Defeating Coercive Information Operations in Future Crises
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Aalseth Aaron Aarup Aasen Aasheim Abair Abanatha Abandschon Abarca Abarr Abate Abba Abbas Abbate Abbe Abbett Abbey Abbott Abbs
BUSCAPRONTA www.buscapronta.com ARQUIVO 35 DE PESQUISAS GENEALÓGICAS 306 PÁGINAS – MÉDIA DE 98.500 SOBRENOMES/OCORRÊNCIA Para pesquisar, utilize a ferramenta EDITAR/LOCALIZAR do WORD. A cada vez que você clicar ENTER e aparecer o sobrenome pesquisado GRIFADO (FUNDO PRETO) corresponderá um endereço Internet correspondente que foi pesquisado por nossa equipe. Ao solicitar seus endereços de acesso Internet, informe o SOBRENOME PESQUISADO, o número do ARQUIVO BUSCAPRONTA DIV ou BUSCAPRONTA GEN correspondente e o número de vezes em que encontrou o SOBRENOME PESQUISADO. Número eventualmente existente à direita do sobrenome (e na mesma linha) indica número de pessoas com aquele sobrenome cujas informações genealógicas são apresentadas. O valor de cada endereço Internet solicitado está em nosso site www.buscapronta.com . Para dados especificamente de registros gerais pesquise nos arquivos BUSCAPRONTA DIV. ATENÇÃO: Quando pesquisar em nossos arquivos, ao digitar o sobrenome procurado, faça- o, sempre que julgar necessário, COM E SEM os acentos agudo, grave, circunflexo, crase, til e trema. Sobrenomes com (ç) cedilha, digite também somente com (c) ou com dois esses (ss). Sobrenomes com dois esses (ss), digite com somente um esse (s) e com (ç). (ZZ) digite, também (Z) e vice-versa. (LL) digite, também (L) e vice-versa. Van Wolfgang – pesquise Wolfgang (faça o mesmo com outros complementos: Van der, De la etc) Sobrenomes compostos ( Mendes Caldeira) pesquise separadamente: MENDES e depois CALDEIRA. Tendo dificuldade com caracter Ø HAMMERSHØY – pesquise HAMMERSH HØJBJERG – pesquise JBJERG BUSCAPRONTA não reproduz dados genealógicos das pessoas, sendo necessário acessar os documentos Internet correspondentes para obter tais dados e informações. DESEJAMOS PLENO SUCESSO EM SUA PESQUISA. -
Rns Over the Long Term and Critical to Enabling This Is Continued Investment in Our Technology and People, a Capital Allocation Priority
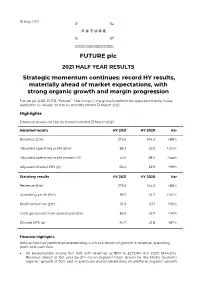
19 May 2021 FUTURE plc 2021 HALF YEAR RESULTS Strategic momentum continues: record HY results, materially ahead of market expectations, with strong organic growth and margin progression Future plc (LSE: FUTR, “Future”, “the Group”), the global platform for specialist media, today publishes its results for the six months ended 31 March 2021. Highlights Financial results for the six months ended 31 March 2021 Adjusted results HY 2021 HY 2020 Var Revenue (£m) 272.6 144.3 +89% Adjusted operating profit (£m)1 89.2 39.9 +124% Adjusted operating profit margin (%) 33% 28% +5ppt Adjusted diluted EPS (p) 65.4 32.9 +99% Statutory results HY 2021 HY 2020 Var Revenue (£m) 272.6 144.3 +89% Operating profit (£m) 59.7 24.7 +142% Profit before tax (£m) 56.9 27.1 +110% Cash generated from operations (£m) 85.9 35.7 +141% Diluted EPS (p) 40.7 21.8 +87% Financial highlights Robust first-half performance extending our track record of growth in revenue, operating profit and cash flow: An exceptionally strong first half, with revenue up 89% to £272.6m (HY 2020: £144.3m). Revenue ahead of last year by 21% on an organic2 basis, driven by the Media division’s organic2 growth of 30% and in particular digital advertising on-platform organic2 growth of 30% and eCommerce affiliates’ organic2 growth of 56%. US achieved revenue growth of 31% on an organic2 basis and UK revenues grew by 5% organically (UK has a higher mix of events and magazines revenues which were impacted more materially by the pandemic). -

