Alan Turing - Wikipedia, the Free Encyclopedia Page 1 of 23
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Crypto Review
Crypto Review Track 3: Security Workshop Overview • What is Cryptography? • Symmetric Key Cryptography • Asymmetric Key Cryptography • Block and Stream Cipher • Digital Signature and Message Digest Cryptography • Cryptography is everywhere German Lorenz cipher machine Cryptography • Cryptography deals with creang documents that can be shared secretly over public communicaon channels • Other terms closely associated – Cryptanalysis = code breaking – Cryptology • Kryptos (hidden or secret) and Logos (descripGon) = secret speech / communicaon • combinaon of cryptography and cryptanalysis • Cryptography is a funcGon of plaintext and a Notaon: Plaintext (P) cryptographic key Ciphertext (C) C = F(P, k) Cryptographic Key (k) Typical Scenario • Alice wants to send a “secret” message to Bob • What are the possible problems? – Data can be intercepted • What are the ways to intercept this message? • How to conceal the message? – Encrypon Crypto Core • Secure key establishment Alice has key (k) Bob has key (k) • Secure communicaon m Confidenality and integrity m m Alice has key (k) Bob has key (k) Source: Dan Boneh, Stanford It can do much more • Digital Signatures • Anonymous communicaon • Anonymous digital cash – Spending a digital coin without anyone knowing my idenGty – Buy online anonymously? • ElecGons and private aucGons – Finding the winner without actually knowing individual votes (privacy) Source: Dan Boneh, Stanford Other uses are also theoreGcally possible (Crypto magic) What did she • Privately outsourcing computaon search for? E(query) -

Simply Turing
Simply Turing Simply Turing MICHAEL OLINICK SIMPLY CHARLY NEW YORK Copyright © 2020 by Michael Olinick Cover Illustration by José Ramos Cover Design by Scarlett Rugers All rights reserved. No part of this publication may be reproduced, distributed, or transmitted in any form or by any means, including photocopying, recording, or other electronic or mechanical methods, without the prior written permission of the publisher, except in the case of brief quotations embodied in critical reviews and certain other noncommercial uses permitted by copyright law. For permission requests, write to the publisher at the address below. [email protected] ISBN: 978-1-943657-37-7 Brought to you by http://simplycharly.com Contents Praise for Simply Turing vii Other Great Lives x Series Editor's Foreword xi Preface xii Acknowledgements xv 1. Roots and Childhood 1 2. Sherborne and Christopher Morcom 7 3. Cambridge Days 15 4. Birth of the Computer 25 5. Princeton 38 6. Cryptology From Caesar to Turing 44 7. The Enigma Machine 68 8. War Years 85 9. London and the ACE 104 10. Manchester 119 11. Artificial Intelligence 123 12. Mathematical Biology 136 13. Regina vs Turing 146 14. Breaking The Enigma of Death 162 15. Turing’s Legacy 174 Sources 181 Suggested Reading 182 About the Author 185 A Word from the Publisher 186 Praise for Simply Turing “Simply Turing explores the nooks and crannies of Alan Turing’s multifarious life and interests, illuminating with skill and grace the complexities of Turing’s personality and the long-reaching implications of his work.” —Charles Petzold, author of The Annotated Turing: A Guided Tour through Alan Turing’s Historic Paper on Computability and the Turing Machine “Michael Olinick has written a remarkably fresh, detailed study of Turing’s achievements and personal issues. -

Algorithmic Social Sciences Research Unit ASSRU Department of Economics University of Trento Via Inama 5 381 22 Trento, Italy
Algorithmic Social Sciences Research Unit ASSRU Department of Economics University of Trento Via Inama 5 381 22 Trento, Italy Discussion Paper Series 7 – 2014/I Alan Turing A Forbidden Fruit, its Serendipitous Fall and a Poisoned Bite K. VELA VELUPILLAI1 August 2014 ! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! 1!Department of Economics, The New School for Social Research (NSSR), 6 East 16th Street, New York, NY 10003, USA & Department of Economics, University of Trento, via Inama 5, 381 22 Trento, Italy. Email: [email protected] Forthcoming in: the Interdisciplinary Journal of Economics and Business Law (IJEBL), Vol. 4, Issue 1. Alan Turing A Forbidden Fruit, its Serendipitous Fall and a Poisoned Bite K. Vela Velupillai Department of Economics New School for Social Research (NSSR) New York, NY 10003 USA 15 August 2014 “We can only see a short distance ahead, but we can see plenty that needs to be done.”. Turing, 1950, p. 460. The metaphor of the ‘fall of man’ (at least in Christian traditions), the story of the origins of the Universal Law of Gravitation (at the imaginative hands of Newton) and the ‘bite’ that tragically ended a young Turing’s life, sixty years ago, even at the very heights of his intellectual powers, are all about the way apples have shaped our fate – for good and evil. This is a commemorative essay, on the sixtieth anniversary of the death of Turing, apparently by his own hands, as a result of a bite – or two – in an apple, found to have been poisoned, most likely by himself (although conspiracy theories have not completely ‘died’, during these six decades of sadness, at his untimely death). -

