BSD Magazine
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

BSD Magazine
FREENAS MINI FREENAS STORAGE APPLIANCE CERTIFIED IT SAVES YOUR LIFE. STORAGE HOW IMPORTANT IS YOUR DATA? With over six million downloads, As one of the leaders in the storage industry, you FreeNAS is undisputedly the most know that you’re getting the best combination of hardware designed for optimal performance Years of family photos. Your entire music popular storage operating system and movie collection. Office documents with FreeNAS. Contact us today for a FREE Risk in the world. you’ve put hours of work into. Backups for Elimination Consultation with one of our FreeNAS experts. Remember, every purchase directly supports every computer you own. We ask again, how Sure, you could build your own FreeNAS system: the FreeNAS project so we can continue adding important is your data? research every hardware option, order all the features and improvements to the software for years parts, wait for everything to ship and arrive, vent at to come. And really - why would you buy a FreeNAS customer service because it hasn’t, and finally build it server from anyone else? NOW IMAGINE LOSING IT ALL yourself while hoping everything fits - only to install the software and discover that the system you spent Losing one bit - that’s all it takes. One single bit, and days agonizing over isn’t even compatible. Or... your file is gone. The worst part? You won’t know until you MAKE IT EASY ON YOURSELF absolutely need that file again. Example of one-bit corruption As the sponsors and lead developers of the FreeNAS project, iXsystems has combined over 20 years of THE SOLUTION hardware experience with our FreeNAS expertise to The Mini boasts these state-of-the- The FreeNAS Mini has emerged as the clear choice to bring you FreeNAS Certified Storage.We make it art features: save your digital life. -

Github: a Case Study of Linux/BSD Perceptions from Microsoft's
1 FLOSS != GitHub: A Case Study of Linux/BSD Perceptions from Microsoft’s Acquisition of GitHub Raula Gaikovina Kula∗, Hideki Hata∗, Kenichi Matsumoto∗ ∗Nara Institute of Science and Technology, Japan {raula-k, hata, matumoto}@is.naist.jp Abstract—In 2018, the software industry giants Microsoft made has had its share of disagreements with Microsoft [6], [7], a move into the Open Source world by completing the acquisition [8], [9], the only reported negative opinion of free software of mega Open Source platform, GitHub. This acquisition was not community has different attitudes towards GitHub is the idea without controversy, as it is well-known that the free software communities includes not only the ability to use software freely, of ‘forking’ so far, as it it is considered as a danger to FLOSS but also the libre nature in Open Source Software. In this study, development [10]. our aim is to explore these perceptions in FLOSS developers. We In this paper, we report on how external events such as conducted a survey that covered traditional FLOSS source Linux, acquisition of the open source platform by a closed source and BSD communities and received 246 developer responses. organization triggers a FLOSS developers such the Linux/ The results of the survey confirm that the free community did trigger some communities to move away from GitHub and raised BSD Free Software communities. discussions into free and open software on the GitHub platform. The study reminds us that although GitHub is influential and II. TARGET SUBJECTS AND SURVEY DESIGN trendy, it does not representative all FLOSS communities. -

Systemd – Easy As 1, 2, 3
Systemd – Easy as 1, 2, 3 Ben Breard, RHCA Solutions Architect, Red Hat [email protected] Agenda ● Systemd functionality ● Coming to terms ● Learning the basics ● More advanced topics ● Learning the journal ● Available resources 2 Systemd is more than a SysVinit replacement 3 Systemd is a system and service manager 4 Systemd Overview ● Controls “units” rather than just daemons ● Handles dependency between units. ● Tracks processes with service information ● Services are owned by a cgroup. ● Simple to configure “SLAs” based on CPU, Memory, and IO. ● Properly kill daemons ● Minimal boot times ● Debuggability – no early boot messages are lost ● Easy to learn and backwards compatible. 5 Closer look at Units 6 Systemd - Units ● Naming convention is: name.type ● httpd.service, sshd.socket, or dev-hugepages.mount ● Service – Describe a daemon's type, execution, environment, and how it's monitored. ● Socket – Endpoint for interprocess communication. File, network, or Unix sockets. ● Target – Logical grouping of units. Replacement for runlevels. ● Device – Automatically created by the kernel. Can be provided to services as dependents. ● Mounts, automounts, swap – Monitor the mounting/unmounting of file systems. 7 Systemd – Units Continued ● Snapshots – save the state of units – useful for testing ● Timers – Timer-based activation ● Paths – Uses inotify to monitor a path ● Slices – For resource management. ● system.slice – services started by systemd ● user.slice – user processes ● machine.slice – VMs or containers registered with systemd 8 Systemd – Dependency Resolution ● Example: ● Wait for block device ● Check file system for device ● Mount file system ● nfs-lock.service: ● Requires=rpcbind.service network.target ● After=network.target named.service rpcbind.service ● Before=remote-fs-pre.target 9 That's all great .......but 10 Replace Init scripts!? Are you crazy?! 11 We're not crazy, I promise ● SysVinit had a good run, but leaves a lot to be desired. -

