Fraud Prevention in Ecommerce Report 2020 / 2021 the Ultimate Source in Securing Transactions While Offering a Frictionless Journey to Customers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Voice of Online Sellers — Singapore Introduction
The Voice of Online Sellers — Singapore Introduction Here at WorldFirst, we take great pleasure in helping online sellers grow their business. We like to think we do more than simply lower their currency exchange costs - we enable sellers to go global and we always feel part of their journey. In Q4 2017, we conducted the ‘Voice of Online Sellers’ survey, which was completed by people based in Singapore who are selling internationally through marketplaces like Amazon and eBay and platforms like Shopify. We had a great response to this campaign, where one lucky participant was drawn at random and won $5,000 to help grow their eCommerce business. We had three key objectives for this project: 1. Collect insights to share with other online sellers who are just starting out, or who are looking to grow their existing business 2. Better understand the challenges, motivations and successes of our clients 3. Help one participant grow their business A big thank you to all those who participated in the survey and congratulations to our lucky winner, Alvin, who sells on Amazon and through Shopify. We hope that you find this report useful in running and improving your eCommerce business. Peter Scully Country Manager WorldFirst Singapore Online Selling Trends Marketplaces & platforms Singapore-based sellers are using three household names to tap into the international eCommerce market. Amazon and eBay are the most popular choices for marketplace selling and Shopify was the clear leading platform for those building their own website to go global. Top primary platforms/marketplaces: Most popular secondary platforms/marketplaces: 1. -

Response: Just Eat Takeaway.Com N. V
NON- CONFIDENTIAL JUST EAT TAKEAWAY.COM Submission to the CMA in response to its request for views on its Provisional Findings in relation to the Amazon/Deliveroo merger inquiry 1 INTRODUCTION AND BACKGROUND 1. In line with the Notice of provisional findings made under Rule 11.3 of the Competition and Markets Authority ("CMA") Rules of Procedure published on the CMA website, Just Eat Takeaway.com N.V. ("JETA") submits its views on the provisional findings of the CMA dated 16 April 2020 (the "Provisional Findings") regarding the anticipated acquisition by Amazon.com BV Investment Holding LLC, a wholly-owned subsidiary of Amazon.com, Inc. ("Amazon") of certain rights and minority shareholding of Roofoods Ltd ("Deliveroo") (the "Transaction"). 2. In the Provisional Findings, the CMA has concluded that the Transaction would not be expected to result in a substantial lessening of competition ("SLC") in either the market for online restaurant platforms or the market for online convenience groceries ("OCG")1 on the basis that, as a result of the Coronavirus ("COVID-19") crisis, Deliveroo is likely to exit the market unless it receives the additional funding available through the Transaction. The CMA has also provisionally found that no less anti-competitive investors were available. 3. JETA considers that this is an unprecedented decision by the CMA and questions whether it is appropriate in the current market circumstances. In its Phase 1 Decision, dated 11 December 20192, the CMA found that the Transaction gives rise to a realistic prospect of an SLC as a result of horizontal effects in the supply of food platforms and OCG in the UK. -