Alan Turing: Virtuosity and Visualisation
http://dx.doi.org/10.14236/ewic/EVA2016.40 Alan Turing: Virtuosity and visualisation Jonathan P. Bowen London South Bank University, UK & Museophile Limited, Oxford, UK http://www.jpbowen.com [email protected] Alan Turing (1912–1954) has been increasingly recognised as an important mathematician who, despite his short life, developed mathematical ideas that today have led to foundational aspects of computer science, especially with respect to computability, artificial intelligence and morphogenesis (the growth of biological patterns, important in mathematical biology). Some of Turing’s mathematics and related ideas can be visualised in interesting and even artistic ways, aided using software. In addition, a significant corpus of the historical documentation on Turing can now be accessed online as a number of major archives have digitised material related to Turing. This paper introduces some of the major scientific work of Turing and ways in which it can be visualised, often artistically. Turing’s fame has, especially since his centenary in 2012, reached a level where he has had a cultural influence on the arts in general. Although the story of Turing can be seen as one of tragedy, with his life cut short, from a historical viewpoint Turing’s contribution to humankind has been triumphant. Artificial Intelligence. Digital art. History of mathematics. Morphogenesis. Turing Machines. Visualisation. 1. BACKGROUND AND INTRODUCTION a Turing Machine, with visualisations related to of some of Turing’s ideas. Section 3 presents some Alan Mathison Turing, OBE, FRS (23 June 1912 – 7 Turing-related artwork, leading to a new book cover. June 1954) was a British mathematician and In Section 4, major archives relating to Turing are codebreaker (Newman 1955, Hodges 1983/2012). -

A Complete Bibliography of Publications in Cryptologia
A Complete Bibliography of Publications in Cryptologia Nelson H. F. Beebe University of Utah Department of Mathematics, 110 LCB 155 S 1400 E RM 233 Salt Lake City, UT 84112-0090 USA Tel: +1 801 581 5254 FAX: +1 801 581 4148 E-mail: [email protected], [email protected], [email protected] (Internet) WWW URL: http://www.math.utah.edu/~beebe/ 04 September 2021 Version 3.64 Title word cross-reference 10016-8810 [?, ?]. 1221 [?]. 125 [?]. 15.00/$23.60.0 [?]. 15th [?, ?]. 16th [?]. 17-18 [?]. 18 [?]. 180-4 [?]. 1812 [?]. 18th (t; m)[?]. (t; n)[?, ?]. $10.00 [?]. $12.00 [?, ?, ?, ?, ?]. 18th-Century [?]. 1930s [?]. [?]. 128 [?]. $139.99 [?]. $15.00 [?]. $16.95 1939 [?]. 1940 [?, ?]. 1940s [?]. 1941 [?]. [?]. $16.96 [?]. $18.95 [?]. $24.00 [?]. 1942 [?]. 1943 [?]. 1945 [?, ?, ?, ?, ?]. $24.00/$34 [?]. $24.95 [?, ?]. $26.95 [?]. 1946 [?, ?]. 1950s [?]. 1970s [?]. 1980s [?]. $29.95 [?]. $30.95 [?]. $39 [?]. $43.39 [?]. 1989 [?]. 19th [?, ?]. $45.00 [?]. $5.95 [?]. $54.00 [?]. $54.95 [?]. $54.99 [?]. $6.50 [?]. $6.95 [?]. $69.00 2 [?, ?]. 200/220 [?]. 2000 [?]. 2004 [?, ?]. [?]. $69.95 [?]. $75.00 [?]. $89.95 [?]. th 2008 [?]. 2009 [?]. 2011 [?]. 2013 [?, ?]. [?]. A [?]. A3 [?, ?]. χ [?]. H [?]. k [?, ?]. M 2014 [?]. 2017 [?]. 2019 [?]. 20755-6886 [?, ?]. M 3 [?]. n [?, ?, ?]. [?]. 209 [?, ?, ?, ?, ?, ?]. 20th [?]. 21 [?]. 22 [?]. 220 [?]. 24-Hour [?, ?, ?]. 25 [?, ?]. -Bit [?]. -out-of- [?, ?]. -tests [?]. 25.00/$39.30 [?]. 25.00/839.30 [?]. 25A1 [?]. 25B [?]. 26 [?, ?]. 28147 [?]. 28147-89 000 [?]. 01Q [?, ?]. [?]. 285 [?]. 294 [?]. 2in [?, ?]. 2nd [?, ?, ?, ?]. 1 [?, ?, ?, ?]. 1-4398-1763-4 [?]. 1/2in [?, ?]. 10 [?]. 100 [?]. 10011-4211 [?]. 3 [?, ?, ?, ?]. 3/4in [?, ?]. 30 [?]. 310 1 2 [?, ?, ?, ?, ?, ?, ?]. 312 [?]. 325 [?]. 3336 [?, ?, ?, ?, ?, ?]. affine [?]. [?]. 35 [?]. 36 [?]. 3rd [?]. Afluisterstation [?, ?]. After [?]. Aftermath [?]. Again [?, ?]. Against 4 [?]. 40 [?]. 44 [?]. 45 [?]. 45th [?]. 47 [?]. [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. Age 4in [?, ?]. [?, ?]. Agencies [?]. Agency [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. -

