred Consultants, Inc. PO Box 1926, Fremont, CA 94538-0192 (510) 490-1111 / (510) 490-4499 (fax) www.werkhorse.com email: [email protected] Copyright 2009 WERK THOROUGHBRED CONSULTANTS MATINGS and BEST OF SALE STAKES WINNERS (Domestic Stakes $25,000 and up · October 1 through October 31, 2009) NORTH AMERICAN GRADED STAKES RESULTS Grade 1 Races SHADWELL TURF MILE S. ( GI ), KEE, $600,000, 3YO/UP, 1MT, 10-10. — COURT VISION, c, 4, Gulch--Weekend Storm, by Storm Bird. WTC “BEST OF SALE” – KEESEP06 - $180,000 – 2.0 STARS – A NICK ($350,000 2yo 2007 FTFFEB.). O-IEAH Stables and Resolute Group Stables, B-W. S. Farish &Kilroy Thoroughbred Partnership (KY), $360,000. — Karelian, g, 7, Bertrando--Leaning Tower, by Theatrical (IRE). WTC “BEST OF SALE” – KEESEP03 – ($47,000)RNA – 1.5 STARS – C+ NICK O-Green Lantern Stables LLC, B-Green Lantern Stables (KY), $120,000. — Mr. Sidney, h, 5, Storm Cat--Tomisue's Delight, by A.P. Indy. WTC “BEST OF SALE” – KEESEP05 - $3,900,000 – 3.5 STARS – A NICK O-Circle E Racing, B-Hilbert Thoroughbreds (KY), $60,000. JOE HIRSCH TURF CLASSIC INVITATIONAL S. ( GI ), BEL, $600,000, 3YO/UP, 1 1/2MT, 10-3. —INTERPATATION, g, 7, Langfuhr--Idealistic Cause, by Habitony. -

THE CORE SVIN Newsletter December 2014
THE CORE SVIN Newsletter December 2014 In This Issue President’s Message p. 2-4 Editor’s Corner p. 5 The Westin Diplomat Hotel, Hollywood, FL SVIN 2014 Meeting Highlights p. 6-8 Interventional Stroke Trials p. 9-11 The Evolving Technology of Flow Diversion p. 12-15 Pipeline and Antiplatelets p. 16-18 Field Administration of Stroke Therapy-Magnesium Phase III Results p. 18-19 ‘Basilar Artery’ SVIN FUNDRAISER SVIN Cilostazal Editorial 30% of proceeds go to SVIN p. 19-21 Journal Core Review of ARUBA Leah Guzman presented her beautiful Brain Series paintings at the 2014 p. 21-22 SVIN Annual Meeting and donated 30% of her proceeds to SVIN. She has offered this promotion again for any purchases generated from the December 2014 Newsletter. To view her artwork and make your purchase, please visit her website: www.leahguzman.com Leah Guzman, ATR-BC President’s Message At the crossroads of history: SVIN meeting witnesses news that will forever change acute stroke treatment paradigms It is a momentous time for patients with acute is- chemic stroke, their families and medical profes- sionals who treat them. Tudor Jovin, MD SVIN members, its supporters and friends had the privilege to live together moments of historical SVIN President importance at the SVIN’s 8-th annual meeting in Hollywood, Florida, which has just concluded on November 10-th 2014. During the two and a half entirely with stentrievers. The study, by now pub- days event superbly organized by Robin Nova- lished in the New England Journal of Medicine kovic MD, meeting chair, together with the rest of demonstrated a shift in the distribution of the pri- the meeting’s organizing committee, events have mary-outcome scores in favor of the intervention. -
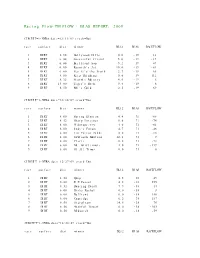
Racing Flow-TM FLOW + BIAS REPORT: 2009
Racing Flow-TM FLOW + BIAS REPORT: 2009 CIRCUIT=1-NYRA date=12/31/09 track=Dot race surface dist winner BL12 BIAS RACEFLOW 1 DIRT 5.50 Hollywood Hills 0.0 -19 13 2 DIRT 6.00 Successful friend 5.0 -19 -19 3 DIRT 6.00 Brilliant Son 5.2 -19 47 4 DIRT 6.00 Raynick's Jet 10.6 -19 -61 5 DIRT 6.00 Yes It's the Truth 2.7 -19 65 6 DIRT 8.00 Keep Thinking 0.0 -19 -112 7 DIRT 8.32 Storm's Majesty 4.0 -19 6 8 DIRT 13.00 Tiger's Rock 9.4 -19 6 9 DIRT 8.50 Mel's Gold 2.5 -19 69 CIRCUIT=1-NYRA date=12/30/09 track=Dot race surface dist winner BL12 BIAS RACEFLOW 1 DIRT 8.00 Spring Elusion 4.4 71 -68 2 DIRT 8.32 Sharp Instinct 0.0 71 -74 3 DIRT 6.00 O'Sotopretty 4.0 71 -61 4 DIRT 6.00 Indy's Forum 4.7 71 -46 5 DIRT 6.00 Ten Carrot Nikki 0.0 71 -18 6 DIRT 8.00 Sawtooth Moutain 12.1 71 9 7 DIRT 6.00 Cleric 0.6 71 -73 8 DIRT 6.00 Mt. Glittermore 4.0 71 -119 9 DIRT 6.00 Of All Times 0.0 71 0 CIRCUIT=1-NYRA date=12/27/09 track=Dot race surface dist winner BL12 BIAS RACEFLOW 1 DIRT 8.50 Quip 4.5 -38 49 2 DIRT 6.00 E Z Passer 4.2 -38 255 3 DIRT 8.32 Dancing Daisy 7.9 -38 14 4 DIRT 6.00 Risky Rachel 0.0 -38 8 5 DIRT 6.00 Kaffiend 0.0 -38 150 6 DIRT 6.00 Capridge 6.2 -38 187 7 DIRT 8.50 Stargleam 14.5 -38 76 8 DIRT 8.50 Wishful Tomcat 0.0 -38 -203 9 DIRT 8.50 Midwatch 0.0 -38 -59 CIRCUIT=1-NYRA date=12/26/09 track=Dot race surface dist winner BL12 BIAS RACEFLOW 1 DIRT 6.00 Papaleo 7.0 108 129 2 DIRT 6.00 Overcommunication 1.0 108 -72 3 DIRT 6.00 Digger 0.0 108 -211 4 DIRT 6.00 Bryan Kicks 0.0 108 136 5 DIRT 6.00 We Get It 16.8 108 129 6 DIRT 6.00 Yawanna Trust 4.5 108 -21 7 DIRT 6.00 Smarty Karakorum 6.5 108 83 8 DIRT 8.32 Almighty Silver 18.7 108 133 9 DIRT 8.32 Offlee Cool 0.0 108 -60 CIRCUIT=1-NYRA date=12/13/09 track=Dot race surface dist winner BL12 BIAS RACEFLOW 1 DIRT 8.32 Crafty Bear 3.0 -158 -139 2 DIRT 6.00 Cheers Darling 0.5 -158 61 3 DIRT 6.00 Iberian Gate 3.0 -158 154 4 DIRT 6.00 Pewter 0.5 -158 8 5 DIRT 6.00 Wolfson 6.2 -158 86 6 DIRT 6.00 Mr. -

