PSUP Uncorrected Proofs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Derogatory Discourses of Veganism and the Reproduction of Speciesism in UK 1 National Newspapers Bjos 1348 134..152
The British Journal of Sociology 2011 Volume 62 Issue 1 Vegaphobia: derogatory discourses of veganism and the reproduction of speciesism in UK 1 national newspapers bjos_1348 134..152 Matthew Cole and Karen Morgan Abstract This paper critically examines discourses of veganism in UK national newspapers in 2007. In setting parameters for what can and cannot easily be discussed, domi- nant discourses also help frame understanding. Discourses relating to veganism are therefore presented as contravening commonsense, because they fall outside readily understood meat-eating discourses. Newspapers tend to discredit veganism through ridicule, or as being difficult or impossible to maintain in practice. Vegans are variously stereotyped as ascetics, faddists, sentimentalists, or in some cases, hostile extremists. The overall effect is of a derogatory portrayal of vegans and veganism that we interpret as ‘vegaphobia’. We interpret derogatory discourses of veganism in UK national newspapers as evidence of the cultural reproduction of speciesism, through which veganism is dissociated from its connection with debates concerning nonhuman animals’ rights or liberation. This is problematic in three, interrelated, respects. First, it empirically misrepresents the experience of veganism, and thereby marginalizes vegans. Second, it perpetuates a moral injury to omnivorous readers who are not presented with the opportunity to understand veganism and the challenge to speciesism that it contains. Third, and most seri- ously, it obscures and thereby reproduces -

Palmer Primary Source Analysis
Palmer’s Case Against “Red” 1920 ! Primary Source Analysis Image Analysis Point of View Writing Prompt Copyright Stephanie’s History Store Brief Background! In 1919 and 1920, Attorney General Palmer led a crusade against Americans believed to be “leftist,” “anarchists,” and threats to the general safety of democratic America. His plan was to arrest and deport those threats to America. The Department of Labor thwarted many of Palmer’s deportations attempt because deportation was under its jurisdiction and the Department objected to Palmer’s methods. These Palmer Raids were one aspect of the Red Scare, the fear of, and reaction to, political radicals in America. With the Russian Revolution making !news, for many people this Red Scare became more of a reality. A fear was that the Russian Revolution would bleed into America via Russian immigrants and other immigrants sympathetic to the Russian cause. People were targeted by Palmer both fairly and unfairly. A person could denounce his or her neighbor and proof of radical activities was not necessary for the arrest to happen. Below is a speech given by Palmer regarding his crusade against “Red.” In two years hundreds of individuals were deported, multiple thousands were arrested, and more than a few were unfortunately innocent of being !anarchists, communists, or leftists. Attorney General Palmer’s Case! Against the “Reds,” 1920 In this brief review of the work which the Department of Justice has undertaken, to tear out the radical seeds that have entangled American ideas in their poisonous theories, I desire not merely to explain what the real menace of communism is, but also to tell how we have been compelled to clean up the country almost unaided by !any virile legislation. -

When Fear Is Substituted for Reason: European and Western Government Policies Regarding National Security 1789-1919
WHEN FEAR IS SUBSTITUTED FOR REASON: EUROPEAN AND WESTERN GOVERNMENT POLICIES REGARDING NATIONAL SECURITY 1789-1919 Norma Lisa Flores A Dissertation Submitted to the Graduate College of Bowling Green State University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY December 2012 Committee: Dr. Beth Griech-Polelle, Advisor Dr. Mark Simon Graduate Faculty Representative Dr. Michael Brooks Dr. Geoff Howes Dr. Michael Jakobson © 2012 Norma Lisa Flores All Rights Reserved iii ABSTRACT Dr. Beth Griech-Polelle, Advisor Although the twentieth century is perceived as the era of international wars and revolutions, the basis of these proceedings are actually rooted in the events of the nineteenth century. When anything that challenged the authority of the state – concepts based on enlightenment, immigration, or socialism – were deemed to be a threat to the status quo and immediately eliminated by way of legal restrictions. Once the façade of the Old World was completely severed following the Great War, nations in Europe and throughout the West started to revive various nineteenth century laws in an attempt to suppress the outbreak of radicalism that preceded the 1919 revolutions. What this dissertation offers is an extended understanding of how nineteenth century government policies toward radicalism fostered an environment of increased national security during Germany’s 1919 Spartacist Uprising and the 1919/1920 Palmer Raids in the United States. Using the French Revolution as a starting point, this study allows the reader the opportunity to put events like the 1848 revolutions, the rise of the First and Second Internationals, political fallouts, nineteenth century imperialism, nativism, Social Darwinism, and movements for self-government into a broader historical context. -

