February 2005 VOLUME 30 NUMBER 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Portace Na Jin´E Os
VYSOKEU´ CENˇ ´I TECHNICKE´ V BRNEˇ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA INFORMACNˇ ´ICH TECHNOLOGI´I USTAV´ INFORMACNˇ ´ICH SYSTEM´ U˚ FACULTY OF INFORMATION TECHNOLOGY DEPARTMENT OF INFORMATION SYSTEMS REDIRFS - PORTACE NA JINE´ OS PORTING OF REDIRFS ON OTHER OS DIPLOMOVA´ PRACE´ MASTER’S THESIS AUTOR PRACE´ Bc. LUKA´ Sˇ CZERNER AUTHOR VEDOUC´I PRACE´ Ing. TOMA´ Sˇ KASPˇ AREK´ SUPERVISOR BRNO 2010 Abstrakt Tato pr´acepopisuje jak pˇr´ıpravu na portaci, tak samotnou portaci Linuxov´ehomodulu RedirFS na operaˇcn´ısyst´emFreeBSD. Jsou zde pops´any z´akladn´ırozd´ılypˇr´ıstupuk Lin- uxov´emu a FreeBSD j´adru,d´alerozd´ılyv implementaci, pro RedirFS z´asadn´ı,ˇc´astij´adra a sice VFS vrstvy. D´alezkoum´amoˇznostia r˚uzn´epˇr´ıstupy k implementaci funkcionality linuxov´ehoRedirFS na operaˇcn´ımsyst´emu FreeBSD. N´aslednˇejsou zhodnoceny moˇznostia navrˇzenide´aln´ıpostup portace. N´asleduj´ıc´ıkapitoly pak popisuj´ıpoˇzadovanou funkcional- itu spolu s navrhovanou architekturou nov´ehomodulu. D´aleje detailnˇepops´ann´avrha implementace nov´ehomodulu tak, aby mˇelˇcten´aˇrjasnou pˇredstavu jak´ymzp˚usobem modul implementuje poˇzadovanou funkcionalitu. Abstract This thesis describes preparation for porting as well aw porting itself of RedirFS Linux kernel module to FreeBSD. Basic differences between Linux and FreeBSD kernels are de- scribed as well as differences in implementation of the Virtual Filesystem, crucial part for RedirFS. Further there are described possibilities and different approaches to implemen- tation RedirFS functionality to FreeBSD. Then, the possibilities are evaluated and ideal approach is proposed. Next chapters introduces erquired functionality of the new module as well as its solutions. Then the implementation details are describet so the reader can very well understand how the new module works and how the required functionality is implemented into the module. -

Introduzione Al Mondo Freebsd
Introduzione al mondo FreeBSD Corso avanzato Netstudent Netstudent http://netstudent.polito.it E.Richiardone [email protected] maggio 2009 CC-by http://creativecommons.org/licenses/by/2.5/it/ The FreeBSD project - 1 ·EÁ un progetto software open in parte finanziato ·Lo scopo eÁ mantenere e sviluppare il sistema operativo FreeBSD ·Nasce su CDROM come FreeBSD 1.0 nel 1993 ·Deriva da un patchkit per 386BSD, eredita codice da UNIX versione Berkeley 1977 ·Per problemi legali subisce un rallentamento, release 2.0 nel 1995 con codice royalty-free ·Dalla release 5.0 (2003) assume la struttura che ha oggi ·Disponibile per x86 32 e 64bit, ia64, MIPS, ppc, sparc... ·La mascotte (Beastie) nasce nel 1984 The FreeBSD project - 2 ·Erede di 4.4BSD (eÁ la stessa gente...) ·Sistema stabile; sviluppo uniforme; codice molto chiaro, ordinato e ben commentato ·Documentazione ufficiale ben curata ·Licenza molto permissiva, spesso attrae aziende per progetti commerciali: ·saltuariamente esterni collaborano con implementazioni ex-novo (i.e. Intel, GEOM, atheros, NDISwrapper, ZFS) ·a volte no (i.e. Windows NT) ·Semplificazione di molte caratteristiche tradizionali UNIX Di cosa si tratta Il progetto FreeBSD include: ·Un sistema base ·Bootloader, kernel, moduli, librerie di base, comandi e utility di base, servizi tradizionali ·Sorgenti completi in /usr/src (~500MB) ·EÁ giaÁ abbastanza completo (i.e. ipfw, ppp, bind, ...) ·Un sistema di gestione per software aggiuntivo ·Ports e packages ·Documentazione, canali di assistenza, strumenti di sviluppo ·i.e. Handbook, -

