Platform Architecture Report
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Unisys 2001 Annual Report
Services and Technology: Helping You Create Business Value. Unisys Unisys Corporation 2001 Annual Report Unisys Unisys is a worldwide information technology ser- vices and solutions company whose 39,000 people Contents help clients in more than 100 countries utilize tech- Letter to Stakeholders 1 nology to seize opportunities, overcome challenges Chairman, President and CEO Larry Weinbach reviews 2001 and succeed in the global economy. and outlines the Unisys strategy for 2002. Chairman’s Q&A 3 Larry Weinbach answers operational questions. Our company offers a rich portfolio of business Our Work: Services and Technology 4 solutions led by our expertise in consulting and What we do. Our Success: Unisys Customers 6 systems integration, outsourcing, network services Who we do it for. and security, coupled with leading enterprise-class Our Strength: Unisys People 11 Who we are. server and related technologies. Primary vertical Our Premise: Educating 12 for Leadership markets for Unisys worldwide are the financial How we innovate. Financial Review 13 services, transportation, communications, media, Corporate Officers 47 commercial and public sectors, including U.S. Board of Directors 48 federal government customers. Investor Information 49 Unisys is headquartered in Blue Bell, Pennsylvania, in the Greater Philadelphia area. For more informa- tion on the company, access the Unisys home page on the World Wide Web at www.unisys.com. Investor information can be found at www.unisys.com/investor. About our cover Unisys provides the solution to the puzzle of how organizations can use technology to create business value. Our cover graphically represents what we do and shows how we intertwine our expertise in the service areas of outsourcing, network services and systems integration, as well as in technology. -

Emerging Technologies Multi/Parallel Processing
Emerging Technologies Multi/Parallel Processing Mary C. Kulas New Computing Structures Strategic Relations Group December 1987 For Internal Use Only Copyright @ 1987 by Digital Equipment Corporation. Printed in U.S.A. The information contained herein is confidential and proprietary. It is the property of Digital Equipment Corporation and shall not be reproduced or' copied in whole or in part without written permission. This is an unpublished work protected under the Federal copyright laws. The following are trademarks of Digital Equipment Corporation, Maynard, MA 01754. DECpage LN03 This report was produced by Educational Services with DECpage and the LN03 laser printer. Contents Acknowledgments. 1 Abstract. .. 3 Executive Summary. .. 5 I. Analysis . .. 7 A. The Players . .. 9 1. Number and Status . .. 9 2. Funding. .. 10 3. Strategic Alliances. .. 11 4. Sales. .. 13 a. Revenue/Units Installed . .. 13 h. European Sales. .. 14 B. The Product. .. 15 1. CPUs. .. 15 2. Chip . .. 15 3. Bus. .. 15 4. Vector Processing . .. 16 5. Operating System . .. 16 6. Languages. .. 17 7. Third-Party Applications . .. 18 8. Pricing. .. 18 C. ~BM and Other Major Computer Companies. .. 19 D. Why Success? Why Failure? . .. 21 E. Future Directions. .. 25 II. Company/Product Profiles. .. 27 A. Multi/Parallel Processors . .. 29 1. Alliant . .. 31 2. Astronautics. .. 35 3. Concurrent . .. 37 4. Cydrome. .. 41 5. Eastman Kodak. .. 45 6. Elxsi . .. 47 Contents iii 7. Encore ............... 51 8. Flexible . ... 55 9. Floating Point Systems - M64line ................... 59 10. International Parallel ........................... 61 11. Loral .................................... 63 12. Masscomp ................................. 65 13. Meiko .................................... 67 14. Multiflow. ~ ................................ 69 15. Sequent................................... 71 B. Massively Parallel . 75 1. Ametek.................................... 77 2. Bolt Beranek & Newman Advanced Computers ........... -