Annotated Bibliography Primary Sources
1 Annotated Bibliography Primary Sources “Alan Turing's Trial Charges and Sentences, 31 March 1952.” Alan Turing: The Enigma, Andrew Hodges, https://www.turing.org.uk/sources/sentence.html. This source is an image from the Alan Turing: The Enigma website depicting the arrest and sentencing record of Alan Turing and his lover Arnold Murray from 1952. This primary source shows off the fact that Turing stood strong against the charges of “indecency” that were leveled his way due to his sexuality and pleaded guilty. It interested our group to find out that Murray received a much lighter sentence than Turing for the same “crime” “A Memoir of Turing in 1954 from by M.H. Newman.” The Turing Digital Archive, King's College, Cambridge, http://www.turingarchive.org/viewer/?id=18&title=Manchester Guardian June 1954. This source is a primary source image from The Turing Digital Archive containing newspaper clippings of Turing’s obituary and an appreciation article. These images helped us to understand the significance that Alan Turing had to society at the time of his death, giving us a starting point to observe how the legacy of Turing grew after his death, as well as the impact his life had even after it came to a close. “AMT Aged 16, Head and Shoulders.” The Turing Digital Archive, King's College, Cambridge, http://www.turingarchive.org/viewer/?id=521&title=4. This image of Alan Turing as a young man helps us depict his life as a story rather than a disconnected series of events. We included it because we felt that it was important to discuss Turing’s early years and education as well as his work on Enigma and his personal life in order to present the full story to the best of our ability on our website. -

Profalanturing-Decoded-Biography
CONTENTS Title Introduction 1. Unreliable Ancestors 2. Dismal Childhoods 3. Direction of Travel 4. Kingsman 5. Machinery of Logic 6. Prof 7. Looking Glass War 8. Lousy Computer 9. Taking Shape 10. Machinery of Justice 11. Unseen Worlds Epilogue: Alan Turing Decoded Notes and Accreditations Copyright Blue Plaques in Hampton, Maida Vale, Manchester and Wilmslow. At Bletchley Park, where Alan Turing did the work for which he is best remembered, there is no plaque but a museum exhibition. INTRODUCTION ALAN TURING is now a household name, and in Britain he is a national hero. There are several biographies, a handful of documentaries, one Hollywood feature film, countless articles, plays, poems, statues and other tributes, and a blue plaque in almost every town where he lived or worked. One place which has no blue plaque is Bletchley Park, but there is an entire museum exhibition devoted to him there. We all have our personal image of Alan Turing, and it is easy to imagine him as a solitary, asocial genius who periodically presented the world with stunning new ideas, which sprang unaided and fully formed from his brain. The secrecy which surrounded the story of Bletchley Park after World War Two may in part be responsible for the commonly held view of Alan Turing. For many years the codebreakers were permitted only to discuss the goings-on there in general, anecdotal terms, without revealing any of the technicalities of their work. So the easiest things to discuss were the personalities, and this made good copy: eccentric boffins busted the Nazi machine. -