BSD UNIX Toolbox 1000+ Commands for Freebsd, Openbsd
76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page i BSD UNIX® TOOLBOX 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iv BSD UNIX® Toolbox: 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD® Power Users Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2008 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN: 978-0-470-37603-4 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 Library of Congress Cataloging-in-Publication Data is available from the publisher. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permis- sion should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. -

Ask Bjørn Hansen Develooper LLC
If this text is too small to read, move closer! http://groups.google.com/group/scalable Real World Web: Performance & Scalability Ask Bjørn Hansen Develooper LLC http://develooper.com/talks/ April 14, 2008 – r17 Hello. • I’m Ask Bjørn Hansen perl.org, ~10 years of mod_perl app development, mysql and scalability consulting YellowBot • I hate tutorials! • Let’s do 3 hours of 5 minute° lightning talks! ° Actual number of minutes may vary Construction Ahead! • Conflicting advice ahead • Not everything here is applicable to everything • Ways to “think scalable” rather than be-all-end-all solutions • Don’t prematurely optimize! (just don’t be too stupid with the “we’ll fix it later” stuff) Questions ... • How many ... • ... are using PHP? Python? Python? Java? Ruby? C? • 3.23? 4.0? 4.1? 5.0? 5.1? 6.x? • MyISAM? InnoDB? Other? • Are primarily “programmers” vs “DBAs” • Replication? Cluster? Partitioning? • Enterprise? Community? • PostgreSQL? Oracle? SQL Server? Other? Seen this talk before? Slide count 200 No, you haven’t. • 150 • :-) 100 • ~266 people * 3 hours = half a work year! 50 0 2001 2004 2006 2007 2008 Question Policy! http://groups.google.com/group/scalable • Do we have time for Slides per minute questions? 1.75 • Yes! (probably) • Quick questions anytime • Long questions after 1.00 • or on the list! • (answer to anything is likely “it depends” or “let’s talk about it 0.25 after / send me an email”) 2001 2002 2004 2005 2006 2007 2008 • The first, last and only lesson: • Think Horizontal! • Everything in your architecture, not just the front end web servers • Micro optimizations and other implementation details –– Bzzzzt! Boring! (blah blah blah, we’ll get to the cool stuff in a moment!) Benchmarking techniques • Scalability isn't the same as processing time • Not “how fast” but “how many” • Test “force”, not speed. -