Animal Rights Is a Social Justice Issue
WellBeing International WBI Studies Repository 2015 Animal Rights is a Social Justice Issue Robert C. Jones California State University, Chico, [email protected] Follow this and additional works at: https://www.wellbeingintlstudiesrepository.org/anirmov Part of the Animal Studies Commons, Civic and Community Engagement Commons, and the Politics and Social Change Commons Recommended Citation Jones, R. C. (2015). Animal rights is a social justice issue. Contemporary Justice Review, 18(4), 467-482. This material is brought to you for free and open access by WellBeing International. It has been accepted for inclusion by an authorized administrator of the WBI Studies Repository. For more information, please contact [email protected]. Animal Rights is a Social Justice Issue Robert C. Jones California State University – Chico KEYWORDS animal rights, animal liberation, animal ethics, sentience, social justice, factory farming, industrialized agriculture ABSTRACT The literature on social justice, and social justice movements themselves, routinely ignore nonhuman animals as legitimate subjects of social justice. Yet, as with other social justice movements, the contemporary animal liberation movement has as its focus the elimination of institutional and systemic domination and oppression. In this paper, I explicate the philosophical and theoretical foundations of the contemporary animal rights movement, and situate it within the framework of social justice. I argue that those committed to social justice – to minimizing violence, exploitation, domination, objectification, and oppression – are equally obligated to consider the interests of all sentient beings, not only those of human beings. Introduction I start this essay with a discouraging observation: despite the fact that the modern animal1 rights movement is now over 40 years old, the ubiquitous domination and oppression experienced by other- than-human animals has yet to gain robust inclusion in social justice theory or practice. -

Animals Liberation Philosophy and Policy Journal Volume 5, Issue 1
AAnniimmaallss LLiibbeerraattiioonn PPhhiilloossoopphhyy aanndd PPoolliiccyy JJoouurrnnaall VVoolluummee 55,, IIssssuuee 11 -- 22000077 Animal Liberation Philosophy and Policy Journal Volume 5, Issue 1 2007 Edited By: Steven Best, Chief Editor ____________________________________________________________ TABLE OF CONTENTS Introduction Steven Best, Chief Editor Pg. 2-3 Introducing Critical Animal Studies Steven Best, Anthony J. Nocella II, Richard Kahn, Carol Gigliotti, and Lisa Kemmerer Pg. 4-5 Extrinsic and Intrinsic Arguments: Strategies for Promoting Animal Rights Katherine Perlo Pg. 6-19 Animal Rights Law: Fundamentalism versus Pragmatism David Sztybel Pg. 20-54 Unmasking the Animal Liberation Front Using Critical Pedagogy: Seeing the ALF for Who They Really Are Anthony J. Nocella II Pg. 55-64 The Animal Enterprise Terrorism Act: New, Improved, and ACLU-Approved Steven Best Pg. 65-81 BOOK REVIEWS _________________ In Defense of Animals: The Second Wave, by Peter Singer ed. (2005) Reviewed by Matthew Calarco Pg. 82-87 Dominion: The Power of Man, the Suffering of Animals, and the Call to Mercy, by Matthew Scully (2003) Reviewed by Lisa Kemmerer Pg. 88-91 Terrorists or Freedom Fighters?: Reflections on the Liberation of Animals, by Steven Best and Anthony J. Nocella, II, eds. (2004) Reviewed by Lauren E. Eastwood Pg. 92 Introduction Welcome to the sixth issue of our journal. You’ll first notice that our journal and site has undergone a name change. The Center on Animal Liberation Affairs is now the Institute for Critical Animal Studies, and the Animal Liberation Philosophy and Policy Journal is now the Journal for Critical Animal Studies. The name changes, decided through discussion among our board members, were prompted by both philosophical and pragmatic motivations. -

