Everything You Need to Know About Internet Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Symantec Report on Rogue Security Software July 08 – June 09
REPORT: SYMANTEC ENTERPRISE SECURITY SYMANTEC REPORT: Symantec Report on Rogue Security Software July 08 – June 09 Published October 2009 Confidence in a connected world. White Paper: Symantec Enterprise Security Symantec Report on Rogue Security Software July 08 – June 09 Contents Introduction . 1 Overview of Rogue Security Software. 2 Risks . 4 Advertising methods . 7 Installation techniques . 9 Legal actions and noteworthy scam convictions . 14 Prevalence of Rogue Security Software . 17 Top reported rogue security software. 17 Additional noteworthy rogue security software samples . 25 Top rogue security software by region . 28 Top rogue security software installation methods . 29 Top rogue security software advertising methods . 30 Analysis of Rogue Security Software Distribution . 32 Analysis of Rogue Security Software Servers . 36 Appendix A: Protection and Mitigation. 45 Appendix B: Methodologies. 48 Credits . 50 Symantec Report on Rogue Security Software July 08 – June 09 Introduction The Symantec Report on Rogue Security Software is an in-depth analysis of rogue security software programs. This includes an overview of how these programs work and how they affect users, including their risk implications, various distribution methods, and innovative attack vectors. It includes a brief discussion of some of the more noteworthy scams, as well as an analysis of the prevalence of rogue security software globally. It also includes a discussion on a number of servers that Symantec observed hosting these misleading applications. Except where otherwise noted, the period of observation for this report was from July 1, 2008, to June 30, 2009. Symantec has established some of the most comprehensive sources of Internet threat data in the world through the Symantec™ Global Intelligence Network. -

Information Disclosure Mechanism for Technological Protection Measures in China
Journal of Intellectual Property Rights Vol 17, November 2012, pp 532-538 Information Disclosure Mechanism for Technological Protection Measures in China Lili Zhao† Center for China Information Security Law, Xi’an Jiao tong University, Shaanxi Xi’an, P R China 710 049 Received 12 February 2012, revised 21 May 2012 With increasing cases of digital works being copied and pirated, technological protection measures have been greatly favoured by copyright owners for protecting the intellectual property in their digital works, while ensuring that these works can be used and disseminated. However, when any copyright owner or supplier fails to disclose the information of technological protection measures appropriately or effectively, damages such as privacy violations, security breaches and unfair competition may be caused to the public. Therefore, it is necessary to establish an information disclosure mechanism for technological protection measures, make the labeling obligation with regard to technological protection measures by copyright owners apparent and warning to security risks obligatory by legislation; effectively guarding against information security threats from the technological protection measures. Keywords: Technological protection measures, TPM, information disclosure, label and warning The advance of digital technologies make many information security, it is necessary to integrate such acts things become possible, including the copy and in a standardized, normalized and legal manner. dissemination of commercially valuable digital works Therefore, to further prevent copyright owners from through global digital network. Particularly, among using insecure or untested software, protect information the copyright owners of entertainment industry, security and prohibit the abuse of TPMs; disclosure technological protection measures (TPMs) have been obligations should be established for the right holders of regarded as a necessary creation to help digital works TPMs in the form of legislation. -

Adware-Searchsuite
McAfee Labs Threat Advisory Adware-SearchSuite June 22, 2018 McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalent malware. This Threat Advisory contains behavioral information, characteristics and symptoms that may be used to mitigate or discover this threat, and suggestions for mitigation in addition to the coverage provided by the DATs. To receive a notification when a Threat Advisory is published by McAfee Labs, select to receive “Malware and Threat Reports” at the following URL: https://www.mcafee.com/enterprise/en-us/sns/preferences/sns-form.html Summary Detailed information about the threat, its propagation, characteristics and mitigation are in the following sections: Infection and Propagation Vectors Mitigation Characteristics and Symptoms Restart Mechanism McAfee Foundstone Services The Threat Intelligence Library contains the date that the above signatures were most recently updated. Please review the above mentioned Threat Library for the most up to date coverage information. Infection and Propagation Vectors Adware-SearchSuite is a "potentially unwanted program" (PUP). PUPs are any piece of software that a reasonably security- or privacy-minded computer user may want to be informed of and, in some cases, remove. PUPs are often made by a legitimate corporate entity for some beneficial purpose, but they alter the security state of the computer on which they are installed, or the privacy posture of the user of the system, such that most users will want to be aware of them. Mitigation Mitigating the threat at multiple levels like file, registry and URL could be achieved at various layers of McAfee products. Browse the product guidelines available here (click Knowledge Center, and select Product Documentation from the Support Content list) to mitigate the threats based on the behavior described in the Characteristics and symptoms section. -