Freesbie - Français
FreeBSD FreeSBIE - Français Surfer anonymement sur la toile avec Tor et Liste de choses à faire (TODO list) pour la Privoxy prochaine édition de FreeSBIE La vie privée n'est pas seulement importante, c'est une né- Les point suivants sont ceux qui n'ont pas été réalisés FreeBSD cessité. Vous ne voulez pas que d'autres personnes ap- dans la présente version. Si une version possédait toutes prennent les adresses des sites que vous allez visiter, d'où les caractéristiques nécessaires aux utilisateurs et celles FreeSBIE LiveCD vous venez, et ainsi de suite. Les mêmes principes s'appli- souhaitées par les programmeurs alors il n'y aurait plus de quent pour les autres services internet : SSH, IRC, etc. nouvelle version. FreeSBIE fournit deux puissants outils pour rendre la 1. Relecture du code - Bien que la boîte à outils de FreeS- Qu'est ce que FreeSBIE ? navigation anonyme et plus sûre: Tor et Privoxy. Vous BIE ait été complètement réécrite au cours de l'été 2004, FreeSBIE est un système d'exploitation complet utilisable pouvez rediriger vos connexions à travers différents il subsiste bon nombre de parties modifiées qui requièrent à partir d'un CD ou d'un DVD. Il est capable de détecter routeurs et obtenir un anonymat presque parfait. Parce un examen minutieux. automatiquement les composants de votre ordinateur et il qu'une telle configuration est loin d'être simple, FreeSBIE 2. Réécriture de BSDinstaller. Cette tâche progresse rap- reconnaît quantité de cartes graphiques, de périphériques vous assiste avec un script : /usr/local/bin/freesbie_tor. En idement. USB et autres matériels. -
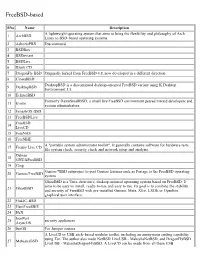
List of BSD Operating Systems
FreeBSD-based SNo Name Description A lightweight operating system that aims to bring the flexibility and philosophy of Arch 1 ArchBSD Linux to BSD-based operating systems. 2 AskoziaPBX Discontinued 3 BSDBox 4 BSDeviant 5 BSDLive 6 Bzerk CD 7 DragonFly BSD Originally forked from FreeBSD 4.8, now developed in a different direction 8 ClosedBSD DesktopBSD is a discontinued desktop-oriented FreeBSD variant using K Desktop 9 DesktopBSD Environment 3.5. 10 EclipseBSD Formerly DamnSmallBSD; a small live FreeBSD environment geared toward developers and 11 Evoke system administrators. 12 FenestrOS BSD 13 FreeBSDLive FreeBSD 14 LiveCD 15 FreeNAS 16 FreeSBIE A "portable system administrator toolkit". It generally contains software for hardware tests, 17 Frenzy Live CD file system check, security check and network setup and analysis. Debian 18 GNU/kFreeBSD 19 Ging Gentoo/*BSD subproject to port Gentoo features such as Portage to the FreeBSD operating 20 Gentoo/FreeBSD system GhostBSD is a Unix-derivative, desktop-oriented operating system based on FreeBSD. It aims to be easy to install, ready-to-use and easy to use. Its goal is to combine the stability 21 GhostBSD and security of FreeBSD with pre-installed Gnome, Mate, Xfce, LXDE or Openbox graphical user interface. 22 GuLIC-BSD 23 HamFreeSBIE 24 HeX IronPort 25 security appliances AsyncOS 26 JunOS For Juniper routers A LiveCD or USB stick-based modular toolkit, including an anonymous surfing capability using Tor. The author also made NetBSD LiveUSB - MaheshaNetBSD, and DragonFlyBSD 27 MaheshaBSD LiveUSB - MaheshaDragonFlyBSD. A LiveCD can be made from all these USB distributions by running the /makeiso script in the root directory. -

Gbruen Knujon Mitspamconf2
The Future of Anti-Spam: A Blueprint for New Internet Abuse Tools Garth Bruen, CEO Knujon.com LLC [email protected] Process and Document Map Abstract I. Introduction II. Failures and Limitations III. KnujOn Principles IV. Data Collection = Consumer Enfranchisement V. Sort, Categorize, Analyze VI. Redefining the Scope VII. Addressing the Support Structure VIII. Fixing Policy and Technology IX. Use the Law When Called For X. Brand Protection XI. The Daily Tally XII. Non-URL Successes XIII. Conclusion: What is Needed Next (Map of the Process and the Document) Abstract: It is this author’s contention that the efforts, technology, funding, and even critical thought in anti-spam development have been incorrectly focused on the email itself. In essence, the Internet security community has been “looking through the wrong end of the telescope.” Resources poured into larger and larger filtering engines and algorithms have failed to reduce the volume and flow of unsolicited email. In fact, spam volumes have generally increased since filtering was declared the de facto solution. The problem is not really about flaws in SMTP (simple mail transfer protocol), or email clients, or even email security in general. Nor is the problem solely attributed to botnets and malware. Garth Bruen and Dr. Robert Bruen have developed a solution that is based on mass abuse data collection, data analysis, policy enforcement, public reporting, and infrastructure enhancement. The ultimate key to solving the spam problem is about blocking transactions, stopping the flow of money to criminals who hire spammers to market their illicit products. Doing this through the existing, but enhanced, policy structure addresses the issue without exaggerated costs or reinventing the Internet. -

