How to Be Invisble, Revised Edition
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

What Is Peer-To-Peer File Transfer? Bandwidth It Can Use
sharing, with no cap on the amount of commonly used to trade copyrighted music What is Peer-to-Peer file transfer? bandwidth it can use. Thus, a single NSF PC and software. connected to NSF’s LAN with a standard The Recording Industry Association of A peer-to-peer, or “P2P,” file transfer 100Mbps network card could, with KaZaA’s America tracks users of this software and has service allows the user to share computer files default settings, conceivably saturate NSF’s begun initiating lawsuits against individuals through the Internet. Examples of P2P T3 (45Mbps) internet connection. who use P2P systems to steal copyrighted services include KaZaA, Grokster, Gnutella, The KaZaA software assesses the quality of material or to provide copyrighted software to Morpheus, and BearShare. the PC’s internet connection and designates others to download freely. These services are set up to allow users to computers with high-speed connections as search for and download files to their “Supernodes,” meaning that they provide a How does use of these services computers, and to enable users to make files hub between various users, a source of available for others to download from their information about files available on other create security issues at NSF? computers. users’ PCs. This uses much more of the When configuring these services, it is computer’s resources, including bandwidth possible to designate as “shared” not only the and processing capability. How do these services function? one folder KaZaA sets up by default, but also The free version of KaZaA is supported by the entire contents of the user’s computer as Peer to peer file transfer services are highly advertising, which appears on the user well as any NSF network drives to which the decentralized, creating a network of linked interface of the program and also causes pop- user has access, to be searchable and users. -

Bad Is Stronger Than Good
Review of General Psychology Copyright 2001 by the Educational Publishing Foundation 2001. Vol. 5. No. 4. 323-370 1089-2680/O1/S5.O0 DOI: 10.1037//1089-2680.5.4.323 Bad Is Stronger Than Good Roy F. Baumeister and Ellen Bratslavsky Catrin Finkenauer Case Western Reserve University Free University of Amsterdam Kathleen D. Vohs Case Western Reserve University The greater power of bad events over good ones is found in everyday events, major life events (e.g., trauma), close relationship outcomes, social network patterns, interper- sonal interactions, and learning processes. Bad emotions, bad parents, and bad feedback have more impact than good ones, and bad information is processed more thoroughly than good. The self is more motivated to avoid bad self-definitions than to pursue good ones. Bad impressions and bad stereotypes are quicker to form and more resistant to disconfirmation than good ones. Various explanations such as diagnosticity and sa- lience help explain some findings, but the greater power of bad events is still found when such variables are controlled. Hardly any exceptions (indicating greater power of good) can be found. Taken together, these findings suggest that bad is stronger than good, as a general principle across a broad range of psychological phenomena. Centuries of literary efforts and religious pothesis that bad is stronger than good (see also thought have depicted human life in terms of a Rozin & Royzman, in press). That is, events struggle between good and bad forces. At the that are negatively valenced (e.g., losing metaphysical level, evil gods or devils are the money, being abandoned by friends, and receiv- opponents of the divine forces of creation and ing criticism) will have a greater impact on the harmony. -

The Effects of Digital Music Distribution" (2012)
Southern Illinois University Carbondale OpenSIUC Research Papers Graduate School Spring 4-5-2012 The ffecE ts of Digital Music Distribution Rama A. Dechsakda [email protected] Follow this and additional works at: http://opensiuc.lib.siu.edu/gs_rp The er search paper was a study of how digital music distribution has affected the music industry by researching different views and aspects. I believe this topic was vital to research because it give us insight on were the music industry is headed in the future. Two main research questions proposed were; “How is digital music distribution affecting the music industry?” and “In what way does the piracy industry affect the digital music industry?” The methodology used for this research was performing case studies, researching prospective and retrospective data, and analyzing sales figures and graphs. Case studies were performed on one independent artist and two major artists whom changed the digital music industry in different ways. Another pair of case studies were performed on an independent label and a major label on how changes of the digital music industry effected their business model and how piracy effected those new business models as well. I analyzed sales figures and graphs of digital music sales and physical sales to show the differences in the formats. I researched prospective data on how consumers adjusted to the digital music advancements and how piracy industry has affected them. Last I concluded all the data found during this research to show that digital music distribution is growing and could possibly be the dominant format for obtaining music, and the battle with piracy will be an ongoing process that will be hard to end anytime soon. -

