The Mathematical-Function Computation Handbook Nelson H.F
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Elementary Functions: Towards Automatically Generated, Efficient
Elementary functions : towards automatically generated, efficient, and vectorizable implementations Hugues De Lassus Saint-Genies To cite this version: Hugues De Lassus Saint-Genies. Elementary functions : towards automatically generated, efficient, and vectorizable implementations. Other [cs.OH]. Université de Perpignan, 2018. English. NNT : 2018PERP0010. tel-01841424 HAL Id: tel-01841424 https://tel.archives-ouvertes.fr/tel-01841424 Submitted on 17 Jul 2018 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Délivré par l’Université de Perpignan Via Domitia Préparée au sein de l’école doctorale 305 – Énergie et Environnement Et de l’unité de recherche DALI – LIRMM – CNRS UMR 5506 Spécialité: Informatique Présentée par Hugues de Lassus Saint-Geniès [email protected] Elementary functions: towards automatically generated, efficient, and vectorizable implementations Version soumise aux rapporteurs. Jury composé de : M. Florent de Dinechin Pr. INSA Lyon Rapporteur Mme Fabienne Jézéquel MC, HDR UParis 2 Rapporteur M. Marc Daumas Pr. UPVD Examinateur M. Lionel Lacassagne Pr. UParis 6 Examinateur M. Daniel Menard Pr. INSA Rennes Examinateur M. Éric Petit Ph.D. Intel Examinateur M. David Defour MC, HDR UPVD Directeur M. Guillaume Revy MC UPVD Codirecteur À la mémoire de ma grand-mère Françoise Lapergue et de Jos Perrot, marin-pêcheur bigouden. -

Github: a Case Study of Linux/BSD Perceptions from Microsoft's
1 FLOSS != GitHub: A Case Study of Linux/BSD Perceptions from Microsoft’s Acquisition of GitHub Raula Gaikovina Kula∗, Hideki Hata∗, Kenichi Matsumoto∗ ∗Nara Institute of Science and Technology, Japan {raula-k, hata, matumoto}@is.naist.jp Abstract—In 2018, the software industry giants Microsoft made has had its share of disagreements with Microsoft [6], [7], a move into the Open Source world by completing the acquisition [8], [9], the only reported negative opinion of free software of mega Open Source platform, GitHub. This acquisition was not community has different attitudes towards GitHub is the idea without controversy, as it is well-known that the free software communities includes not only the ability to use software freely, of ‘forking’ so far, as it it is considered as a danger to FLOSS but also the libre nature in Open Source Software. In this study, development [10]. our aim is to explore these perceptions in FLOSS developers. We In this paper, we report on how external events such as conducted a survey that covered traditional FLOSS source Linux, acquisition of the open source platform by a closed source and BSD communities and received 246 developer responses. organization triggers a FLOSS developers such the Linux/ The results of the survey confirm that the free community did trigger some communities to move away from GitHub and raised BSD Free Software communities. discussions into free and open software on the GitHub platform. The study reminds us that although GitHub is influential and II. TARGET SUBJECTS AND SURVEY DESIGN trendy, it does not representative all FLOSS communities. -

What Is a Closed-Form Number? Timothy Y. Chow the American
What is a Closed-Form Number? Timothy Y. Chow The American Mathematical Monthly, Vol. 106, No. 5. (May, 1999), pp. 440-448. Stable URL: http://links.jstor.org/sici?sici=0002-9890%28199905%29106%3A5%3C440%3AWIACN%3E2.0.CO%3B2-6 The American Mathematical Monthly is currently published by Mathematical Association of America. Your use of the JSTOR archive indicates your acceptance of JSTOR's Terms and Conditions of Use, available at http://www.jstor.org/about/terms.html. JSTOR's Terms and Conditions of Use provides, in part, that unless you have obtained prior permission, you may not download an entire issue of a journal or multiple copies of articles, and you may use content in the JSTOR archive only for your personal, non-commercial use. Please contact the publisher regarding any further use of this work. Publisher contact information may be obtained at http://www.jstor.org/journals/maa.html. Each copy of any part of a JSTOR transmission must contain the same copyright notice that appears on the screen or printed page of such transmission. JSTOR is an independent not-for-profit organization dedicated to and preserving a digital archive of scholarly journals. For more information regarding JSTOR, please contact [email protected]. http://www.jstor.org Mon May 14 16:45:04 2007 What Is a Closed-Form Number? Timothy Y. Chow 1. INTRODUCTION. When I was a high-school student, I liked giving exact answers to numerical problems whenever possible. If the answer to a problem were 2/7 or n-6 or arctan 3 or el/" I would always leave it in that form instead of giving a decimal approximation. -