Understanding the Business Ofonline Pharmaceutical Affiliate Programs
PharmaLeaks: Understanding the Business of Online Pharmaceutical Affiliate Programs Damon McCoy Andreas Pitsillidis∗ Grant Jordan∗ Nicholas Weaver∗† Christian Kreibich∗† Brian Krebs‡ Geoffrey M. Voelker∗ Stefan Savage∗ Kirill Levchenko∗ Department of Computer Science ∗Department of Computer Science and Engineering George Mason University University of California, San Diego †International Computer Science Institute ‡KrebsOnSecurity.com Berkeley, CA Abstract driven by competition between criminal organizations), a broad corpus of ground truth data has become avail- Online sales of counterfeit or unauthorized products able. In particular, in this paper we analyze the content drive a robust underground advertising industry that in- and implications of low-level databases and transactional cludes email spam, “black hat” search engine optimiza- metadata describing years of activity at the GlavMed, tion, forum abuse and so on. Virtually everyone has en- SpamIt and RX-Promotion pharmaceutical affiliate pro- countered enticements to purchase drugs, prescription- grams. By examining hundreds of thousands of orders, free, from an online “Canadian Pharmacy.” However, comprising a settled revenue totaling over US$170M, even though such sites are clearly economically moti- we are able to provide comprehensive documentation on vated, the shape of the underlying business enterprise three key aspects of underground advertising activity: is not well understood precisely because it is “under- Customers. We provide detailed analysis on the con- ground.” In this paper we exploit a rare opportunity to sumer demand for Internet-advertised counterfeit phar- view three such organizations—the GlavMed, SpamIt maceuticals, covering customer demographics, product and RX-Promotion pharmaceutical affiliate programs— selection (including an examination of drug abuse as a from the inside. -
Berkeley DB from Wikipedia, the Free Encyclopedia
Berkeley DB From Wikipedia, the free encyclopedia Berkeley DB Original author(s) Margo Seltzer and Keith Bostic of Sleepycat Software Developer(s) Sleepycat Software, later Oracle Corporation Initial release 1994 Stable release 6.1 / July 10, 2014 Development status production Written in C Operating system Unix, Linux, Windows, AIX, Sun Solaris, SCO Unix, Mac OS Size ~1244 kB compiled on Windows x86 Type Embedded database License AGPLv3 Website www.oracle.com/us/products/database/berkeley-db /index.html (http://www.oracle.com/us/products/database/berkeley- db/index.html) Berkeley DB (BDB) is a software library that provides a high-performance embedded database for key/value data. Berkeley DB is written in C with API bindings for C++, C#, PHP, Java, Perl, Python, Ruby, Tcl, Smalltalk, and many other programming languages. BDB stores arbitrary key/data pairs as byte arrays, and supports multiple data items for a single key. Berkeley DB is not a relational database.[1] BDB can support thousands of simultaneous threads of control or concurrent processes manipulating databases as large as 256 terabytes,[2] on a wide variety of operating systems including most Unix- like and Windows systems, and real-time operating systems. "Berkeley DB" is also used as the common brand name for three distinct products: Oracle Berkeley DB, Berkeley DB Java Edition, and Berkeley DB XML. These three products all share a common ancestry and are currently under active development at Oracle Corporation. Contents 1 Origin 2 Architecture 3 Editions 4 Programs that use Berkeley DB 5 Licensing 5.1 Sleepycat License 6 References 7 External links Origin Berkeley DB originated at the University of California, Berkeley as part of BSD, Berkeley's version of the Unix operating system. -