Echoes of Memory Volume 9
Echoes of Memory Volume 9 CONTENTS JACQUELINE MENDELS BIRN MICHEL MARGOSIS The Violins of Hope ...................................................2 In Transit, Spain ........................................................ 28 RUTH COHEN HARRY MARKOWICZ Life Is Good ....................................................................3 A Letter to the Late Mademoiselle Jeanne ..... 34 Sunday Lunch at Charlotte’s House ................... 36 GIDEON FRIEDER True Faith........................................................................5 ALFRED MÜNZER Days of Remembrance in Rymanow ..................40 ALBERT GARIH Reunion in Ebensee ................................................. 43 Flory ..................................................................................8 My Mother ..................................................................... 9 HALINA YASHAROFF PEABODY Lying ..............................................................................46 PETER GOROG A Gravestone for Those Who Have None .........12 ALFRED TRAUM A Three-Year-Old Saves His Mother ..................14 The S.S. Zion ...............................................................49 The Death Certificate That Saved Vienna, Chanukah 1938 ...........................................52 Our Lives ..................................................................................... 16 SUSAN WARSINGER JULIE KEEFER Bringing the Lessons Home ................................. 54 Did He Know I Was Jewish? ...................................18 Feeling Good ...............................................................55 -

Piratez Are Just Disgruntled Consumers Reach Global Theaters That They Overlap the Domestic USA Blu-Ray Release
Moviegoers - or perhaps more accurately, lovers of cinema - are frustrated. Their frustrations begin with the discrepancies in film release strategies and timing. For example, audiences that saw Quentin Tarantino’s1 2 Django Unchained in the United States enjoyed its opening on Christmas day 2012; however, in Europe and other markets, viewers could not pay to see the movie until after the 17th of January 2013. Three weeks may not seem like a lot, but some movies can take months to reach an international audience. Some take so long to Piratez Are Just Disgruntled Consumers reach global theaters that they overlap the domestic USA Blu-Ray release. This delay can seem like an eternity for ultiscreen is at the top of the entertainment a desperate fan. This frustrated enthusiasm, combined industry’s agenda for delivering digital video. This with a lack of timely availability, leads to the feeling of M is discussed in the context of four main screens: being treated as a second class citizen - and may lead TVs, PCs, tablets and mobile phones. The premise being the over-anxious fan to engage in piracy. that multiscreen enables portability, usability and flexibility for consumers. But, there is a fifth screen which There has been some evolution in this practice, with is often overlooked – the cornerstone of the certain films being released simultaneously to a domestic and global audience. For example, Avatar3 was released entertainment industry - cinema. This digital video th th ecosystem is not complete without including cinema, and in theaters on the 10 and 17 of December in most it certainly should be part of the multiscreen discussion. -