Elementary Functions and Their Inverses*
ELEMENTARYFUNCTIONS AND THEIR INVERSES* BY J. F. RITT The chief item of this paper is the determination of all elementary functions whose inverses are elementary. The elementary functions are understood here to be those which are obtained in a finite number of steps by performing algebraic operations and taking exponentials and logarithms. For instance, the function tan \cf — log,(l + Vz)] + [«*+ log arc sin*]1« is elementary. We prove that if F(z) and its inverse are both elementary, there exist n functions Vt(*)j <hiz), •', <Pniz), where each <piz) with an odd index is algebraic, and each (p(z) with an even index is either e? or log?, such that F(g) = <pn(pn-f-<Pn9i(z) each q>i(z)ii<ît) being substituted for z in ^>iiiz). That every F(z) of this type has an elementary inverse is obvious. It remains to develop a method for recognizing whether a given elementary function can be reduced to the above form for F(.z). How to test fairly simple functions will be evident from the details of our proofs. For the immediate present, we let the general question stand. The present paper is an addition to Liouville's work of almost a century ago on the classification of the elementary functions, on the possibility of effecting integrations in finite terms, and on the impossibility of solving certain differentia] equations, and certain transcendental equations, in finite terms.!" Free use is made here of the ingenious methods of Liouville. * Presented to the Society, October 25, 1924. -(•Journal de l'Ecole Polytechnique, vol. -

Kratka Povijest Unixa Od Unicsa Do Freebsda I Linuxa
Kratka povijest UNIXa Od UNICSa do FreeBSDa i Linuxa 1 Autor: Hrvoje Horvat Naslov: Kratka povijest UNIXa - Od UNICSa do FreeBSDa i Linuxa Licenca i prava korištenja: Svi imaju pravo koristiti, mijenjati, kopirati i štampati (printati) knjigu, prema pravilima GNU GPL licence. Mjesto i godina izdavanja: Osijek, 2017 ISBN: 978-953-59438-0-8 (PDF-online) URL publikacije (PDF): https://www.opensource-osijek.org/knjige/Kratka povijest UNIXa - Od UNICSa do FreeBSDa i Linuxa.pdf ISBN: 978-953- 59438-1- 5 (HTML-online) DokuWiki URL (HTML): https://www.opensource-osijek.org/dokuwiki/wiki:knjige:kratka-povijest- unixa Verzija publikacije : 1.0 Nakalada : Vlastita naklada Uz pravo svakoga na vlastito štampanje (printanje), prema pravilima GNU GPL licence. Ova knjiga je napisana unutar inicijative Open Source Osijek: https://www.opensource-osijek.org Inicijativa Open Source Osijek je član udruge Osijek Software City: http://softwarecity.hr/ UNIX je registrirano i zaštićeno ime od strane tvrtke X/Open (Open Group). FreeBSD i FreeBSD logo su registrirani i zaštićeni od strane FreeBSD Foundation. Imena i logo : Apple, Mac, Macintosh, iOS i Mac OS su registrirani i zaštićeni od strane tvrtke Apple Computer. Ime i logo IBM i AIX su registrirani i zaštićeni od strane tvrtke International Business Machines Corporation. IEEE, POSIX i 802 registrirani i zaštićeni od strane instituta Institute of Electrical and Electronics Engineers. Ime Linux je registrirano i zaštićeno od strane Linusa Torvaldsa u Sjedinjenim Američkim Državama. Ime i logo : Sun, Sun Microsystems, SunOS, Solaris i Java su registrirani i zaštićeni od strane tvrtke Sun Microsystems, sada u vlasništvu tvrtke Oracle. Ime i logo Oracle su u vlasništvu tvrtke Oracle. -
![Arxiv:1911.10319V2 [Math.CA] 29 Dec 2019 Roswl Egvni H Etscin.Atraiey Ecnuse Can We Alternatively, Sections](https://docslib.b-cdn.net/cover/9632/arxiv-1911-10319v2-math-ca-29-dec-2019-roswl-egvni-h-etscin-atraiey-ecnuse-can-we-alternatively-sections-1059632.webp)
Arxiv:1911.10319V2 [Math.CA] 29 Dec 2019 Roswl Egvni H Etscin.Atraiey Ecnuse Can We Alternatively, Sections
Elementary hypergeometric functions, Heun functions, and moments of MKZ operators Ana-Maria Acu1a, Ioan Rasab aLucian Blaga University of Sibiu, Department of Mathematics and Informatics, Str. Dr. I. Ratiu, No.5-7, RO-550012 Sibiu, Romania, e-mail: [email protected] bTechnical University of Cluj-Napoca, Faculty of Automation and Computer Science, Department of Mathematics, Str. Memorandumului nr. 28 Cluj-Napoca, Romania, e-mail: [email protected] Abstract We consider some hypergeometric functions and prove that they are elementary functions. Con- sequently, the second order moments of Meyer-K¨onig and Zeller type operators are elementary functions. The higher order moments of these operators are expressed in terms of elementary func- tions and polylogarithms. Other applications are concerned with the expansion of certain Heun functions in series or finite sums of elementary hypergeometric functions. Keywords: hypergeometric functions, elementary functions, Meyer-K¨onig and Zeller type operators, polylogarithms; Heun functions 2010 MSC: 33C05, 33C90, 33E30, 41A36 1. Introduction This paper is devoted to some families of elementary hypergeometric functions, with applica- tions to the moments of Meyer-K¨onig and Zeller type operators and to the expansion of certain Heun functions in series or finite sums of elementary hypergeometric functions. In [4], J.A.H. Alkemade proved that the second order moment of the Meyer-K¨onig and Zeller operators can be expressed as 2 2 x(1 − x) Mn(e2; x)= x + 2F1(1, 2; n + 2; x), x ∈ [0, 1). (1.1) arXiv:1911.10319v2 [math.CA] 29 Dec 2019 n +1 r Here er(t) := t , t ∈ [0, 1], r ≥ 0, and 2F1(a,b; c; x) denotes the hypergeometric function. -