A Crawler-Based Study of Spyware on the Web
A Crawler-based Study of Spyware on the Web Alexander Moshchuk, Tanya Bragin, Steven D. Gribble, and Henry M. Levy Department of Computer Science & Engineering University of Washington {anm, tbragin, gribble, levy}@cs.washington.edu Abstract servers [16]. The AOL scan mentioned above has provided simple summary statistics by directly examining desktop in- Malicious spyware poses a significant threat to desktop fections [2], while a recent set of papers have considered security and integrity. This paper examines that threat from user knowledge of spyware and its behavior [6, 29]. an Internet perspective. Using a crawler, we performed a In this paper we change perspective, examining the na- large-scale, longitudinal study of the Web, sampling both ture of the spyware threat not on the desktop but from an executables and conventional Web pages for malicious ob- Internet point of view. To do this, we conduct a large-scale jects. Our results show the extent of spyware content. For outward-looking study by crawling the Web, downloading example, in a May 2005 crawl of 18 million URLs, we found content from a large number of sites, and then analyzing it spyware in 13.4% of the 21,200 executables we identified. to determine whether it is malicious. In this way, we can At the same time, we found scripted “drive-by download” answer several important questions. For example: attacks in 5.9% of the Web pages we processed. Our analy- sis quantifies the density of spyware, the types of of threats, • How much spyware is on the Internet? and the most dangerous Web zones in which spyware is • Where is that spyware located (e.g., game sites, chil- likely to be encountered. -

Gedownloade Software
KIJK SOMS UIT MET UPDATEN !!! 2 e CD zie onderaan! GEDOWNLOADE SOFTWARE Ace Utilities 5 TROJAN!!!!!!!! Advanced System Care Pro 3.4.0 Advanced System Optimizer 3.0.6 Any Video Converter 2.7.7 Pro Ashampoo Internet Accelerator 3 Ashampoo Winoptimizer 6.24 Auslogics Boost Speed 4.5.1.4 Clean My PC 4.2.3 Error Repair Pro 4.0.5 Glary Soft Utilities Pro 2.17 Lavasoft Ad-Aware 2009 Pro Limewire Pro 5.1.4 Final Microsoft Windows XP Pro with SP 3 MS Office 2007 PC Washer 2.2.1 Power Video Converter 2.2.15 Ramsaver Raxco Perfect Disk 10 Raxco Perfect Speed PC Optimizer 2.0.0.104 Registry Booster 2010 Registry First Aid Platinum 7.1.1.1 Registry Winner 5.5.9.4 Speedconnect 7.5 Tune-Up 2010 Winzip Pro Final CD 3 PC Optimizer Pro 4.5.44 PC Tools Registry Mechanic 9.0 RamSaver Pro Registry Ace 1.0 Probleem met Patch Registry Clean Expert 4.7.6 Registry Easy 4.6 GOED PROGRAMMA! RegistryFix 7.1 Registry Tidy 2009 Registry Vac 5.0.1.26 UITSTEKEND !!! Serials Grabber 1.1 Softflyers Speed Video Converter Trojan Remover 30 dagen geldig wel update mogelijk! (SCANT ELKE DAG) Ultra Optimizer 2.0.0 UITSTEKEND!!! Ultra Video Converter 44.0827 Uniblue Driver Scanner 2009 (hoort bij Powersuite) Uniblue Registry Booster 2010 versie 4.5.0.17 Uniblue Speed Up My PC! Versie 3.5 Very PDF to Word Converter versie 3jkkkjk Webroot Windows Washer 6.5.5.155 RETAILVERSION!!! Wintools Pro 10.0.1 Winutilities 9.1 YL Computing Winutilities Wise Registry Cleaner Pro 4.83 YL Computing Winutilities 9.1 XP Antispy CD 4 1 Million Serial Keys Advanced System Care Pro 3.2.0 Any Video -