The Moral Standing of Animals: Towards a Psychology of Speciesism
The Moral Standing of Animals: Towards a Psychology of Speciesism Journal of Personality and Social Psychology Lucius Caviola, Jim A.C. Everett, and Nadira S. Faber University of Oxford We introduce and investigate the philosophical concept of ‘speciesism’ — the assignment of different moral worth based on species membership — as a psychological construct. In five studies, using both general population samples online and student samples, we show that speciesism is a measurable, stable construct with high interpersonal differences, that goes along with a cluster of other forms of prejudice, and is able to predict real-world decision- making and behavior. In Study 1 we present the development and empirical validation of a theoretically driven Speciesism Scale, which captures individual differences in speciesist attitudes. In Study 2, we show high test-retest reliability of the scale over a period of four weeks, suggesting that speciesism is stable over time. In Study 3, we present positive correlations between speciesism and prejudicial attitudes such as racism, sexism, homophobia, along with ideological constructs associated with prejudice such as social dominance orientation, system justification, and right-wing authoritarianism. These results suggest that similar mechanisms might underlie both speciesism and other well-researched forms of prejudice. Finally, in Studies 4 and 5, we demonstrate that speciesism is able to predict prosociality towards animals (both in the context of charitable donations and time investment) and behavioral food choices above and beyond existing related constructs. Importantly, our studies show that people morally value individuals of certain species less than others even when beliefs about intelligence and sentience are accounted for. -

The Life and Times of Emma Goldman: a Curriculum for Middle and High School Students
DOCUMENT RESUME ED 356 998 SO 023 057 AUTHOR Falk, Candace; And Others TITLE The Life and Times of Emma Goldman: A Curriculum for Middle and High School Students. Primary Historical Documents on: Immigration, Freedom of Expression, Women's Rights, Anti-Militarism, Art and Literature of Social Change. INSTITUTION California Univ., Berkeley. Emma Goldman Papers Project.; Los Angeles Educational Partnership, CA.; New Directions Curriculum Developers, Berkeley, CA. REPORT NO ISBN-0-9635443-0-6 PUB DATE 92 NOTE 139p.; Materials reproduced from other sources will not reproduce well. AVAILABLE FROMEmma Goldman Papers Project, University of California, 2372 Ellsworth Street, Berkeley, CA 94720 ($13, plus $3 shipping). PCB TYPE Guides Classroom Use Teaching Guides (For Teacher) (052) EDRS PRICE MF01/PC06 Plus Postage. DESCRIPTORS *Females; Feminism; Freedom of Speech; Higher Education; High Schools; Hig ,School Students; *Humanities Instruction; Intermediate Grades; Junior High Schools; Labor; Middle Schools; Primary Sources; *Social Studies; *United States History; Units of Study IDENTIFIERS *Goldman (Emma); Middle School Students ABSTRACT The documents in this curriculum unit are drawn from the massive archive collected by the Emma Goldman Papers Project at the University of California (Berkeley). They are linked to the standard social studies and humanities curriculum themes of art and literature, First Amendment rights, labor, progressive politics, and Red Scare, the rise of industrialization, immigration, women's rights, World War I, and -

Beyond Reductionism: Reconsidering the Right to Privacy
BEYOND REDUCTIONISM: RECONSIDERING THE RIGHT TO PRIVACY Amy L. Peikoff∗ INTRODUCTION ........................................................................................2 I. A SKETCH OF RAND’S VALIDATION OF INDIVIDUAL RIGHTS...............................................................................................5 II. THE RIGHT TO PROPERTY AS FUNDAMENTAL................................14 III. SHOULD THERE BE A LEGAL RIGHT TO PRIVACY? ........................20 A. Any Law Protecting a Right to Privacy Would be Non-Objective, and Thus Unjust. ..........................................20 B. Laws Directed Specifically at Invasions of Privacy Tend, in Their Application and Proliferation, to Erode Fundamental Rights to Liberty and Property ....................................................................24 ∗ Assistant Professor of Philosophy, United States Air Force Academy, J.D., Univer- sity of California Los Angeles School of Law, Ph.D. in Philosophy, University of Southern California. Thank you to S.A. Lloyd, Tara Smith and participants in the Anthem Foundation Workshop at the University of Texas at Austin, Philosophy Department, Spring 2004, for comments on earlier drafts of this piece. 1 2 N.Y.U. Journal of Law & Liberty [Vol. 3:1 1. “Decisional” Privacy – Roe v. Wade and its progeny.......................................................................................... 26 2 “Informational” Privacy Cases: Eroding the Right to Property .......................................................................... 34 IV. RECOMMENDATION....................................................................... -