Move Beyond Passwords Index
Move Beyond Passwords Index The quest to move beyond passwords 4 Evaluation of current authentication method 6 Getting started with passwordless authentication 8 Early results to going passwordless 9 Common approaches to going passwordless 11 Email magic links 11 Factor sequencing 12 Webauthn 14 Planning for a passwordless future 16 Move Beyond Passwords 2 Introduction Traditional authentication using a username and password has been the foundation of digital identity and security for over 50 years. But with the ever-growing number of user accounts, there are a number of new issues: the burden on end users to remember multiple passwords, support costs, and most importantly, the security risks posed by compromised credentials. These new challenges are now outweighing the usefulness of passwords. The case for eliminating passwords from the authentication experience is getting more compelling every day. Emerging passwordless security standards, elevated consumer and consumer-like experience expectations, and ballooning costs have moved eliminating passwords from a theoretical concept to a real possibility. In this whitepaper, we will explore the case for going passwordless for both customer and employee authentication, and map out steps that organizations can take on their journey to true passwordless authentication. Move Beyond Passwords 3 The quest to move beyond passwords Understanding the need for passwordless authentication starts with understanding the challenges presented by passwords. The core challenges with passwords can be broken down into the following areas: Poor Account Security Passwords have spawned a whole category of security/identity-driven attacks — compromised passwords due to credential breaches, phishing, password spraying attacks, or poor password hygiene can result in account takeover attacks (ATO). -
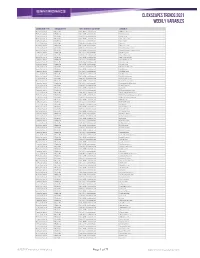
Clickscapes Trends 2021 Weekly Variables
ClickScapes Trends 2021 Weekly VariableS Connection Type Variable Type Tier 1 Interest Category Variable Home Internet Website Arts & Entertainment 1075koolfm.com Home Internet Website Arts & Entertainment 8tracks.com Home Internet Website Arts & Entertainment 9gag.com Home Internet Website Arts & Entertainment abs-cbn.com Home Internet Website Arts & Entertainment aetv.com Home Internet Website Arts & Entertainment ago.ca Home Internet Website Arts & Entertainment allmusic.com Home Internet Website Arts & Entertainment amazonvideo.com Home Internet Website Arts & Entertainment amphitheatrecogeco.com Home Internet Website Arts & Entertainment ancestry.ca Home Internet Website Arts & Entertainment ancestry.com Home Internet Website Arts & Entertainment applemusic.com Home Internet Website Arts & Entertainment archambault.ca Home Internet Website Arts & Entertainment archive.org Home Internet Website Arts & Entertainment artnet.com Home Internet Website Arts & Entertainment atomtickets.com Home Internet Website Arts & Entertainment audible.ca Home Internet Website Arts & Entertainment audible.com Home Internet Website Arts & Entertainment audiobooks.com Home Internet Website Arts & Entertainment audioboom.com Home Internet Website Arts & Entertainment bandcamp.com Home Internet Website Arts & Entertainment bandsintown.com Home Internet Website Arts & Entertainment barnesandnoble.com Home Internet Website Arts & Entertainment bellmedia.ca Home Internet Website Arts & Entertainment bgr.com Home Internet Website Arts & Entertainment bibliocommons.com -

Special Edition on Advanced Analytics in Banking
McKinsey on Payments Special Edition on Advanced Analytics in Banking Highlights 4 13 36 The analytics-enabled How machine learning can Hidden figures: The quiet collections model improve pricing performance discipline of managing people using data 52 60 68 Designing a data Building an effective “All in the mind”: Harnessing transformation that delivers analytics organization psychology and analytics to value right from the start counter bias and reduce risk Volume 11 Number 28 August 2018 McKinsey on Payments is written by experts and practitioners in the McKinsey & Company Global Payments Practice. To send comments or request copies, email us at: [email protected] To download selected articles from previous issues, visit: https://www.mckinsey.com/industries/financial-services/our-insights/payments Editorial board for special analytics issue: Kevin Buehler, Vijay D’Silva, Matt Fitzpatrick, Arvind Govindarajan, Megha Kansal, Gloria Macias-Lizaso Miranda McKinsey on Payments editorial board: Alessio Botta, Philip Bruno, Robert Byrne, Olivier Denecker, Vijay D’Silva, Tobias Lundberg, Marc Niederkorn Editors: John Crofoot, Peter Jacobs, Glen Sarvady, Anne Battle Schultz, Jill Willder Global Payments Practice manager: Natasha Karr Global Advanced Analytics in Banking Practice manager: Josephine Axtman Managing editor: Pa ul Feldman Design and layout: Derick Hudspith Copyright © 201 8 McKinsey & Company. All rights reserved. This publication is not intended to be used as the basis for any transaction. Nothing herein shall be construed as legal, financial, accounting, investment, or other type of professional advice. If any such advice is required, the services of appropriate advisers should be sought. No part of this publication may be copied or redistributed in any form without the prior written permission of McKinsey & Company. -

E-Commerce and Its Impact on Competition Policy and Law in Singapore
E-commerce and its impact on competition policy and law in Singapore A DotEcon study for the Competition Commission of Singapore Final Report – October 2015 DotEcon Ltd 17 Welbeck Street London W1G 9XJ www.dotecon.com Content Content 1 Introduction ................................................................................................................. 1 2 E-commerce activity in Singapore ............................................................................... 4 2.1 An introduction to e-commerce ........................................................................... 4 2.2 E-commerce adoption in Singapore ................................................................... 17 3 E-commerce and competition .................................................................................... 38 3.1 What changes with e-commerce? ...................................................................... 38 3.2 The impact of e-commerce on market boundaries ............................................. 59 3.3 The impact of e-commerce on market structure and competition ...................... 65 3.4 Vertical restraints ............................................................................................... 77 4 Implications of e-commerce for competition policy in Singapore .............................. 83 4.1 Defining a relevant market ................................................................................. 84 4.2 Assessing market power ................................................................................... -