Open Systems December 27, 2019
1969 1970 1971 1972 1973 UNIX Time-Sharing System UNIX Time-Sharing System UNIX Time-Sharing System UNICS First Edition (V1) Second Edition (V2) Third Edition (V3) september 1969 november 3, 1971 june 12, 1972 february 1973 Open Systems December 27, 2019 Éric Lévénez 1998-2019 <http://www.levenez.com/unix/> 1974 1975 1976 1977 SRI Eunice UNSW Mini Unix may 1977 LSX UNIX Time-Sharing System UNIX Time-Sharing System UNIX Time-Sharing System Fourth Edition (V4) Fifth Edition (V5) Sixth Edition (V6) november 1973 june 1974 may 1975 PWB/UNIX PWB 1.0 1974 july 1, 1977 USG 1.0 TS 1.0 1977 MERT 1974 RT 1.0 1977 1978 1979 1980 UNIX Time-Sharing System Seventh Edition Modified (V7M) december 1980 1BSD 2BSD 2.79BSD march 9, 1978 may 10, 1979 april 1980 3BSD 4.0BSD march 1980 october 1980 UCLA Secure Unix 1979 The Wollongong Group Eunice (Edition 7) 1980 UNSW 01 UNSW 04 january 1978 november 1979 BRL Unix V4.1 july 1979 UNIX 32V V7appenda may 1979 february 12, 1980 UNIX Time-Sharing System Seventh Edition (V7) january 1979 PWB 2.0 PWB 1.2 1978 XENIX OS august 25, 1980 CB UNIX 1 CB CB UNIX 3 UNIX 2 USG 2.0 USG 3.0 TS 2.0 TS 3.0 TS 3.0.1 1978 1979 1980 Interactive IS/1 UCLA Locally Cooperating Unix Systems 1980 Note 1 : an arrow indicates an inheritance like a compatibility, it is not only a matter of source code. Note 2 : this diagram shows complete systems and [micro]kernels like Mach, Linux, the Hurd.. -
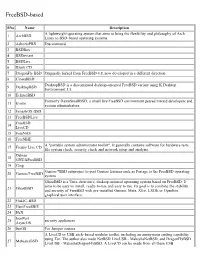
List of BSD Operating Systems
FreeBSD-based SNo Name Description A lightweight operating system that aims to bring the flexibility and philosophy of Arch 1 ArchBSD Linux to BSD-based operating systems. 2 AskoziaPBX Discontinued 3 BSDBox 4 BSDeviant 5 BSDLive 6 Bzerk CD 7 DragonFly BSD Originally forked from FreeBSD 4.8, now developed in a different direction 8 ClosedBSD DesktopBSD is a discontinued desktop-oriented FreeBSD variant using K Desktop 9 DesktopBSD Environment 3.5. 10 EclipseBSD Formerly DamnSmallBSD; a small live FreeBSD environment geared toward developers and 11 Evoke system administrators. 12 FenestrOS BSD 13 FreeBSDLive FreeBSD 14 LiveCD 15 FreeNAS 16 FreeSBIE A "portable system administrator toolkit". It generally contains software for hardware tests, 17 Frenzy Live CD file system check, security check and network setup and analysis. Debian 18 GNU/kFreeBSD 19 Ging Gentoo/*BSD subproject to port Gentoo features such as Portage to the FreeBSD operating 20 Gentoo/FreeBSD system GhostBSD is a Unix-derivative, desktop-oriented operating system based on FreeBSD. It aims to be easy to install, ready-to-use and easy to use. Its goal is to combine the stability 21 GhostBSD and security of FreeBSD with pre-installed Gnome, Mate, Xfce, LXDE or Openbox graphical user interface. 22 GuLIC-BSD 23 HamFreeSBIE 24 HeX IronPort 25 security appliances AsyncOS 26 JunOS For Juniper routers A LiveCD or USB stick-based modular toolkit, including an anonymous surfing capability using Tor. The author also made NetBSD LiveUSB - MaheshaNetBSD, and DragonFlyBSD 27 MaheshaBSD LiveUSB - MaheshaDragonFlyBSD. A LiveCD can be made from all these USB distributions by running the /makeiso script in the root directory. -