Cisco Virtualized Infrastructure Manager Installation Guide, 2.4.9
Cisco Virtualized Infrastructure Manager Installation Guide, 2.4.9 First Published: 2019-01-09 Last Modified: 2019-05-20 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB's public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Ixsystems Truenas Product Family
iXsystems TrueNAS Product Family Platforms FreeNAS FreeNAS TrueNAS TrueNAS TrueNAS TrueNAS Mini Certified X10 X20 M40 M50 Typical User SoHo Small/Med Office Business Essential/Mission-Critical Enterprise Form Factor Mini Tower 1U, 2U, 4U 2U 4U High Availability No Yes, Hot Swappable Storage Controllers (1 or 2) Storage Architecture HDD + Optional R/W Cache HDD + R/W Cache or SSD only Storage Technology SATA SATA/SAS SAS SAS SAS, NVMe Read Cache SATA SSD SAS3 SSD NVMe Technology Read Cache Size 480GB 800 GB 400 GB 800 GB 2.4 TB 12.5 TB NVMe Write Cache SATA SSD SATA SSD SAS3 SSD NVDIMM Technology vCPU per Controller 2-8 12-64 12 12 20 40 RAM per Controller 8-64 GB 32-256 GB 32 GB 64 GB 128 GB 256 GB-1.5 TB Expansion Shelves 0 By Request 2 2 2 12 Max Physical Storage 80 TB 240 TB 500 TB 1 PB 2 PB 10 PB Max Effective Storage* 200 TB 600 TB 1.2 PB 2.5 PB 5 PB 25 PB Max Ethernet Speed 2x10 GbE 2x40 GbE 2x10 GbE 4x10 GbE 2x40 GbE 4x100 GbE Fibre Channel (option) Not Available 8 Gb 4x16 Gb 4x32 Gb Software Enterprise File System OpenZFS - File, Block, and Object Services - Open Source Data Management Snapshots, Replication, Rollback, Clones, Encryption, Mirroring, RAIDZ1/Z2/Z3 Data Reduction Thin Provisioning, Compression, Clones, Deduplication Access Protocols NFSv3, NFSv4, SMB, AFP, iSCSI, HTTP/WebDAV, FTP, S3 Management IPMI, WebUI, REST API, SSH, SNMP, LDAP, Kerberos, Active Directory Protocols Application Application Plugins vCenter plugin, OpenStack Cinder driver Integration Software Clients: Unix, Linux, Windows, + Enterprise Software: VMware, OpenStack, Citrix, Veeam Compatibility FreeBSD, MacOS Support Hardware Warranty 1 to 3 Years 3 to 5 Years Up to 5 Years, Worldwide, Advanced Parts Replacement Deployment Services Self-deployment Included Deployment and Tuning, Proactive Monitoring option Software Support Community Worldwide, up to 24x365, Phone or email Software Updates Included Included-Zero downtime upgrades with HA * Compression rates vary by application. -