Natural/Unconventional Computing and Its Philosophical Significance
Entropy 2012, 14, 2408-2412; doi:10.3390/e14122408 OPEN ACCESS entropy ISSN 1099-4300 www.mdpi.com/journal/entropy Editorial Natural/Unconventional Computing and Its Philosophical Significance Gordana Dodig Crnkovic 1,* and Raffaela Giovagnoli 2 1 Department of Computer Science and Networks, School of Innovation, Design and Engineering Mälardalen University, Västerås 721 23, Sweden 2 Department of Philosophy, Lateran University, Vatican City, Rome 00184, Italy; E-Mail: [email protected] * Author to whom correspondence should be addressed; E-Mail: [email protected]; Tel.: +46-21-15-17-25. Received: 31 October 2012; in revised form: 21 November 2012 / Accepted: 26 November 2012 / Published: 27 November 2012 Abstract: In this special issue we present a selection of papers from the Symposium on Natural/Unconventional Computing and its Philosophical Significance, held during the AISB/IACAP 2012 World Congress in Birmingham (UK). This article is an editorial, introducing the special issue of the journal with the selected papers and the research program of Natural/Unconventional Computing. Keywords: natural computing; unconventional computing; computation beyond the Turing limit; unconventional models of computation 1. Introduction The AISB/IACAP 2012 World Congress combined the British Society for the Study of Artificial Intelligence and the Simulation of Behaviour (AISB) convention and the International Association for Computing and Philosophy (IACAP) conference honoring Alan Turing’s essential impact on the theory of computation, AI and philosophy of computing. The Congress was one of the events of the Alan Turing Year. Even though Turing is best known for his Logical Machine (the Turing machine) and the Turing test of a machine's ability to exhibit intelligent behavior, his contribution to the foundations of Entropy 2012, 14 2409 computation is significantly broader in scope. -
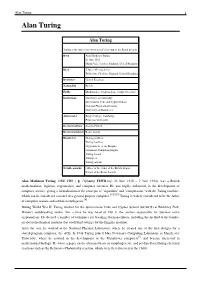
Alan Turing 1 Alan Turing
Alan Turing 1 Alan Turing Alan Turing Turing at the time of his election to Fellowship of the Royal Society. Born Alan Mathison Turing 23 June 1912 Maida Vale, London, England, United Kingdom Died 7 June 1954 (aged 41) Wilmslow, Cheshire, England, United Kingdom Residence United Kingdom Nationality British Fields Mathematics, Cryptanalysis, Computer science Institutions University of Cambridge Government Code and Cypher School National Physical Laboratory University of Manchester Alma mater King's College, Cambridge Princeton University Doctoral advisor Alonzo Church Doctoral students Robin Gandy Known for Halting problem Turing machine Cryptanalysis of the Enigma Automatic Computing Engine Turing Award Turing test Turing patterns Notable awards Officer of the Order of the British Empire Fellow of the Royal Society Alan Mathison Turing, OBE, FRS ( /ˈtjʊərɪŋ/ TEWR-ing; 23 June 1912 – 7 June 1954), was a British mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, giving a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which can be considered a model of a general purpose computer.[1][2][3] Turing is widely considered to be the father of computer science and artificial intelligence.[4] During World War II, Turing worked for the Government Code and Cypher School (GC&CS) at Bletchley Park, Britain's codebreaking centre. For a time he was head of Hut 8, the section responsible for German naval cryptanalysis. He devised a number of techniques for breaking German ciphers, including the method of the bombe, an electromechanical machine that could find settings for the Enigma machine. -