18734 Homework 3
18734 Homework 3 Released: October 7, 2016 Due: 12 noon Eastern, 9am Pacific, Oct 21, 2016 1 Legalease [20 points] In this question, you will convert a simple policy into the Legalease language. To review the Legalease language and its grammar, refer to the lecture slides from September 28. You may find it useful to go through a simple example provided in Section III.C in the paper Bootstrapping Privacy Compliance in Big Data Systems 1. A credit company CreditX has the following information about its customers: • Name • Address • PhoneNumber • DateOfBirth • SSN All this information is organized under a common table: AccountInfo. Their privacy policy states the following: We will not share your SSN with any third party vendors, or use it for any form of advertising. Your phone number will not be used for any purpose other than notifying you about inconsistencies in your account. Your address will not be used, except by the Legal Team for audit purposes. Convert this statement into Legalease. You may use the attributes: DataType, UseForPur- pose, AccessByRole. Relevant attribute-values for DataType are AccountInfo, Name, Address, PhoneNumber, DateOfBirth, and SSN. Useful attribute-values for UseForPurpose are ThirdPar- tySharing, Advertising, Notification and Audit. One attribute-value for AccessByRole is LegalTeam. 1http://www.andrew.cmu.edu/user/danupam/sen-guha-datta-oakland14.pdf 1 2 AdFisher [35=15+20 points] For this part of the homework, you will work with AdFisher. AdFisher is a tool written in Python to automate browser based experiments and run machine learning based statistical analyses on the collected data. 2.1 Installation AdFisher was developed around 2014 on MacOS. -

August Sunday Talk Shows Data
August Sunday Talk Shows Data August 1, 2010 21 men and 6 women NBC's Meet the Press with David Gregory: 5 men and 1 woman Admiral Michael Mullen (M) Mayor Michael Bloomberg (M) Alan Greenspan (M) Gov. Ed Rendell (M) Doris Kearns Goodwin (F) Mark Halperin (M) CBS's Face the Nation with Bob Schieffer: 4 men and 0 women Admiral Michael Mullen (M) Sen. Jon Kyl (M) Richard Haass (M) Thomas Saenz (M) ABC's This Week with Jake Tapper: 4 men and 2 women Sen. Nancy Pelosi (F) Robert Gates (M) George Will (M) Paul Krugman (M) Donna Brazile (F) Ahmed Rashid (M) CNN's State of the Union with Candy Crowley: 4 men and 0 women Sen. Carl Levin (M) Sen. Lindsey Graham (M) Dan Balz (M) Peter Baker (M) Fox News' Fox News Sunday with Chris Wallace: 4 men and 3 women Sarah Palin (F) Sen. Mitch McConnell (M) Rep. John Boehner (M) Bill Kristol (M) Ceci Connolly (F) Liz Cheney (F) Juan Williams (M) August 8, 2010 20 men and 7 women NBC's Meet the Press with David Gregory: 4 men and 2 women Carol Browner (F) Rep. John Boehner (M) Rep. Mike Pence (M) former Rep. Harold Ford (M) Andrea Mitchell (F) Todd S. Purdum (M) CBS's Face the Nation with Bob Schieffer: 4 men and 1 woman Admiral Thad Allen (M) David Boies (M) Tony Perkins (M) Dan Balz (M) Jan Crawford (F) ABC's This Week with Jake Tapper: 5 men and 1 woman General Ray Odierno (M) Gen. -
Last Name First Name Ticket Number ACIKEL FATIH 644001 ADAMS
Last Name First Name Ticket Number ACIKEL FATIH 644001 ADAMS AURORA 644002 ADAMS CHRISTIAN 644003 AHAD COLE 644004 ALAIMO JOSEPH 644005 ALAIMO SAM 644006 ALDERSON NOLAN 644007 ALEXANDER BRANDON 644008 ALEXANDER COHEN 644009 ALLAN CHARLIE 644010 ALLAN NOLAN 644011 ALLCHIN BENJAMIN 644012 ALVARADO NICHOLAS 644013 AMIRAULT GAVIN 644014 AMIRAULT JOSHUA 644015 AMMENDOLIA MARCO 644016 ANDERSON BRANDON 644017 ANDERSON OWEN 644018 ANDERSON SETH 644019 APPEL JOSH 644020 ARCAND WESTON 644021 ARKELL IAN 644022 ARMENTI LUCAS 644023 ARMENTI MASSIMO 644024 ARSENAULT TROY 644025 ASIS GRAYSON 644026 ASSELIN WYATT 644027 ATHERTON DATON 644028 AZEM SIMMONS BLAZE 644029 AZEM SIMMONS JADE 644030 AZEM SIMMONS KYLEN 644031 BACH AYDEN 644032 BAIOCCO MARIO 644033 BAIRD EVAN 644034 BAIRD LIAM 644035 BAIRD OWEN 644036 BAKER BENNETT 644037 BALL DANIEL 644038 BALL MATTHEW 644039 BANDERS LEO 644040 BANNISTER DYLAN 644041 BANNISTER LANDEN 644042 BARCHIESI BRYNN 644043 BARCHIESI SLOAN 644044 BARCLAY LONDON 644045 BARKER CHARLIE 644046 BARLOW HOLDEN 644047 BARNHARDT JAMES 644048 BARNHARDT WILLIAM 644049 BARRINGTON DYLAN 644050 BARRON LUCAS 644051 BARRY KELDON 644052 BARRY NOLAN 644053 BARRY TYSEN 644054 BARTON BROGAN 644055 BARTON NOLAN 644056 BASS-MELDRUM CALEB 644057 BAUGHMAN BRICE 644058 BAUGHMAN BRODY 644059 BEAMISH LEVI 644060 BEAMISH ZACK 644061 BEAUVAIS NOAH 644062 BEAVER BENJAMIN 644063 BEAVER JOSHUA 644064 BECK ERIC 644065 BELANGER BEAU 644066 BELANGER ETHAN 644067 BELFORD LINCOLN 644068 BENNETT COOPER 644069 BENSON JACK 644070 BERECZ MAX 644071 BERGEN CONNELL -