Kratka Povijest Unixa Od Unicsa Do Freebsda I Linuxa
Kratka povijest UNIXa Od UNICSa do FreeBSDa i Linuxa 1 Autor: Hrvoje Horvat Naslov: Kratka povijest UNIXa - Od UNICSa do FreeBSDa i Linuxa Licenca i prava korištenja: Svi imaju pravo koristiti, mijenjati, kopirati i štampati (printati) knjigu, prema pravilima GNU GPL licence. Mjesto i godina izdavanja: Osijek, 2017 ISBN: 978-953-59438-0-8 (PDF-online) URL publikacije (PDF): https://www.opensource-osijek.org/knjige/Kratka povijest UNIXa - Od UNICSa do FreeBSDa i Linuxa.pdf ISBN: 978-953- 59438-1- 5 (HTML-online) DokuWiki URL (HTML): https://www.opensource-osijek.org/dokuwiki/wiki:knjige:kratka-povijest- unixa Verzija publikacije : 1.0 Nakalada : Vlastita naklada Uz pravo svakoga na vlastito štampanje (printanje), prema pravilima GNU GPL licence. Ova knjiga je napisana unutar inicijative Open Source Osijek: https://www.opensource-osijek.org Inicijativa Open Source Osijek je član udruge Osijek Software City: http://softwarecity.hr/ UNIX je registrirano i zaštićeno ime od strane tvrtke X/Open (Open Group). FreeBSD i FreeBSD logo su registrirani i zaštićeni od strane FreeBSD Foundation. Imena i logo : Apple, Mac, Macintosh, iOS i Mac OS su registrirani i zaštićeni od strane tvrtke Apple Computer. Ime i logo IBM i AIX su registrirani i zaštićeni od strane tvrtke International Business Machines Corporation. IEEE, POSIX i 802 registrirani i zaštićeni od strane instituta Institute of Electrical and Electronics Engineers. Ime Linux je registrirano i zaštićeno od strane Linusa Torvaldsa u Sjedinjenim Američkim Državama. Ime i logo : Sun, Sun Microsystems, SunOS, Solaris i Java su registrirani i zaštićeni od strane tvrtke Sun Microsystems, sada u vlasništvu tvrtke Oracle. Ime i logo Oracle su u vlasništvu tvrtke Oracle. -

BSD Projects IV – BSD Certification • Main Features • Community • Future Directions a (Very) Brief History of BSD
BSD Overview Jim Brown May 24, 2012 BSD Overview - 5/24/2012 - Jim Brown, ISD BSD Overview I – A Brief History of BSD III – Cool Hot Stuff • ATT UCB Partnership • Batteries Included • ATT(USL) Lawsuit • ZFS , Hammer • BSD Family Tree • pf Firewall, pfSense • BSD License • Capsicum • Virtualization Topics • Jails, Xen, etc. • Desktop PC-BSD II – The Core BSD Projects IV – BSD Certification • Main Features • Community • Future Directions A (Very) Brief History of BSD 1971 – ATT cheaply licenses Unix source code to many organizations, including UCB as educational material 1975 – Ken Thompson takes a sabbatical from ATT, brings the latest Unix source on tape to UCB his alma mater to run on a PDP 11 which UCB provided. (Industry/academic partnerships were much more common back then.) Computer Science students (notably Bill Joy and Chuck Haley) at UCB begin to make numerous improvements to Unix and make them available on tape as the “Berkeley Software Distribution” - BSD A (Very) Brief History of BSD Some notable CSRG • 1980 – Computer Science Research Group members (CSRG) forms at UCB with DARPA funding to make many more improvements to Unix - job control, autoreboot, fast filesystem, gigabit address space, Lisp, IPC, sockets, TCP/IP stack + applications, r* utils, machine independence, rewriting almost all ATT code with UCB/CSRG code, including many ports • 1991 – The Networking Release 2 tape is released on the Internet via anon FTP. A 386 port quickly follows by Bill and Lynne Jolitz. The NetBSD group is formed- the first Open Source community entirely on the Internet • 1992 – A commercial version, BSDI (sold for $995, 1-800-ITS-UNIX) draws the ire of USL/ATT. -

The Mathematical-Function Computation Handbook Nelson H.F
The Mathematical-Function Computation Handbook Nelson H.F. Beebe The Mathematical-Function Computation Handbook Programming Using the MathCW Portable Software Library Nelson H.F. Beebe Department of Mathematics University of Utah Salt Lake City, UT USA ISBN 978-3-319-64109-6 ISBN 978-3-319-64110-2 (eBook) DOI 10.1007/978-3-319-64110-2 Library of Congress Control Number: 2017947446 © Springer International Publishing AG 2017 This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. The use of general descriptive names, registered names, trademarks, service marks, etc. in this publication does not imply, even in the absence of a specific statement, that such names are exempt from the relevant protective laws and regulations and therefore free for general use. The publisher, the authors and the editors are safe to assume that the advice and information in this book are believed to be true and accurate at the date of publication. Neither the publisher nor the authors or the editors give a warranty, express or implied, with respect to the material contained herein or for any errors or omissions that may have been made. The publisher remains neutral with regard to jurisdictional claims in published maps and institutional affiliations. Printed on acid-free paper This Springer imprint is published by Springer Nature The registered company is Springer International Publishing AG The registered company address is: Gewerbestrasse 11, 6330 Cham, Switzerland Dedication This book and its software are dedicated to three Williams: Cody, Kahan, and Waite. -