INTEGRATION STRATEGIES 1. Introduction It Should Be Clear Now
INTEGRATION STRATEGIES 1. Introduction It should be clear now that it is a whole lot easier to differentiate a function than integrating one. Typically the formula used to determine the derivative of a function is apparent. With integration, the appropriate formula won't necessarily be obvious. So far we have reviewed each of the basic techniques of integration: with substitutions (ch. 5.5, 7.2, 7.3 ), integration by parts (ch. 7.1), and partial fractions (ch 7.4). More realistically, integrals will be given outside of the context of a textbook chapter and the challenge is to identify which formula(s) to use. We will review several integrals at random and suggest strategies for determining which formula to evaluate the integral. These strategies will only be helpful if one has a knowledge of basic integration formulas. Listed in the table below are an expanded list of the formulas for commonly used integrals. Many of these can be derived using basic principles it will be helpful to memorize these. In lieu of formulas 19 and 20 one could use partial fractions and trigonometric substitutions respectively. Figure 1. Table of Integration Formulas Constant of integra- tion have been omitted. 1 2 INTEGRATION STRATEGIES 2. Strategies If an integral does not fit into this basic list of integration formulas, try the following strategy: (1) Simplify the Integrand if Possible: Algebraic manipulation or trigono- metric identities can simplify the integrand and allow for integration in its new form. For example, p p p R x(1 + x)dx = R ( x + x)dx; R tan θ R sin θ 2 R R sec2 θ dθ = cos θ cos θdθ = sin θ cos θdθ = frac12 sin 2θdθ; R (sin x + cos x)2dx = R (sin2 x + 2 sin x cos x + cos2 x)dx = R (1 + 2 sin x cos x)dx; (2) Look for an Obvious Substitution: Try substitutions u = g(x) in the integrand for which the differential du = g0(x)dx also appears in the integran. -