Comodo Cloud Scanner User Guide
Comodo Cloud Scanner Software Version 2.0 User Guide Guide Version 2.0.092611 Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Comodo Cloud Scanner - User Guide Table of Contents 1.Comodo Cloud Scanner - Introduction.................................................................................................................................... 3 1.1.System Requirements ........................................................................................................................................................ 4 1.2.Installing Comodo Cloud Scanner....................................................................................................................................... 5 1.3.Starting Comodo Cloud Scanner......................................................................................................................................... 9 1.4.The Main Interface.............................................................................................................................................................. 9 2.Scanning Your System............................................................................................................................................................ 11 2.1.Summary of the Scanning Process................................................................................................................................... 11 2.2.Scanning Full System....................................................................................................................................................... -
ABBREVIATIONS EBU Technical Review
ABBREVIATIONS EBU Technical Review AbbreviationsLast updated: January 2012 720i 720 lines, interlaced scan ACATS Advisory Committee on Advanced Television 720p/50 High-definition progressively-scanned TV format Systems (USA) of 1280 x 720 pixels at 50 frames per second ACELP (MPEG-4) A Code-Excited Linear Prediction 1080i/25 High-definition interlaced TV format of ACK ACKnowledgement 1920 x 1080 pixels at 25 frames per second, i.e. ACLR Adjacent Channel Leakage Ratio 50 fields (half frames) every second ACM Adaptive Coding and Modulation 1080p/25 High-definition progressively-scanned TV format ACS Adjacent Channel Selectivity of 1920 x 1080 pixels at 25 frames per second ACT Association of Commercial Television in 1080p/50 High-definition progressively-scanned TV format Europe of 1920 x 1080 pixels at 50 frames per second http://www.acte.be 1080p/60 High-definition progressively-scanned TV format ACTS Advanced Communications Technologies and of 1920 x 1080 pixels at 60 frames per second Services AD Analogue-to-Digital AD Anno Domini (after the birth of Jesus of Nazareth) 21CN BT’s 21st Century Network AD Approved Document 2k COFDM transmission mode with around 2000 AD Audio Description carriers ADC Analogue-to-Digital Converter 3DTV 3-Dimension Television ADIP ADress In Pre-groove 3G 3rd Generation mobile communications ADM (ATM) Add/Drop Multiplexer 4G 4th Generation mobile communications ADPCM Adaptive Differential Pulse Code Modulation 3GPP 3rd Generation Partnership Project ADR Automatic Dialogue Replacement 3GPP2 3rd Generation Partnership -

Intellectual Property Part 2 Pornography
Intellectual Property Part 2 Pornography By Jeremy Parmenter What is pornography Pornography is the explicit portrayal of sexual subject matter Can be found as books, magazines, videos The web has images, tube sites, and pay sites scattered with porn Statistics 12% of total websites are pornography websites 25% of total daily search engine requests are pornographic requests 42.7% of internet users who view pornography 34% internet users receive unwanted exposure to sexual material $4.9 billion in internet pornography sales 11 years old is the average age of first internet exposure to pornography Innovations ● Richard Gordon created an e-commerce start up in mid- 90s that was used on many sites, most notably selling Pamela Anderson/Tommey Lee sex tape ● Danni Ashe founded Danni's Hard Drive with one of the first streaming video without requiring a plug-in ● Adult content sites were one of the first to use traffic optimization by linking to similar sites ● Live chat during the early days of the web ● Pornographic companies were known to give away broadband devices to promote faster connections Negative Impacts ● Between 2001-2002 adult-oriented spam rose 450% ● Malware such as Trojans and video codecs occur most often on porn sites ● Domain hijacking, using fake documents and information to steal a site ● Pop-ups preventing users from leaving the site or infecting their computer ● Browser hijacking adware or spyware manipulating the browser to change home page or search engine to a bogus site, including pay-per-click adult site ● Accessibility -

December 8.2006 Ari Schwartz Alissa Cooper Center for Democracy
CORR CRONIN MICHELSON BAUMGARDNER & PREECE LLP PAUL R. RASKIN Attorney at Law December 8.2006 Via Facsimile to (202) 637-0968 and First Class Mail Ari Schwartz Alissa Cooper Center For Democracy & Technology 634 Eve Street N W # 1 100 Washington DC, 20006 Re: Sol'twireOnli~ie.coni Dear Mr. Scliwariz and Ms. Cooper We represent SoftwareOt~liiie.com.We write to bring to your attention misleading characterizations of certain litigation published on the Center For Democracy & Technology's website. The litigation is State of Washington v. Software0nline.com. It is discussed on the "Spyware Enforcement - State" portion of your website under the "Consumer Privacy" Section (located at: http://~v~vw.cdt.or.~privacy/sp~are/20060626spvware-e1iSorcciiici~t-state.pl~p).Your website's niiscategorization of this matter as a "spyware case" and "spyware enforcement" creates the potential for serious damage to SoftwareOnli~ie.coi~i'sbrand, goodwill. and business prospects. SoftwarcOnl~nevoluntarily settled Consumer Protection Act claims brought by the Washington Attorney General's Office on April 1 1, 2006 The complaint filed by the State of Washington against Sott\\areO~iIinecon1 and the judgment voluntarily entered by S~ft~~~~~reOiiIiiiecoiii clo not co11ta111 cla~nisunder anti-spyware statiites or laws If yoii go to the Washington Stale Attorney General's website (located at ww w.atr.wa.yov) and type the word 'spyware" in the sciirchbox, you will not find any references to Sof'twarcOnlinc corn Further. if you search through press releases on the WSAG website, you will see that the Attorney General reports the Secure Computer action filed on January 25, 2006 as the "first lawsuit under the btate-s new conipiitcr sppvarc act" (m hup ww 'ity \\ '1 ~ov/ielcases/2006!rcl Spyware Lawsuit 0 12506 html) and the Movie Land Art Schwart7 Al issa Cooper December 8. -
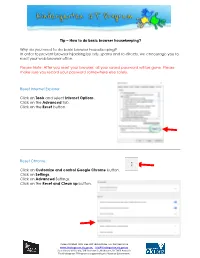
Tip – How to Do Basic Browser Housekeeping?
Tip – How to do basic browser housekeeping? Why do you need to do basic browser housekeeping? In order to prevent browser hijacking by ads, spams and re-directs, we encourage you to reset your web browser often. Please Note: After you reset your browser, all your saved password will be gone. Please make sure you record your password somewhere else safely. _______________________________________________________________________________________ Reset Internet Explorer Click on Tools and select Internet Options . Click on the Advanced tab. Click on the Reset button. _______________________________________________________________________________________ Reset Chrome Click on Customize and control Google Chrome button. Click on Settings . Click on Advanced Settings. Click on the Reset and Clean up button. Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Firefox In the address bar of the FireFox type in about:support and hit Enter. Click Refresh Firefox… button. A window will appear showing the details of this action. Click Refresh Firefox button. _______________________________________________________________________________________ Clear website data in Safari Click on Safari tab and select Preferences… Click Privacy tab. Click Manage Website Data… Click on Remove All . Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Edge Click on Settings and More button. -