Open Systems December 27, 2019
1969 1970 1971 1972 1973 UNIX Time-Sharing System UNIX Time-Sharing System UNIX Time-Sharing System UNICS First Edition (V1) Second Edition (V2) Third Edition (V3) september 1969 november 3, 1971 june 12, 1972 february 1973 Open Systems December 27, 2019 Éric Lévénez 1998-2019 <http://www.levenez.com/unix/> 1974 1975 1976 1977 SRI Eunice UNSW Mini Unix may 1977 LSX UNIX Time-Sharing System UNIX Time-Sharing System UNIX Time-Sharing System Fourth Edition (V4) Fifth Edition (V5) Sixth Edition (V6) november 1973 june 1974 may 1975 PWB/UNIX PWB 1.0 1974 july 1, 1977 USG 1.0 TS 1.0 1977 MERT 1974 RT 1.0 1977 1978 1979 1980 UNIX Time-Sharing System Seventh Edition Modified (V7M) december 1980 1BSD 2BSD 2.79BSD march 9, 1978 may 10, 1979 april 1980 3BSD 4.0BSD march 1980 october 1980 UCLA Secure Unix 1979 The Wollongong Group Eunice (Edition 7) 1980 UNSW 01 UNSW 04 january 1978 november 1979 BRL Unix V4.1 july 1979 UNIX 32V V7appenda may 1979 february 12, 1980 UNIX Time-Sharing System Seventh Edition (V7) january 1979 PWB 2.0 PWB 1.2 1978 XENIX OS august 25, 1980 CB UNIX 1 CB CB UNIX 3 UNIX 2 USG 2.0 USG 3.0 TS 2.0 TS 3.0 TS 3.0.1 1978 1979 1980 Interactive IS/1 UCLA Locally Cooperating Unix Systems 1980 Note 1 : an arrow indicates an inheritance like a compatibility, it is not only a matter of source code. Note 2 : this diagram shows complete systems and [micro]kernels like Mach, Linux, the Hurd.. -
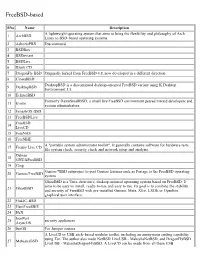
List of BSD Operating Systems
FreeBSD-based SNo Name Description A lightweight operating system that aims to bring the flexibility and philosophy of Arch 1 ArchBSD Linux to BSD-based operating systems. 2 AskoziaPBX Discontinued 3 BSDBox 4 BSDeviant 5 BSDLive 6 Bzerk CD 7 DragonFly BSD Originally forked from FreeBSD 4.8, now developed in a different direction 8 ClosedBSD DesktopBSD is a discontinued desktop-oriented FreeBSD variant using K Desktop 9 DesktopBSD Environment 3.5. 10 EclipseBSD Formerly DamnSmallBSD; a small live FreeBSD environment geared toward developers and 11 Evoke system administrators. 12 FenestrOS BSD 13 FreeBSDLive FreeBSD 14 LiveCD 15 FreeNAS 16 FreeSBIE A "portable system administrator toolkit". It generally contains software for hardware tests, 17 Frenzy Live CD file system check, security check and network setup and analysis. Debian 18 GNU/kFreeBSD 19 Ging Gentoo/*BSD subproject to port Gentoo features such as Portage to the FreeBSD operating 20 Gentoo/FreeBSD system GhostBSD is a Unix-derivative, desktop-oriented operating system based on FreeBSD. It aims to be easy to install, ready-to-use and easy to use. Its goal is to combine the stability 21 GhostBSD and security of FreeBSD with pre-installed Gnome, Mate, Xfce, LXDE or Openbox graphical user interface. 22 GuLIC-BSD 23 HamFreeSBIE 24 HeX IronPort 25 security appliances AsyncOS 26 JunOS For Juniper routers A LiveCD or USB stick-based modular toolkit, including an anonymous surfing capability using Tor. The author also made NetBSD LiveUSB - MaheshaNetBSD, and DragonFlyBSD 27 MaheshaBSD LiveUSB - MaheshaDragonFlyBSD. A LiveCD can be made from all these USB distributions by running the /makeiso script in the root directory. -