North Dakota Homeland Security Anti-Terrorism Summary
UNCLASSIFIED North Dakota Homeland Security Anti-Terrorism Summary The North Dakota Open Source Anti-Terrorism Summary is a product of the North Dakota State and Local Intelligence Center (NDSLIC). It provides open source news articles and information on terrorism, crime, and potential destructive or damaging acts of nature or unintentional acts. Articles are placed in the Anti-Terrorism Summary to provide situational awareness for local law enforcement, first responders, government officials, and private/public infrastructure owners. UNCLASSIFIED UNCLASSIFIED NDSLIC Disclaimer The Anti-Terrorism Summary is a non-commercial publication intended to educate and inform. Further reproduction or redistribution is subject to original copyright restrictions. NDSLIC provides no warranty of ownership of the copyright, or accuracy with respect to the original source material. Quick links North Dakota Energy Regional Food and Agriculture National Government Sector (including Schools and Universities) International Information Technology and Banking and Finance Industry Telecommunications Chemical and Hazardous Materials National Monuments and Icons Sector Postal and Shipping Commercial Facilities Public Health Communications Sector Transportation Critical Manufacturing Water and Dams Defense Industrial Base Sector North Dakota Homeland Security Emergency Services Contacts UNCLASSIFIED UNCLASSIFIED North Dakota Nothing Significant to Report Regional (Minnesota) Hacker charged over siphoning off funds meant for software devs. An alleged hacker has been charged with breaking into the e-commerce systems of Digital River before redirecting more than $250,000 to an account under his control. The hacker, of Houston, Texas, 35, is charged with fraudulently obtaining more than $274K between December 2008 and October 2009 following an alleged hack against the network of SWReg Inc, a Digital River subsidiary. -

Toward an Enhanced Strategic Policy in the Philippines
Toward an Enhanced Strategic Policy in the Philippines EDITED BY ARIES A. ARUGAY HERMAN JOSEPH S. KRAFT PUBLISHED BY University of the Philippines Center for Integrative and Development Studies Diliman, Quezon City First Printing, 2020 UP CIDS No part of this book may be reprinted or reproduced or utilised in any form or by any electronic, mechanical, or other means, now known or hereafter invented, without written permission from the publishers. Recommended Entry: Towards an enhanced strategic policy in the Philippines / edited by Aries A. Arugay, Herman Joseph S. Kraft. -- Quezon City : University of the Philippines, Center for Integrative Studies,[2020],©2020. pages ; cm ISBN 978-971-742-141-4 1. Philippines -- Economic policy. 2. Philippines -- Foreign economic relations. 2. Philippines -- Foreign policy. 3. International economic relations. 4. National Security -- Philippines. I. Arugay, Aries A. II. Kraft, Herman Joseph S. II. Title. 338.9599 HF1599 P020200166 Editors: Aries A. Arugay and Herman Joseph S. Kraft Copy Editors: Alexander F. Villafania and Edelynne Mae R. Escartin Layout and Cover design: Ericson Caguete Printed in the Philippines UP CIDS has no responsibility for the persistence or accuracy of urls for external or third-party internet websites referred to in this publication, and does not guarantee that any content on such websites is, or will remain, accurate or appropriate. TABLE OF CONTENTS Acknowledgements ______________________________________ i Foreword Stefan Jost ____________________________________________ iii Teresa S. Encarnacion Tadem _____________________________v List of Abbreviations ___________________________________ ix About the Contributors ________________________________ xiii Introduction The Strategic Outlook of the Philippines: “Situation Normal, Still Muddling Through” Herman Joseph S. Kraft __________________________________1 Maritime Security The South China Sea and East China Sea Disputes: Juxtapositions and Implications for the Philippines Jaime B. -