Engineering Strategy Overview Preliminary
March 1982 Engineering Preliminary Strategy Company Overview Confidential If.-t8···· L..4L ~ \:')' j.~.! / .;.' ' 1985 1990 1995 2000 - P,O S SIB L E DEC PRO Due T S - $lJOO cellular radio net discontinouous.100 word ~ lim! ted context HANDHELD speaker independent speaker independent $1.0K speech recogn. • sketchpad , interpretation Glata structures , ' & relat~onsh~ps object filing natural languaqe (invisible, protected structures) $40K I CAB I NET I ,4 (dedicated fixture) ~~~n limited context [:~~~~e~ ~~~:~~i:ti~n ~ ak rind pendent • voice ~tuate~ retrieval spe ~ e _ .. • te1econferenc1ng center cont1nued speechlrecogn~tion " ;., encryption associa tiveJparallel a;;;'e'los (, ..j." .---~ provide CAtt= ASSISTANT -------...--- .. • LIBRARlj\N ~ ?ertified "best match" retrieval ~ (secure) os (holographic? ) $650K BD 1/15/81 PRELIMINARY ENGINEERING STRATEGY OVERVIEW MARCH lYtil SECONIJ IJRAFT PRELIMINARY ENGINEERING STRATEGY OVERVIEW TABLE OF CONTENTS ,Preface Chapter I fhe Product Strategy and Transitioning to the Fifth Generation - Product Strategy Overview - The Transitions - Personal Computer Clusters, PCC, Are An Alternative to Timeshared Computers - The Product Strategy - Fifth and Sixth Computer Technology Generations - Uistributed Processing and Limits to Its Growth Chapter II Essays on the Criteria for Allocation of Engineering Resources - Overview, - Heuristics for Building Great Products, - Proposed Resource Allocation Criteria - UEC's Position in the VAN - Buyout Philosophy/Process/Criteria - Example of a "Make vs Buy" Analysis - Engineering Investment Sieve Chapter III Essays on Strategic Threats and Opportunities - Uverview, - Strategic Threats - Getting Organized in Engineering and Manufacturing to Face Our Future Competitors p - View of Competitors ---~,.~".~.-~ l f;t-1) IPrT Co?"! v. 7U/L, / IJ ...J - Te-Iecommunications Environment ) ;2f e-c.. - Competitive TeChnology Exercise, ltv • Chapter IV TeChnology Managers Committee Report ,MC- . -

A History of the Personal Computer Index/11
A History of the Personal Computer 6100 CPU. See Intersil Index 6501 and 6502 microprocessor. See MOS Legend: Chap.#/Page# of Chap. 6502 BASIC. See Microsoft/Prog. Languages -- Numerals -- 7000 copier. See Xerox/Misc. 3 E-Z Pieces software, 13/20 8000 microprocessors. See 3-Plus-1 software. See Intel/Microprocessors Commodore 8010 “Star” Information 3Com Corporation, 12/15, System. See Xerox/Comp. 12/27, 16/17, 17/18, 17/20 8080 and 8086 BASIC. See 3M company, 17/5, 17/22 Microsoft/Prog. Languages 3P+S board. See Processor 8514/A standard, 20/6 Technology 9700 laser printing system. 4K BASIC. See Microsoft/Prog. See Xerox/Misc. Languages 16032 and 32032 micro/p. See 4th Dimension. See ACI National Semiconductor 8/16 magazine, 18/5 65802 and 65816 micro/p. See 8/16-Central, 18/5 Western Design Center 8K BASIC. See Microsoft/Prog. 68000 series of micro/p. See Languages Motorola 20SC hard drive. See Apple 80000 series of micro/p. See Computer/Accessories Intel/Microprocessors 64 computer. See Commodore 88000 micro/p. See Motorola 80 Microcomputing magazine, 18/4 --A-- 80-103A modem. See Hayes A Programming lang. See APL 86-DOS. See Seattle Computer A+ magazine, 18/5 128EX/2 computer. See Video A.P.P.L.E. (Apple Pugetsound Technology Program Library Exchange) 386i personal computer. See user group, 18/4, 19/17 Sun Microsystems Call-A.P.P.L.E. magazine, 432 microprocessor. See 18/4 Intel/Microprocessors A2-Central newsletter, 18/5 603/4 Electronic Multiplier. Abacus magazine, 18/8 See IBM/Computer (mainframe) ABC (Atanasoff-Berry 660 computer. -

George A. Michael Papers
http://oac.cdlib.org/findaid/ark:/13030/c8vh5t99 No online items Guide to the George A. Michael papers Finding aid prepared by Bo Doub, Kim Hayden, and Sara Chabino Lott Processing of this collection was made possible through generous funding from The Andrew W. Mellon Foundation, administered through the Council on Library and Information Resources' Cataloging Hidden Special Collections and Archives grant. Computer History Museum 1401 N. Shoreline Blvd. Mountain View, CA, 94043 (650) 810-1010 [email protected] September 2015 Guide to the George A. Michael X4269.2008 1 papers Title: George A. Michael papers Identifier/Call Number: X4269.2008 Contributing Institution: Computer History Museum Language of Material: English Physical Description: 65.92 Linear feet, 49 record cartons, 1 manuscript box, 2 oversize flat boxes, and 1 small flat box Date (bulk): Bulk, 1953-1991 Date (inclusive): 1945-2000 Abstract: The George A. Michael papers consist of material related to the growth of the supercomputing industry and Lawrence Livermore National Laboratory's (LLNL) computing activities while Michael worked there as a computational scientist from 1953 to 1991. The collection reflects Michael's key role in the advancement of supercomputing inside and outside of LLNL, with reports, manuals, articles, and records related to conferences and projects from LLNL, Los Alamos National Laboratory, and other computing companies and organizations. His personal projects are also represented. Languages: The majority of the material in the collection is in English, but there is a small amount of material in French, German, and Italian. Processing Information Collection processed by Bo Doub and Kim Hayden, August 2015. -