30 ROCK� � "Hard to Swallow"� � Written By� Sam Mandragona
THIS SCRIPTS IS AVAILABLE TO READ OR DOWNLOAD PLEASE SCROLL DOWN 30 ROCK "Hard to Swallow" Written by Sam Mandragona Sam Mandragona [email protected] 609 819 5921 1. ACT ONE FADE IN: EXT. 45TH STREET - DAY LIZ LEMON is walking down the street and stops at a store to watch some people play Rock Band. She glances up at the TVs in the window to see CNBC with the caption title "GE and Rooster Roaster Merger." CUT TO: INT. GE BOARD ROOM - DAY Seated at the conference table are DON GEISS, JACK DONAGHY, COLONEL AUGUSTUS SHERIDAN, the Chairman of Rooster Roaster and JONAH FLEMING, the CEO of The BIG Network with an unknown woman. The press conference is underway. DON GEISS This is the greatest opportunity in the history of General Electric to prepare us for the future. Everybody at the table nods their approval and smiles. DON GEISS (CONT'D) Isn't that right Colonel Sheridan? The Colonel is a tall man with white muttonchops, wearing a tan suit with a large cowboy hat. He stands and picks up the microphone to make his point. COLONEL SHERIDAN Well, Great Balls of Fire, this here is 'bout the finest business deal I rightly done since I started sellin' chicken tenders from the back of my 1965 Vista Cruiser wagon. The Colonel sits down as Don Geiss motions for a question from the reporters. REPORTER 1 Mr. Geiss, you each own a television network, NBC and the BIG Network. Will this pose a problem for FCC approval? 2. Jack clears his throat and motions to Don Geiss who nods approvingly. -

Cash Country Service Listing April 2014
® WorldLink Payment Services Cash Country Service Listing April 2014 WorldLink® Cash payments is currently offered through Western Union and is thus required to follow the requirements and regulations of within the destination country of your beneficiary. Failure to meet those requirements will result in the payment being rejected. The information provided in the WorldLink Cash Country Service Listing includes updates sent to Western Union prior to:April 2014. The material contained in this Cash Country Service Listing is for informational purposes only, and is provided solely as a courtesy by WorldLink. Although WorldLink believes this information to be reliable, WorldLink makes no representation or warranty with respect to its accuracy or completeness. The information in this Cash Country Service Listing does not constitute a recommendation to take or refrain from taking any action, and WorldLink is not providing any tax, legal or other advice. Citigroup and its affiliates accept no liability whatsoever for any use of this material or any action taken based on or arising from anything contained herein. The information in this Cash Country Service Listing is subject to change at any time according to changes in local law. WorldLink is not obligated to inform you of changes to local law. Citibank Europe plc (“Citibank Europe”) may, at its discretion, reasonably modify or amend this Cash Country Service Listing from time to time, which modification or amendment will become binding when your organization receives a copy of it. These materials are confidential and proprietary to Citigroup or its affiliates and no part of these materials should be reproduced, published in any form by any means, electronic or mechanical including photocopy or any information storage or retrieval system nor should the materials be disclosed to third parties without our express written authorization. -

The Robustness of Content-Based Search in Hierarchical Peer to Peer Networks
The Robustness of Content-Based Search in Hierarchical Peer to Peer Networks ∗ M. Elena Renda Jamie Callan I.S.T.I. – C.N.R. Language Technologies Institute and School of Computer Science Scuola Superiore Sant’Anna Carnegie Mellon University I-56100 Pisa, Italy Pittsburgh, PA 15213, US [email protected] [email protected] ABSTRACT Keywords Hierarchical peer to peer networks with multiple directory services Peer to Peer, Hierarchical, Search, Retrieval, Content-based, Ro- are an important architecture for large-scale file sharing due to their bustness effectiveness and efficiency. Recent research argues that they are also an effective method of providing large-scale content-based federated search of text-based digital libraries. In both cases the 1. INTRODUCTION directory services are critical resources that are subject to attack Peer to peer (P2P) networks have emerged in recent years as a or failure, but the latter architecture may be particularly vulnera- popular method of sharing information, primarily popular music, ble because content is less likely to be replicated throughout the movies, and software, among large numbers of networked com- network. puters. Computers (‘nodes’) in P2P networks can be information This paper studies the robustness, effectiveness and efficiency providers and information consumers, and may provide network of content-based federated search in hierarchical peer to peer net- services such as message routing and regional directory services. works when directory services fail unexpectedly. Several recovery A single node may play several roles at once, for example, posting methods are studied using simulations with varying failure rates. queries, sharing files, and relaying messages. -