DEPARTMENT of DEFENSE Office of the Secretary, the Pentagon, Washington, DC 20301–1155 Phone, 703–545–6700
DEPARTMENT OF DEFENSE Office of the Secretary, The Pentagon, Washington, DC 20301–1155 Phone, 703–545–6700. Internet, www.defenselink.mil. SECRETARY OF DEFENSE ROBERT M. GATES DEPUTY SECRETARY OF DEFENSE WILLIAM LYNN III Under Secretary of Defense for Acquisition, ASHTON B. CARTER Technology, and Logistics Deputy Under Secretary of Defense (Business PAUL A. BRINKLEY Transformation) Deputy Under Secretary of Defense LOUIS W. ARNY III (Installations and Environment) Under Secretary of Defense for Policy MICHELE FLOURNOY Principal Deputy Under Secretary of Defense JAMES N. MILLER, JR. for Policy Assistant Secretary of Defense (International ALEXANDER R. VERSHBOW Security Affairs) Assistant Secretary of Defense (Special MICHAEL VICKERS Operations and Low-Intensity Conflict) Assistant Secretary of Defense (Homeland (VACANCY) Defense and America’s Security) Assistant Secretary of Defense (Global Strategic JOSEPH BENKERT Affairs Assistant Secretary of Defense (Asian and (VACANCY) Pacific Security Affairs) Deputy Assistant Secretary of Defense (Plans) JANINE DAVIDSON Deputy Under Secretary of Defense (VACANCY) (Technology Security Policy/Counter Proliferation) Deputy Under Secretary of Defense (Strategy, KATHLEEN HICKS Plans and Forces) Deputy Under Secretary of Defense (Policy PETER VERGA Integration and Chief of Staff) Principal Deputy Under Secretary of Defense WILLIAM J. CARR, Acting for Personnel and Readiness Assistant Secretary of Defense (Reserve Affairs) DAVID L. MCGINNIS, Acting Deputy Assistant Secretary of Defense (Reserve JENNIFER C. BUCK Affairs) Deputy Under Secretary of Defense (Program JEANNE FITES Integration) Deputy Under Secretary of Defense (Readiness) SAMUEL D. KLEINMAN Deputy Under Secretary of Defense (Military WILLIAM J. CARR Personnel Policy) Deputy Under Secretary of Defense (Military ARTHUR J. MYERS, Acting Community and Family Policy) Deputy Under Secretary of Defense (Plans) GAIL H. -

How America Lost Its Mind the Nation’S Current Post-Truth Moment Is the Ultimate Expression of Mind-Sets That Have Made America Exceptional Throughout Its History
1 How America Lost Its Mind The nation’s current post-truth moment is the ultimate expression of mind-sets that have made America exceptional throughout its history. KURT ANDERSEN SEPTEMBER 2017 ISSUE THE ATLANTIC “You are entitled to your own opinion, but you are not entitled to your own facts.” — Daniel Patrick Moynihan “We risk being the first people in history to have been able to make their illusions so vivid, so persuasive, so ‘realistic’ that they can live in them.” — Daniel J. Boorstin, The Image: A Guide to Pseudo-Events in America (1961) 1) WHEN DID AMERICA become untethered from reality? I first noticed our national lurch toward fantasy in 2004, after President George W. Bush’s political mastermind, Karl Rove, came up with the remarkable phrase reality-based community. People in “the reality-based community,” he told a reporter, “believe that solutions emerge from your judicious study of discernible reality … That’s not the way the world really works anymore.” A year later, The Colbert Report went on the air. In the first few minutes of the first episode, Stephen Colbert, playing his right-wing-populist commentator character, performed a feature called “The Word.” His first selection: truthiness. “Now, I’m sure some of the ‘word police,’ the ‘wordinistas’ over at Webster’s, are gonna say, ‘Hey, that’s not a word!’ Well, anybody who knows me knows that I’m no fan of dictionaries or reference books. They’re elitist. Constantly telling us what is or isn’t true. Or what did or didn’t happen. -