The Computer Museum Report, Fall 1984
THE COMPUTER MUSEUM REPORT NUMBER 10 FALL 1984 Individual Founders D Charles W. Adams D Ken R. Adcock D David Ahl D John Alexanderson D Kendall Allphin D Gene M. Amdahl D Michael and Merry Andelman D Harlan E. & Lois Anderson D Applied Magnetics Corp. D Mr. & Mrs. Rolland B. Arndt D Dr. John Atanasoff D Isaac 1. Auerbach D AVX Corporation D Charles and Constance Bachman D Jean-Loup Baer D Robert W. Bailey, Ph.D. D John Banning D Jeremy Barker D Steve F. Barnebey D Harut Barsamian D John C. Barstow D Jordan and Rhoda Baruch D Gordon & Barbara Beeton D G. C. Belden, Jr. D C. Gordon & Gwen Bell D James and Roberta Bell D Chester Bell D Alan G. Bell D J. Weldon Bellville D Dr. Leo 1. Beranek D Roger & Kay Berger D Jeffrey Bernstein D Alfred M. Bertocchi D Gregory C . F. Bettice D Lamar C . Bevil. Jr. D Bitstream, Inc. D Erich & Renee Bloch D David R. Block D Elizabeth Boiger D Ted Bonn D Allen H. Brady D John G. Brainerd D David H. Brandin D Daniel S. Bricklin D Richard A. Brockelman D David A. Brown D Gordon S. Brown D Lawrence C. Brown D Arthur and Alice Burks D James R. Burley D Max Burnet D Jim & Margaret Butler D Marshall D. Butler D~oger C. Cady D Philip and Betsey Caldwell D Walter M. Carlson D Charles T. & Virginia G . Casale D George A. Chamberlain III D George A. Champine D Alan Chinnock D Donald Christiansen D Peter Christy and Carol Peters D Dr. -

Competitive Update
competitive update VOLUME 6 NUMBER 5 NOVEMBER 10, 1986 !!!!!!!!!!I!!I!!!!!!II!I!IIII!II!!!!!!!!!!I!!!I!!I!!!!!I!!I New Competitive Hotline Number 11/14/86) DTN: 283-6300 , , H" " , f f , , , , , , , H~ II ~ rr r r , r rr rr rr , r Outside: (617) 273-6300 IN THIS ISSUE Burroughs/Sperry Comlwtitiv(' Strategies: Looking at the Merger .................... 1 COlnpllt('r-Aided Softwar'(' Engineering Solution Competitive Positioning .............. 15 Mp('t ing t.he Challenge of Alliant .................................................. 25 Taking on Alliant, CorlvPx and S('quent ........................................... 31 Data (,('neral's MV/l7HOO and UG's Weakening Market Position ....................... 37 ()i~ital Applkation Center f()J' Technology (At:'!') Progralll .......................... 41 A'I'&'r ... in tht· Wak(' of ISI)N ................................................... 45 ~D~DDmD FOR INTERNAL USE ONLY comp-etitive up-date Published monthly, Competitive Update is the official Corporate publication to communicate information regarding major competitors' products and related Digital products. distribution The readership of Competitive Update comprises PACjMSCC members, Sales, Software, Field Service, Headquarters, Order Administration, Literature Contacts and other exempt personnel. Em~IOyeeS must submit their request to Carolyn Smith via memo OG01-1jU06), VAXMAIL (SALES::SMITH), or DECMAIL (COMP _UPDA ), stating name, badge number, job code, job title, cost center and location. change of address Notification of address changes should be directed to the employee's Personnel Representative or PSA for incorporation on the individual's Employee Profile form. Processing of this information is accomplished only through the Personnel Department. administration Competitive Update is published by HEADQUARTER SALES, OG01-1jU06, STOW, and is printed and distributed by Digital's Publishing and Circulation Services in Northboro. -