COVID-19 Updates and Resources for Local Governments G Tuesday, March 23, 2021 Welcome Greeting
COVID-19 Updates and Resources for Local Governments g Tuesday, March 23, 2021 Welcome Greeting Kayla Rosen Departmental Analyst, Community Engagement and Finance, Department of Treasury 2 Tools and Resources for Local Governments: 11th Webinar Tuesday, March 23, 2021 – 2 p.m. – 3 p.m. I. Welcome & Introductions Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury I. Treasury Update a. CARES Act Grant b. FDCVT Grant c. Overviews of Recreational Marijuana Payments d. American Rescue Plan Eric Bussis, Chief Economist and Director of the Office of Revenue and Tax Analysis, Michigan Department of Treasury I. Cybersecurity for Local Governments Derek Larson, Acting Deputy Chief Security Officer, Department of Technology, Management and Budget (DTMB) I. Question and Answer II. Closing Remarks Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury 3 Welcome & Introductions Heather Frick Bureau Director, Bureau of Local Government and School Services, Department of Treasury 4 Treasury Local Government Funding Update Eric Bussis Chief Economist and Director Office of Revenue and Tax Analysis Michigan Department of Treasury 5 Treasury Update • CARES Act Grant • FDCVT Grant Agenda • Overviews of Recreational Marijuana Payments • American Rescue Plan 6 First Responder Hazard Pay Premiums Program (FRHPPP) • Payments made to 740 applicants, supporting approximately 37,500 first responders • 97 applications were selected for further federal -

The Emergence of Exploit-As-A-Service
Manufacturing Compromise: The Emergence of Exploit-as-a-Service Chris Grier† Lucas Ballard2 Juan Caballerox Neha Chachra∗ Christian J. Dietrichq Kirill Levchenko∗ Panayiotis Mavrommatis2 Damon McCoyz Antonio Nappax Andreas Pitsillidis∗ Niels Provos2 M. Zubair Rafiquex Moheeb Abu Rajab2 Christian Rossowq Kurt Thomasy Vern Paxson† Stefan Savage∗ Geoffrey M. Voelker∗ y University of California, Berkeley ∗ University of California, San Diego 2 Google International Computer Science Institute x IMDEA Software Institute q University of Applied Sciences Gelsenkirchen z George Mason University ABSTRACT 1. INTRODUCTION We investigate the emergence of the exploit-as-a-service model for In this work we investigate the emergence of a new paradigm: the driveby browser compromise. In this regime, attackers pay for an exploit-as-a-service economy that surrounds browser compromise. exploit kit or service to do the “dirty work” of exploiting a vic- This model follows in the footsteps of a dramatic evolution in the tim’s browser, decoupling the complexities of browser and plugin world of for-profit malware over the last five years, where host com- vulnerabilities from the challenges of generating traffic to a web- promise is now decoupled from host monetization. Specifically, the site under the attacker’s control. Upon a successful exploit, these means by which a host initially falls under an attacker’s control are kits load and execute a binary provided by the attacker, effectively now independent of the means by which an(other) attacker abuses transferring control of a victim’s machine to the attacker. the host in order to realize a profit. This shift in behavior is exem- In order to understand the impact of the exploit-as-a-service plified by the pay-per-install model of malware distribution, where paradigm on the malware ecosystem, we perform a detailed anal- miscreants pay for compromised hosts via the underground econ- ysis of the prevalence of exploit kits, the families of malware in- omy [4, 41].