Food and Tech August 13
⚡️ Love our newsletter? Share the ♥️ by forwarding it to a friend! ⚡️ Did a friend forward you this email? Subscribe here. FEATURED Small Farmers Left Behind in Covid Relief, Hospitality Industry Unemployment Remains at Depression-Era Levels + More Our round-up of this week's most popular business, tech, investment and policy news. Pathways to Equity, Diversity + Inclusion: Hiring Resource - Oyster Sunday This Equity, Diversity + Inclusion Hiring Resource aims to help operators to ensure their tables are filled with the best, and most equal representation of talent possible – from drafting job descriptions to onboarding new employees. 5 Steps to Move Your Food, Beverage or Hospitality Business to Equity Jomaree Pinkard, co-founder and CEO of Hella Cocktail Co, outlines concrete steps businesses and investors can take to foster equity in the food, beverage and hospitality industries. Food & Ag Anti-Racism Resources + Black Food & Farm Businesses to Support We've compiled a list of resources to learn about systemic racism in the food and agriculture industries. We also highlight Black food and farm businesses and organizations to support. CPG China Says Frozen Chicken Wings from Brazil Test Positive for Virus - Bloomberg The positive sample appears to have been taken from the surface of the meat, while previously reported positive cases from other Chinese cities have been from the surface of packaging on imported seafood. Upcycled Molecular Coffee Startup Atomo Raises $9m Seed Funding - AgFunder S2G Ventures and Horizons Ventures co-led the round. Funding will go towards bringing the product to market. Diseased Chicken for Dinner? The USDA Is Considering It - Bloomberg A proposed new rule would allow poultry plants to process diseased chickens. -

Cybersecurity in a Digital Era.Pdf
Digital McKinsey and Global Risk Practice Cybersecurity in a Digital Era June 2020 Introduction Even before the advent of a global pandemic, executive teams faced a challenging and dynamic environ- ment as they sought to protect their institutions from cyberattack, without degrading their ability to innovate and extract value from technology investments. CISOs and their partners in business and IT functions have had to think through how to protect increasingly valuable digital assets, how to assess threats related to an increasingly fraught geopolitical environment, how to meet increasingly stringent customer and regulatory expectations and how to navigate disruptions to existing cybersecurity models as companies adopt agile development and cloud computing. We believe there are five areas for CIOs, CISOs, CROs and other business leaders to address in particular: 1. Get a strategy in place that will activate the organization. Even more than in the past cybersecurity is a business issue – and cybersecurity effectiveness means action not only from the CISO organiza- tion, but also from application development, infrastructure, product development, customer care, finance, human resources, procurement and risk. A successful cybersecurity strategy supports the business, highlights the actions required from across the enterprise – and perhaps most importantly captures the imagination of the executive in how it can manage risk and also enable business innovation. 2. Create granular, analytic risk management capabilities. There will always be more vulnerabilities to address and more protections you can consider than you will have capacity to implement. Even companies with large and increasing cybersecurity budgets face constraints in how much change the organization can absorb. -

List of Unregistered Controlled Goods Found
ANNEX A List of Unregistered Controlled Goods Found S/N Product Information E-Commerce Name of seller on Platform Sold e-commerce On platform 1 Product Type: USB Wall charger Lazada.sg Rareus Singapore Brand & Model Number: Tronsmart W2DT 2 Product Type: 5-Port USB charger Lazada.sg PROLink Brand & Model Number: PROLink PDC53001 3 Product Type: C48 Breakthrough Lazada.sg iShopee.sg 3USB Charger Brand & Model Number: hoco C48 4 Product Type: USB Wall Charger Lazada.sg Ace Star Brand & Model Number: K.FULAI KA-16 5 Product Type: Vertical Multi Lazada.sg LongerVogue.com Socket Brand & Model Number: JW401 6 Product Type: Dual Port USB Lazada.sg Best Dealss Charger Adapter Brand & Model Number: None 7 Product Type: Funzi U+ Type-C Lazada.sg Airdrop Tech PD Charger Brand & Model Number: Baseus BS-UKQC02 8 Product Type: Essential Quick Lazada.sg SGP3M Charge 3.0 Wall Charger Brand & Model Number: Spigen F207 9 Product Type: Convert Design Lazada.sg iCool Accessories Travel Charger Brand & Model Number: LDNIO A2502Q 10 Product Type: LED Touchlamp Lazada.sg Illusion distribution with USB Port Charger Brand & Model Number: TOPK C4405 11 Product Type: 6 USB 3 Power Lazada.sg 32Day.Tech Socket Brand & Model Number: LDNIO SC3604 12 Product Type: 6 USB 3 Power Lazada.sg Offer & Save Socket Superstore Brand & Model Number: LDNIO SC3604 13 Product Type: 6 USB 3 Power Lazada.sg D-Tech Socket Brand & Model Number: LDNIO SC3604 14 Product Type: Juicer Lazada.sg SCI SG Mall Brand & Model Number: Joyoung JYZ-V15 15 Product Type: Electric Kettle Lazada.sg -