Nee ™ Fami Iy Overvi W NGEN
CONVERGENT TECHNOLOGIES NeE ™ Fami Iy Overvi w NGEN II Modular, high performance III Programming languages II Office Automation facilities desktop computing systems include COBOL, FORTRAN, include the Convergent Word BASIC, Pascal, assembler, Processor, Multiplan™, the 18 System components fit and C . Project Planner, the Business together like building blocks Graphics Package, and ;; Data management facilities System installation, CT-Mail ~ include CT-DBMS, ISAM, expansion and Sort/Merge, and an E Comprehensive Visinostics reconfiguration easily interactive Forms facility diagnostic package verifies p-erformed by end users system configuration, and 111 Data Communications allows operator to visually Basic system· includes an facilities include X.25, SNA Intel 16-bit microprocessor, select system components to (RJE and interactl-ve), Bisync with 256 KB of RAM be tested 3270 and 2780/3780, CT aNal Systems are expandable to (over RS-232 and X.25 Software compatible with the 768 KB or 1024 KB- in 256 KB media), and asynchronous Convergent AWSTM and IWSTM increments terminal emulation Workstations High quality 12-inch and 14-inch monochrome and 15-inch color displays with The ConvergenFMfamily of NGENTM Workstations is a modular family of work 29 lines of 80 characters stations which can be configured in a wide variety of ways, to meet diverse' application requirements in office and business applications. i~ Both monochrome and color graphics with 720 x: 348 pixel Configured around 16-bit Intel microprocessors, and the latest in 51f4-inch resolution mass storage technologies, the NGEN family is designed for applications that require the power and flexibility of a minicomputer, but at a far lower cost. -
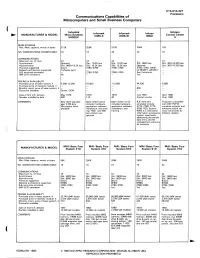
Communications Capabilities of Minicomputers and Small Business
C13-010-221 Processors Communications Capabilities of Minicomputers and Small Business Computers ( Industrial Infomark Infotecs Infomark Inforex Control Center MANUFACTURER & MODEL Micro Systems OMS-II OMS-III 9000 5000SX II MAIN STORAGE Min.lMax. capacity, words or bytes 512K 256K 512K 256K 1M NO. WORKSTATIONS CONNECTABLE 16 16 24 24 16 COMMUNICATIONS Maximum no. of lines 24 16 24 - 16 Synchronous Optional Opt.; 19.2K bps Opt.; 19.2K bps Std.; 9600 bps Std.; 300-19,200 bps Asynchronous Std.; 9600-19.2K bps Std.; 19.2K bps Std.; 19.2K bps Optional Std.; 300-19,200 bps Protocols supported Async 2780/3780 2780/3780 2780/3780, HASP, - Network architecture supported Turbodos (opt.) - - ULTRANET, ARCNET - RJE terminals emulated - 2780/3780 2780/3780 See Comments - IBM 3270 emulation No - - Yes - PRICING & AVAlLA81L1TY Purchase price of basic system, $ 3,000-12,000 67,000 113,300 44,630 6,995 Purchase price of memory module, $ - - - - - Monthly maint. price of basic system, $ - - - 800 - Discounts available Dealer, OEM - - - - Date of first U.S. delivery May 1979 1976 1976 July 1981 April 1980 Number installed to date 500 110 40 Contact vendor Over 1000 COMMENTS New table-top pack- 8asic system price 8asic system price RJE terminals Programs compatible age; 5.5M-byte includes hardware, includes hardware, emulated include with DEC PDP-8; Winchester drive application software application software, 2770, 2780, 3770, complete systems and available installation, and train- installation, and 3780, RES; System software sold & ser- ing; *600- and 900- training 9000 is a distributed viced nationwide by Ipm printers are information processing Infotecs' dealers optional system, specifically addressing distributed data entry and file management solutions for business MAli Basic Four MAl/Basic Four MAl/Basic Four MAli Basic Four MANUFACTURER & MODEL MAl/Basic Four System 210 System 310 System 510 System 610 System 710 MAIN STORAGE Min.lMax. -