Karaoke Mietsystem Songlist
Karaoke Mietsystem Songlist Ein Karaokesystem der Firma Showtronic Solutions AG in Zusammenarbeit mit Karafun. Karaoke-Katalog Update vom: 13/10/2020 Singen Sie online auf www.karafun.de Gesamter Katalog TOP 50 Shallow - A Star is Born Take Me Home, Country Roads - John Denver Skandal im Sperrbezirk - Spider Murphy Gang Griechischer Wein - Udo Jürgens Verdammt, Ich Lieb' Dich - Matthias Reim Dancing Queen - ABBA Dance Monkey - Tones and I Breaking Free - High School Musical In The Ghetto - Elvis Presley Angels - Robbie Williams Hulapalu - Andreas Gabalier Someone Like You - Adele 99 Luftballons - Nena Tage wie diese - Die Toten Hosen Ring of Fire - Johnny Cash Lemon Tree - Fool's Garden Ohne Dich (schlaf' ich heut' nacht nicht ein) - You Are the Reason - Calum Scott Perfect - Ed Sheeran Münchener Freiheit Stand by Me - Ben E. King Im Wagen Vor Mir - Henry Valentino And Uschi Let It Go - Idina Menzel Can You Feel The Love Tonight - The Lion King Atemlos durch die Nacht - Helene Fischer Roller - Apache 207 Someone You Loved - Lewis Capaldi I Want It That Way - Backstreet Boys Über Sieben Brücken Musst Du Gehn - Peter Maffay Summer Of '69 - Bryan Adams Cordula grün - Die Draufgänger Tequila - The Champs ...Baby One More Time - Britney Spears All of Me - John Legend Barbie Girl - Aqua Chasing Cars - Snow Patrol My Way - Frank Sinatra Hallelujah - Alexandra Burke Aber Bitte Mit Sahne - Udo Jürgens Bohemian Rhapsody - Queen Wannabe - Spice Girls Schrei nach Liebe - Die Ärzte Can't Help Falling In Love - Elvis Presley Country Roads - Hermes House Band Westerland - Die Ärzte Warum hast du nicht nein gesagt - Roland Kaiser Ich war noch niemals in New York - Ich War Noch Marmor, Stein Und Eisen Bricht - Drafi Deutscher Zombie - The Cranberries Niemals In New York Ich wollte nie erwachsen sein (Nessajas Lied) - Don't Stop Believing - Journey EXPLICIT Kann Texte enthalten, die nicht für Kinder und Jugendliche geeignet sind. -

And Transhumanism Robert Ranisch & Stefan Lorenz Sorgner Scientific and Technological Advances Have Questioned Predominant Doctrines Concerning the Human Condition
Introducing Post- and Transhumanism Robert Ranisch & Stefan Lorenz Sorgner Scientific and technological advances have questioned predominant doctrines concerning the human condition. Transhumanism and posthumanism are among the most recent and prominent manifestations of this phenomenon. Debates on trans- and posthumanism have not only gained a considerable amount of aca- demic and popular attention recently, but have also created a widespread con- ceptual confusion. This is no surprise, considering their recent dates of origin, their conceptual similarities, and their engagements with similar questions, top- ics, and motifs. Furthermore, trans- as well as posthumanism frequently question their relationship to humanism1 and reconsider what it means to be human. In this regard both movements are streaming beyond humanism. What this means, however, is far from clear and shall be subject of discussion in this volume. In order to make sense of these two approaches and to investigate their inter- relationship, a clarification of these concepts is necessary. As a first approxima- tion, transhumanism can be seen as a stance that affirms the radical transfor- mation of human’s biological capacities and social conditions by means of tech- 1 We will not be able to address the complex histories and varieties of humanism in this chapter. Yet, the following must be noted: The word “humanism” (Humanismus) was coined in 1808 by the German theologian and philosopher Friedrich I. Niethammer in the context of educational curricula, as it is derived from the Latin word humanitas. This word has a variety of meaning but has strongly been identified with the Greek word paideia (παιδεία), e.g., i.) in Cicero’s De Oratore (I, 71) the meaning of the concept hu- manitas corresponds to that of the concept paideia; ii.) in the text Noctes Acticae (XIII, 17) by the Latin author Aulus Gellius, who lived in the 2nd century, an explicit identifi- cation of paideia and humanitas can be found. -