Implementing a Web Application for W3C Webauthn Protocol Testing †
proceedings Proceedings Implementing a Web Application for W3C WebAuthn Protocol Testing † Martiño Rivera Dourado 1,* , Marcos Gestal 1,2 and José M. Vázquez-Naya 1,2 1 Grupo RNASA-IMEDIR, Departamento de Computación, Facultade de Informática, Universidade da Coruña, Elviña, 15071 A Coruña, Spain; [email protected] (M.G.); [email protected] (J.M.V.-N.) 2 Centro de Investigación CITIC, Universidade da Coruña, Elviña, 15071 A Coruña, Spain * Correspondence: [email protected] † Presented at the 3rd XoveTIC Conference, A Coruña, Spain, 8–9 October 2020. Published: 18 August 2020 Abstract: During the last few years, the FIDO Alliance and the W3C have been working on a new standard called WebAuthn that aims to substitute the obsolete password as an authentication method by using physical security keys instead. Due to its recent design, the standard is still changing and so are the needs for protocol testing. This research has driven the development of a web application that supports the standard and gives extensive information to the user. This tool can be used by WebAuthn developers and researchers, helping them to debug concrete use cases with no need for an ad hoc implementation. Keywords: WebAuthn; authentication; testing 1. Introduction Authentication is one of the most critical parts of an application. It is a security service that aims to guarantee the authenticity of an identity. This can be done by using several security mechanisms but currently, without a doubt, the most common is the username and password method. Although this method is easy for a user to conceptually understand, it constitutes many security problems. -

ANNUAL CRIME BRIEF 2020 Singapore Remains One of the Safest Cities in the World
POLICE NEWS RELEASE _________________________________________________________________ ANNUAL CRIME BRIEF 2020 Singapore Remains One of the Safest Cities in the World Overall Crime Rate increased due to rise in scam cases Singapore remains one of the safest cities in the world. Singapore was ranked first in the Gallup’s 2020 Global Law and Order report for the seventh consecutive year, with 97% of residents reporting that they felt safe walking home alone in their neighbourhood at night, as compared to an average of 69% worldwide.1 The World Justice Project’s Rule of Law Index 2020 also ranked Singapore first for order and security.2 2. In 2020, the total number of reported crimes increased by 6.5% to 37,409 cases, from 35,115 cases in 2019. The Overall Crime Rate also increased, with 658 cases per 100,000 population in 2020, compared to 616 cases per 100,000 population in 2019.3 3. The increase in the number of reported crimes was due to a rise in scam cases. In particular, online scams saw a significant increase as Singaporeans carried out more online transactions due to the COVID-19 situation. 4 Please see Annex A for the statistics on the top ten scam types. 4. If scam cases were excluded, the total number of reported crimes in 2020 would have decreased by 15.3% to 21,653 from 25,570 in 2019. Decrease in physical crimes and more crime-free days 5. There was a decrease in physical crimes in 2020. 201 days were free from three confrontational crimes, namely snatch theft, robbery and housebreaking, an increase of 23 days compared to 178 days in 2019. -

8 Steps for Effectively Deploying
8 Steps for Effectively Deploying MFA Table of Contents The value of MFA 3 1. Educate your users 4 2. Consider your MFA policies 5 3. Plan and provide for a variety of access needs 7 4. Think twice about using SMS for OTP 10 5. Check compliance requirements carefully 11 6. Plan for lost devices 12 7. Plan to deploy MFA to remote workers 14 8. Phase your deployment: Be prepared to review and revise 16 8 Steps for Effectively Deploying MFA 2 The value of MFA Multi-factor authentication (MFA) has never been more important. With the growing number of data breaches and cybersecurity threats—and the steep financial and reputational costs that come with them—organizations need to prioritize MFA deployment for their workforce and customers alike. Not doing so could spell disaster; an invitation for bad actors to compromise accounts and breach your systems. Adopting modern MFA means implementing a secure, simple, and context-aware solution that ensures that only the right people have access to the right resources. It adds a layer of security, giving your security team, your employees, and your customers peace of mind. Unfortunately, while the benefits are clear, implementing MFA can be a complex project. In our Multi-factor Authentication Deployment Guide, we’ve outlined eight steps that you can take to better enable your MFA deployment: Educate your users Consider your MFA policies Plan and provide for a variety of access needs Think twice about using SMS for OTP Check compliance requirements carefully Plan for lost devices Plan to deploy MFA to remote workers Phase your deployment: be prepared to review and revise In this eBook, we’ll take a deeper dive into each of these elements, giving you tactical advice and best practices for how to implement each step as you get ready to roll out Okta MFA.