The Computer Museum Report, Winter 1987/88
THE COMPUTER MUSEUM REPORT VOLUME 21 WINTER 1987/88 Contnbullng Members Michel Doreau John V Levy Thomas S Roy II Board ol Directors Operating Joseph L. Levy Grcmts Donor-$500 or more li'~J~ Drapes John D.C. Little ~~n~~n ~ PodusIta, Sr. Esthe r ~n Reed Little Howard~en Andover Pub~c Llbrary Joseph . Eachus MichaelSarnek Stellar Co~ Inc Anonymous Richard J. Eckhouse and ~rgel2e= Michael Sand ~F . ~p RollandAmdt Ruth M auIucci Arthur Luehrmann Robert Santy Executiv e Duector Burlingjon Public Library William T. Elliott Edwin Mallack ~=~~~Jr . ~~ter Museum $10,000 David Cutler P.J. Evans Julius M arcus SustaIMr~r James B Deaderick NeilFaiman Benneh Schwartz Founding President NlCkDe WolI Andrew Farber ~Mf~~n Andrew Scott [)jgital ~~men t Corp. ~Co=ter M useum Hewlett- ard I«ly Duncan ~g~tleldman and Richard O. M ason Curtis A. Scott IBM Branko Gerovac Sib~1 Masquelier Ronald F. Shea National Science Tom and Rosemarie Hall Harold J. evadsOn Massey Philip Shearer Foundation M assachusetts Councll Fifc~ for the Arts and Martin K1rkpatnck Robert France & Ruth Peter M asters Aaron Seidman Lynda Schubert Bodrncm Alex Koller Doan Robert Mayer. Jr R. &. M . Shamel Schubert Associates Humanilles Sequent Computer Corp Raymond Kurzweil J. Thomas Franklin W . Lee Shevel Davtd L Cbapmcm Andrew Levien Clark Frazier Wg~~t~~iY Dan Siewiorek Culhnet Software. Inc Sun Micros~tems Thomas Marill Darnel Freedman F. Warren M cFarlan DIane J Skiba Symbo~cs . c . DavId Donakbon Mllton Public Library Alan E. Frisbie Douglas M cKenna Charles SkoUield ~J~ay Chnstofher M organ Bruce Gee William M cLean Benefactor-$IO,OOO Llnda . -

Information Technology R&D: Critical Trends and Issues
Information Technology R&D: Critical Trends and Issues February 1985 NTIS order #PB85-245660 — Recommended Citation: Information Technology and R&D: Critical Trends and Issues (Washington, DC: U.S. Congress, Office of Technology Assessment, OTA-CIT-268, February 1985). Library of Congress Catalog Card Number 84-601150 For sale by the Superintendent of Documents U.S. Government Printing Office, Washington, DC 20402 Foreword New computer and communications technologies are obviously transforming American life. They are the basis of many of the changes in our telecommunica- tions system and also a new wave of automation on the farm, in manufacturing and transportation, and in the office. They are changing the form and delivery of government services such as education and the judicial system. Information products and services have become a major and still rapidly growing component of our economy. A strong U.S. research and development effort has, in the past, been the source of much of this new technology. However, recent events, such as the restructur- ing of the U.S. telecommunications industry and the emergence of strong foreign competition for some technologies, have changed the environment for R&D. Con- sequently, the House Committee on Science and Technology, the House Commit- tee on Energy and Commerce, and its Subcommittee on Telecommunications, Con- sumer Protection, and Finance asked OTA to conduct an assessment of the current state of R&D in these critical areas. In this report, OTA examines four specific areas of research as case studies: computer architecture, artificial intelligence, fiber optics, and software engineer- ing. It discusses the structure and orientation of some selected foreign programs. -

Securities and Exchange Commission Washington, D.C
SECURITIES AND EXCHANGE COMMISSION WASHINGTON, D.C. 20549 FORM 10-K (Mark One) ___ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE [_X_] SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 31, 1997 OR ___ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) [___] OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from ____________ to ____________. Commission file number: 1-8729 UNISYS CORPORATION (Exact name of registrant as specified in its charter) Delaware 38-0387840 (State or other jurisdiction of (I.R.S. Employer incorporation or organization) Identification No.) Township Line and Union Meeting Roads Blue Bell, Pennsylvania 19424 (Address of principal executive offices) (Zip Code) Registrant's telephone number, including area code: (215) 986-4011 Securities registered pursuant to Section 12(b) of the Act: NAME OF EACH EXCHANGE ON TITLE OF EACH CLASS WHICH REGISTERED ------------------- ------------------------ Common Stock, par value $.01 New York Stock Exchange Series A Cumulative Convertible Preferred Stock, par value $1, $3.75 annual fixed dividend New York Stock Exchange Preferred Share Purchase Rights New York Stock Exchange 8 1/4% Convertible Subordinated Notes Due 2006 New York Stock Exchange Securities registered pursuant to Section 12(g) of the Act: None -2- Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days.