Breaking Enigma Samantha Briasco-Stewart, Kathryn Hendrickson, and Jeremy Wright
Breaking Enigma Samantha Briasco-Stewart, Kathryn Hendrickson, and Jeremy Wright 1 Introduction 2 2 The Enigma Machine 2 2.1 Encryption and Decryption Process 3 2.2 Enigma Weaknesses 4 2.2.1 Encrypting the Key Twice 4 2.2.2 Cillies 5 2.2.3 The Enigma Machine Itself 5 3 Zygalski Sheets 6 3.1 Using Zygalski Sheets 6 3.2 Programmatic Replication 7 3.3 Weaknesses/Problems 7 4 The Bombe 8 4.1 The Bombe In Code 10 4.1.1 Making Menus 10 4.1.2 Running Menus through the Bombe 10 4.1.3 Checking Stops 11 4.1.4 Creating Messages 11 4.1.5 Automating the Process 11 5 Conclusion 13 References 14 1 Introduction To keep radio communications secure during World War II, forces on both sides of the war relied on encryption. The main encryption scheme used by the German military for most of World War II employed the use of an Enigma machine. As such, Britain employed a large number of codebreakers and analysts to work towards breaking the Enigma-created codes, using many different methods. In this paper, we lay out information we learned while researching these methods, as well as describe our attempts at programatically recreating two methods: Zygalski sheets and the Bombe. 2 The Enigma Machine The Enigma machine was invented at the end of World War I, by a German engineer named Arthur Scherbius. It was commercially available in the 1920s before being adopted by the German military, among others, around the beginning of World War II. -

Problem Set 4: the Lorenz Cipher and the Postman's Computer 2/11/2007
CS150: Problem Set 4: The Lorenz Cipher and the Postman's Computer Page 1 of 8 University of Virginia, Department of Computer Science cs150: Computer Science — Spring 2007 Out: 12 February 2007 Problem Set 4: Creating Colossi Due: 19 February 2007 (beginning of class) Collaboration Policy - Read Carefully This problem set is intended to help you prepare for Exam 1. You may work on it by yourself or with other students, but you will need to do the exam on your own. Regardless of whether you work alone or with a partner, you are encouraged to discuss this assignment with other students in the class and ask and provide help in useful ways. You may consult any outside resources you wish including books, papers, web sites and people. If you use resources other than the class materials, indicate what you used along with your answer. You have only one week to complete this problem set. We recommend you start early and take advantage of the staffed lab hours . Purpose Get practice with some of the material that will be on Exam 1 including: recursive definitions, procedures, lists, and measuring work. Learn about cryptography and the first problems that were solved by computers. Download: Download ps4.zip to your machine and unzip it into your home directory J:\cs150\ps4 . This file contains: ps4.scm — A template for your answers. You should do the problem set by editing this file. lorenz.scm — Some helpful definitions for this problem set. Background Cryptography means secret writing . The goal of much cryptography is for one person to send a message to another person over a channel that an adversary may be eavesdropping on without the eavesdropper understanding the message. -

Copyrighted Material
k Trim Size: 170mm x 244mm Walker c01.tex V3 - 01/27/2016 3:11 P.M. Page 1 1 Why Graphics Processing Units Perri Needham1, Andreas W. Götz2 and Ross C. Walker1,2 1San Diego Supercomputer Center, UCSD, La Jolla, CA, USA 2Department of Chemistry and Biochemistry, UCSD, La Jolla, CA, USA 1.1 A Historical Perspective of Parallel Computing k The first general-purpose electronic computers capable of storing instructions came into existence in k 1950. That is not to say, however, that the use of computers to solve electronic structure problems had not already been considered, or realized. From as early as 1930 scientists used a less advanced form of computation to solve their quantum mechanical problems, albeit a group of assistants simultaneously working on mechanical calculators but an early parallel computing machine nonetheless [1]. It was clear from the beginning that solutions to electronic structure problems could not be carried forward to many-electron systems without the use of some computational device to lessen the mathematical burden. Today’s computational scientists rely heavily on the use of parallel electronic computers. Parallel electronic computers can be broadly classified as having either multiple processing ele- ments in the same machine (shared memory) or multiple machines coupled together to form a cluster/ grid of processing elements (distributed memory). These arrangements make it possible to perform calculations concurrently across multiple processing elements, enabling large problems to be broken down into smaller parts that can be solved simultaneously (in parallel). The first electronic computers were primarily designed for and funded by military projects to assist in World War II and the start of the Cold War [2].