Women's Representation in Michigan
Women’s Representation in Michigan Parity Ranking: 8th of 50 Levels of Government Score of 27: Ten points for former Governor Jennifer Granholm, 3 for the secretary of state, 8 Statewide Executives points for U.S. Sen. Debbie Stabenow’s two most Female governors: Jennifer Granholm (2003- recent elections, 1 points for its single woman House member, 4 points for its percentage of 2011) state legislators who are women, and 1 point for Current female statewide elected executives: 1 of senate president pro tempore. 4 (secretary of state) Quick Fact Number of women to have held statewide elected In 2002, Michigan elected its third foreign-born executive office: 7, one of whom was appointed governor and its first woman governor, Jennifer Congress Granholm (D). Originally from Canada, Granholm became a naturalized American U.S. Senate: 1 of 2 seats held by women, Debbie citizen at the age of 21. She served two terms. Stabenow (2001-present) Trending U.S. House: 1 of 14 seats held by women In recent years, the Michigan state legislature In its history, Michigan has elected 7 women to has experienced large fluctuations in the the U.S. House, one of whom was also elected to percentage of seats held by women. Between the U.S. Senate. 2008 and 2009, it increased 5.4 points, but has State Legislature since decreased by 6.1 to 18.9%. Percentage women: 18.9% Rankings: 36th of 50 % Michigan Legislature Women Senate: 4 of 38 (10.5%) are women 30% 25% House: 24 of 110 (21.8%) are women 20% 15% Method of election: single-member districts 10% MI Local 5% USA 0% None of Michigan’s five largest cities and counties with elected executives has a woman mayor or county executive. -

Doomscrolling: Special Report 2
Copyright © All rights reserved worldwide. YOUR RIGHTS: This book is restricted to your personal use only. It does not come with any other rights. LEGAL DISCLAIMER: This book is protected by international copyright law and may not be copied, reproduced, given away, or used to create derivative works without the publisher’s expressed permission. The publisher retains full copyrights to this book. The author has made every reasonable effort to be as accurate and complete as possible in the creation of this book and to ensure that the information provided is free from errors; however, the author/publisher/ reseller assumes no responsibility for errors, omissions, or contrary interpretation of the subject matter herein and does not warrant or represent at any time that the contents within are accurate due to the rapidly changing nature of the internet. Any perceived slights of specific persons, peoples, or organizations are unintentional. The purpose of this book is to educate, and there are no guarantees of income, sales, or results implied. The publisher/author/reseller can, therefore, not be held accountable for any poor results you may attain when implementing the techniques or when following any guidelines set out for you in this book. Any product, website, and company names mentioned in this report are the trademarks or copyright properties of their respective owners. The author/publisher/reseller are not associated or affiliated with them in any way. Nor does the referred product, website, and company names sponsor, endorse, or approve this product. COMPENSATION DISCLOSURE: Unless otherwise expressly stated, you should assume that the links contained in this book may be affiliate links, and either the author/publisher/reseller will earn a commission if you click on them and buy the product/service mentioned in this book. -

14 DAYS in JANUARY Photojournalists’ Experiences and Images from Two Historic Weeks in Washington, D.C
JANUARY | FEBRUARY 2021 | A SPECIAL REPORT 14 DAYS IN JANUARY Photojournalists’ experiences and images from two historic weeks in Washington, D.C. After 75 years, this is the final News Photographer in magazine format. Say hell0 to News Photographer digital on nppa.org. See stories on pages 5 and 27. CONTENTS | JANUARY / FEBRUARY 2021 Editor's Column Sue Morrow 5 President's Column Katie Schoolov 27 Advocacy: Legal issues in the wake of the Capitol insurrection Mickey Osterreicher & Alicia Calzada 28 Spotlight: Small-market Carin Dorghalli 36 Pandemic changes the game for sports photographers Peggy Peattie 38 Eyes on Research: Training the next generation to see Dr. Gabriel B. Tate 44 Now we know her story: The woman in the iconic photograph Dai Sugano & Julia Prodis Sulek 48 Irresponsibility could cut off journalists' access to disasters Tracy Barbutes 54 The Image Deconstructed Rich-Joseph Facun, by Ross Taylor 60 14 Days in January Oliver Janney & contributors 70-117 Columnists Doing It Well: Matt Pearl 31 It's a Process: Eric Maierson 32 Career/Life Balance: Autumn Payne 35 Openers/Enders Pages 8, 10, 12, 14, 16, 18, 20 22, 24, 118, 120, 122, 124, 126, 128, 130, 132 ON THE COVER National Guard troops from New York City get a tour through the Rotunda of the U.S. Capitol on January 14, 2021. They were part of the defensive security build-up leading up to the inauguration of President-elect Joe Biden. Photo by David Burnett ©2020 Contact Press Images U.S. Capitol police try to fend off a pro-Trump mob that breached the Capitol on January 6, 2021, in Washington, D.C.