200306 IMPACT02.Qxd
Volume 9, Number 6, June 2003 Local Activism: Introducing Ayn Rand’s In the Media: Dr. Brook on PBS In May 2002 Dr. Yaron Brook was a panelist on Books Into Texas Schools The McCuistion Program; the topic was “The Israel-Palestine Conflict: Solutions for Peace.” That program re-aired last month, at various The Houston Objectivism Society (HOS), an At one school she suggested that her times, on PBS and cable channels throughout independent community group that promotes the department obtain copies of Anthem and Ayn the country. study of Ayn Rand’s philosophy, has long Rand’s play Night of January 16th. As a result, supported ARI’s projects. For several years a fellow teacher is using them in class, “because . and on Fox News Channel HOS has amplified the effect of our high school she saw them on the shelves, and she remem- On April 27 Dr. Brook was interviewed on the essay contest on Anthem and The Fountainhead bered me telling her how much my students Fox News Channel show At Large With by sponsoring prizes for contest winners in the enjoyed the books,” said Ms. Wich. Geraldo. He discussed the dangers of an Houston area. Since 1995 the members of HOS Iranian-backed attempt to install an Islamic have given more than $18,000 in scholarship Books Quickly Win Fans Among Students theocracy in post-war Iraq. money to local winners. The overwhelming response to Though the efforts of HOS Anthem and The Fountainhead, . and on C-SPAN have helped to encourage teachers she continued, “was extremely In April Dr. -
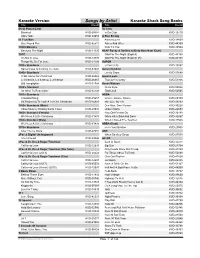
Karaoke Version Song Book
Karaoke Version Songs by Artist Karaoke Shack Song Books Title DiscID Title DiscID (Hed) Planet Earth 50 Cent Blackout KVD-29484 In Da Club KVD-12410 Other Side KVD-29955 A Fine Frenzy £1 Fish Man Almost Lover KVD-19809 One Pound Fish KVD-42513 Ashes And Wine KVD-44399 10000 Maniacs Near To You KVD-38544 Because The Night KVD-11395 A$AP Rocky & Skrillex & Birdy Nam Nam (Duet) 10CC Wild For The Night (Explicit) KVD-43188 I'm Not In Love KVD-13798 Wild For The Night (Explicit) (R) KVD-43188 Things We Do For Love KVD-31793 AaRON 1930s Standards U-Turn (Lili) KVD-13097 Santa Claus Is Coming To Town KVD-41041 Aaron Goodvin 1940s Standards Lonely Drum KVD-53640 I'll Be Home For Christmas KVD-26862 Aaron Lewis Let It Snow, Let It Snow, Let It Snow KVD-26867 That Ain't Country KVD-51936 Old Lamplighter KVD-32784 Aaron Watson 1950's Standard Outta Style KVD-55022 An Affair To Remember KVD-34148 That Look KVD-50535 1950s Standards ABBA Crawdad Song KVD-25657 Gimme Gimme Gimme KVD-09159 It's Beginning To Look A Lot Like Christmas KVD-24881 My Love, My Life KVD-39233 1950s Standards (Male) One Man, One Woman KVD-39228 I Saw Mommy Kissing Santa Claus KVD-29934 Under Attack KVD-20693 1960s Standard (Female) Way Old Friends Do KVD-32498 We Need A Little Christmas KVD-31474 When All Is Said And Done KVD-30097 1960s Standard (Male) When I Kissed The Teacher KVD-17525 We Need A Little Christmas KVD-31475 ABBA (Duet) 1970s Standards He Is Your Brother KVD-20508 After You've Gone KVD-27684 ABC 2Pac & Digital Underground When Smokey Sings KVD-27958 I Get Around KVD-29046 AC-DC 2Pac & Dr.