The Ocaml System Release 4.02
The OCaml system release 4.02 Documentation and user's manual Xavier Leroy, Damien Doligez, Alain Frisch, Jacques Garrigue, Didier R´emy and J´er^omeVouillon August 29, 2014 Copyright © 2014 Institut National de Recherche en Informatique et en Automatique 2 Contents I An introduction to OCaml 11 1 The core language 13 1.1 Basics . 13 1.2 Data types . 14 1.3 Functions as values . 15 1.4 Records and variants . 16 1.5 Imperative features . 18 1.6 Exceptions . 20 1.7 Symbolic processing of expressions . 21 1.8 Pretty-printing and parsing . 22 1.9 Standalone OCaml programs . 23 2 The module system 25 2.1 Structures . 25 2.2 Signatures . 26 2.3 Functors . 27 2.4 Functors and type abstraction . 29 2.5 Modules and separate compilation . 31 3 Objects in OCaml 33 3.1 Classes and objects . 33 3.2 Immediate objects . 36 3.3 Reference to self . 37 3.4 Initializers . 38 3.5 Virtual methods . 38 3.6 Private methods . 40 3.7 Class interfaces . 42 3.8 Inheritance . 43 3.9 Multiple inheritance . 44 3.10 Parameterized classes . 44 3.11 Polymorphic methods . 47 3.12 Using coercions . 50 3.13 Functional objects . 54 3.14 Cloning objects . 55 3.15 Recursive classes . 58 1 2 3.16 Binary methods . 58 3.17 Friends . 60 4 Labels and variants 63 4.1 Labels . 63 4.2 Polymorphic variants . 69 5 Advanced examples with classes and modules 73 5.1 Extended example: bank accounts . 73 5.2 Simple modules as classes . -

Continuous Integration with Jenkins
Automated Deployment … of Debian & Ubuntu Michael Prokop About Me Debian Developer Project lead of Grml.org ounder of Grml-Forensic.org #nvolved in A#$ initramf"-tools$ etc. Member in Debian orensic Team Author of &ook $$Open Source Projektmanagement) #T *on"ultant Disclaimer" Deployment focuses on Linux (everal tools mentioned$ but there exist even more :. We'll cover some sections in more detail than others %here's no one-size-fits-all solution – identify what works for you Sy"tems Management Provisioning 4 Documentation &oot"trapping #nfrastructure 'rche"tration 4 Development Dev'ps Automation 6isualization/Trends *onfiguration 4Metric" + Logs Management Monitoring + *loud Service Updates Deployment Systems Management Remote Acce"" ipmi, HP i+'$ IBM RSA,... irm3are Management 9Vendor Tools Provisioning / Bootstrapping :ully) A(utomatic) I(n"tallation) Debian, Ubuntu$ Cent'( + Scientific +inu, http://fai-project.org/ ;uju Ubuntu <Charms= https-44juju.ubuntu.com/ grml-debootstrap netscript=http://example.org/net"cript.sh http-44grml.org4 d-i preseeding auto url>http-44debian.org/releases4\ "queeze/example-preseed.txt http-443iki.debian.org/DebianInstaller/Preseed Kickstart Cobbler Foreman AutoYa(%$ openQRM, (pace3alk,... Orche"tration / Automation Fabric (Python) % cat fabfile.py from fabric.api import run def host_type(): run('uname -s') % fab -H host1, host2,host3 host_type Capistrano (Ruby) % cat Capfile role :hosts, "host1", "host2", "host3" task :host_type, :roles => :hosts do run "uname -s" end % cap host_type 7undeck apt-dater % cat .config/apt-dater/hosts.conf [example.org] [email protected];mika@ mail.example.org;... *ontrolTier, Func$ MCollective$... *luster((8$ dsh, TakTuk,... *obbler$ Foreman$ openQRM, Spacewalk,... *onfiguration Management Puppet Environment" :production4"taging/development.