\0-9\0 and X ... \0-9\0 Grad Nord ... \0-9\0013 ... \0-9\007 Car Chase ... \0-9\1 X 1 Kampf ... \0-9\1, 2, 3
... \0-9\0 and X ... \0-9\0 Grad Nord ... \0-9\0013 ... \0-9\007 Car Chase ... \0-9\1 x 1 Kampf ... \0-9\1, 2, 3 ... \0-9\1,000,000 ... \0-9\10 Pin ... \0-9\10... Knockout! ... \0-9\100 Meter Dash ... \0-9\100 Mile Race ... \0-9\100,000 Pyramid, The ... \0-9\1000 Miglia Volume I - 1927-1933 ... \0-9\1000 Miler ... \0-9\1000 Miler v2.0 ... \0-9\1000 Miles ... \0-9\10000 Meters ... \0-9\10-Pin Bowling ... \0-9\10th Frame_001 ... \0-9\10th Frame_002 ... \0-9\1-3-5-7 ... \0-9\14-15 Puzzle, The ... \0-9\15 Pietnastka ... \0-9\15 Solitaire ... \0-9\15-Puzzle, The ... \0-9\17 und 04 ... \0-9\17 und 4 ... \0-9\17+4_001 ... \0-9\17+4_002 ... \0-9\17+4_003 ... \0-9\17+4_004 ... \0-9\1789 ... \0-9\18 Uhren ... \0-9\180 ... \0-9\19 Part One - Boot Camp ... \0-9\1942_001 ... \0-9\1942_002 ... \0-9\1942_003 ... \0-9\1943 - One Year After ... \0-9\1943 - The Battle of Midway ... \0-9\1944 ... \0-9\1948 ... \0-9\1985 ... \0-9\1985 - The Day After ... \0-9\1991 World Cup Knockout, The ... \0-9\1994 - Ten Years After ... \0-9\1st Division Manager ... \0-9\2 Worms War ... \0-9\20 Tons ... \0-9\20.000 Meilen unter dem Meer ... \0-9\2001 ... \0-9\2010 ... \0-9\21 ... \0-9\2112 - The Battle for Planet Earth ... \0-9\221B Baker Street ... \0-9\23 Matches .. -

NPRC) VIP List, 2009
Description of document: National Archives National Personnel Records Center (NPRC) VIP list, 2009 Requested date: December 2007 Released date: March 2008 Posted date: 04-January-2010 Source of document: National Personnel Records Center Military Personnel Records 9700 Page Avenue St. Louis, MO 63132-5100 Note: NPRC staff has compiled a list of prominent persons whose military records files they hold. They call this their VIP Listing. You can ask for a copy of any of these files simply by submitting a Freedom of Information Act request to the address above. The governmentattic.org web site (“the site”) is noncommercial and free to the public. The site and materials made available on the site, such as this file, are for reference only. The governmentattic.org web site and its principals have made every effort to make this information as complete and as accurate as possible, however, there may be mistakes and omissions, both typographical and in content. The governmentattic.org web site and its principals shall have neither liability nor responsibility to any person or entity with respect to any loss or damage caused, or alleged to have been caused, directly or indirectly, by the information provided on the governmentattic.org web site or in this file. The public records published on the site were obtained from government agencies using proper legal channels. Each document is identified as to the source. Any concerns about the contents of the site should be directed to the agency originating the document in question. GovernmentAttic.org is not responsible for the contents of documents published on the website.