The Postal Service Is Amending Mailing Standards of the United
This document is scheduled to be published in the Federal Register on 10/11/2018 and available online at https://federalregister.gov/d/2018-22107 , and on govinfo.gov 7710-12 POSTAL SERVICE 39 CFR Part 111 POSTNET Barcode AGENCY: Postal Service™. ACTION: Final rule. SUMMARY: The Postal Service is amending Mailing Standards of the United States Postal Service, Domestic Mail Manual (DMM®) to remove all references to the POSTNET™ barcode. DATES: Effective Date: [INSERT DATE PUBLISHED IN THE FEDERAL REGISTER]. FOR FURTHER INFORMATION CONTACT: Lizbeth Dobbins at (202) 268-3789 or Garry Rodriguez at (202) 268-7261. SUPPLEMENTARY INFORMATION: The Postal Service published a notice of proposed rulemaking on July 23, 2018, (83 FR 34806–07) to amend the DMM to remove all references to the POSTNET barcode. This decision was based on the limited use of the POSTNET barcode and the need to simplify the standards in regard to barcoding letter-size and flat-size mailpieces. The Postal Service received 1 formal response which was in agreement with the removal of POSTNET barcodes in the DMM. The Postal Service will remove all references to the POSTNET barcode from the DMM. The Postal Service will continue to process mailpieces with a POSTNET barcode to accommodate customers who may have preprinted stock bearing a POSTNET barcode. List of Subjects in 39 CFR Part 111 Administrative practice and procedure, Postal Service. The Postal Service adopts the following changes to Mailing Standards of the United States Postal Service, Domestic Mail Manual (DMM), incorporated by reference in the Code of Federal Regulations. See 39 CFR 111.1. -