What Is Perl
AdvancedAdvanced PerlPerl TechniquesTechniques DayDay 22 Dave Cross Magnum Solutions Ltd [email protected] Schedule 09:45 – Begin 11:15 – Coffee break (15 mins) 13:00 – Lunch (60 mins) 14:00 – Begin 15:30 – Coffee break (15 mins) 17:00 – End FlossUK 24th February 2012 Resources Slides available on-line − http://mag-sol.com/train/public/2012-02/ukuug Also see Slideshare − http://www.slideshare.net/davorg/slideshows Get Satisfaction − http://getsatisfaction.com/magnum FlossUK 24th February 2012 What We Will Cover Modern Core Perl − What's new in Perl 5.10, 5.12 & 5.14 Advanced Testing Database access with DBIx::Class Handling Exceptions FlossUK 24th February 2012 What We Will Cover Profiling and Benchmarking Object oriented programming with Moose MVC Frameworks − Catalyst PSGI and Plack FlossUK 24th February 2012 BenchmarkingBenchmarking && ProfilingProfiling Benchmarking Ensure that your program is fast enough But how fast is fast enough? premature optimization is the root of all evil − Donald Knuth − paraphrasing Tony Hoare Don't optimise until you know what to optimise FlossUK 24th February 2012 Benchmark.pm Standard Perl module for benchmarking Simple usage use Benchmark; my %methods = ( method1 => sub { ... }, method2 => sub { ... }, ); timethese(10_000, \%methods); Times 10,000 iterations of each method FlossUK 24th February 2012 Benchmark.pm Output Benchmark: timing 10000 iterations of method1, method2... method1: 6 wallclock secs \ ( 2.12 usr + 3.47 sys = 5.59 CPU) \ @ 1788.91/s (n=10000) method2: 3 wallclock secs \ ( 0.85 usr + 1.70 sys = 2.55 CPU) \ @ 3921.57/s (n=10000) FlossUK 24th February 2012 Timed Benchmarks Passing timethese a positive number runs each piece of code a certain number of times Passing timethese a negative number runs each piece of code for a certain number of seconds FlossUK 24th February 2012 Timed Benchmarks use Benchmark; my %methods = ( method1 => sub { .. -

Compiling Your Own Perl
APPENDIX A Compiling Your Own Perl Compiling Perl on a Unix-like system is simple. First, obtain the source for Perl from CPAN (dppl6++_l]j*lanh*knc+on_+NA=@IA*dpih). Then input the following sequence of commands: p]nvtrblanh)1*4*4*p]n*cv _`lanh)1*4*4 od?kjbecqna)`ao i]ga i]gapaop oq`ki]gaejop]hh On most Unix systems, this code will result in your lanh being installed into the +qon+ hk_]h+ directory tree. If you want it installed elsewhere—for example, in the local directory in your home directory—then replace od?kjbecqna)`a with the following: od?kjbecqna)`ao)@lnabet9z+hk_]h+ which should enable you to install Perl on your computer without root access. Note that the )`ao flag uses all the default options for compiling Perl. If you know that you want nonstandard configuration, just use the flag )`a instead to be prompted for your requirements. Be aware that the source for Perl 5.10.0 requires a patch to work properly with Catalyst. This is fixed in subsequent versions of Perl 5.10. If you need to test code guaranteed to run on a wide range of systems, you should con- sider using Perl version 5.8.7. Perl versions greater than 5.8.7 contain features that were not available in earlier versions of Perl, so Perl 5.8.7 is feature complete for all versions of Perl that Catalyst will run on (version 5.8.1 and later). Put another way, versions 5.8.8 and later have new features that you can’t rely on in earlier releases. -

Fast Statistical Spam Filter by Approximate Classifications
Fast Statistical Spam Filter by Approximate Classifications Kang Li Zhenyu Zhong Department of Computer Science Department of Computer Science University of Georgia University of Georgia Athens, Georgia, USA Athens, Georgia, USA [email protected] [email protected] ABSTRACT based on its contents, have found wide acceptance in tools Statistical-based Bayesian filters have become a popular and used to block spam. These filters can be continually trained important defense against spam. However, despite their ef- on updated corpora of spam and ham (good email), resulting fectiveness, their greater processing overhead can prevent in robust, adaptive, and highly accurate systems. them from scaling well for enterprise-level mail servers. For Bayesian filters usually perform a dictionary lookup on example, the dictionary lookups that are characteristic of each individual token and summarize the result in order to this approach are limited by the memory access rate, there- arrive at a decision. It is not unusual to accumulate over fore relatively insensitive to increases in CPU speed. We 100,000 tokens in a dictionary, depending on how training is address this scaling issue by proposing an acceleration tech- handled [23]. Unfortunately, the performance of these dic- nique that speeds up Bayesian filters based on approximate tionary lookups is limited by the memory access rate, there- classification. The approximation uses two methods: hash- fore relatively insensitive to increases in CPU speed. As a based lookup and lossy encoding. Lookup approximation is result of this lookup overhead, classification can be relatively based on the popular Bloom filter data structure with an ex- slow.