Elementary Functions and Approximate Computing Jean-Michel Muller
Elementary Functions and Approximate Computing Jean-Michel Muller To cite this version: Jean-Michel Muller. Elementary Functions and Approximate Computing. Proceedings of the IEEE, Institute of Electrical and Electronics Engineers, 2020, 108 (12), pp.1558-2256. 10.1109/JPROC.2020.2991885. hal-02517784v2 HAL Id: hal-02517784 https://hal.archives-ouvertes.fr/hal-02517784v2 Submitted on 29 Apr 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. 1 Elementary Functions and Approximate Computing Jean-Michel Muller** Univ Lyon, CNRS, ENS de Lyon, Inria, Université Claude Bernard Lyon 1, LIP UMR 5668, F-69007 Lyon, France Abstract—We review some of the classical methods used for consequence of that nonlinearity is that a small input error quickly obtaining low-precision approximations to the elementary can sometimes imply a large output error. Hence a very careful functions. Then, for each of the three main classes of elementary error control is necessary, especially when approximations are function algorithms (shift-and-add algorithms, polynomial or rational approximations, table-based methods) and for the ad- cascaded: approximate computing cannot be quick and dirty y y log (x) ditional, specific to approximate computing, “bit-manipulation” computing. -

The Ocaml System Release 4.02
The OCaml system release 4.02 Documentation and user's manual Xavier Leroy, Damien Doligez, Alain Frisch, Jacques Garrigue, Didier R´emy and J´er^omeVouillon August 29, 2014 Copyright © 2014 Institut National de Recherche en Informatique et en Automatique 2 Contents I An introduction to OCaml 11 1 The core language 13 1.1 Basics . 13 1.2 Data types . 14 1.3 Functions as values . 15 1.4 Records and variants . 16 1.5 Imperative features . 18 1.6 Exceptions . 20 1.7 Symbolic processing of expressions . 21 1.8 Pretty-printing and parsing . 22 1.9 Standalone OCaml programs . 23 2 The module system 25 2.1 Structures . 25 2.2 Signatures . 26 2.3 Functors . 27 2.4 Functors and type abstraction . 29 2.5 Modules and separate compilation . 31 3 Objects in OCaml 33 3.1 Classes and objects . 33 3.2 Immediate objects . 36 3.3 Reference to self . 37 3.4 Initializers . 38 3.5 Virtual methods . 38 3.6 Private methods . 40 3.7 Class interfaces . 42 3.8 Inheritance . 43 3.9 Multiple inheritance . 44 3.10 Parameterized classes . 44 3.11 Polymorphic methods . 47 3.12 Using coercions . 50 3.13 Functional objects . 54 3.14 Cloning objects . 55 3.15 Recursive classes . 58 1 2 3.16 Binary methods . 58 3.17 Friends . 60 4 Labels and variants 63 4.1 Labels . 63 4.2 Polymorphic variants . 69 5 Advanced examples with classes and modules 73 5.1 Extended example: bank accounts . 73 5.2 Simple modules as classes . -

Antiderivatives Basic Integration Formulas Structural Type Formulas
Antiderivatives Definition 1 (Antiderivative). If F 0(x) = f(x) we call F an antideriv- ative of f. Definition 2 (Indefinite Integral). If F is an antiderivative of f, then R f(x) dx = F (x) + c is called the (general) Indefinite Integral of f, where c is an arbitrary constant. The indefinite integral of a function represents every possible antideriv- ative, since it has been shown that if two functions have the same de- rivative on an interval then they differ by a constant on that interval. Terminology: When we write R f(x) dx, f(x) is referred to as the in- tegrand. Basic Integration Formulas As with differentiation, there are two types of formulas, formulas for the integrals of specific functions and structural type formulas. Each formula for the derivative of a specific function corresponds to a formula for the derivative of an elementary function. The following table lists integration formulas side by side with the corresponding differentiation formulas. Z xn+1 d xn dx = if n 6= −1 (xn) = nxn−1 n + 1 dx Z d sin x dx = − cos x + c (cos x) = − sin x dx Z d cos x dx = sin x + c (sin x) = cos x dx Z d sec2 x dx = tan x + c (tan x) = sec2 x dx Z d ex dx = ex + c (ex) = ex dx Z 1 d 1 dx = ln x + c (ln x) = x dx x Z d k dx = kx + c (kx) = k dx Structural Type Formulas We may integrate term-by-term: R kf(x) dx = k R f(x) dx 1 2 R f(x) ± g(x) dx = R f(x) dx ± R g(x) dx In plain language, the integral of a constant times a function equals the constant times the derivative of the function and the derivative of a sum or difference is equal to the sum or difference of the derivatives.