Bossypants? One, Because the Name Two and a Half Men Was Already Taken
Acknowledgments I would like to gratefully thank: Kay Cannon, Richard Dean, Eric Gurian, John Riggi, and Tracy Wigfield for their eyes and ears. Dave Miner for making me do this. Reagan Arthur for teaching me how to do this. Katie Miervaldis for her dedicated service and Latvian demeanor. Tom Ceraulo for his mad computer skills. Michael Donaghy for two years of Sundays. Jeff and Alice Richmond for their constant loving encouragement and their constant loving interruption, respectively. Thank you to Lorne Michaels, Marc Graboff, and NBC for allowing us to reprint material. Contents Front Cover Image Welcome Dedication Introduction Origin Story Growing Up and Liking It All Girls Must Be Everything Delaware County Summer Showtime! That’s Don Fey Climbing Old Rag Mountain Young Men’s Christian Association The Windy City, Full of Meat My Honeymoon, or A Supposedly Fun Thing I’ll Never Do Again Either The Secrets of Mommy’s Beauty Remembrances of Being Very Very Skinny Remembrances of Being a Little Bit Fat A Childhood Dream, Realized Peeing in Jars with Boys I Don’t Care If You Like It Amazing, Gorgeous, Not Like That Dear Internet 30 Rock: An Experiment to Confuse Your Grandparents Sarah, Oprah, and Captain Hook, or How to Succeed by Sort of Looking Like Someone There’s a Drunk Midget in My House A Celebrity’s Guide to Celebrating the Birth of Jesus Juggle This The Mother’s Prayer for Its Daughter What Turning Forty Means to Me What Should I Do with My Last Five Minutes? Acknowledgments Copyright * Or it would be the biggest understatement since Warren Buffett said, “I can pay for dinner tonight.” Or it would be the biggest understatement since Charlie Sheen said, “I’m gonna have fun this weekend.” So, you have options. -
C:\Documents and Settings\Fre...N.Default\Cache\0\11
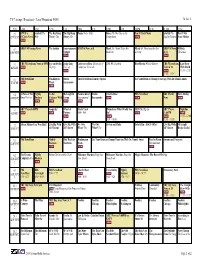
TV Listings Broadcast - Local Broadcast 94501 Fri, Jun. 8 PDT 6 PM 6:30 7 PM 7:30 8 PM 8:30 9 PM 9:30 10 PM 10:30 11 PM 11:30 2.1 KTVU 6 Seinfeld The The Big Bang The Big Bang House Better Half Bones The Hot Dog in the Ten O'Clock News Seinfeld The How I Met KTVUDT O'Clock News Wife Theory The Theory The Competition new English Patient Your Mother new 4.1 KRON 4 Evening News The Insider Entertainment KRON 4 News at 8 Monk Mr. Monk Takes His Monk Mr. Monk and the Red KRON 4 News 30 Rock KRONDT Tonight Medicine Herring at 11 Christmas new new 5.1 CBS 5 Eyewitness News at 6PM Eye on the Bay Judge Judy Undercover Boss University of CSI: NY Crushed Blue Bloods Whistle Blower CBS 5 Eyewitness Late Show KPIXDT new Daytrip: Tires of California, Riverside News at 11 With David new new 11:35 - 12:37 11:00 - 11:35 6.1 PBS NewsHour Washington Studio The Ed Sullivan Comedy Special Use Your Brain to Change Your Age With Dr. Daniel Amen KVIEDT new Week Sacramento new 6.2 A Place of Our Nightly To the McLaughlin Need to Know Studio Charlie Rose PBS NewsHour BBC World Tavis Smiley KVIEDT2 Own Week in Business Contrary With Group International Sacramento new new News new new new new new 7.1 ABC7 News 6:00PM Jeopardy! Wheel of Shark Tank Primetime: What Would You 20/20 The Big Lie ABC7 News Nightline KGODT new new Fortune 8:00 - 9:01 Do? new 11:00PM new new new new 11:35 - 12:00 9:01 - 10:00 11:00 - 11:35 7.2 Alyssa Milano Uses Wen Hair! Live Big With Live Big With We Owe We Owe Steven and Chris Total Gym - $14.95 Offer! Live Big With My Family KGODT2 Ali Vincent Ali Vincent What? The What? The Ali Vincent Recipe Rocks! 9.1 PBS NewsHour Nightly This Week in Washington Use Your Brain to Change Your Age With Dr. -

Postal Service 39 CFR Part 111 Changes to the Domestic Mail Manual to Implement Confirm Service; Final Rule
Thursday, August 15, 2002 Part IV Postal Service 39 CFR Part 111 Changes To the Domestic Mail Manual To Implement Confirm Service; Final Rule VerDate Aug<2,>2002 16:44 Aug 14, 2002 Jkt 197001 PO 00000 Frm 00001 Fmt 4717 Sfmt 4717 E:\FR\FM\15AUR4.SGM pfrm17 PsN: 15AUR4 53454 Federal Register / Vol. 67, No. 158 / Thursday, August 15, 2002 / Rules and Regulations POSTAL SERVICE seq.), filed a Request for a recommended comments and recommendations for decision by the Postal Rate Commission improving and expanding Confirm, and 39 CFR Part 111 (PRC) on the proposed classification and for ensuring that the service meets the [Docket No. MC 2002–1] fees for Confirm, a new service using a business needs and the operational uniquely identifying mailer-applied requirements of the mailing industry at Changes to the Domestic Mail Manual barcode called PLANET Code. Using large. Moreover, the Postal Service has To Implement Confirm Service these barcodes, along with the continued to solicit recommendations appropriate delivery address POSTNET from the mailing industry for AGENCY: Postal Service. barcodes, enables a participating mailer enhancements to the infrastructure ACTION: Final rule. to identify where and when outgoing supporting this subscriber-based automation-compatible mail and service. The recommendations coming SUMMARY: This final rule sets forth the incoming automation-compatible reply from actual customer use and testing of Domestic Mail Manual (DMM) mail are scanned in various postal the whole Confirm system have greatly standards adopted